by Cody Dumont
October 20, 2025
The Payment Card Industry Security Standards Council (PCI SSC) maintains, evolves, and promotes Payment Card Industry standards for the safety of cardholder data across the globe. The PCI SSC provides technical and operational requirements for organizations accepting or processing payment transactions. The guidance also applies to software developers and manufacturers of applications and devices used in those transactions.
The Payment Card Industry Data Security Standard (PCI DSS) helps entities understand and implement standards for security policies, technologies and ongoing processes that protect their payment systems from breaches and theft of cardholder data. The standards have historically been revised on a 2-3 year cycle, but the PCI SSC is transitioning to a posture of revising the PCI DSS as required based on changes to the current threat landscape. The current standard revision is PCI DSS Version 4.x. Any organization that handles payment card information must comply with the PCI DSS and must demonstrate compliance annually. Tenable Vulnerability Management is able to help organizations monitor ongoing PCI DSS compliance.
As part of the PCI DSS version 4.x the requirement for authenticated internal vulnerability scanning was introduced. Tenable has always emphasized that credentialed scanning is required to get the most accurate information, now the PCI Council requires credentialed scanning where possible. The Council recognizes that all systems may not be accessible as part of a credentialed vulnerability scan, but those systems must be clearly documented. As part of the vulnerability scanning, Tenable uses two methods to perform elevated vulnerability scans, Nessus and Nessus Agents. Nessus vulnerability scans access the system over a network protocol such as SMB, SSH, and etc, while the Nessus Agents run a local version of the Nessus scan engine as a system level service. (Note: When using Nessus Agent, uncredentialed port scans are still required to identify open ports) There are benefits to each method, however each provides the ability to enumerate vulnerabilities based on the operating system, system configurations, and installed software.
As part of the requirement 11.3.1.2 (Internal vulnerability scans are performed via authenticated scanning), the internal systems located within the Cardholder Data Environment (CDE) are to be documented as accessible with and without credentials. Using Nessus to scan devices on the network will provide the necessary information as to the accessibility of a system using the defined protocols and supplied credentials. Nessus will report on the success of authentication and the status of collecting vulnerabilities. Once authenticated, Nessus will enumerate vulnerabilities found on the system. The vulnerabilities detected are identified using industry-recognized vulnerability databases and our research teams. Tenable provides Vulnerability Intelligence attributes that assist in identifying vulnerabilities used in ransomware attacks and other emerging threat categories.
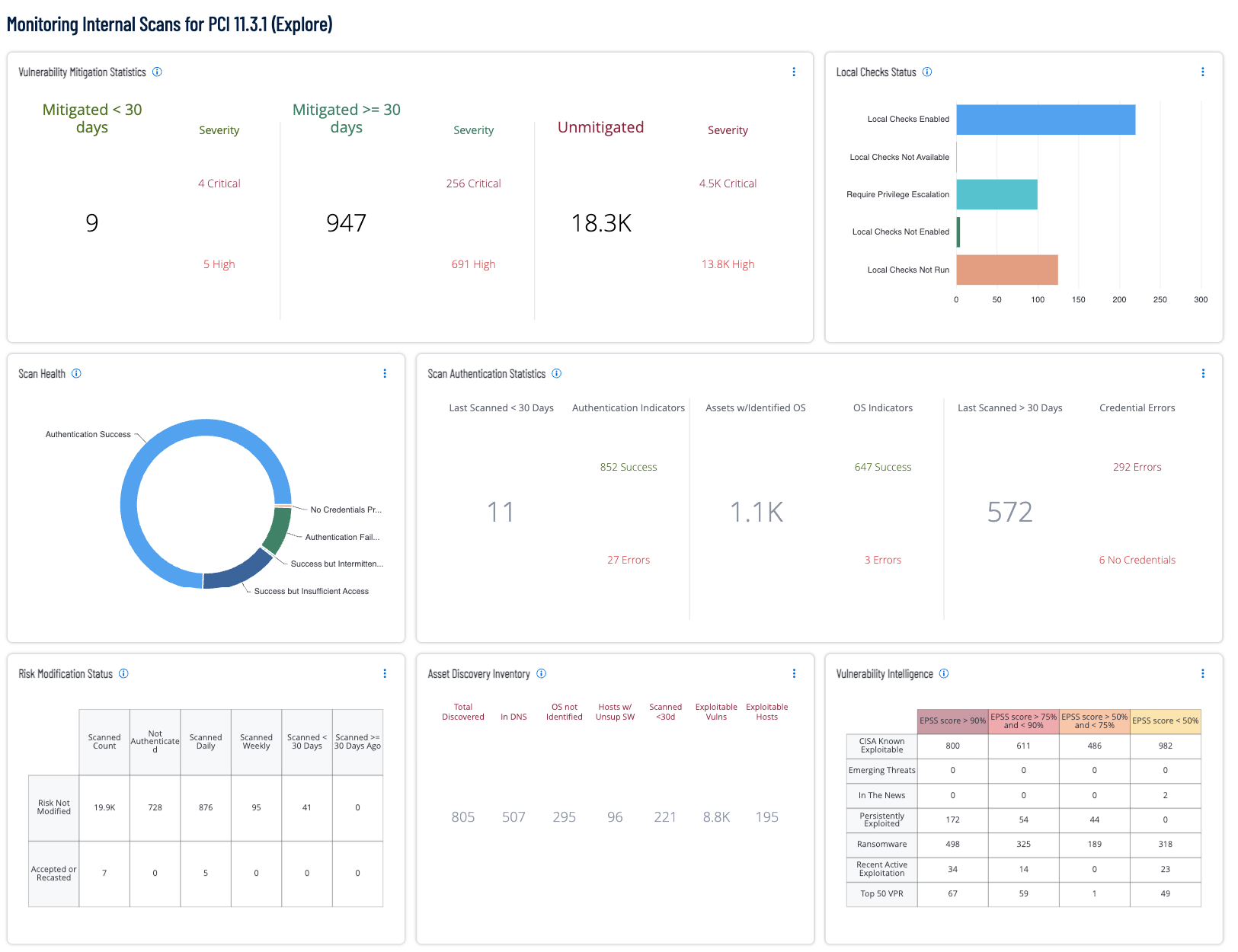
As directed in the 11.3.1 (Internal vulnerability scans are performed), the organization must conduct internal scans every three months and perform rescans to confirm all high and critical vulnerabilities are resolved. Tenable Vulnerability Management supports the scheduling of scans, allowing the assessment teams to continuously monitor the CDE accordingly. The dashboard consists of widgets that provide an overview of how internal scanning is being performed. These information based queries provide authentication, scan health, and diagnostic information to assist risk managers with ability to drill down into the appropriate data and better understand the problems that need to be addressed to mitigate risks or solve scan heath related issues. While the vulnerability based queries are filtered for high and critical severity vulnerabilities, along with other attributes such mitigation status, risk categories, and risk accepted; allowing assessors to focus on vulnerabilities of particular concerns identified during the scans. Identified vulnerabilities are tracked by time, severity, and host in order to provide multiple perspectives into the vulnerability status of the organization.
