Code-to-Cloud Visibility: Why Fragmented Security Can’t Scale

Widespread visibility is critical for cloud security, but obtaining it is easier said than done. To discover insights and best practices for code-to-cloud visibility, check out highlights from a new IDC white paper. Plus, learn how Tenable’s CNAPP and exposure management platform give you an unimpeded view of your multi-cloud and hybrid environment.
The modern cloud-native stack is fluid, ephemeral and multi-layered. Containers spin up and vanish in seconds. Third-party APIs integrate with your most critical systems. Infrastructure-as-code templates get pushed by developers who don’t own runtime security.
Yet many cloud-native application protection platform (CNAPP) vendors still treat development, infrastructure and runtime as separate silos. This fragmentation creates risky blind spots that attackers are experts at exploiting.
Attaining code-to-cloud visibility is a must. Without unifying visibility from development through production, you’re left with misaligned priorities, wasted effort and threats that slip through the cracks.
In a new white paper commissioned by Tenable, “Bridging Cloud Security and Exposure Management for Unified Risk Reduction,” IDC states the risk plainly: “Fragmented visibility hampers tracking exposures, misconfigurations, and ownership across multicloud, multi-team environments.”
In fact, the visibility problem is so pervasive and disruptive that a 2023 IDC survey found that improving visibility topped respondents’ IT security operations (SecOps) priorities.
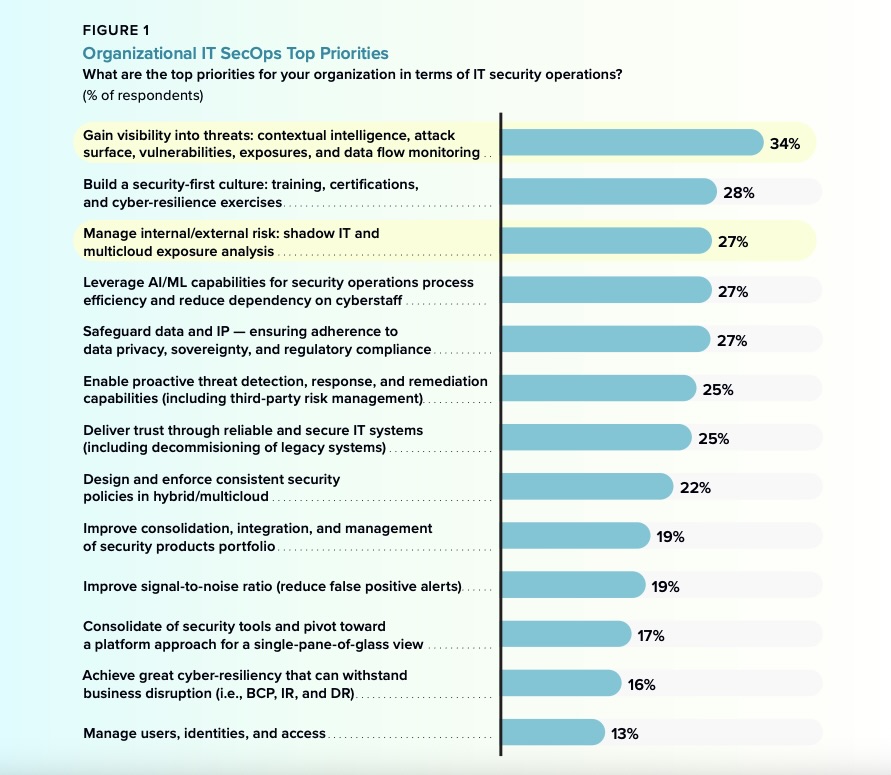
(n = 1,000; Source: IDC’s AP IT Business Services Sourcing Survey, 2023 Notes: This is an IDC Syndicated Survey. Respondents were professionals who are enterprise buyers.)
When your security is siloed, you can't answer basic questions:
- Which vulnerabilities pose the biggest actual risk to our business?
- Who owns this misconfigured asset?
- How can we fix this flaw in development before it ever reaches production?
From blind spots to bullseyes: The power of a unified CNAPP
In the white paper, IDC makes an assessment of Tenable Cloud Security, saying it is a unified CNAPP designed to protect the full cloud stack and to offer “holistic identity, visibility and risk management.”
As IDC notes, this unified approach is “critical to managing growing security complexity, while also streamlining workflows between IT and cloud security stakeholders.”
IDC goes on to say that through its integration with the Tenable One Exposure Management Platform, Tenable Cloud Security removes blind spots across multi-cloud and hybrid environments.
“This integration enables stakeholders to understand and mitigate cloud risks within the context of their broader IT and cloud landscape. Unified risk visualization allows teams to make informed decisions and prioritize security actions more effectively,” the IDC white paper reads.
Moreover, IDC observes that Tenable’s cloud security approach is effective in addressing both tool sprawl and code-to-cloud visibility.
“Tool sprawl is a major organizational challenge. Tenable helps consolidate cloud security functions into a unified platform, enhancing risk management and operational efficiency,” the IDC white paper reads.
Meanwhile, IDC notes that Tenable addresses fragmented visibility “with real-time discovery across workloads, identities, and data.”
“With Tenable One, this is enhanced by asset context and ownership metadata to support risk prioritization,” IDC adds.
Why we view our CNAPP-exposure management integration as a game changer
Tenable Cloud Security delivers on the promise of end-to-end cloud-native protection by tightly integrating:
- An ecosystem view of cloud security risk
- Complete cloud risk visibility and SDLC security
- Runtime workload protection
- Data security posture management (DSPM)
- AI security posture management (AI-SPM)
With Tenable’s integration of CNAPP and exposure management, these capabilities extend into on-prem vulnerability management scanning, identity management and business-level exposure scoring — bridging security across all domains.
Tenable’s platform unifies telemetry from these diverse layers into a single source of truth. Developers can remediate issues in IaC or container images before deployment. Operations teams can monitor for runtime threats in Kubernetes clusters. And CISOs can report on business risk with confidence.
It’s about connecting the dots
Tenable’s CNAPP isn’t just about breadth — it’s about correlation. Vulnerabilities in container images are linked to IaC sources. Sensitive data is correlated with permissions and runtime access. Exploitable paths are modeled in real time.
This architectural clarity is key to scaling secure development and operations without slowing down innovation. No more waiting for quarterly pen tests or manual ticket handoffs. Security becomes continuous — and actionable.
Your cloud security strategy should mirror your cloud application architecture: integrated, scalable and context-rich. Unified CNAPPs like Tenable’s are built to evolve with you — not bottleneck you with complexity.
To dive deeper into the best practices for achieving code-to-cloud visibility and to find out how Tenable Cloud Security can help you, download the IDC white paper “Bridging Cloud Security and Exposure Management for Unified Risk Reduction” today.
- Cloud
- Container security
- DevOps
- Exposure Management


