by Stephanie Dunn
July 6, 2017
Many security solutions within the enterprise often use both whitelisting and blacklisting technologies to allow or deny applications and processes to run. With the number of advanced persistent threats (APT) continuing to grow, malware and other malicious processes are being designed to evade security solutions and remain undetected. This dashboard will assist security teams in detecting and mitigating unknown processes running within the enterprise.
Organizations rely on a variety of security solutions to help prevent malicious processes from running on hosts within their network. These solutions use a database of 'known good' or 'known bad' software to craft security policies. Misconfigurations within these solutions can allow unknown processes to run that could be malicious or lie dormant for long periods of time before being activated. AutoRuns can also be a source for unknown processes to launch and execute malicious code on the network.
This dashboard presents information on unknown processes, Microsoft Windows AutoRuns, gray area processes, and known installed software across a series of components. Filters within this dashboard leverage plugin 70768, Reputation of Windows Executables: Unknown Process(es), to highlight systems running unknown processes. Information is collected on any unknown processes within Windows temp folders on systems. Active scans using Tenable Nessus will assist in tracking AutoRuns that can help to identify malicious or unknown processes being started at system boot or after logging in. A summary of hosts running unknown processes is included, which can help security teams address potentially malicious software. Security teams can obtain additional information such as file name, file path, and MD5 hash on the detected unknown process. Using this information can assist security teams in quickly addressing security gaps and improving the organization's security posture.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 5.5
- Nessus 6.10.8
Tenable SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction and compliance monitoring. SecurityCenter is continuously updated with information about advanced threats and zero-day vulnerabilities, as well as new types of regulatory compliance configuration audits. Active scanning periodically examines devices to determine vulnerabilities and compliance concerns. Host data and data from other security solutions is analyzed to monitor for unknown processes. SecurityCenter CV provides an organization with the most comprehensive view of the network, and the intelligence needed to protect and secure the enterprise.
The following components are included within this dashboard:
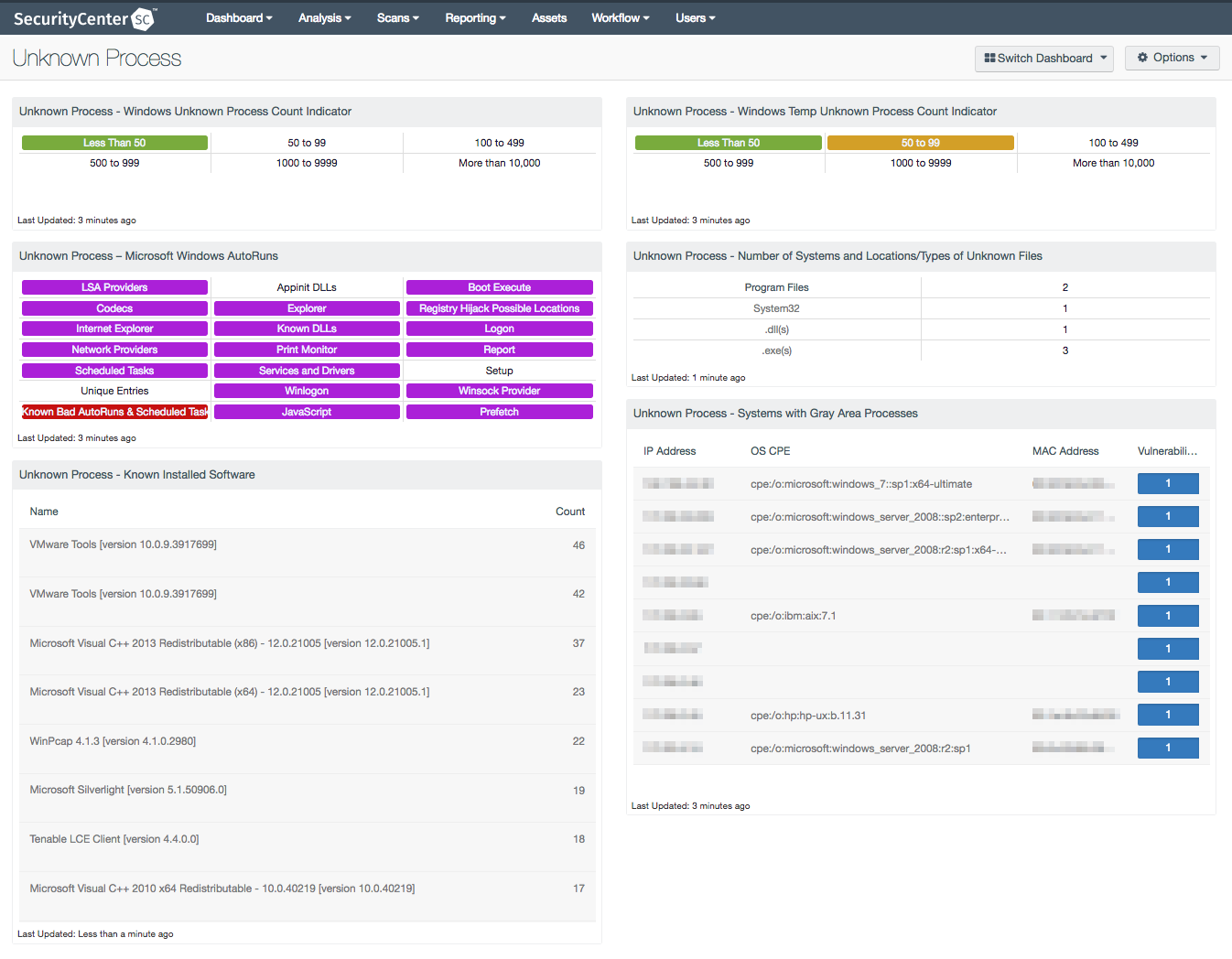
- Unknown Process - Windows Unknown Process Count Indicator: This component utilizes regex patterns to categorize and indicate the total number of unknown process counts reported in plugin 70768.
- Unknown Process – Microsoft Windows AutoRuns: This component presents 21 indicators that will alert on a variety of Windows AutoRun and startup service issues detected on the network.
- Unknown Process - Known Installed Software: This component utilizes the List Software tool in SecurityCenter to provide a table of known installed software.
- Unknown Process - Windows Temp Unknown Process Count Indicator: The component utilizes regex patterns to categorize and indicate the total number of unknown process running from the Windows temp folder.
- Unknown Process - Number of Systems and Locations/Types of Unknown Files: This component uses output from plugin ID 70768, as well as key word indicators, to display a count in regard to the number of devices and locations and types of unknown files.
- Unknown Process - Systems with Gray Area Processes: This component presents a table that contains the detailed vulnerability list of running processes that are not present in a database of 'known good' or 'known bad' software.