Applica i privilegi minimi con accesso Just-in-Time
Ora è possibile concedere l'accesso privilegiato solo quando necessario e impostare limiti di tempo per l'accesso. Fornisci approvazioni di accesso rapide, riducendo al minimo la superficie di attacco del cloud e prevenendo i privilegi in piedi.
Bilancia accesso e rischio
Riduci al minimo il rischio che gli utenti malintenzionati sfruttino privilegi eccessivi, concedendo l'accesso solo quando esiste una chiara giustificazione aziendale e solo per un breve periodo di tempo.

Limita le esposizioni
con l'accesso Just-in-Time
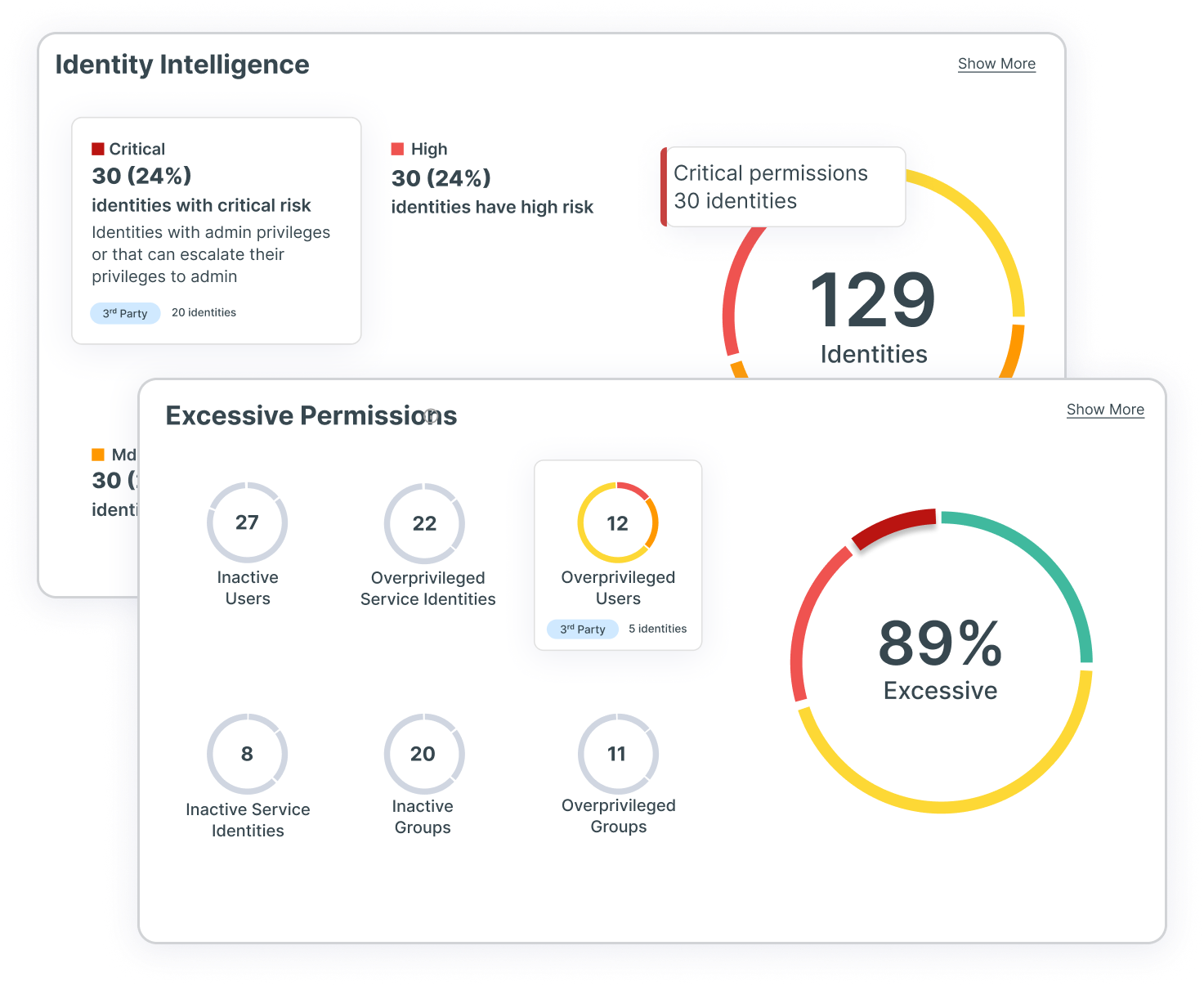
Ottieni approfondimenti basati sulle identità per una valutazione del rischio completa
Con le principali funzionalità CIEM che forniscono una visibilità completa multi-cloud su identità e autorizzazioni, il tuo team di sicurezza può garantire che gli utenti abbiano solo l'accesso giusto alle risorse giuste, al momento giusto e per i motivi giusti. Ottieni vantaggi dall'analisi full-stack che valuta i modelli di autorizzazione del provider cloud attraverso identità, rete, risorse di elaborazione e di dati per far emergere risultati precisi nel contesto. Grazie a Tenable Cloud Security, i tuoi team possono avere una visione completa dei rischi legati alle identità, comprese le autorizzazioni eccessive, l'esposizione alla rete e i pericoli nascosti.
