Applica il privelegio minimo nel cloud. Ridimensiona le autorizzazione su larga scala.
Riduci i privilegi permanenti eccessivi, complici silenziosi della perdita di dati e del movimento laterale, e consenti l'applicazione continua dei privilegi minimi con Tenable Cloud Security. Analizza gli schemi di accesso, segnala i ruoli con privilegi eccessivi e automatizza l'accesso Just-in-Time senza rallentare la velocità di sviluppo.
Far sì che la sicurezza segua il ciclo di vita delle identità
Passare dall'accesso persistente alle autorizzazioni Just-in-Time.
Gestisci la governance delle identità con Tenable Cloud Security
Riduci le autorizzazioni eccessive del cloud, principali responsabili delle violazioni e degli errori nei controlli. Riduci il raggio d'azione delle identità, con la visibilità, l'automazione e l'applicazione di policy che si allinei alle best practice dei privilegi minimi.
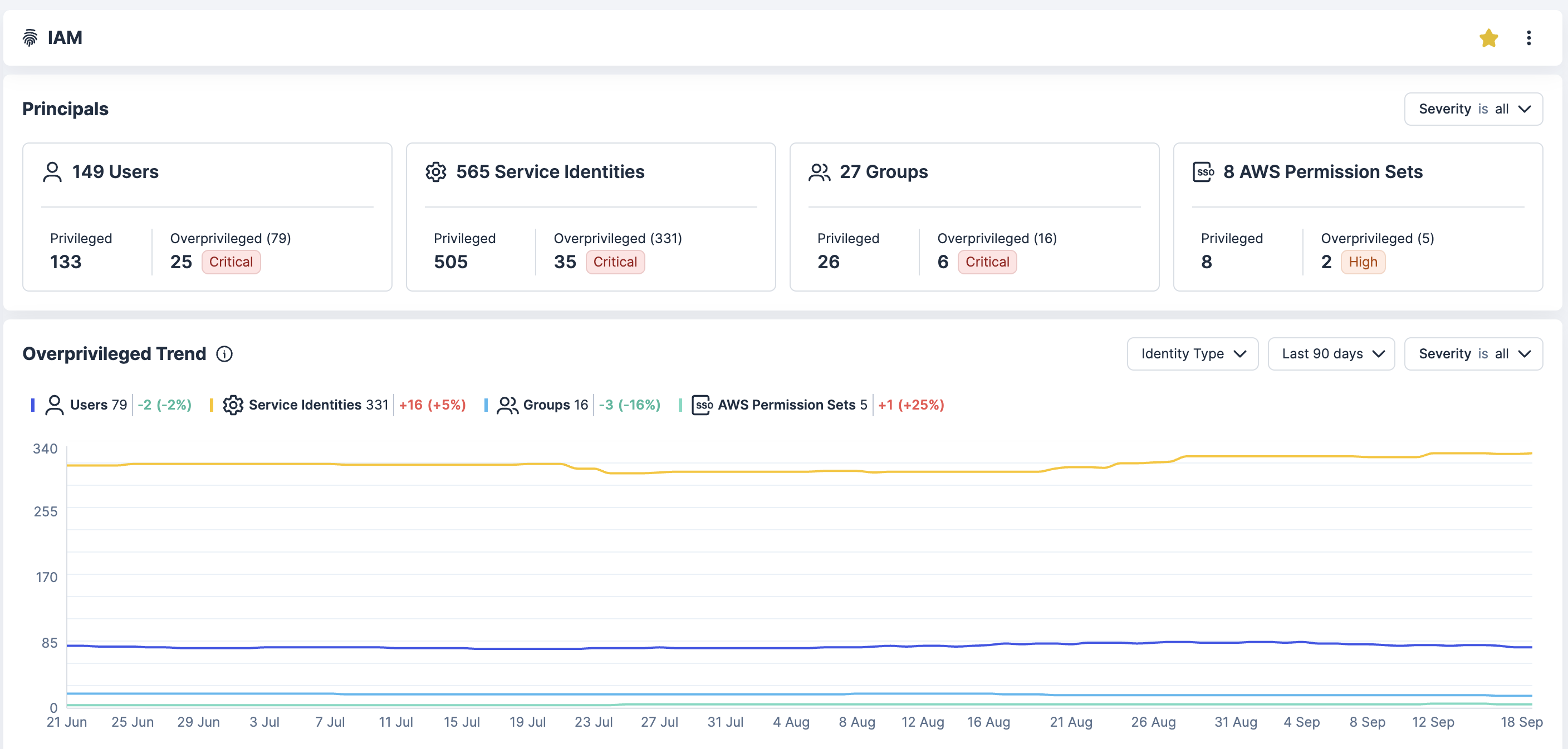
Scopri le identità e i diritti
