by Cesar Navas
December 10, 2019
As new technologies continue to advance, personal devices are increasingly connected to enterprise networks. New or unknown software on an organization's network can pose a great risk to the organization. This dashboard provides information to assist in identifying unwanted or potentially dangerous applications, enabling an efficient vulnerability management program.
The CIS ControlsTM are a prioritized set of actions that collectively form a defense in-depth set of best practices that mitigate the most common attacks against systems and networks. These controls were developed by IT professionals using operational experiences and generally accepted best practices. This dashboard will focus on Control 2. Control 2 requires the organization to actively manage all software. Tenable.sc helps by actively scanning the systems and taking software inventories of properly installed software. System administrators and operation teams can review the software inventories and look for unauthorized software.
Historically CIS has referred the first six CIS controls as cyber hygiene to focus an organization’s cybersecurity activities. The designation of cyber hygiene highlights the point that these practices may be difficult for organizations with resource and/or expertise limitations. To address any resource or expertise limitation, CIS now recommends following Implementation Groups (IG) to help prioritize CIS control utilization. There are three IG’s, which describe organization by size. The IG specifies a subset of the controls that have been assessed to have a similar risk profile and resources to implement. The IG’s are also meant to be prioritized in IG order regardless of the IG organization size. For example, organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3. The IG’s are described as organizations with limited resources and cybersecurity expertise (IG1); organizations with moderate resources (IG2); organizations with significant resources (IG3).
Sub-control 2.2 involves an organization ensuring they are detecting supported and unsupported software that may be in the network. Tenable.sc helps implement sub-control 2.2 by using active and passive detection methods to identify unsupported software on the network. Furthermore, sub-control 2.2 can be implemented by IG1, IG2, and IG3.
Sub-control 2.3 involves an organization using a software inventory tool to create a list of software on the network. Tenable.sc assists implement sub-control 2.3 by identifying software that is installed on hosts on the network. Unsupported applications and missing patches are also identified. Lastly, only IG2 and IG3 can implement this sub-control as CIS understands organizations within IG1 may not have the resources to use a software inventory tool like Tenable.sc.
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Tenable Nessus Network Monitor (NNM). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network vulnerabilities.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.8.0
- Nessus Network Monitor 5.10.1
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to Discover hardware assets, for a more detailed analysis. Not only detecting risks based on Common Vulnerabilities and Exposures (CVE), but also using more advanced methods such a Vulnerability Priority Rating (VPR). Tenable.sc provides customers with a full and completed Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by CIS Controls framework.
This dashboard contains the following components:
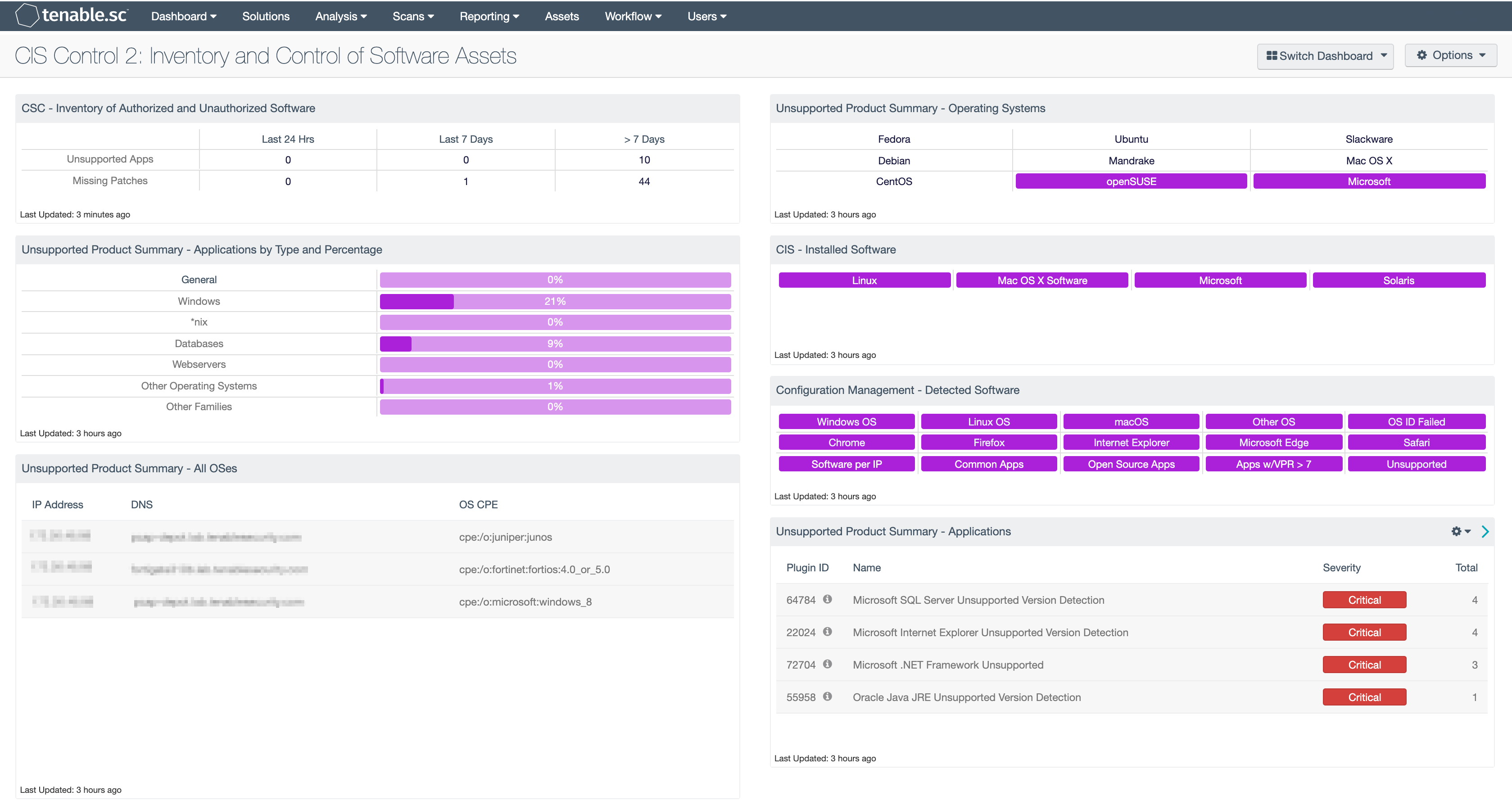
