by Steve Tilson
November 3, 2017
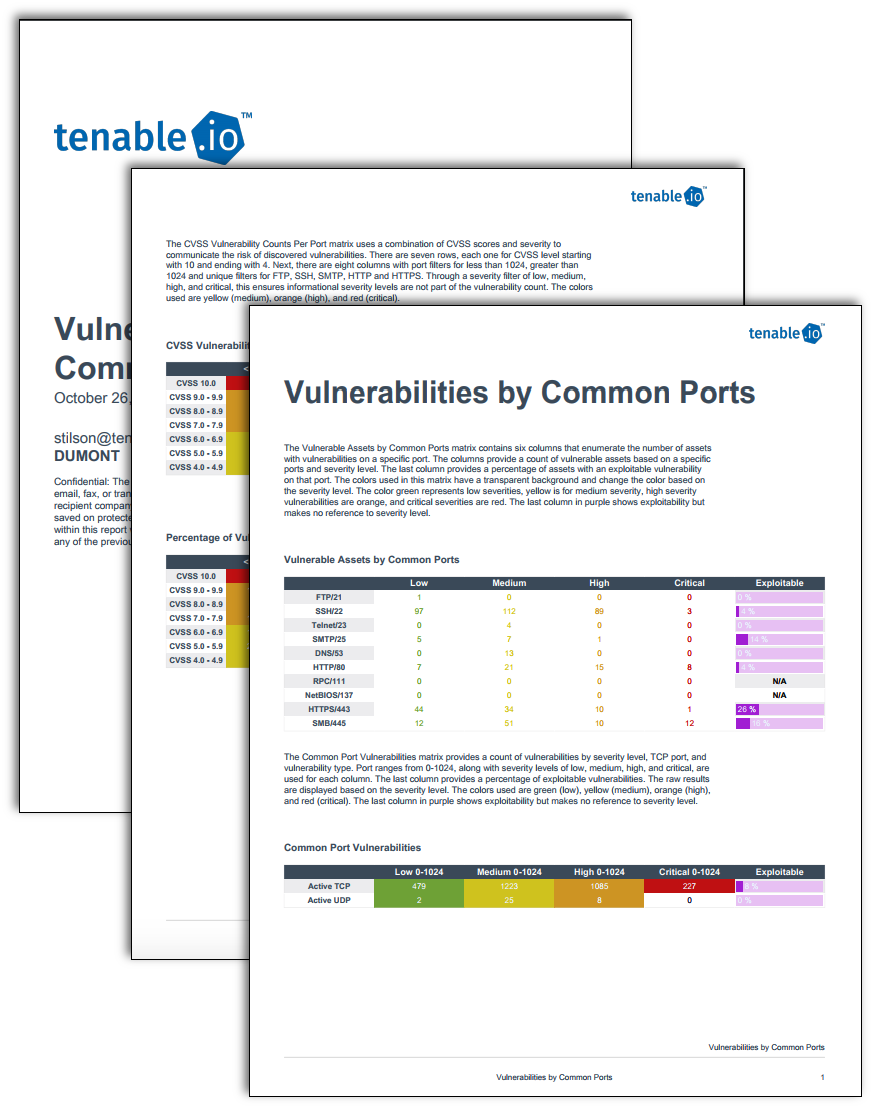
Many systems and software, by default, leave common ports open and can be easy targets for attackers due to the vulnerabilities associated with those ports. Many common services such as DNS, HTTP, SMB and SMTP are tied to common ports. This report leverages a variety of active and passive port filters to display vulnerability information for common ports. As hosts are discovered, Tenable.io enumerates vulnerabilities and their associated TCP/UDP ports. Tenable.io is able to ascertain the server-side transmissions as well as the client-side. Transmissions are detected using passive scanning or active scanning to identify services utilizing those ports. By combining active and passive port scanning, analysts can have a clear view of the port usage across the network.
Some services discovered by Tenable.io may be the result of misconfigurations or rogue software/hardware assets. Some services discovered are just default services still running from the initial set up. One of the critical task for SOC analysts and administrators is to verify the identified open ports on systems and determine if they were misconfigured when installed or updated. Left unresolved, these common ports expand the attack surface, assuring higher cyber risk. This report from Tenable.io presents port status information to risk managers to assist with the prioritization of risk mitigations through the patch management process or other mitigation techniques.
Once the ports are discovered and assessed, following the Cyber Exposure lifecycle, analyzing information provided by this report further assists the CISO in monitoring the business's need for compliancy for services rendered under the common ports utilized. This report can be influential to firewall changes that may be required for further securing from or for these common ports found in the environment.
Cyber Exposure provides a discipline and a process for managing and measuring cyber risk against the modern attack surface. This discipline helps SOC and IT teams collaborate more effectively to identify and resolve common open port issues. Furthermore, Cyber Exposure transforms security monitoring from a static or fragmented view to live and continuous visibility across every asset on every platform. That visibility brings better risk management providing a higher level of security. Tenable.io, the first Cyber Exposure technology, will provide the data, visualization, process management and metrics needed to drive a new way to manage security to reduce cyber risk.
This report contains the following elements:
Vulnerable Assets by Common Ports: This matrix provides a list of common ports such as 21, 22, 23, 25, 53, 80, 111, 137, 443, and 445. For each port, the total number of hosts that have low, medium, high and critical vulnerabilities are given, along with the exploitability percentage.
Common Port Vulnerabilities: This matrix provides a count of hosts found with active TCP and UDP ports. Each count is broken down by vulnerability severity of low, medium, high and critical. The percentage of exploitable vulnerabilities is also given.
CVSS Vulnerability Counts Per Port: This matrix provides a breakdown of vulnerabilities on each common port according to the CVSS scores assigned.
Percentage of Vulnerabilities Based on CVSS and Port: This matrix provides the percentage of vulnerabilities based on a specific common port and the CVSS scores applied to the vulnerabilities.