Cybersecurity Snapshot: scopri le competenze informatiche più preziose, le principali tendenze della sicurezza nel cloud e il grande impatto della sicurezza informatica sulle aziende

Happy New Year! Learn all about the cybersecurity expertise that employers value most; Google Cybersecurity Action Team’s latest take on cloud security trends; a Deloitte report on cybersecurity’s growing business influence; a growth forecast for cyber spending; and more!
Dive into six things that are top of mind for the week ending Jan. 6.
1 - These cyber skills command higher bonus compensation
As we embark on a new year, it’s a good time to check out what cybersecurity expertise is highly valued and triggering robust bonus pay, so we took a look at Foote Partners’ latest data for the six months ending in Oct. 1, 2022 and plucked the following nuggets.
In the category of non-certified IT skills that are both earning juicy bonuses and growing in value, these cybersecurity-related ones caught our eye:
- Security auditing
- Average pay premium: 20% of base salary equivalent
- Market value increase: 5.3%
- Azure key vault
- Average pay premium:19% of base salary equivalent
- Market value increase: 5.6%
- Cryptography
- Average pay premium: 18% of base salary equivalent
- Market value increase: 20%
- Identity and access management
- Average pay premium: 18% of base salary equivalent
- Market value increase: 5.9%
- Penetration testing
- Average pay premium: 17% of base salary equivalent
- Market value increase: 21.4%
- Security testing
- Average pay premium: 17% of base salary equivalent
- Market value increase: 13.3%
- Threat detection / modeling
- Average pay premium: 17% of base salary equivalent
- Market value increase: 13.3%

