Cloud Security Posture Management (CSPM)
Privilegia le configurazioni errate del cloud con gli approfondimenti basati sull'identità
Una singola configurazione errata o una cattiva gestione dei servizi cloud potrebbe comportare multe e cause legali che costerebbero alla tua organizzazione centinaia di milioni di dollari. Ottieni il massimo della sicurezza delle identità nel cloud per rilevare con precisione, assegnare priorità e correggere i maggiori rischi legati alla configurazione e alle autorizzazioni.
Richiedi una demo
Cos'è la gestione della postura di sicurezza del cloud (CSPM)?
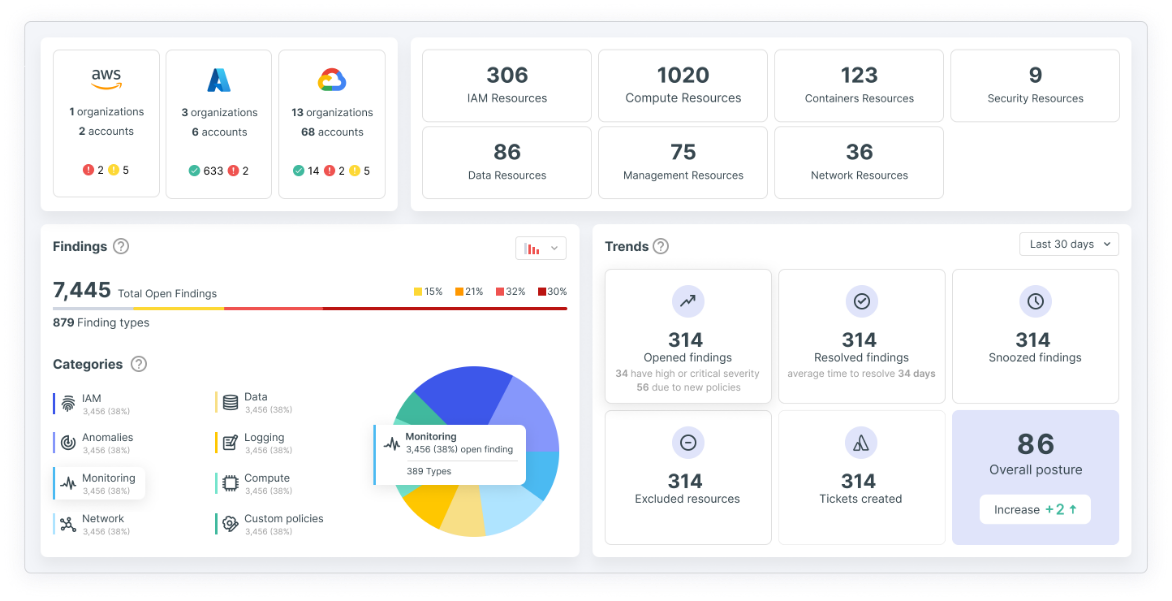
CSPM è un segmento di mercato per gli strumenti di sicurezza informatica progettati per identificare i problemi di configurazione errata e i rischi di conformità nel cloud. Uno strumento CSPM convalida i criteri di sicurezza che definiscono lo stato desiderato del cloud e ne garantisce l'esecuzione in produzione. Controlla i criteri rispetto ad ambienti multi-cloud, in modo da poter visualizzare e assegnare priorità alle configurazioni errate rilevate, fornire report sullo stato di conformità e correggere i rischi riscontrati.
Ottieni la CSPM integrata in un'unica soluzione olistica per la sicurezza del cloud
Con Tenable Cloud Security, non ottieni solo degli avvisi che indicano semplicemente un rischio, bensì risultati praticabili e di facile comprensione che ti aiuteranno a prendere rapidamente le decisioni. Inoltre, puoi automatizzare la tua risposta o scegliere una correzione guidata. Non dovrai più perdere tempo in analisi manuali o smistare gli avvisi da più strumenti in modo frammentario. Tenable consente di impostare criteri precisi che affrontano il rischio e la conformità e di creare un privilegio minimo a livello organizzativo per ridurre l'esposizione.
Riduci le configurazioni errate e i rischi dell'infrastruttura cloud
Puoi avere la conformità, ma non la sicurezza. Anche una piccola impostazione non configurata correttamente può esporre gli asset sensibili ai malintenzionati. Per evitare gli attacchi, è necessario eliminare i rischi e applicare le best practice di sicurezza, compreso il privilegio minimo, ma farlo manualmente su larga scala è quasi impossibile.
Tenable aiuta a verificare automaticamente le configurazioni, le impostazioni di sicurezza e la conformità del cloud rispetto ai framework comuni, ai requisiti normativi e ai criteri aziendali per determinare i casi di rischio eccessivo. In questo modo riduce al minimo gli avvisi e aiuta a definire con precisione le priorità dei rischi, a gestire in modo proattivo la non conformità e a correggere automaticamente configurazioni errate, violazioni e rischi, compresi quelli basati sulle identità.

