by Cody Dumont
November 18, 2016
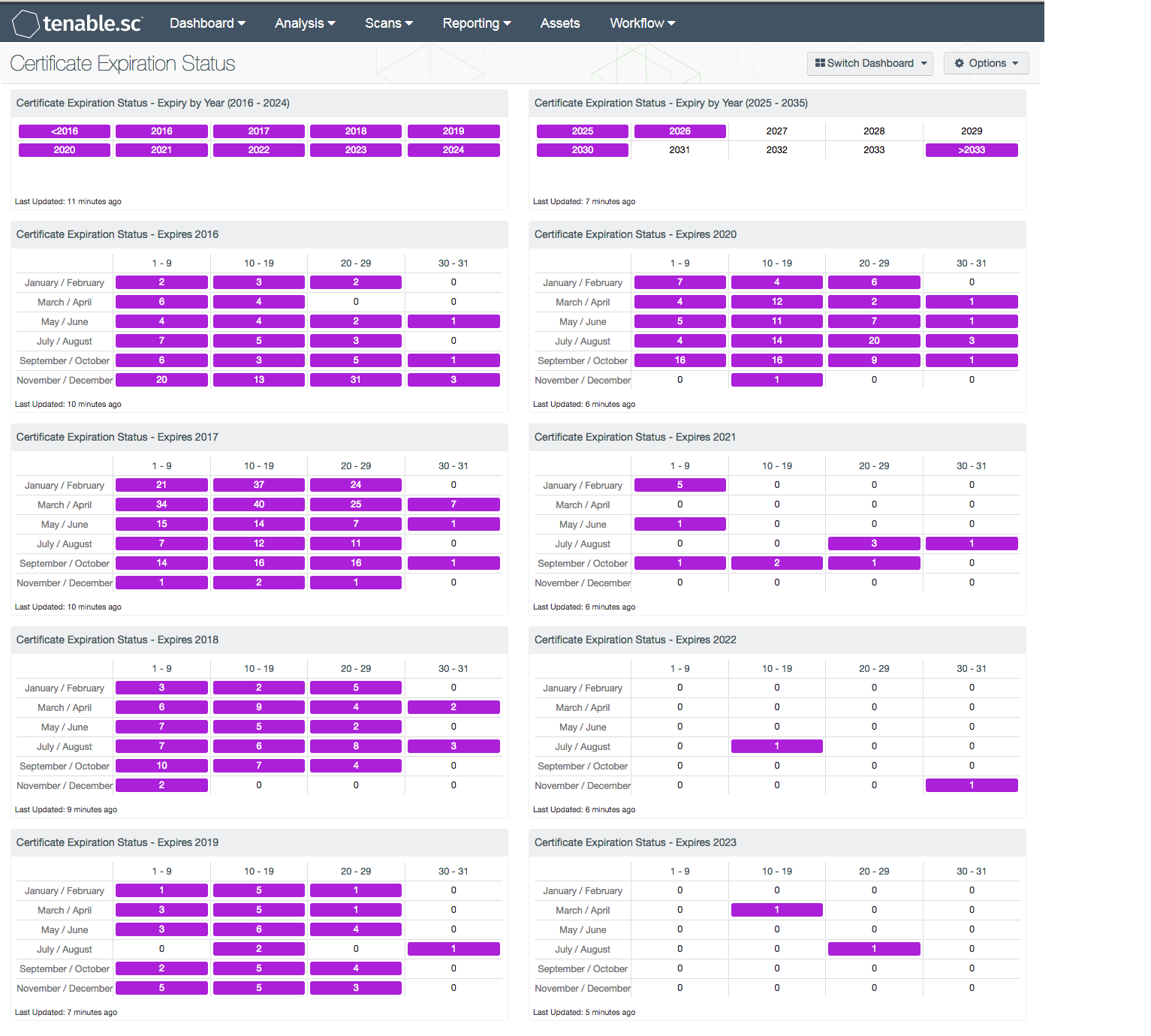
With the ever-expanding need for encryption and the complexity PKI brings to the table, tracking certificate expiry dates becomes more challenging. Tenable.sc can monitor certificate usage and expiration dates using active and passive detection through log correlation. This dashboard provides a concise view of systems and the expiration date of any identified certificates.
In some environments there are often several groups within the organization purchasing certificates. Unfortunate scenarios can occur, such as certificates which are lost with a change of personnel. Additional risks to the organization can be certificates getting lost or certificates that are not part of the monitoring process. For example, if an organization purchased a wild card certificate, the organization may not keep track of all the systems where the certificate is installed. Organizations also need to be aware of threats such as Man in the Middle (MitM) attacks that rely on users blindly accepting invalid certificates. Gaining a thorough understanding to the risk posed by expired certificates is a constant struggle for security operation teams.
The components in this dashboard use regular expression matching to identify certification expiration date fields, which are collected when secure network traffic is detected. The components are broken down by month for the years 2016 to 2023. For subsequent years there is a summary component. Listed below are just a few of the plugins that are matched using the regular expression filter. Showing the flexibility of Tenable.sc, any new plugins that are created which have “Certificate” in the plugin name, an expiration date, or date range will be also be added to the results of the dashboard queries.
- SSL Expired Certificate Detection (7036)
- SSL Certificate Expiration Date Detection (7052)
- SSL/TLS Certificate Validity Dates Detection (7126)
- SSL Certificate Information (10863)
- SSL Certificate Expiry (15901)
- SSL Certificate Expiry - Future Expiry (42981)
- SSL Certificate Cannot Be Trusted (51192)
- SSL Certificate Chain Contains Certificates Expiring Soon (83298)
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.6.0
- NNM 5.9.0
- LCE 6.0.0
One of Tenable’s goals is to help secure the future of organizations with continuous visibility and continuous context, so our customers can take decisive actions and achieve security assurance. To achieve this goal Tenable.sc CV helps to improve visibility, by resolving uncertainty and eliminating blind spots such as expired certificates in the organization. Tenable.sc CV helps organizations to understand the context of the security risks, remove complexity of risk analysis, and prioritize threats. Allowing security operations teams to take action and make smarter decisions helps reduce risk exposure and loss. With Tenable.sc CV, customers can transform their security with continuous visibility and critical context, enabling decisive actions to protect their organizations.
Components
Summary Matrices - There are two matrices that provide a summary view of certificates that expire by the years of expiry. Each cell will identify systems using the plugin name and regular expression (regex) in the vulnerability text. The regex looks for expiration dates found in the certificates. When the indicator turns purple, there are systems with at least one certificate that expires in the respective year. The first matrix is for years 2016 - 2024, the second matrix is 2025 - 2033.
Matrix by Year - The dashboard provides 8 matrix components each for the years (2016 - 2023), that provide a detailed view of system counts with certificates that expire during the respective year, separated by day and month. The filters in this matrix use regular expressions (regex), to provide the security operations team with a detailed view of the systems that have certificates and the date the certificate expires. When a match is found, the cell will turn purple and display a host count. As time progresses, the analyst may want to change the cell color to red to indicate a date that has passed to indicate a greater risk.