Tenable e Microsoft
La gestione delle vulnerabilità di Microsoft non è abbastanza adeguata
Nel marzo 2022, Tenable Research aveva scoperto due vulnerabilità (una critica) nella piattaforma Microsoft Azure ed entrambe erano sfruttabili. Microsoft ne aveva sminuito il rischio e l'azienda ci aveva messo 89 giorni a riconoscere privatamente la gravità del problema.
Osserva Tenable all'opera
Vuoi scoprire come Tenable può aiutare il team di sicurezza a individuare ed eliminare le debolezze informatiche principali che mettono a rischio l'azienda?
Compila il modulo per ottenere un preventivo personalizzato o una demo.
Perché i clienti preferiscono Tenable a Microsoft
Confronto tra Tenable e Microsoft
Vulnerabilità e accuratezza della copertura
89.000 CVE, la copertura più ampia del settore
Non pubblicate
Prioritizzazione
Exposure View combina la classificazione della priorità delle vulnerabilità di Tenable con il punteggio di criticità degli asset
Non considera il contesto aziendale importante
Ambito di copertura
Un'ampia varietà di asset: endpoints, dispositivi di rete, tecnologia operativa (OT), carichi di lavoro sul cloud, app web
Limitato agli endpoint con un agente e capacità di livello elementare basata su SNMP
Dashboard e report
Vasta libreria di dashboard e report
Mancanza di dashboard e report
Ecosistema degli strumenti di gestione delle vulnerabilità
Integrazione e supporto degli strumenti e dei flussi di lavoro di correzione di terze parti
Integrazione minima con strumenti di correzione come BigFix
Tecnologie di scansione
Basate su agente o senza agente
Basate su agente con supporto limitato per la scansione della rete
Trust a leader
In primo piano
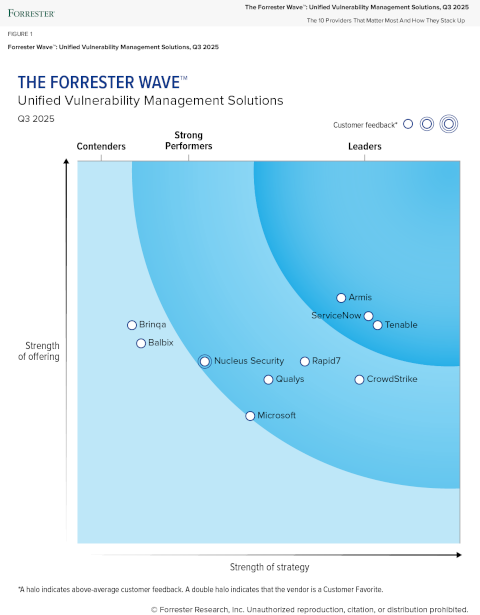
Tenable è stata nominata leader nel report The Forrester Wave™: Unified Vulnerability Management, Q3 2025
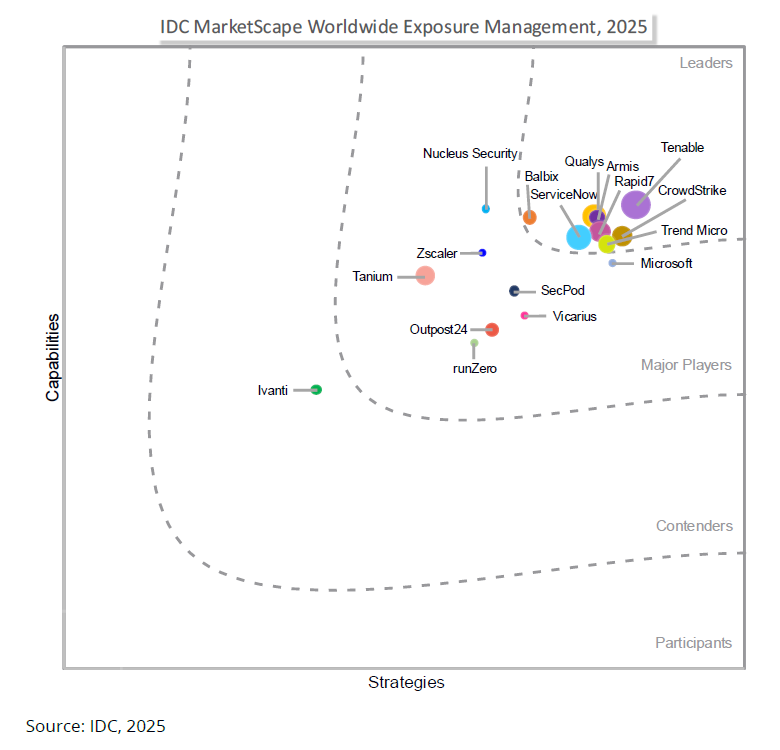
Leggi il reportTenable è stata nominata leader nel report di IDC MarketScape Worldwide Exposure Management 2025 Vendor Assessment
"Organizations should consider Tenable One when seeking a unified exposure management platform that delivers broad asset coverage across IT, cloud, OT/IoT, identity, and application environments."
Leggi il reportOsserva Tenable all'opera
Vuoi scoprire come Tenable può aiutare il team di sicurezza a individuare ed eliminare le debolezze informatiche principali che mettono a rischio l'azienda?
Compila il modulo per ottenere un preventivo personalizzato o una demo.