Gestione della postura di sicurezza di Kubernetes per gli ambienti multi-cloud
Protezione full-stack per Kubernetes
La gestione della postura di sicurezza di Kubernetes è impegnativa. La natura dinamica dei cluster Kubernetes, con pod e container che salgono e scendono rapidamente, crea angoli ciechi dal punto di vista della sicurezza. Allo stesso tempo, Kubernetes offre molte opzioni di configurazione e le configurazioni errate possono portare a vulnerabilità di sicurezza. Per evitare queste insidie, è necessario gestire la sicurezza di Kubernetes in modo coerente e automatizzato.
Scopri come
La sicurezza di Kubernetes viene fornita come parte di una piattaforma di protezione delle applicazioni cloud-native (CNAPP) basato sull'identità
Tenable ti aiuta a superare le incertezze legate alla sicurezza di Kubernetes, fornendoti la visibilità necessaria per capire cosa è in esecuzione e cosa è a rischio nei tuoi ambienti Kubernetes. Con Tenable Cloud Security puoi integrare la sicurezza di Kubernetes nelle tue attività complessive di gestione dell'esposizione e ridurre al minimo i rischi associati all'adozione accelerata del cloud.
Ottieni una visibilità unificata per ridurre i rischi in tutti gli ambienti Kubernetes
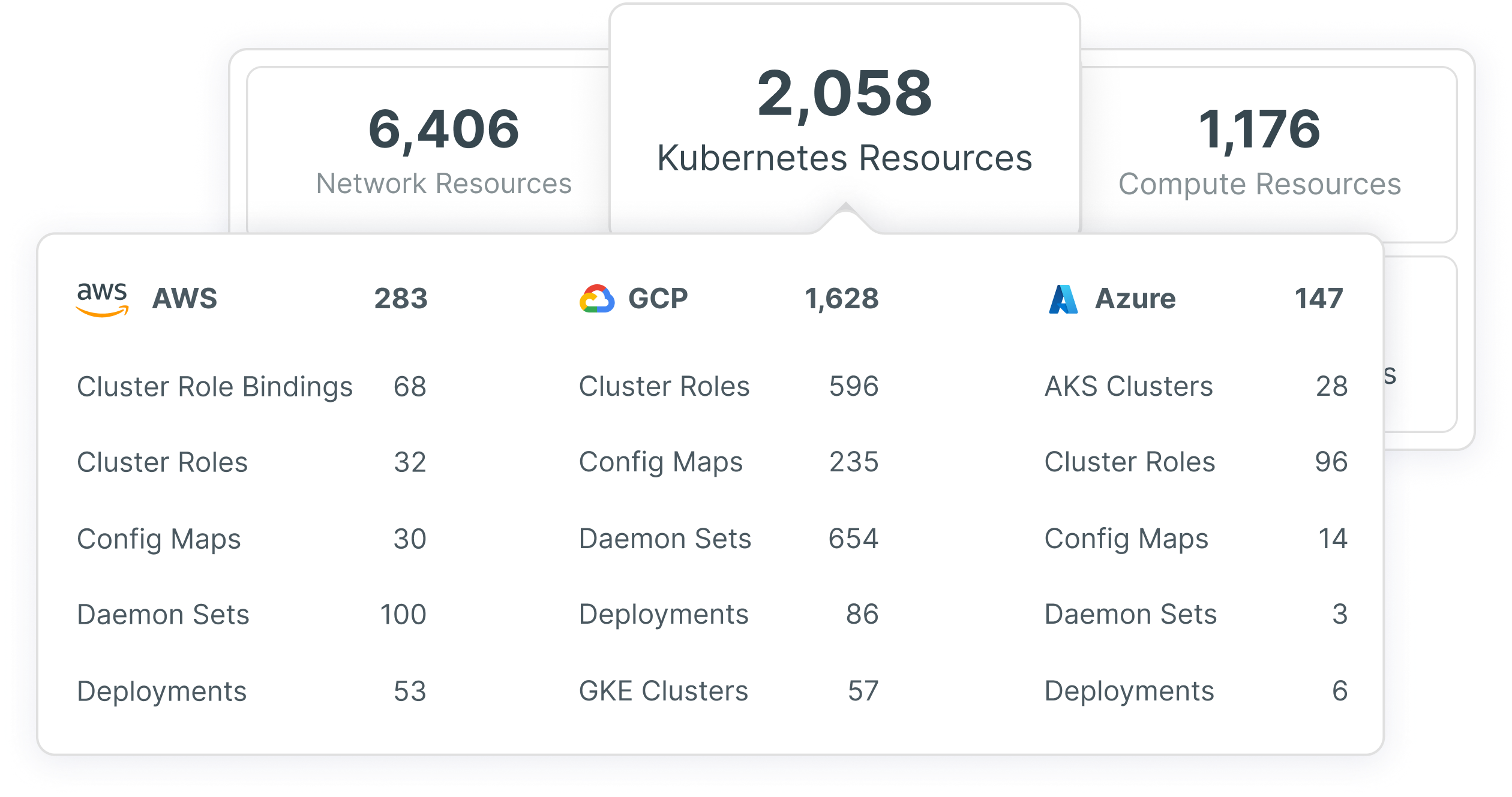
Visibilità full-stack tra i cluster Kubernetes multi-cloud
Con Tenable Cloud Security puoi gestire senza problemi tutte le risorse multi-cloud, compresi i carichi di lavoro, le identità, i dati, la rete e i cluster Kubernetes, tutto da una sola posizione. Tenable scopre e presenta continuamente tutte le risorse in un contesto significativo e multidimensionale, consentendo di indagare facilmente su configurazioni, autorizzazioni e relazioni. Inoltre, è possibile integrare perfettamente i dati dell'inventario Kubernetes interrogando le API del cloud e l'API Kubernetes per ogni cluster, nonché attraverso la scansione continua e senza agenti della configurazione dei nodi Kubernetes e dei container all'interno di ogni nodo.
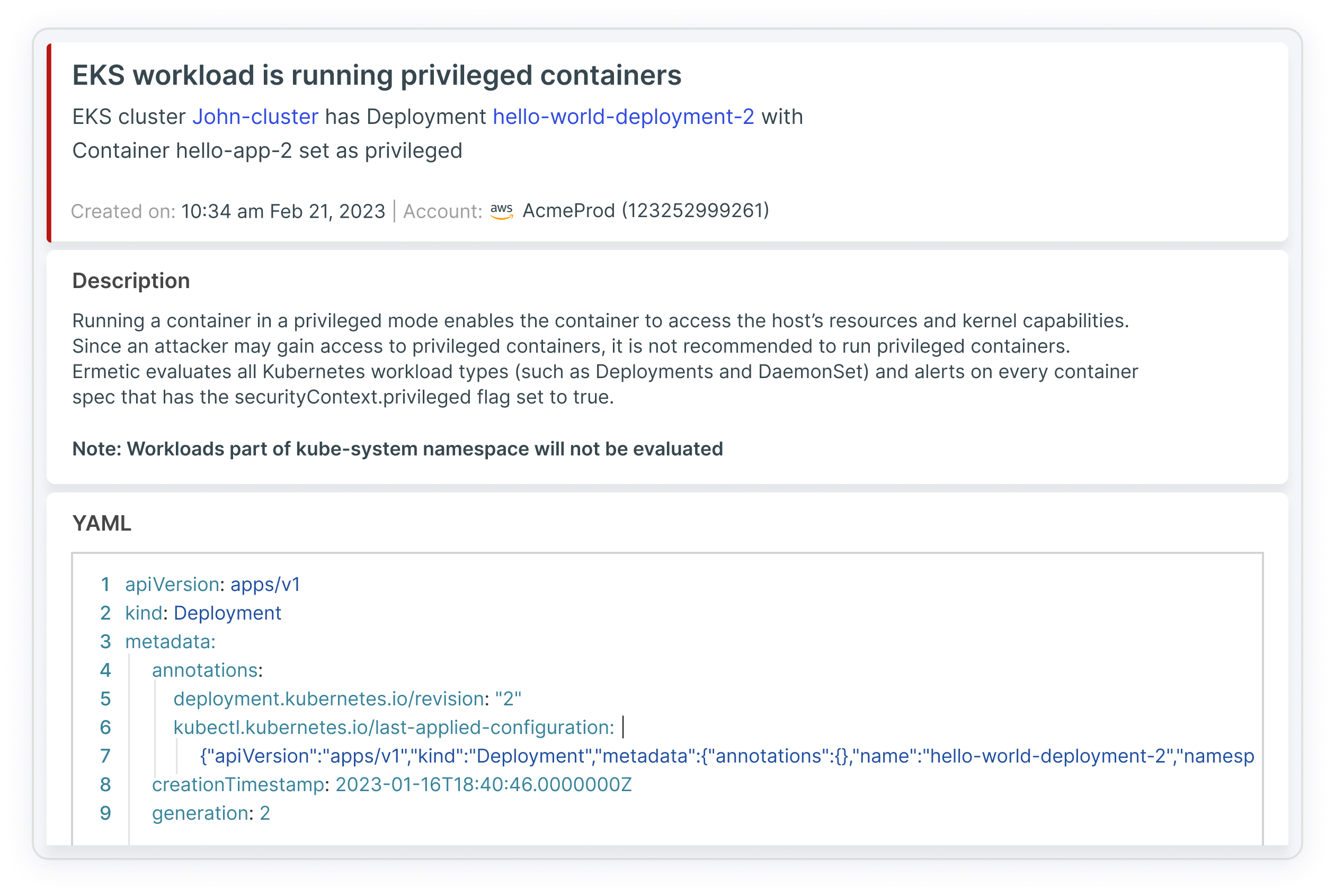
Analisi contestuale dei rischi e reporting automatizzato sulla conformità
