by Andrew Freeborn
June 20, 2016
When implementing controls to address compliance requirements, organizations often lose sight of the specific controls needed to address overall risk. This can lead to adding controls that exceed compliance requirements, which can result in additional costs for an organization. The ISO/IEC27000 Compliance Monitoring dashboard will help monitor ISO compliance checks, along with other industry standards and regulation checks.
The ISO/IEC 27002:2013 framework is a global security standard that provides best practice solutions in support of the controls found in Annex A of ISO/IEC 27001:2013. The framework establishes guidelines and general principles for initiating, implementing, maintaining, and improving Information Security Management Systems (ISMS). Each security controls and objectives provided within the standard can be tailored to specific business and regulatory objectives, and assist with maintaining overall compliance. This dashboard focuses on the ISO/IEC 27002 18.1 control that can assist organizations in complying with security policies and standards that will aid in maintaining legal and regulatory compliance.
Many organizations have multiple compliance solutions in place that address an array of compliance regulations. However, some compliance solutions may not address specific compliance controls that are relevant to an organization. Unnecessary controls can consume valuable resources and add unnecessary compliance related costs. Once appropriate compliance controls are established, organizations will be able to address compliance requirements more effectively. By performing regular compliance monitoring, organizations can respond quickly to audit requests, and can adapt to compliance or regulatory changes.
Management and security teams should review the compliance standards applicable to the organization. The compliance requirements should be mapped to business goals to ensure that risks are appropriately identified and mitigated. To see more information on how Tenable’s solutions can be leveraged to achieve compliance, please refer to the Tenable whitepaper “Real-Time Compliance Monitoring.”
This dashboard presents several components that include ISO 27000 and other industry compliance checks that are currently supported by Tenable audit files. Several components display systems that have passed, failed, or required manual verification to determine the risk to the organization. Any audit check failures are set to high severity, which indicate that the collected result and the expected result do not match. A mismatch may not mean a failure, however each failure should be reviewed and verified to ensure the expected result is correct. If the expected result is incorrect, then the audit file should be modified and the scan should be run again. Systems that require a manual check indicate medium severity level results, and should be reviewed further by the analyst to determine the risk. Information provided within this dashboard can assist organizations in identifying security gaps, and aid in improving overall compliance.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.3.2
