The Breach You Didn’t See Coming: How Invisible Combinations of Risk Are Exposing Your Organization

Most breaches don’t happen because of one glaring issue. They happen when multiple, seemingly low-risk factors silently combine. Learn how invisible risk combinations evade siloed security tools and how an exposure management program gives defenders the context they need to stop attacks before they start.
We often hear that cybersecurity is a game of cat and mouse. But the reality is far more alarming: attackers are playing a different game entirely, and they’re winning. Not because their methods are better, but because their perspective is.
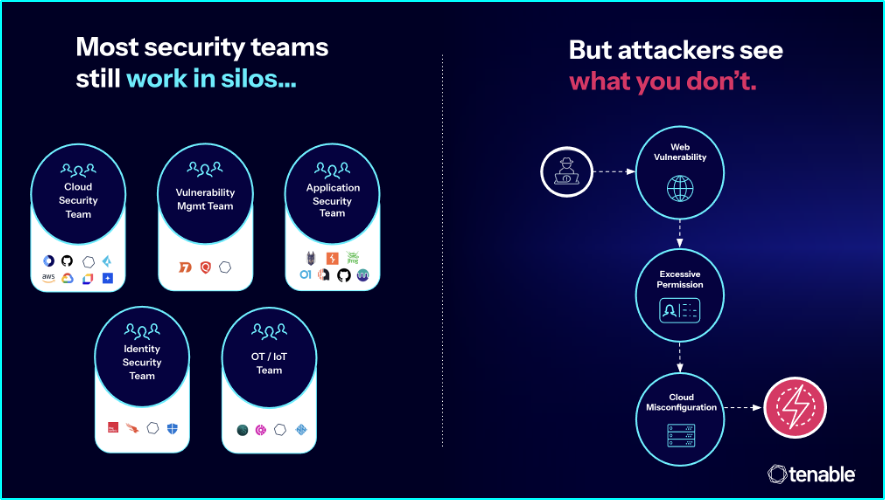
While most security teams still operate in silos, attackers view your environment as one interconnected system. They don’t see isolated issues. They see opportunities in the invisible risk combinations hidden across your environment.
The reality of siloed security
Let’s face it, most security organizations are structured around specific domains — vulnerability management, cloud security, application security, identity and access management (IAM), operational technology (OT) security and more. Each domain has its own tools, its own data and its own separate workflows. And while specialization is important, this siloed approach creates major blind spots when it comes to understanding real risk exposure.
Even with countless security tools scanning every corner of your environment and generating endless findings, your teams are likely still missing the bigger picture. When you assess risk in isolation, without understanding how different asset types or seemingly unrelated weaknesses can connect, it’s almost impossible to see how attackers can actually move through your environment.
A real-world breach: The security illusion
Consider this real-world example from a leading U.S. bank — an organization that had invested heavily in security. They had dozens of tools, followed best practices and checked all the boxes. Yet, despite all that, they suffered a major breach that exposed the personal data of over 100 million of their customers.
The fallout?
$650 million in fines and settlements, not to mention the long-term damage to their reputation.
So, what went wrong?
The breach traced back to a single, low-priority misconfigured firewall. To the team responsible, it was just one item in a backlog of thousands. Nothing urgent, nothing unusual.
But that seemingly minor misconfiguration became the entry point for an attacker. It enabled a server-side request forgery (SSRF) attack, which allowed access to temporary IAM credentials from Amazon Web Services’ (AWS) metadata service. From there, the attacker gained access to Simple Storage Service (S3) buckets containing sensitive customer data.
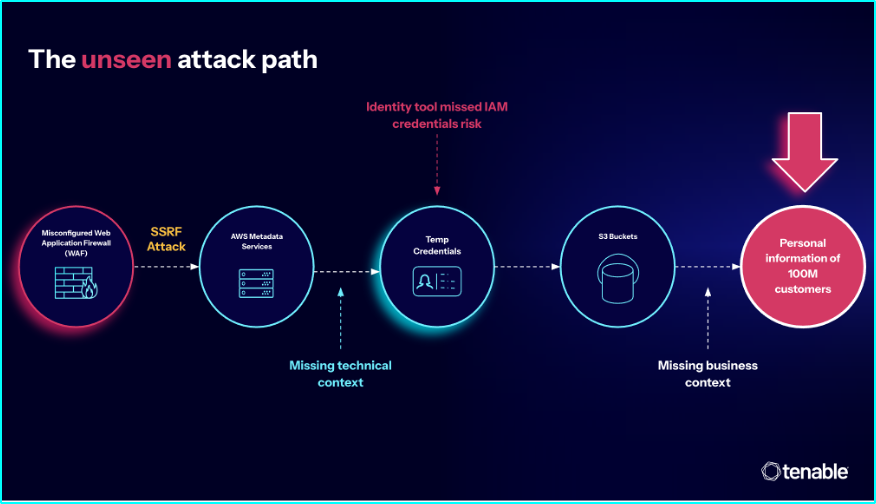
The issue wasn’t a lack of alerts. It was a lack of context.
Without the technical insight to understand how the assets were connected — or the business perspective to recognize that the path led directly to sensitive data — no one could see how the pieces fit together.
This is what we mean by invisible combinations of risk: the kinds of connections attackers see, but your security team doesn’t.
Why context is everything
Security isn’t just about identifying vulnerabilities; it’s about understanding them in context. Without that context, even the most advanced tools can create a false sense of security. A weakness might seem low priority on a dashboard, but could pose a serious risk when connected to other issues. On the other hand, weaknesses that don’t pose a real existential threat to the organization can be flagged as critical, flooding teams with alerts that are hard to prioritize.
To stay ahead of modern threats, you need to move beyond siloed, reactive practices and adopt a proactive, unified strategy that mirrors how attackers think and operate.