Widgets
- Vulnerability Mitigation Statistics: As directed in the 11.3.1, organizations are to rescan assets that have been identified with high risk and critical vulnerabilities. The frequent vulnerability scanning is a proactive approach to maintaining security in dynamic IT environments. Frequent scanning helps identify and address weakness in systems, applications, and networks before they can be exploited. This widget provides a summary count of mitigated risk and current risk found on systems included in the scope of the report and is divided into 3 sections: The first two sections separate mitigated risks into less than 30 days and greater than 30 days, showing how much progress has occurred on the selected assets. The last section displays the current vulnerabilities that are still in need of mitigation.
- Local Checks Status: The Local Checks Status widget provides summaries of local checks status. These local check plugins provide a list of the issues Nessus detects when running a scan. The errors are logged along with the reporting plugin and protocol, if available. The plugins also provide summaries of particular types of authentication local check problems that have been reported by other plugins and report the plugins that encountered these issues.
- Scan Health: This widget provides a summary of scan health in relation to authentication success and failures. System and network devices must be routinely scanned to ensure they are operating in compliance with organizational and regulatory requirements for vulnerability and configuration management. Evidence of scanning activities is often required by regulatory frameworks and Service Level Agreements (SLAs). Credentialed scanning, which requires authentication to the device, provides the most accurate scanning results.
- Scan Authentication Statistics: This widget provides a summary of scan health in relation to authentication success and failures. System and network devices must be routinely scanned to ensure they are operating in compliance with organizational and regulatory requirements for vulnerability and configuration management. Evidence of scanning activities is often required by regulatory frameworks and Service Level Agreements (SLAs). Credentialed scanning, which requires authentication to the device, provides the most accurate scanning results.
- Risk Modification Status: Tenable provides the ability to recast (or change) the severity value of a finding, and accept risk. Often the PCI Assessors are required to identify any vulnerabilities or findings that have been modified. This widget organizes data by two rows, Risk Not Modified and Accepted or Recasted vulnerabilities. The modified risk is any risk that has been accepted and/or recasted. The columns are then broken down into scan and authentication boundaries. The data displayed in this manner allows the accessor to quickly determine if risk modification is a predominant practice, or if the accepted risks are in the minority and may be at acceptable levels.
- Asset Discovery Inventory: This statistics widget displays information related to Asset Discovery and Inventory. Displayed are the total number of assets discovered in the first column. The remaining columns contain supplemental information on those assets such as the number of those assets which are in DNS, the number where the OS is has not been identified, the number of assets which contain unsupported software, the number which have been scanned in the last 30 days, the total number of exploitable vulnerabilities on the assets, and the number of assets which are considered exploitable.
- Vulnerability Intelligence: This widget correlates the Vulnerability Categories with EPSS Score. EPSS Score is a number representing the percentage of likelihood that a vulnerability will be exploited. The number ranges from 1 to 100 with up to three decimal places. Each column creates a range of EPSS scores, into severity based ranges. However note any finding with a Vulnerability Intelligence category assigned is already in the top 3 percent of exposure and requires immediate attention.