- Nessus 8.5.1
- Compliance Data
- Local Checks
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable.sc CV enables you to react to advanced threats, zero-day vulnerabilities and new forms of regulatory compliance. Nessus is the global standard in detecting and assessing network data, and supports more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure. Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance.
This dashboard contains the following components:
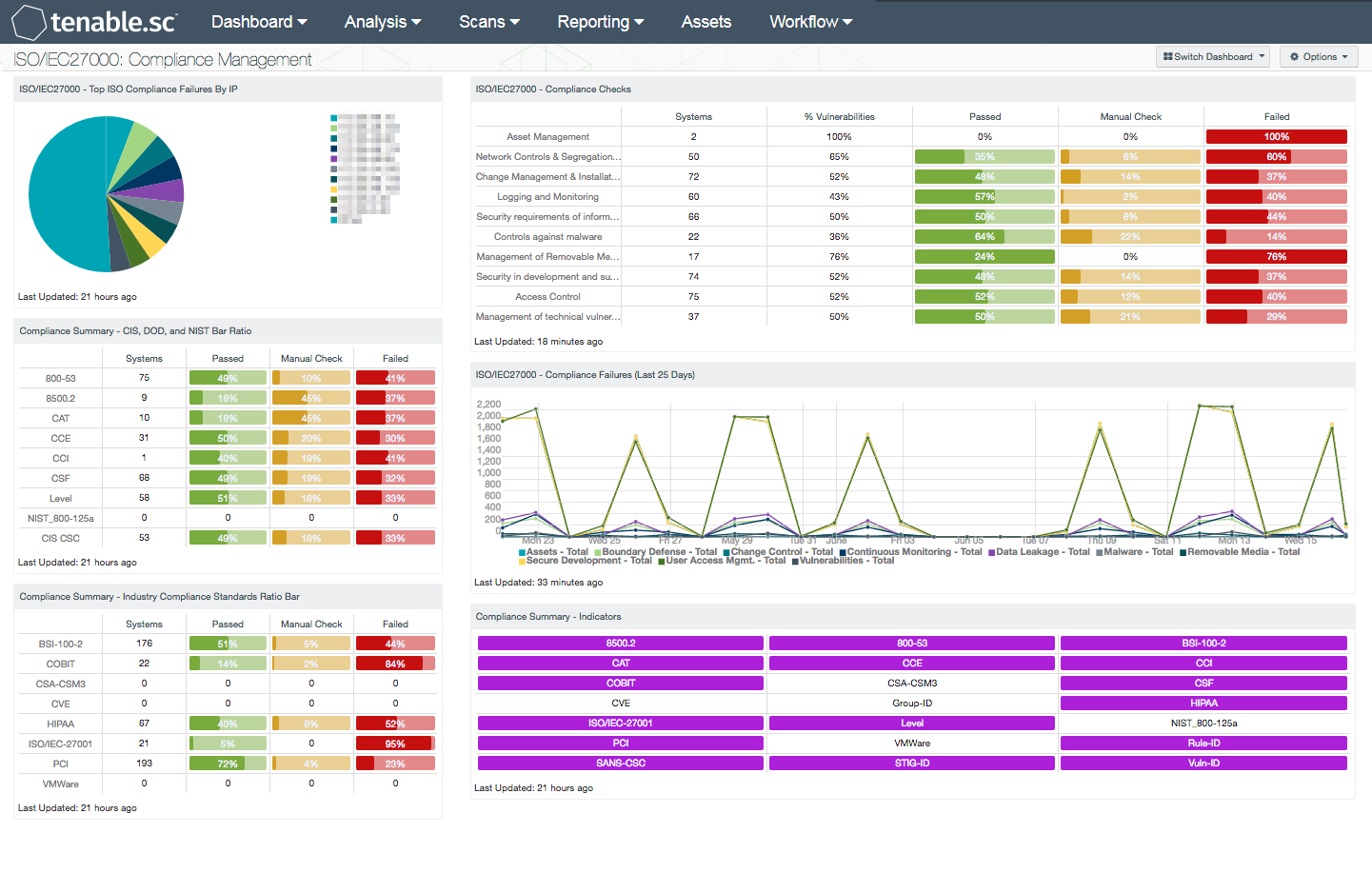
- ISO/IEC27000 - Top ISO Compliance Failures By IP: This component displays the top 10 ISO compliance failures by IP address. The compliance standards in this component include ISO 27000 compliance checks, and are presented with the highest number of compliance failures by IP address at the top. Analysts should review all compliance failures to determine risks
- Compliance Summary - CIS, DOD & NIST Bar Ratio: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are: NIST, DoD, CCE, CCI, CSF, and CSC. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- Compliance Summary - Industry Compliance Standards Ratio Bar: his component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are BSI, COBIT, CCM, CVE, HIPAA, ISO, PCI & VMWare. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- ISO/IEC27000 - Compliance Checks: This component presents ISO compliance checks that align with the ISO/IEC 27000 series dashboards. The matrix is comprised of five columns, with the first displaying a count of affected hosts, followed by the percentage of vulnerabilities. The percentage of passed checks, failed checks, and checks requiring a manual review are presented in the remaining three columns. Info severity represents passed checks, High severity represents failed audit checks, and Medium severity represents checks that must be manually verified. A summary description of each ISO/IEC 27002 control is included within this component.
- ISO/IEC27000 - Compliance Failures (Last 25 Days): This component presents a trend graph of ISO compliance failures over the last 25 days. Each trend line includes ISO compliance checks associates with each ISO/IEC 27000 series dashboards. High severity represents failed audit checks, and should be review further by the analyst to determine the risk to an organization. Analysts can use this data to obtain a status report on patching efforts.
- Compliance Summary - Indicators: This component provides an indicator for the supported compliance standards. Each indicator will provide an easy mechanism to see a list of hosts applicable to each standard. This component will return a list of hosts regardless of whether or not the audit check passed or failed. The indicator will turn purple when a match is found.