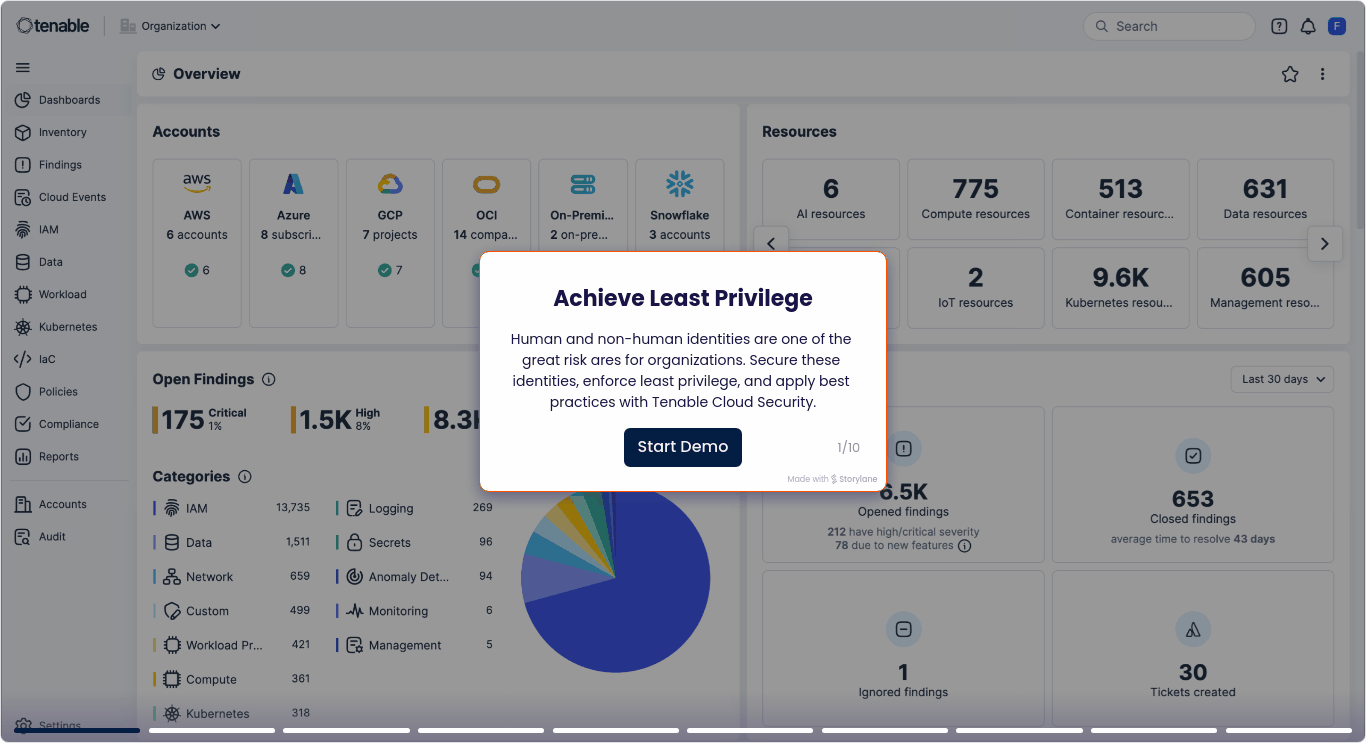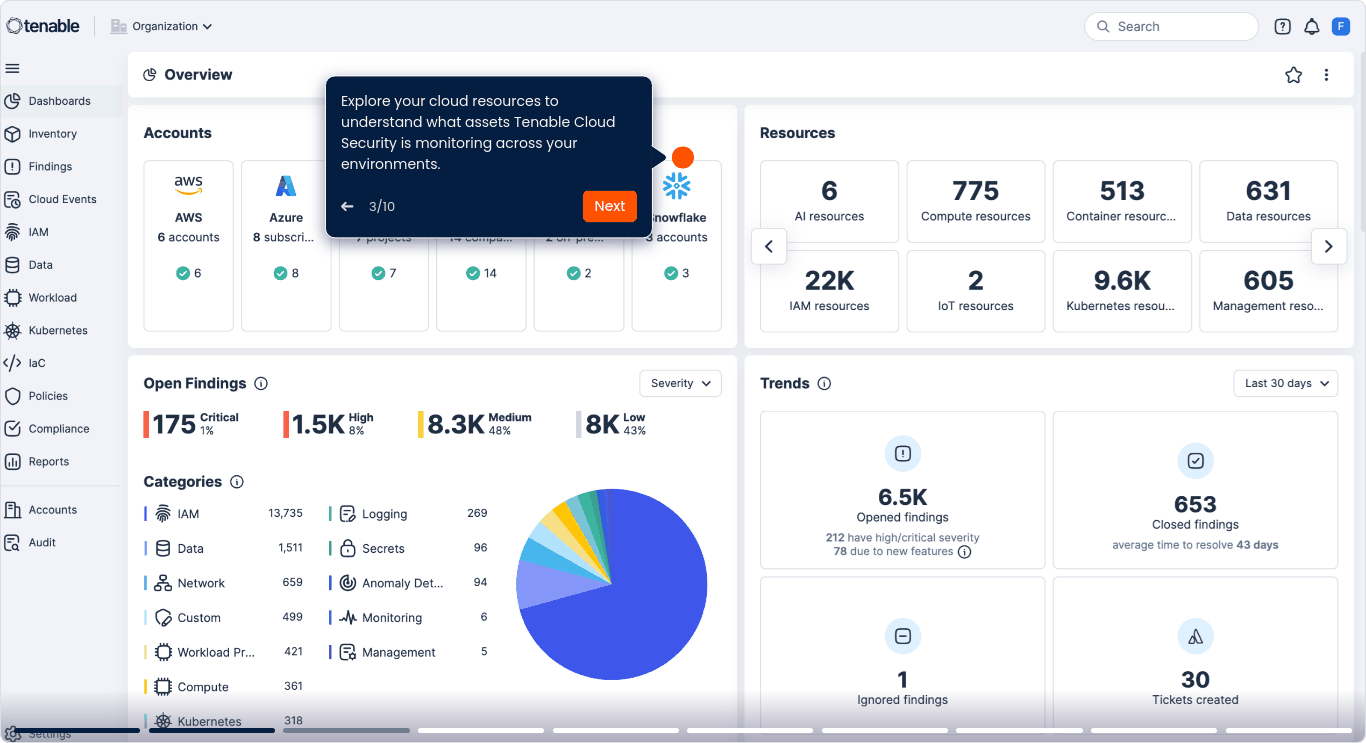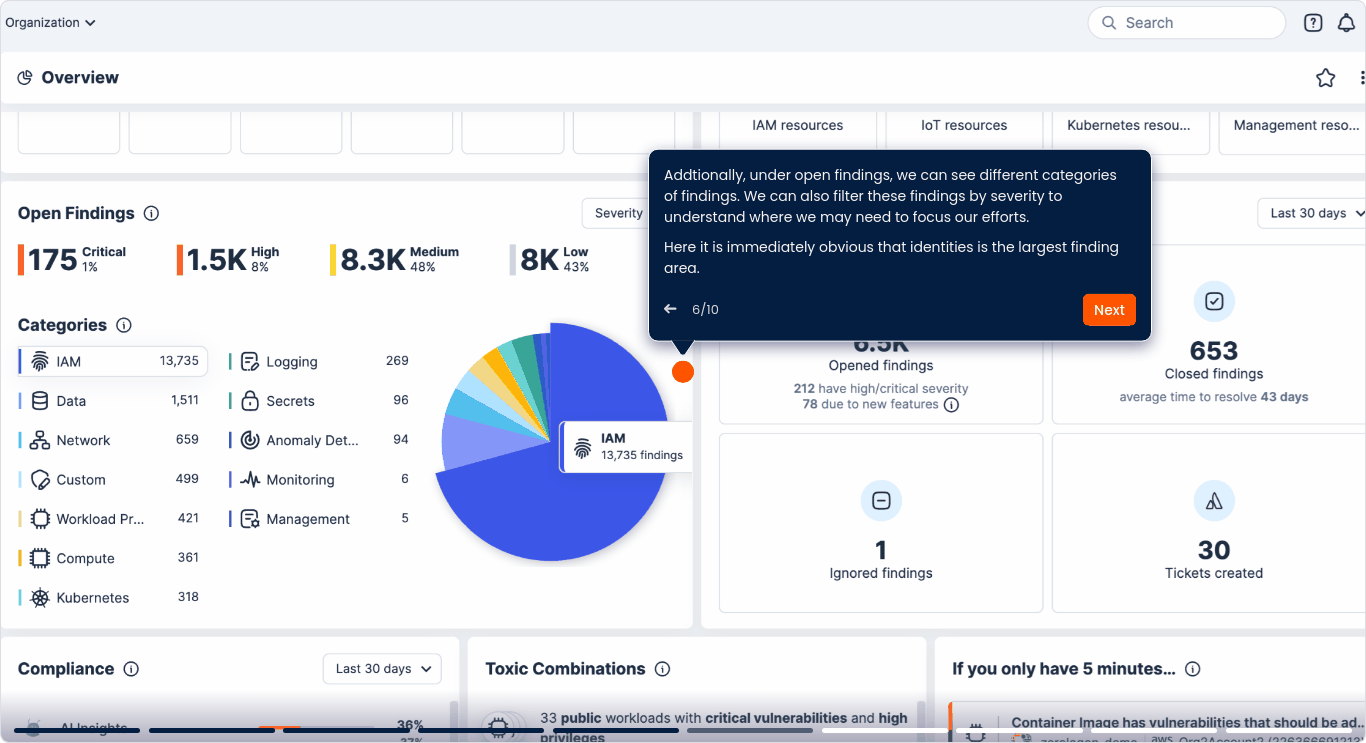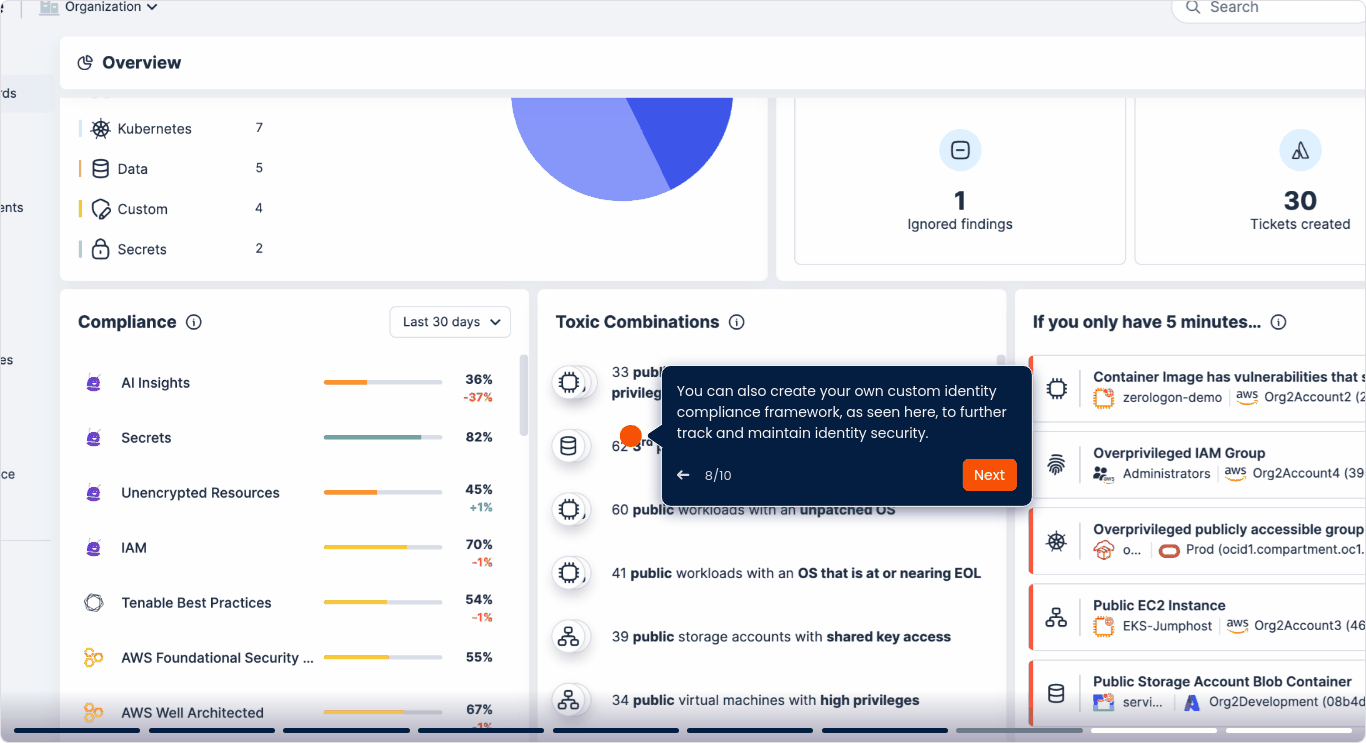
Acquisisci piena visibilità di tutte le identità in AWS, Azure, GCP e Kubernetes, tra cui gli utenti umani, gli account di servizio e le integrazioni di terze parti. Individua gli account orfani, i ruoli inutilizzati e i diritti eccessivi
Analizza il rischio dei privilegi
Analizza le policy, le appartenenze ai gruppi e i presupposti dei ruoli per scoprire i rischi di escalation dei privilegi e le opportunità di movimento laterale. Questo contesto permette ai team di eliminare i percorsi ad alto rischio.