Tenable semplifica la sicurezza di Kubernetes consentendo di scansionare i container alla ricerca di vulnerabilità, visualizzare l'esposizione alla rete, i problemi di postura, le errate configurazioni IAM e quelle definite nei manifesti di Kubernetes e altri rischi, il tutto in un'unica soluzione. In tal modo ti aiutiamo a concentrarti su ciò che conta di più, dando priorità alle vulnerabilità che possono esporre le risorse sensibili e avere l'impatto maggiore sui tuoi asset. Inoltre, Tenable automatizza la conformità e la sicurezza rispetto agli standard di settore, tra cui GDPR, NIST, PCI-DSS e CIS per i benchmark Kubernetes. Puoi generare report dettagliati per la conformità interna, gli audit esterni e le attività di sicurezza quotidiane, come l'inventario degli asset e le configurazioni di rete.
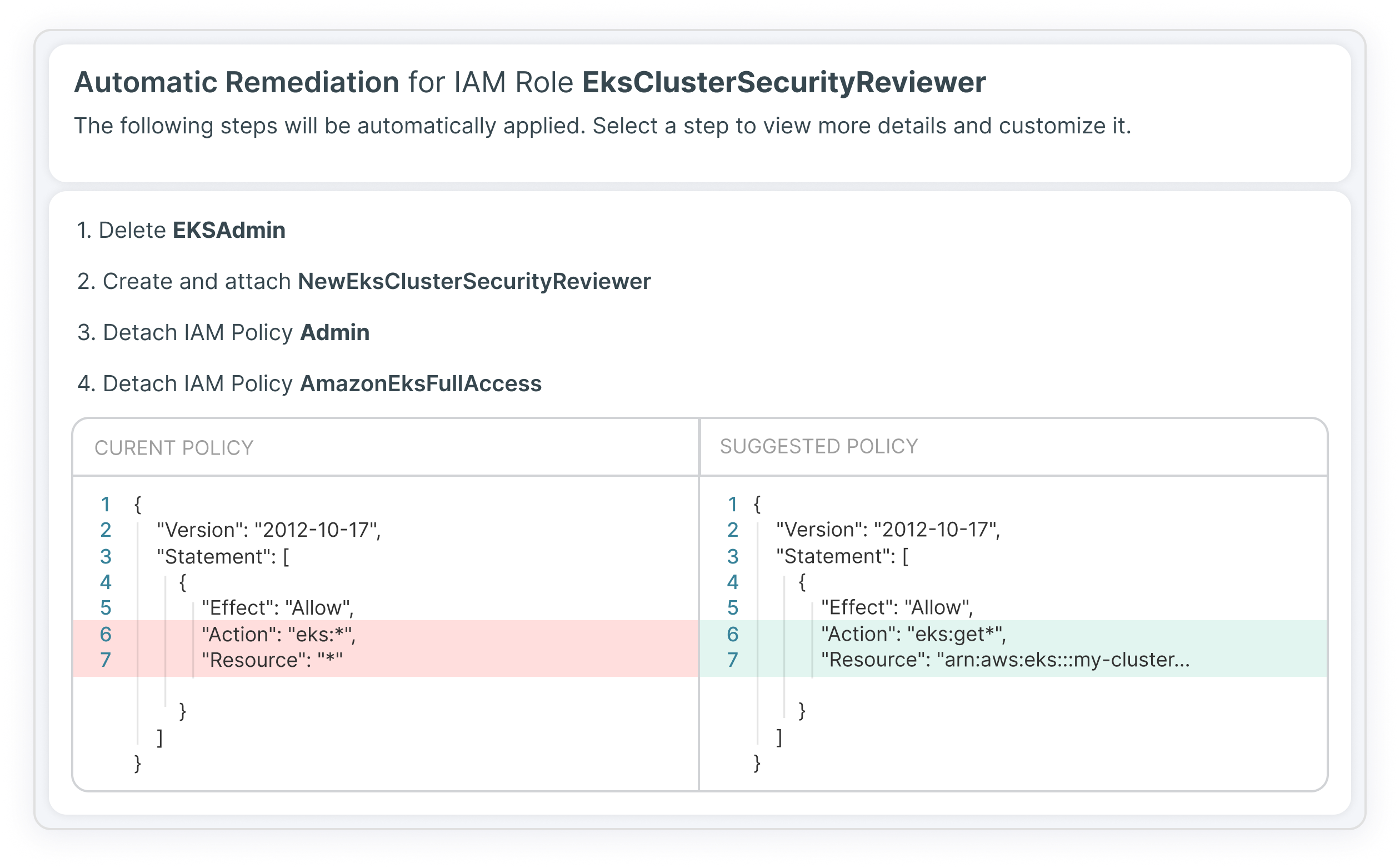
Previeni i rischi con il rilevamento delle anomalie e la correzione automatizzata
Grazie a Tenable Cloud Security, puoi adottare un approccio più preventivo alla sicurezza di Kubernetes, automatizzando il rilevamento delle minacce mediante l'analisi dei registri dei fornitori di servizi cloud e la correlazione con l'architettura sottostante per identificare comportamenti insoliti e sospetti. Consente ai team per la risposta agli incidenti di indagare sui rischi nel contesto e si integra con le soluzioni SIEM e i sistemi di ticketing e notifica per una risposta più rapida. Inoltre, puoi usufruire di correzioni guidate per le configurazioni errate, le violazioni dei criteri e i privilegi a rischio nel tuo ambiente multi-cloud.
"Il più grande vantaggio di lavorare con [Tenable Cloud Security] è la componente di rilevabilità. Riesce davvero a togliere il velo da quello che è un sistema opaco".
MICHAEL BISHOPDir. Architecture and Engineering, BarkBox
Scopri di più su Tenable Cloud Security
L'utilizzo dell'automazione [di Tenable Cloud Security] ci ha permesso di eliminare i processi manuali e di eseguire in pochi minuti ciò che avrebbe richiesto mesi di lavoro a due o tre addetti alla sicurezza.
- Tenable Cloud Security