by Cody Dumont
February 4, 2020
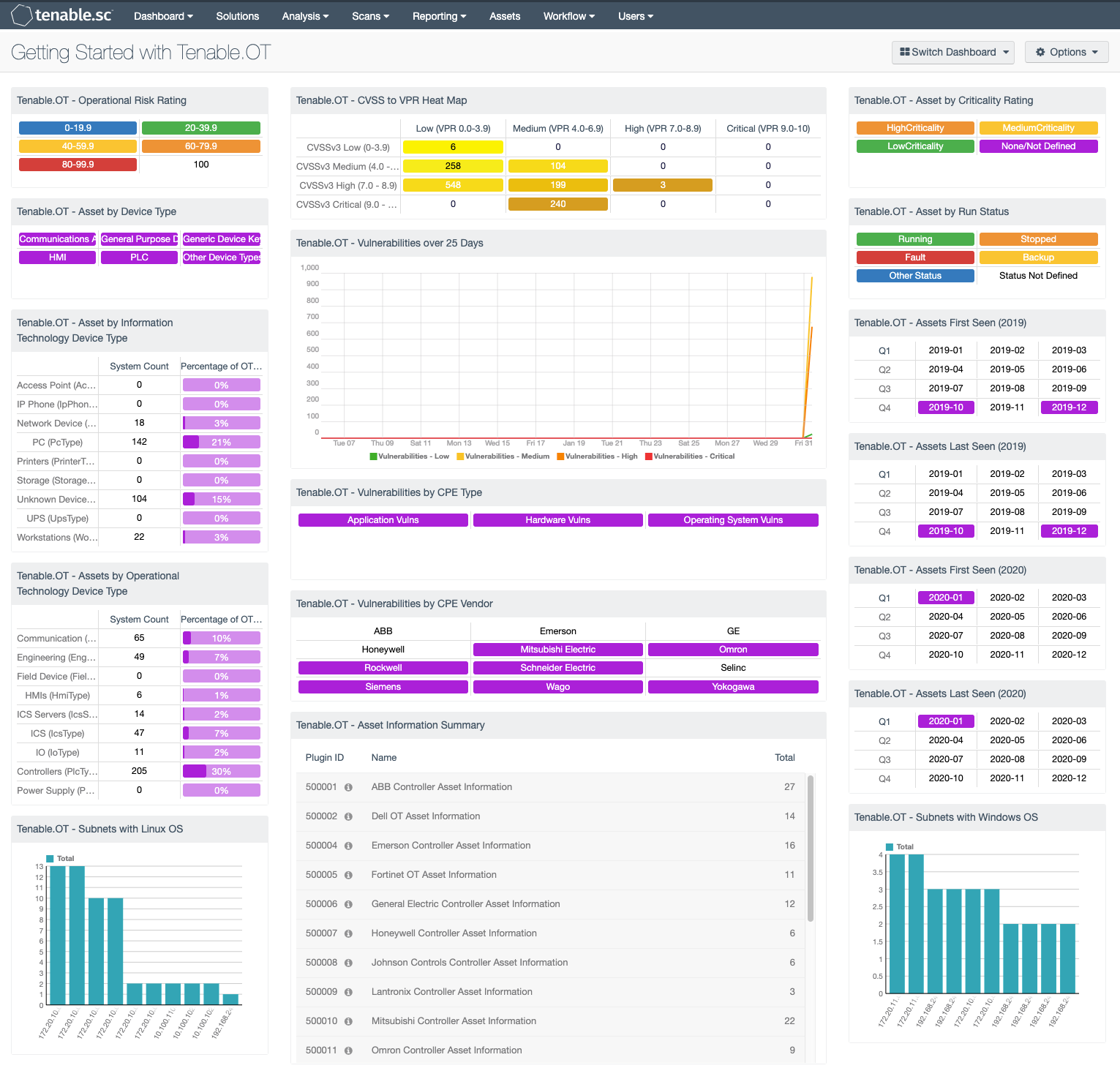
As networks converge between Information Technology (IT) and Operational Technology (OT), organizations struggle to view the complete visibility of the network. Using Tenable.ot and Tenable.sc together, the complete picture of a network is visible to risk managers and CISO’s. Tenable.sc is able to connect with Tenable.ot and incorporate risk scores such as Vulnerability Priority Rating (VPR) and Common Vulnerability Scoring System (CVSS) vectors to fully understand risk.
As Tenable expands into OT markets, organizations are afforded the opportunity to perform risk analysis based on OT and IT data in a single unified platform with Tenable.ot and Tenable.sc. In the first row of components, the dashboard provides added value of combining the two systems together. By showing the correlation of the Risk Ratings, CVSS, VPR, and criticality rating, the risk managers are able to gain clear understanding of the to overall IT/OT risk.
On the left side of the dashboard there are two components that show the percentage of systems with respect to IT and OT asset classification type. Each component has a column for the system count and overall percentage. The components in the middle of the center column use the Common Platform Enumeration (CPE) detections. This attribute is part of the vulnerability plugin and can denote hardware, applications, or operating system vulnerabilities. In addition, the CPE contains manufacture information. System managers can use this information as a starting points for vulnerability analysis and patch management efforts. In the right hand column, there are 4 components that track when an asset is first discovered on the network and when last seen. These two attributes help asset managers track when new systems are detected and if the system are in current use. The bottom components use the Asset Identification plugins to show a summary of the device types detected, and the operating systems used.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Tenable.ot
As threats to cloud, IT, and OT are exposed, organizations that practice Cyber Exposure are able to use Tenable.sc to reduce their Cyber Exposure gap. Tenable.ot helps to expand the enterprise visibility and merge traditional Vulnerability Management (VM) practices to include IT and OT. Using the advanced reporting capabilities of Tenable.sc, risk managers are able to import data from OT networks into single VM platform. The OT data can then be reviewed and assessed alongside the IT VM data for a complete picture of cyber risk.