In the category of IT certifications, these cybersecurity-related options stand out for their bonus pay and for climbing in value:
- GIAC Certified Forensics Analyst (GCFA)
- Average pay premium: 12% of base salary equivalent
- Market value increase: 9.1%
- InfoSys Security Engineering Professional (ISSEP/CISSP)
- Average pay premium: 12% of base salary equivalent
- Market value increase: 9.1%
- Okta certified professional
- Average pay premium: 11% of base salary equivalent
- Market value increase: 57.1%
- AWS certified security
- Average pay premium: 11% of base salary equivalent
- Market value increase: 22.2%
- Certificate of Cloud Security Knowledge (CCSK)
- Pay premium: 11% of base salary equivalent
- Market value increase: 10%
- CompTIA Advanced Security Practitioner (CASP)
- Average pay premium: 10% of base salary equivalent
- Market value increase: 11.1%
The Foote Partners data comes from its third-quarter “2022 IT Skills Demand and Pay Trends Report” and its third-quarter “2022 IT Skills and Certification Pay Volatility Index.” Those two quarterly reports contain data from 4,000-plus U.S. and Canadian employers that provide the IT analyst firm with pay data about 372,000-plus technology employees.
For more information about Foote Partners’ latest data:
- “Tech’s Winning (and Losing) Jobs in 2023” (Dice)
- “Foote Partners: bonus disparities reveal tech skills most in demand in Q3” (CIO Magazine)
- “Security Skills Command Premiums in Tight Market” (Dark Reading)
2 - Google’s Cybersecurity Action Team unpacks cloud security trends
Google’s latest “Threat Horizons” report is out, outlining key cloud security trends for 2023 from the company’s Cybersecurity Action Team, including:
- Attackers will boost their efforts to compromise cloud environment identities that give them access to assets hosted in multiple cloud platforms, as organizations struggle with ever more complex cloud identity and authentication challenges.
- Taking advantage of the increasingly common integration of operational technology (OT) systems with cloud services, attackers will ramp up their attempts to compromise OT systems via the cloud.
- As cloud environments become more attractive for attackers, they will develop more sophisticated tools and malware tailored for breaching cloud environments.
The report also takes a look back at the top cloud compromise factors and at the most frequently targeted cloud software in 2022’s third quarter, based on an analysis of Google Cloud Platform customer data.
Regarding the cloud compromise factors, Google notes that while weak passwords remain atop this category, the incidence of API key compromises has grown.
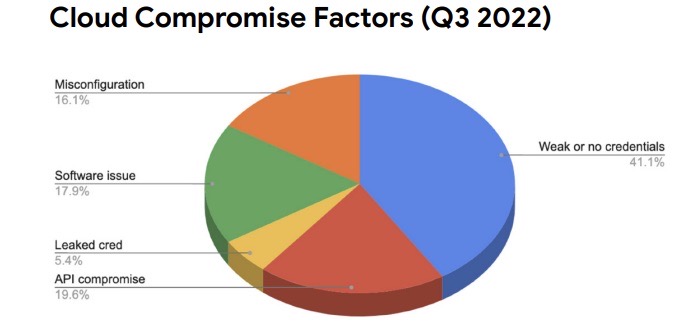
(Source: "Threat Horizons" report from Google's Cybersecurity Action Team, January 2023)
Meanwhile, Google sees an increased diversification in the most commonly targeted cloud software.
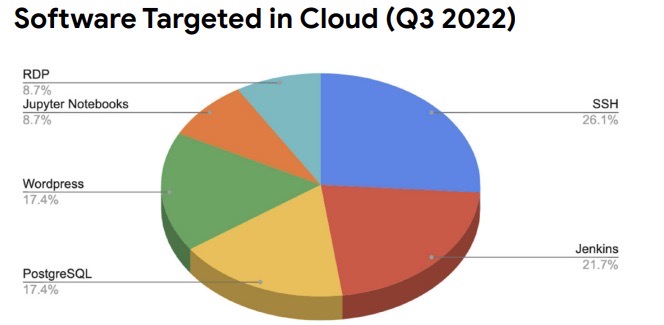
(Source: "Threat Horizons" report from Google's Cybersecurity Action Team, January 2023)
For more information about the report, read this commentary by Google Senior Security Advisor Anton Chuvakin.
To learn more about cloud security challenges and trends:
- “Top challenges for cloud security in 2023” (SC Magazine)
- “The Cloud Is Under Attack: The State of Cloud Security in 2023” (CSO Online)
- “Securing 2023: Cloud security aspects that businesses need to know” (Digital Journal)
VIDEOS:
Multi Cloud Security (Leena Bongale, Manager - Data Analytics & Governance, TD Bank)
Cloud Security for Beginners: Part 1 - Starting Off in the Cloud (SANS Institute)
Zero to Hero in Managing Enterprise Cloud Security (SANS Institute)
3 - Study: Cybersecurity having greater impact on business growth
Cybersecurity’s role has widened beyond the technology realm, as it increasingly influences organizations’ business strategies and goals, and has a progressively larger effect on digital transformation and business success.
That’s according to Deloitte’s “2023 Global Future of Cyber” report, for which the consulting firm polled more than 1,000 cybersecurity leaders from 20 countries, the majority of which said cybersecurity is becoming more and more integrated into the fabric of their business.
Key report findings include:
- 86% of respondents said their focus on cyber has yielded “a significant, positive contribution” to the business.
- 70% said cybersecurity is on their board’s agenda regularly – either monthly or quarterly.
- 58% of organizations polled plan to boost their cybersecurity investment.
What role does cybersecurity play in these digital transformation initiatives?
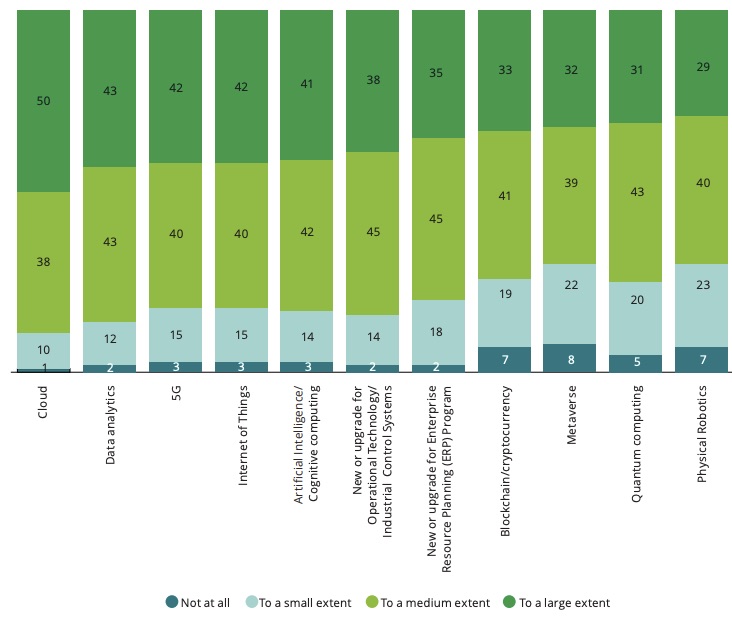
(Source: Deloitte’s “2023 Global Future of Cyber” report, December 2022)
So what characterizes organizations with a high level of cyber maturity and cyber performance that impacts business success? Deloitte identifies three key elements:
- Conducting comprehensive cyber planning, involving strategic, operational and tactical plans to prevent and respond to cyberthreats.
- Carrying out key cyber activities, including qualitative and quantitative risk assessment, the use of industry benchmarking, and planning incident response scenarios.
- Having effective and consistent engagement with the board of directors on a regular basis.
Deloitte also strongly recommends embedding cyber responsibilities throughout the organization, with at least one person in each business unit tasked with coordinating with the cybersecurity team.
Respondents to the survey are cyber decision-makers at the director level or higher in organizations with at least 1,000 employees and US$500 million in annual revenue.
For more coverage about the Deloitte study:
- “Deloitte shows cyber to be an increasing growth enabler” (Data Centre Magazine)
- “Cyber increasingly a growth enabler, Deloitte study shows” (Technology Magazine)
- “Deloitte identifies trust as a common theme in its 2023 Tech Trends” (Silicon Angle)
- “Cybersecurity Drives Improvements in Business Goals” (Dark Reading)
4 - Enterprise IT spending to slow in 2023, but cybersecurity bucks the trend
In its “2023 Technology Spending Intentions Survey,” Enterprise Strategy Group (ESG) forecasts a deceleration in IT spending overall, but several segments will see aggressive investments, including cybersecurity.

