by Josef Weiss
September 17, 2025
The Cyber Essentials is a UK government-backed framework which is designed to assist organisations in protecting themselves against common threats. The Cyber Essentials provides a basic cyber security foundation that can serve as a stepping stone to a more comprehensive zero-trust approach. The Cyber Essentials is built on 5 key components that, when implemented correctly, can reduce cyber risk. The five key components are:
- Firewalls and Boundary Devices
- Secure Configurations
- Access Control
- Malware Protection
- Patch Management
Tenable has released a series of dashboards, that focuses on each of the five basic technical controls, which organisations can use to help strengthen their defences against the most common cyber threats.
The focus of this dashboard is Section 1 - Firewalls and Internet Gateways. Key components of this section apply to all the following in scope devices: Boundary Firewalls, Desktop Computers, Laptops, Routers, Servers, Iaas, PaaS, and SaaS devices. Devices must be secure and only necessary network services should be able to be accessed from the Internet. The objective of this key component is the control of inbound/outbound traffic.
This requirement applies to every in scope device, and can be achieved using Boundary Firewalls to restrict inbound or outbound traffic, a software firewall which is installed and configured on each end point device, or for cloud services, data flow policies. Most end point devices, such as desktops and laptops come with software firewalls pre-installed, and the Cyber Essentials recommends that these services be enabled. Essentially, every in scope device must be protected by either a properly configured firewall, or a network device with firewall functionality.
This dashboard contains the following components:
Components
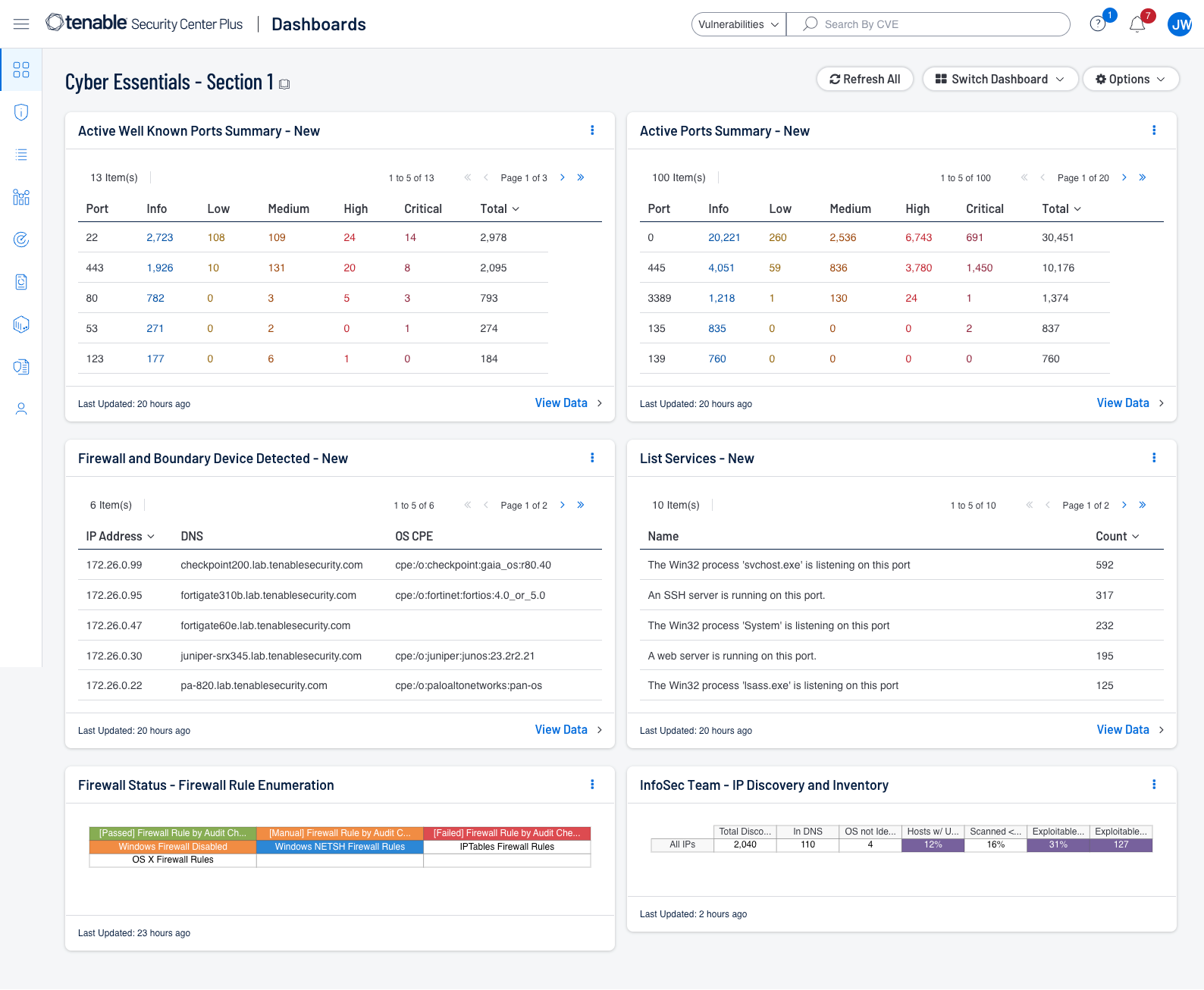
Active Well Known Ports Summary - This table displays vulnerability severity data related to well known ports, the severity, and a count for each port number.
Active Ports Summary - This table displays vulnerability severity data related to all ports except well known ports, the severity, and a count for each port number.
Firewall and Boundary Device Detected - This table displays firewall and boundary devices that have been identified in the environment.
List Services - This table uses the List Services tool to display the top 100 services which have been identified. Services are listed by name, and count, with the most prominent being at the top of the list.
Firewall Status - Firewall Rule Enumeration - This matrix uses plugin 56310 (Firewall Rule Enumeration) and audit checks to report on the status of software-based firewall rules.
InfoSec Team - IP Discovery and Inventory - This matrix displays host discovery and basic scan information. The matrix displays information related to operating system identification, hosts in DNS, hosts scanned, and hosts with unsupported or exploitable applications.