Multiple Vulnerabilities in CodeMeter Leave Managed Industrial Control Systems Open to Attack

Six vulnerabilities in a popular license management product put industrial control systems at risk for remote attacks.
Background
On September 8, researchers at Claroty published their detailed analysis, dubbed “License to Kill,” covering several vulnerabilities they discovered in CodeMeter. CoderMeter is a licensing software produced by Wibu-Systems designed for license management and antipiracy in industrial control systems (ICS). It has been integrated by a number of major device manufacturers in the ICS market like Siemens and Rockwell. Other vendors may also be affected as some third party vendors may integrate CodeMeter into their own solutions and devices. The vulnerabilities are significant on their own, but when chained together they provide attackers with a powerful method to attack ICS devices. On September 17, the Cybersecurity and Infrastructure Security Agency (CISA) further reinforced the seriousness of the vulnerabilities, releasing an ICS Advisory (ICSA-20-203-01).
Analysis
The six vulnerabilities discovered in CodeMeter each relate to individual components of the software. Our analysis focuses on the specific vulnerabilities and chaining of these flaws required to perform an attack on a vulnerable system.
To initiate an attack chain for control of devices managed by vulnerable versions of CodeMeter, an attacker would need to forge a license file (CVE-2020-14515) so that CodeMeter trusts the malicious payload that it will later receive. This is achievable because vulnerable versions of CodeMeter do not contain a chain-of-trust check for license files.
A malicious license file with a topic element set to a length of 0 will cause CodeMeter to hang in an endless loop while it tries to parse the file, thereby creating a denial of service (DoS) condition (CVE-2020-14513). This, however, ends one branch of a potential attack chain, and does not lead to a remote code execution (RCE) attack.
The researchers then found that any authorized client connected back to the CodeMeter server had unrestricted access to all functions through the CodeMeter API. However, an attacker cannot force client authorization, so a user would need to somehow accidentally authorize a malicious client with a forged license, which would then allow an attacker to gain code execution on the CodeMeter server and its connected devices (CVE-2020-14509).
CVE-2020-14519 is another code execution flaw, but unrelated to the license manipulation attack chain. This attack requires host access to the CodeMeter server in order to work. By running a malicious application on the CodeMeter server host operating system, an attacker can attack the local loopback listening port for the CodeMeter API (IP 127.0.0.1) and gain full control of the CodeMeter server. In order to exploit this flaw, the attacker would need to trick a user into running a specially crafted JavaScript payload on the CodeMeter host, or execute the payload themselves if they’ve gained system access through other means. The attacker can potentially deliver this payload through a user’s web browser by convincing them to visit a malicious website from the CodeMeter server host. This vulnerability could also be chained with CVE-2020-14515 to create or alter license files for CmActLicense using CmActLicense Firm Code.
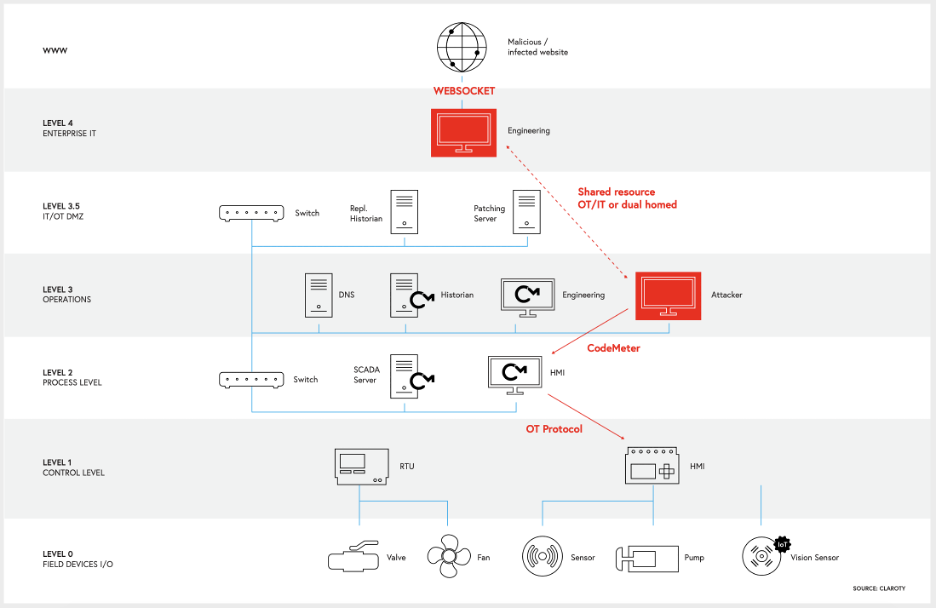
Visualization of the CVE-2020-14519 attack chain
Image Source: Claroty
Below is a list of all six vulnerabilities that were disclosed along with their CVSSv3 and Tenable VPR scores.
| CVE | Vulnerability Type | CVSSv3 | Tenable VPR* |
|---|---|---|---|
| CVE-2020-14509 | Buffer Access With Incorrect Length Value (CWE-805) | 10.0 | 9.4 |
| CVE-2020-14517 | Inadequate Encryption Strength (CWE-326) | 9.4 | 9 |
| CVE-2020-14519 | Origin Validation Error (CWE-346) | 7.5 | 6.9 |
| CVE-2020-14513 | Improper Input Validation (CWE-20) | 7.5 | 6.7 |
| CVE-2020-14515 | Improper Verification Of Cryptographic Signature (CWE-347) | 7.4 | 7.1 |
| CVE-2020-16233 | Improper Resource Shutdown Or Release (CWE-404) | 7.5 | 6.9 |
*Please note Tenable VPR scores are calculated nightly. This blog post was published on September 28 and reflects VPR at that time.
Solution
Wibu-Systems released fixes for all six flaws and recommends upgrading to version 7.10 of CodeMeter. Users are encouraged to upgrade as soon as possible. Much like the Ripple20 vulnerabilities, however, these flaws in CodeMeter present large-scale patch management challenges for vulnerable servers and clients. CodeMeter users can patch their CodeMeter servers, but clients may require vendor intervention and patching. Detection and assessment are key to mitigating risk. We encourage users to manually check for devices like CodeMeter USB dongles in their environment, as device vendors may require additional updates, or issuance of new devices.
If upgrading is not feasible at this time, the mitigations suggested are to block external access to TCP port 22350 to prevent access to the CodeMeter network protocol. However, if an attacker already has local network access via a different vulnerability, they would still be able to exploit CVE-2020-14519.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability is available here.
Tenable.ot customers should contact their Customer Success Manager (CSM) to get access to Suricata rules that can be used for detection. These rules will be fully integrated into the next service pack of the current release and later versions.
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


