by Stephanie Dunn
June 24, 2016
Monitoring network traffic and event log data for suspicious activity can help provide critical information on malicious attacks, intrusions, or data leakage with an organization. By continuously monitoring these events, organizations will be able to detect and respond to potentially suspicious activity before critical systems are affected. This dashboard presents an overview of inbound, internal, and outbound network traffic activity, which can help organizations determine how systems are being compromised, and where network defenses need to be strengthened.
Monitoring the large amounts of data that traverses the network on a daily basis can be difficult for any organization to manage. Many organizations today deploy solutions that protect and monitor the network perimeter against potential intrusions or attacks. Additionally, some organizations have had to change existing security measures to monitor additional services and devices such as mobile, cloud, and Bring Your Own Device (BYOD) programs. Tenable Log Correlation Engine (LCE) monitors and collects logs forwarded by network devices, which can provide real-time information on network utilization issues, unusual traffic patterns, data exfiltration, malware infections, and more. This information can be used to correlate malicious software that may have been installed or unauthorized devices that have connected to the network. Continuous monitoring provides organizations with the ability to adequately protect and defend against emerging threats.
This dashboard provides insight into existing network activity by leveraging LCE’s ability to filter inbound, outbound, and internal network traffic events. Network traffic is identified by the following three methods. Traffic from IP addresses considered external to your network, going to addresses that are internal to your network are considered inbound traffic. Internal traffic is traffic between IP addresses that are considered internal within your network. Any traffic from IP addresses considered internal to your network, going to addresses that are external to your network are considered outbound traffic. Each LCE normalized event that has a source or destination IP address is compared to the network range being monitored by the LCE. Information presented within this dashboard will provide security teams with complete visibility into existing network traffic activity across the enterprise.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring. The dashboard requirements are:
- SecurityCenter 5.3.2
- LCE 4.8.0
Tenable SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. The Tenable Log Correlation Engine (LCE) correlates real-time events, such as port scanning, and then performs analysis to discover vulnerabilities and indicators of compromise (IOC). The Tenable Passive Vulnerability Scanner (PVS) continuously monitors network traffic in real time to discover vulnerabilities on devices and systems. Using SecurityCenter Continuous View (CV) provides organizations with the most comprehensive view of network traffic and events across the enterprise.
The following components are included in this dashboard:
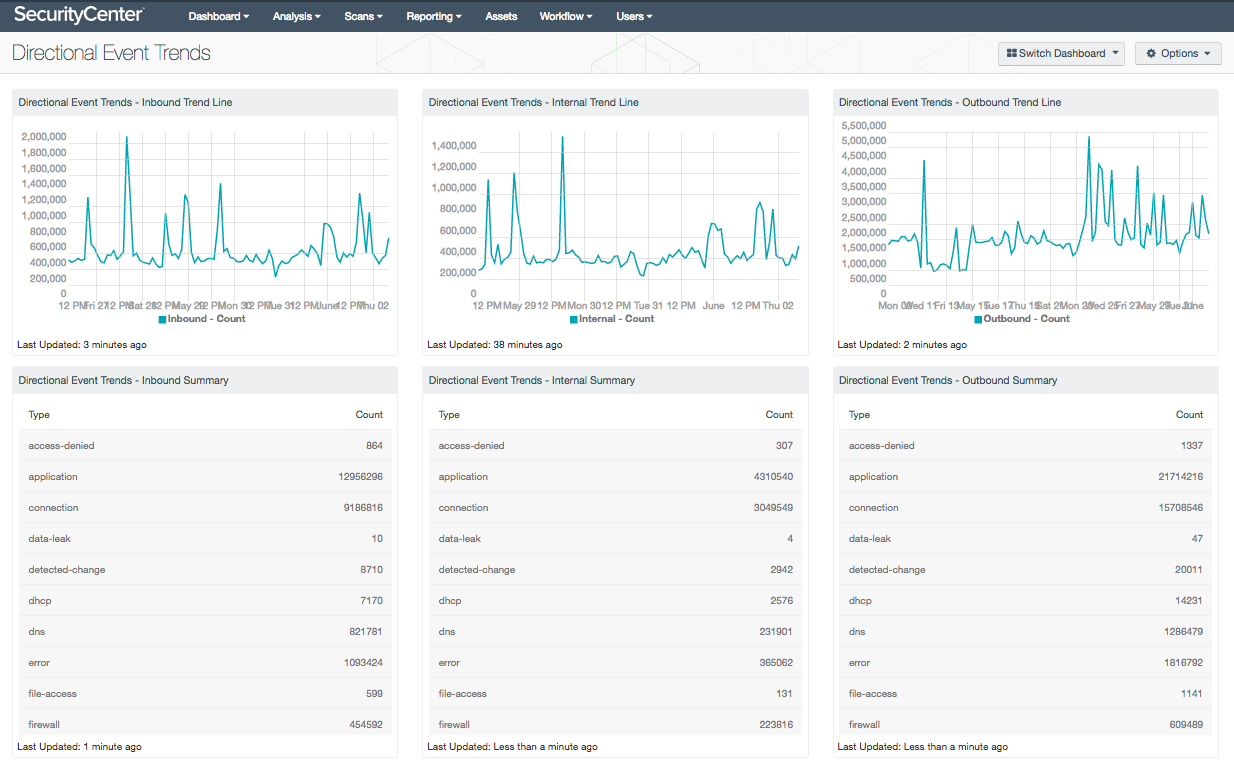
- Directional Event Trends - Inbound Trend Line: This component is a directional trend line over the past 5 days of inbound events. Traffic from IP addresses considered external to your network, going to addresses that are internal to your network are considered inbound traffic. Analysts can use this component to detect inbound network attacks, unusual network connections, and more.
- Directional Event Trends - Inbound Summary: The Inbound Summary table presents a summary of inbound traffic events over the past 5 days. Traffic from IP addresses considered external to your network, going to addresses that are internal to your network are considered inbound traffic. This component can be modified to include additional or specific event data per organizational requirements.
- Directional Event Trends – Internal Trend Line: This component is a directional trend line of internal network events over the last 5 days. IP addresses considered external to your network, going to addresses that are internal to your network are considered inbound traffic. Analysts can use this component to detect a wide variety of internal activity such as internal data transfers, remote access connections, and infected hosts.
- Directional Event Trends - Internal Summary: The Internal Summary table presents a summary of internal traffic events over the past 5 days. Internal traffic is traffic between IP addresses that are considered internal within your network. Information is sorted by event type, and can be modified per organizational requirements.
- Directional Event Trends - Outbound Trend Line: This component is a directional trend line of internal network events over the last 5 days. IP addresses considered external to your network, going to addresses that are internal to your network are considered inbound traffic. Analysts can use this component to detect malicious botnet connections, intrusions, and data leakage.
- Directional Event Trends - Outbound Summary: The Outbound Summary table presents an overview of outbound network traffic over the last 5 days. Any traffic from IP addresses considered internal to your network, going to addresses that are external to your network are considered outbound traffic. Information presented within this component can be useful in identifying botnet activity, compromised hosts, and data exfiltration.