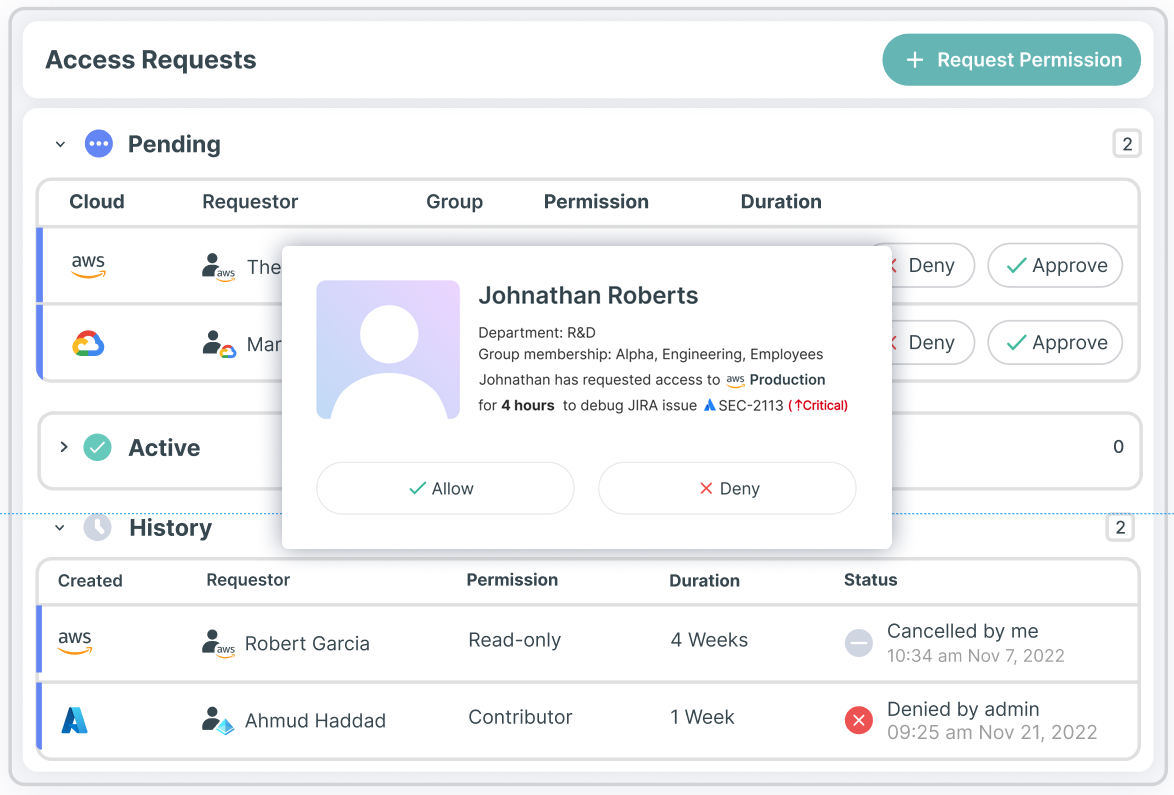
Lavora più velocemente e in totale sicurezza con i flussi di lavoro self-service JIT
Grazie al portale JIT di Tenable Cloud Security è possibile gestire flussi di lavoro self-service e consentire ai team di ingegneri di richiedere e ottenere facilmente l'accesso autorizzato alle risorse necessarie. Migliora la postura di sicurezza multi-cloud con il monitoraggio continuo della conformità. Mantieni un percorso di verifica e indaga sulle attività relative agli accessi, tra cui:
- Chi ha avuto accesso
- A cosa ha avuto accesso
- Quando ha avuto accesso
- Quali azioni ha eseguito
- Chi ha ricevuto autorizzazioni elevate (e quando)
- La giustificazione aziendale
- Chi ha approvato
Sfrutta la sicurezza JIT per l'audit continuo e la governance degli accessi
Utilizzando i report integrati, i team possono comunicare con le parti interessate riguardo alla conformità interna, ai controlli esterni e alle attività di sicurezza giornaliere, che comprendono le attività degli utenti durante le sessioni con privilegi elevati, le richieste passate e il processo di autorizzazione sottostante.
- Dimostra la tua capacità di soddisfare i principali mandati in materia di privacy dei dati, tra cui PCI-DSS, GDPR, HIPAA e molto altro
- Produci report esaustivi per la conformità interna, l'audit esterno e le attività quotidiane di sicurezza
- Riduci i tempi di risposta e di indagine in caso di incidente di sicurezza
Ottieni l'accesso Just-in-Time con Tenable Cloud Security
Scopri di più su Tenable Cloud Security
L'utilizzo dell'automazione [di Tenable Cloud Security] ci ha permesso di eliminare i processi manuali e di eseguire in pochi minuti ciò che avrebbe richiesto mesi di lavoro a due o tre addetti alla sicurezza.
- Tenable Cloud Security