Based on a survey of 742 senior IT leaders, the report states that 52% of midmarket and enterprise organizations will up their IT spending this year.
Respondents identified the need to improve cybersecurity as their top driver of IT spending in 2023, as well as the most common catalyst for approving and funding new IT projects. A large majority of senior IT decision makers – 83% – said their organizations are better prepared to respond to a ransomware attack than they were a year ago.
“With an expected increase in criminal activity, organizations will need to invest strategically in areas like vulnerability management and security hygiene – both internally and throughout their supply chain,” said ESG principal analyst Dave Gruber in the report.
Other areas where ESG expects spending to grow robustly include artificial intelligence and cloud computing.
For more information about cybersecurity spending forecasts for 2023:
- “Security to take an outsized role in IT spending in 2023” (CIO Dive)
- “How 2023 cybersecurity budget allocations are shaping up” (CSO Online)
- “Cloud security expected to drive 11.3% growth in security spending in 2023” (SC Magazine)
- “New survey reveals $2 trillion market opportunity for cybersecurity” (McKinsey)
- “IT leaders adjust budget priorities as economic outlook shifts” (CIO)
5 - U.S. government: Put SHA-1 out to pasture
The U.S. National Institute of Standards and Technology (NIST) is recommending that organizations identify any instances where they’re using the SHA-1 algorithm to protect electronic information and replace it with newer, more secure options like SHA-2 and SHA-3.

SHA-1 has been around since the mid-1990s, and is currently vulnerable to attacks from today’s more powerful computers. NIST deprecated its use in 2011 and disallowed its use for digital signatures in 2013.
Now, it plans to stop using SHA-1 altogether by Dec. 31, 2030, at which point cryptographic modules that still use SHA-1 will not be eligible for purchase by the U.S. federal government.
For more information:
- “NIST to Retire 27-Year-Old SHA-1 Cryptographic Algorithm” (SecurityWeek)
- “Goodbye SHA-1: NIST Retires 27-Year-Old Widely Used Cryptographic Algorithm” (The Hacker News)
- “NIST Finally Retires SHA-1, Kind Of” (Dark Reading)
6 - A roundup of 2023 cybersecurity predictions
It’s that time of year when experts venture predictions for the new year. It’s always interesting to check out these forecasts and educated guesses, so we’ve collected links to a bunch of them.

Have fun peering into the cybersecurity crystal balls of the Center for Internet Security, SC Magazine, Dark Reading, Security Magazine, The Hacker News, Beta News, VentureBeat and GovTech.
- Cybersecurity Snapshot
- Exposure Management
- Vulnerability Management