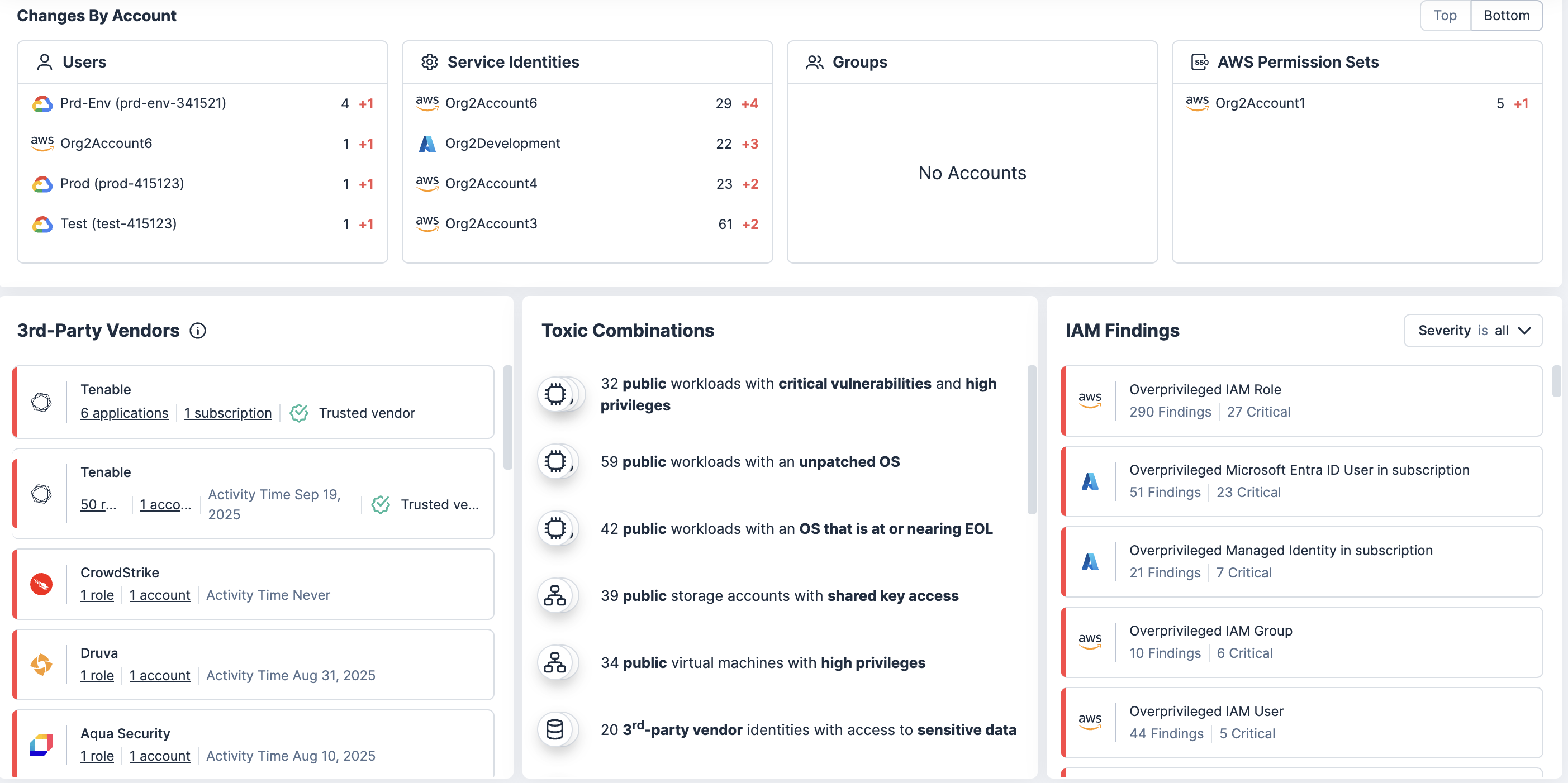
Ottieni correlazione contestuale e prioritizzazione
Metti in correlazione le autorizzazioni eccessive con le vulnerabilità, le configurazioni errate e i dati sensibili, per scoprire dove l'uso improprio dei privilegi può produrre un maggiore impatto.