"Gli audit di sicurezza nel cloud non sono una questione banale. Permettendoci di saltare i controlli, Ermetic [ora Tenable Cloud Security] ha dimostrato di essere una tecnologia all'altezza e in grado di far risparmiare tempo".
Etienne SmithCTO, Kikapay
Ottieni la conformità al cloud grazie alla scansione continua e report con un solo clic
Tenable Cloud Security semplifica la conformità al cloud. Ottieni un'unica soluzione per la scansione continua delle configurazioni e delle risorse in più ambienti cloud, prevenendo le violazioni e garantendo l'aderenza ai criteri di sicurezza.
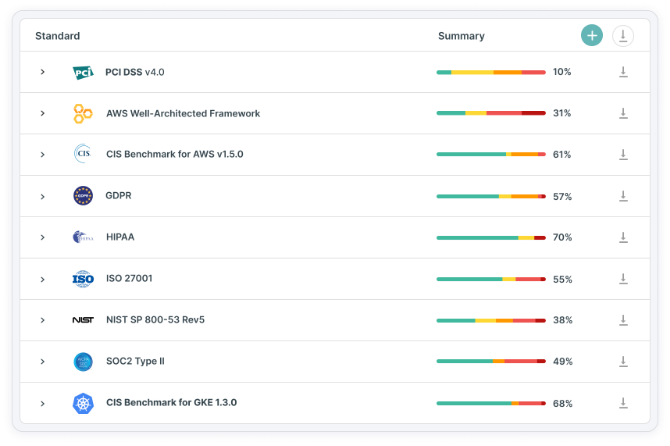
Con Tenable puoi eseguire l'audit di ambienti multi-cloud rispetto a standard di settore come CIS, AWS Well Architected, GDPR, HIPAA, ISO, NIST, PCI-DSS, SOC2, CIS per Kubernetes e creare controlli personalizzati. Inoltre, Tenable genera rapidamente report approfonditi per la conformità interna, gli audit esterni e le operazioni di sicurezza quotidiane (inventario degli asset, configurazioni errate, configurazioni di rete e così via), in modo da ridurre il lavoro manuale e risparmiare tempo.
Automatizza la sicurezza e la conformità per gli ambienti K8S
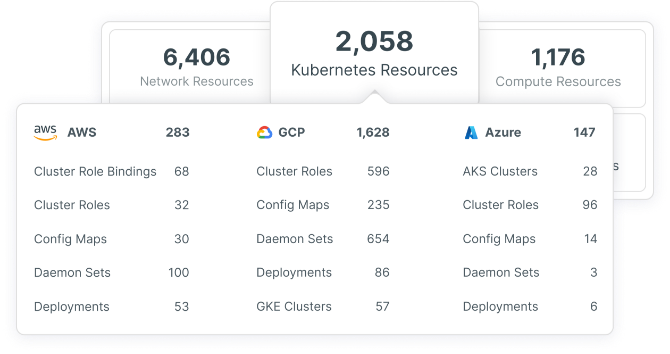
Come parte di Tenable Cloud Security, avrai anche una potente soluzione di Kubernetes Security Posture Management (KSPM) che scansiona Kubernetes, on-premise o nel cloud pubblico. Ottieni una visibilità completa e contestuale delle risorse Kubernetes, compresi nodi, spazi dei nomi, distribuzioni, server e account di servizio. Puoi inoltre controllare e proteggere le nuove risorse create in un cluster Kubernetes con un controller di ammissione Kubernetes integrato e personalizzabile.
Ottieni la sicurezza completa del cloud con la CNAPP unificata di Tenable
Con Tenable Cloud Security, Tenable offre una piattaforma completa di protezione delle applicazioni native per il cloud per AWS, Azure e GCP. Con al centro la soluzione Cloud Infrastructure Entitlement Management (CIEM) leader di mercato, riduce drasticamente la superficie di attacco del cloud e applica privilegi minimi su larga scala.
"L'utilizzo dell'automazione di Tenable Cloud Securit ci ha permesso di eliminare i processi manuali e di eseguire in pochi minuti ciò che avrebbe richiesto mesi di lavoro a due o tre addetti alla sicurezza".
Larry VivianoDirector of Information Security, IntelyCare
Scopri di più su Tenable Cloud Security
L'utilizzo dell'automazione [di Tenable Cloud Security] ci ha permesso di eliminare i processi manuali e di eseguire in pochi minuti ciò che avrebbe richiesto mesi di lavoro a due o tre addetti alla sicurezza.
- Tenable Cloud Security