Components
Tenable.ot - Operational Risk Rating: This matrix provides indicators for different ranges of the operation risk rating calculated by Tenable.ot. This calculation is a combined value, calculated using the total CVSS scores and other factors that are known to increase risk. Each color indicates a greater risk where the lowest risk is blue (0 – 19.9) and the greatest risk is red (80 – 100. This data is extracted from the Asset Identification plugins and can be used in the creation of Dynamic Assets for more detailed analysis.
Tenable.ot - Asset by Device Type: This matrix provides indicators for each of value in the Device Type field stored in the Asset Identification plugins. The Device Type value is collected from the OT vendors and stored in the plugin. This variable is not controlled by Tenable.ot. When the cell is purple, there are devices matching this rule.
Tenable.ot - Asset by Information Technology Device Type: This component helps to group the Information Technology devices so risk managers can understand how IT and OT risk is calculated. The first column is a count of hosts, where the defined value is present in the Asset Identification plugin. The second column is the percentage of overall systems with plugins in the 500k range.
Tenable.ot - Assets by Operational Technology Device Type: This component helps to group the Operational Technology devices so risk managers can understand how IT and OT risk is calculated. The first column is a count of hosts, where the defined value is present in the Asset Identification plugin. The second column is the percentage of overall system with plugins in the 500k range.
Tenable.ot - Subnets with Linux OS: This bar chart shows a count per subnet for assets identified as having the Linux OS installed. The Asset Identification plugin contains an attribute that provides the operating system type. The component is sorted based on count using the subnet mask of /24 to separate networks.
Tenable.ot - CVSS to VPR Heat Map: This matrix provides a heat map showing the alignment of the Vulnerability Priority Rating (VPR) and Common Vulnerability Scoring System (CVSS) for all vulnerabilities with plugin ID in the 500K range. The Tenable.ot plugins are defined in the 500K range and use the CVE to map to the VPR to vulnerability. This integration provides advanced insight into the dynamic nature of risk based on the on going attack surface.
Tenable.ot - Vulnerabilities over 25 Days: This trend graph shows the Tenable.ot vulnerabilities collected over the past 25 days. The filters applied show the vulnerability severity; low, medium, high, and critical. . Each data point shows the vulnerability count from the previous day using the “Vulnerability Last Observed” filter.
Tenable.ot - Vulnerabilities by CPE Type: This component identifies vulnerabilities based on the Common Platform Enumeration (CPE) string and denotes hardware, application, or operating system vulnerabilities. The CPE string for this data is different from other CPE, and is for example “cpe:2.3:a” is for application CPE. The other options have an “cpe:2.3:h” for hardware, and “cpe:2.3:o” for operating system. If the indicator is purple there is a match for the respective pattern.
Tenable.ot - Vulnerabilities by CPE Vendor: This component identifies vulnerabilities based on the Common Platform Enumeration (CPE) string and denotes vulnerabilities by device manufacturer. The CPE is broken down into separate strings and separated using a colon “:”. The first string denotes the manufacturer of the device. If the indicator is purple there is a match for the respective pattern.
Tenable.ot - Asset Information Summary: Tenable.ot provides asset information in the plugins called Asset Summary. This table is a list of these plugins present on the network. The list is sorted based on total plugins present and using the plugin name filter to separate them by Asset Identification plugins from the vulnerability plugins.
Tenable.ot - Asset by Criticality Rating: This matrix provides indictors for the different criticality ratings for devices identified using Tenable.ot. These ratings are established by default per the device type. However, administrators have the option to change this setting. Each color is based on the standard colors Tenable uses for the High (orange), Medium (yellow), and Low (green) severities. The purple indicator is for systems with no criticality rating defined.
Tenable.ot - Asset by Run Status: This matrix provides an indicator for each of the known run statuses. The colors follow the Tenable color standard for severity level. Green being Low for Running status which is the desired state, while the other colors indicate some problem. The “Other Status” indicator is for Asset Identification plugin results present, but are not one of the previous 4 status’. If the run status is not present in the plugin output, then a purple indicator will be displayed.
Tenable.ot - Assets First Seen (2019): Tenable.ot tracks by date the first time an asset is detected. This matrix provides indicators for every month in 2019. Each row is separated by quarter, and will turn purple when a match is discovered. This date does not represent the Tenable.sc “Vulnerability Discovered” date.
Tenable.ot - Assets Last Seen (2019): Tenable.ot tracks by date the last time an asset is detected. This matrix provides indicators for every month in 2019. Each row is separated by quarter, and will turn purple when a match is discovered. This date does not represent the Tenable.sc “Vulnerability Last Observed” date.
Tenable.ot - Assets First Seen (2020): Tenable.ot tracks by date the first time an asset is detected, this matrix provides indicators for every month in 2020. Each row is separated by quarter, and will turn purple when a match is discovered. This date does not represent the Tenable.sc “Vulnerability Discovered” date.
Tenable.ot - Assets Last Seen (2020): Tenable.ot tracks by date the last time an asset is detected, this matrix provides indicators for every month in 2020. Each row is separated by quarter, and will turn purple when a match is discovered. This date does not represent the Tenable.sc “Vulnerability Last Observed” date.
Tenable.ot - Subnets with Windows OS: This bar chart shows a count per subnet for assets identified as having the Windows OS installed. The Asset Identification plugin contains an attribute that provides the operating system type. The component is sorted based on count using the subnet mask of /24 to separate networks.