CSC - Inventory of Authorized and Unauthorized Software: Knowing the count of unsupported applications and systems with missing patches on the network is crucial when assessing the vulnerability of the asset. This component shows the count of applications that either require patches or are unsupported by the vendor. Based the organization’s scanning cadence, this component will help bring focus to the time of discovery. If the time between scans is greater than 7 days, the last observed filters can be modified to better align with scanning cadence.
Unsupported Product Summary - Applications by Type and Percentage: This bar chart component produces a graph on the percentage of unsupported applications and operating systems in the environment sorted product type, such as database servers, web servers, Windows, or other Operating Systems. In this component, a base query with a vulnerability text filter is utilized with the key word of filter against the plugin name, along with additional filters for the plugin family. This allows a chart to be displayed that presents the percentage of unsupported or end-of-life applications by type and categorized by either operating system or application.
Unsupported Product Summary - All OSes: This table lists the hosts determined to be running unsupported operating systems. The table filters for operating systems by CPE and uses the plugin keyword “unsupported.” Security teams should use this table to prioritize systems that are running unsupported operating systems for upgrade.
Unsupported Product Summary - Operating Systems: This indicator matrix reports on operating systems that are no longer supported. The matrix displays popular operating systems, but is easily modified to fit organizational requirements. Plugin ID #33850, with vulnerability text filters that filter for the appropriate operating system name in the plugin output, alert on Unix-based operating systems that are no longer supported. Keyword filters, along with a CPE string for Microsoft, is used to alert on end-of-life Microsoft operating systems by turning the indicator purple when an alert is present.
CIS - Installed Software: This matrix component utilizes software enumeration plugins for each of the platforms the cells are named after. Drilling into a cell and looking at the plugin output, an analyst is able to see a list of software that is installed on the hosts.
Configuration Management - Detected Software: This matrix presents indicators that detect operating systems, browsers, unsupported, and other software installations on systems within a network. Indicators will turn purple when a match is found and display a list of detected software. Analysts will find this information useful in tracking software licenses, and identify hosts running unauthorized or malicious software. Additionally, the data provided within this component can be used to monitor systems running unsupported software, which can contain vulnerabilities and place critical systems at risk. Filters within this component can be modified to include additional or specific software per organizational requirements.
Unsupported Product Summary - Applications: The Unsupported Applications component displays a table of all unsupported applications by name, and sorted by severity. Displayed is the plugin ID, application name, plugin family, severity, and the total found. This component identifies unsupported applications by the “unsupported” filter against the plugin name. The table also filters on severity, dropping any informational results, and presents them via the Vulnerability Summary tool.