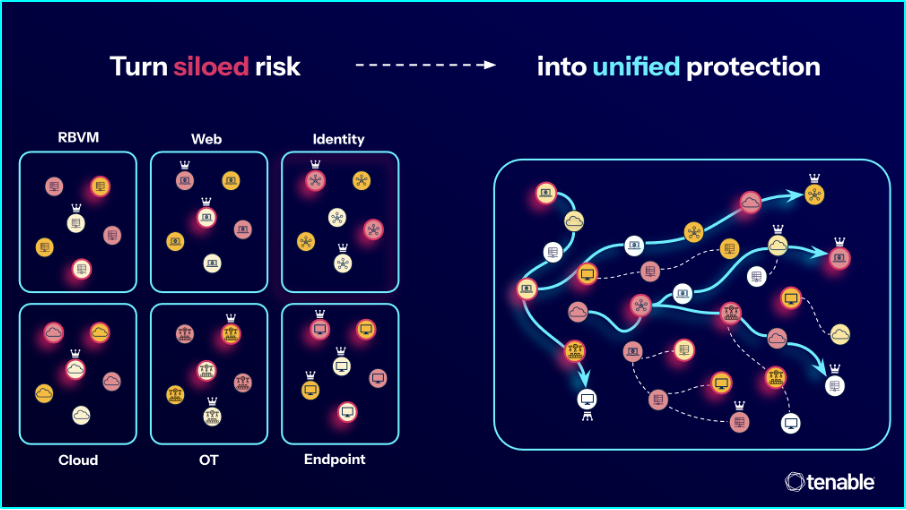
This is where exposure management comes in. It brings together all the essential elements of a modern, risk-based strategy, allowing you to:
- Close your visibility gaps: Eliminate blind spots and uncover hidden risks and critical overlaps across your entire attack surface.
- Expose possible attack paths: See how your assets, users and systems interconnect to uncover potential routes for lateral movement.
- Protect what matters most: Understand where your business-critical assets and sensitive data reside, so you can direct resources to what matters most to your organization.
- Cut through alert noise: Prioritize weaknesses for remediation based on real-world attacker behavior and likelihood of exploitation, reducing alert fatigue.
- Stop attackers in their tracks: Spot choke points to break the chain before an attack can even begin.
This is the core of exposure management — a strategy anchored by a platform that unifies all the essential context to reduce risk in a way that reflects how real-world attacks play out in your environment.
Think like an attacker with Tenable One
Tenable One, one of the world’s leading AI-driven exposure management platforms, is purpose-built to break down data and organizational silos. It serves as the central hub to reduce risk across your entire attack surface. With built-in attack path analysis, Tenable One helps you see your environment the way an attacker would: identifying likely entry points, visualizing lateral movement across assets, understanding the potential business impact and pinpointing choke points where risk can be cut off at the root.
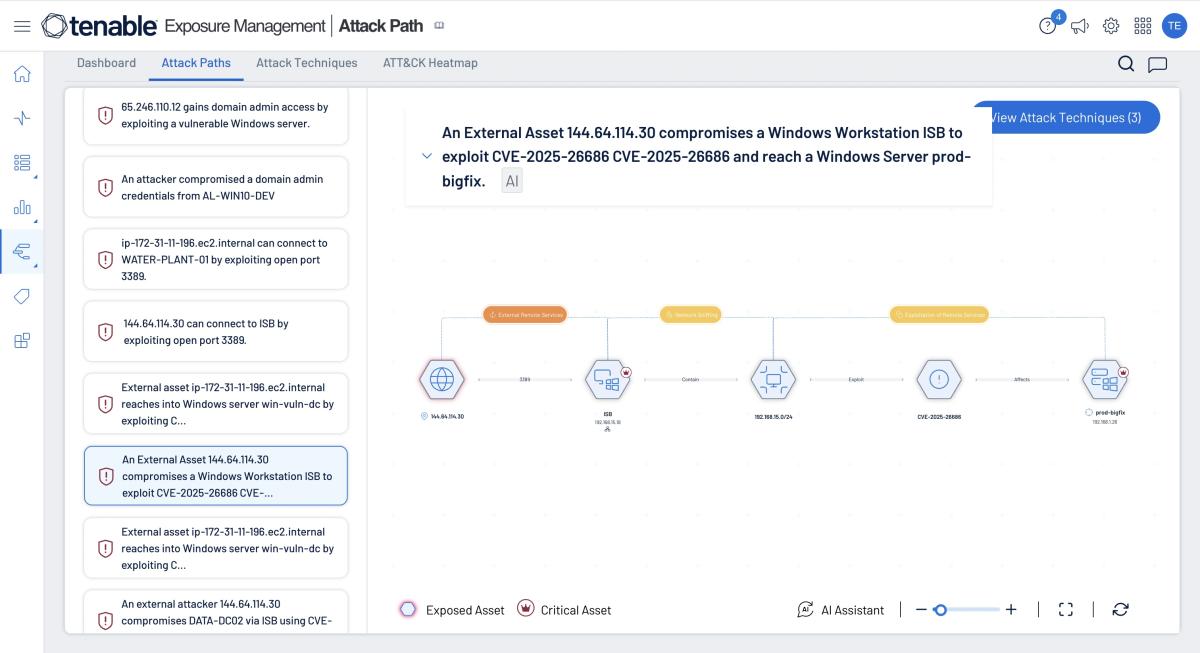
You can explore these attack paths interactively — click into any asset for details, get an instant AI-generated summary of the attack techniques involved and even chat with our AI assistant for answers to everything from asset context to step-by-step remediation guidance.
By shifting from fragmented tools to unified exposure insight, your team can move from reactive to proactive, staying ahead of a breach instead of scrambling to respond after it happens.
- Exposure Management