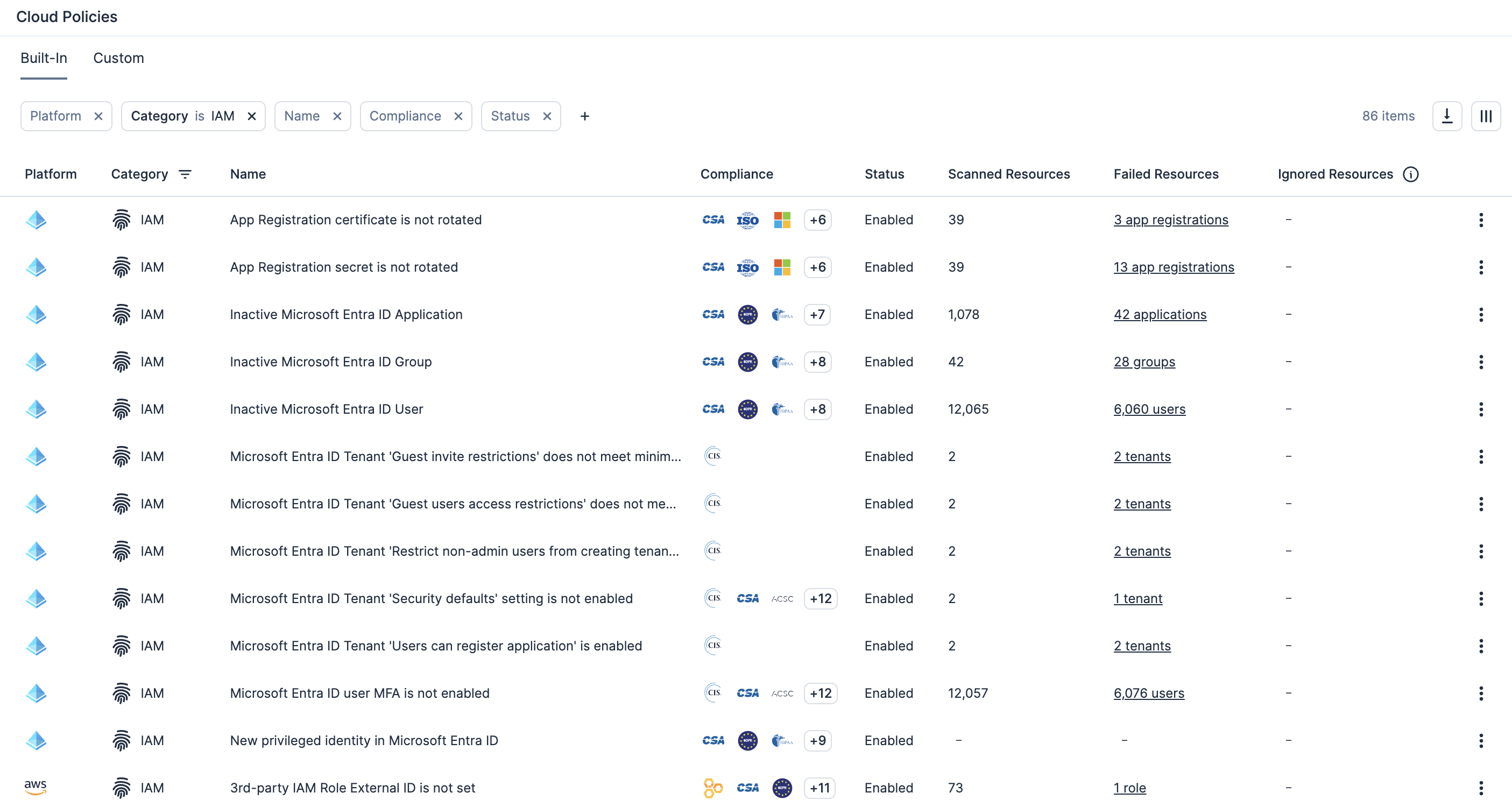
Applica le policy personalizzate e la correzione automatica
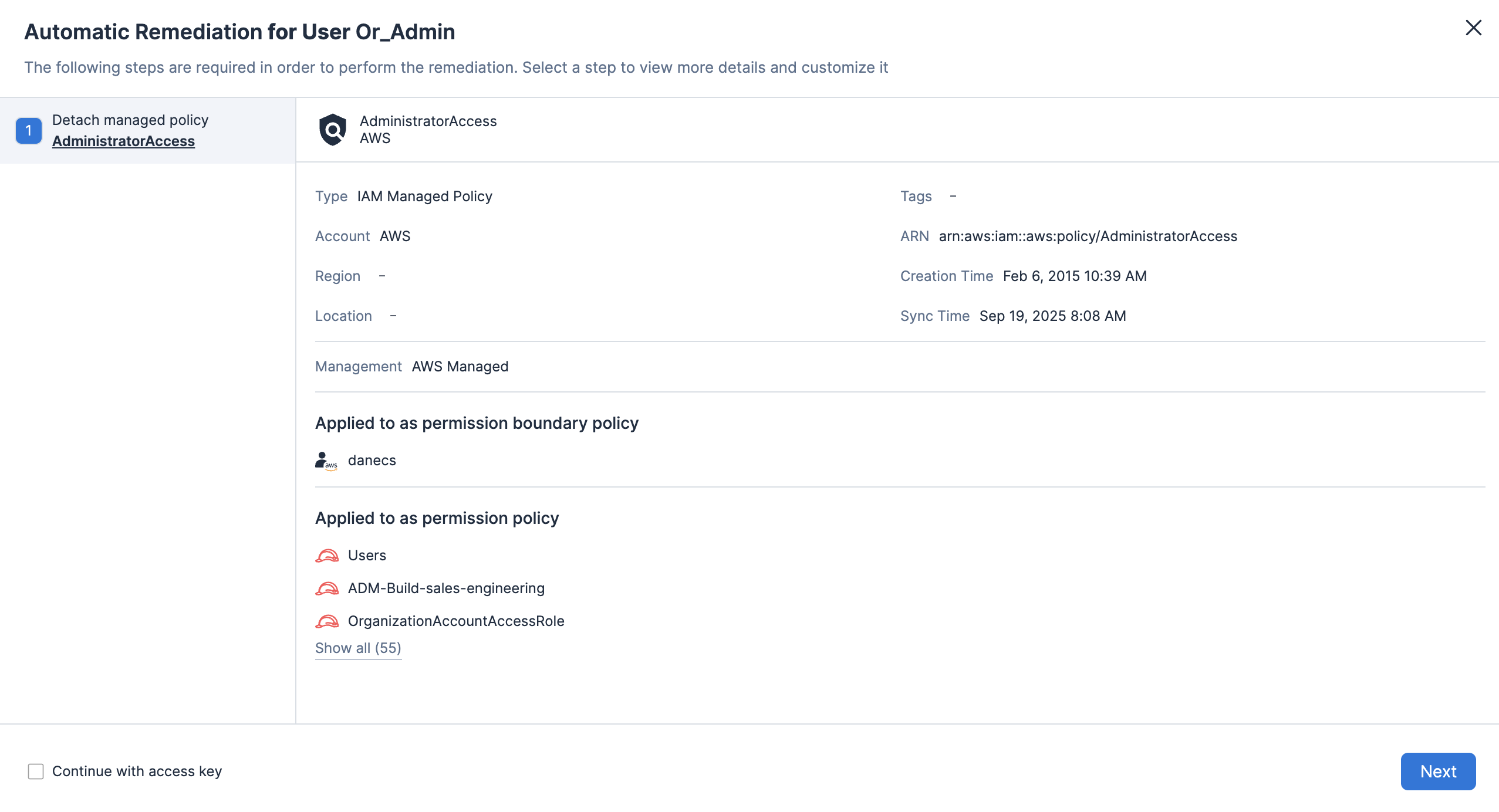
Abilita la definizione della policy personalizzata per rilevare le autorizzazioni eccessive o le configurazioni pericolose sulle risorse, poi abilita i flussi di lavoro di correzione.
Integra CIEM a Tenable One
Applica continuamente i privilegi minimimi con la gestione dell'infrastruttura cloud e dei diritti (CIEM, Cloud Infrastructure Entitlement Management) per assicurare che le autorizzazioni siano limitate al minimo indispensabile, solo per il tempo necessario e mai eccessive.
Scopri di più su Tenable Cloud Security
L'utilizzo dell'automazione [di Tenable Cloud Security] ci ha permesso di eliminare i processi manuali e di eseguire in pochi minuti ciò che avrebbe richiesto mesi di lavoro a due o tre addetti alla sicurezza.
- Tenable Cloud Security