Windows Task Scheduler Zero-Day Exploit Available in the Wild: Caution Urged

Updated September 11: Microsoft released the patch for this vulnerability (CVE-2018-8440) today as part of its monthly security update known as Patch Tuesday. Customers are advised to apply this security update as soon as possible.
Updated September 5: Public exploits of this vulnerability have been seen by researchers at ESET. The Solution section of the CERT page offers the best known workaround until Microsoft releases a patch, which is planned for September 11.
Background
On August 27, a security researcher made waves by releasing a working exploit on Github for a previously unknown, serious local privilege escalation (LPE) vulnerability in Microsoft Windows Task Scheduler.
The zero-day exploit, which was released via a Twitter post, allows a privileged attacker to obtain full SYSTEM access on fully patched Windows 10 and Windows Server 2016 systems. Other platforms may also be affected.
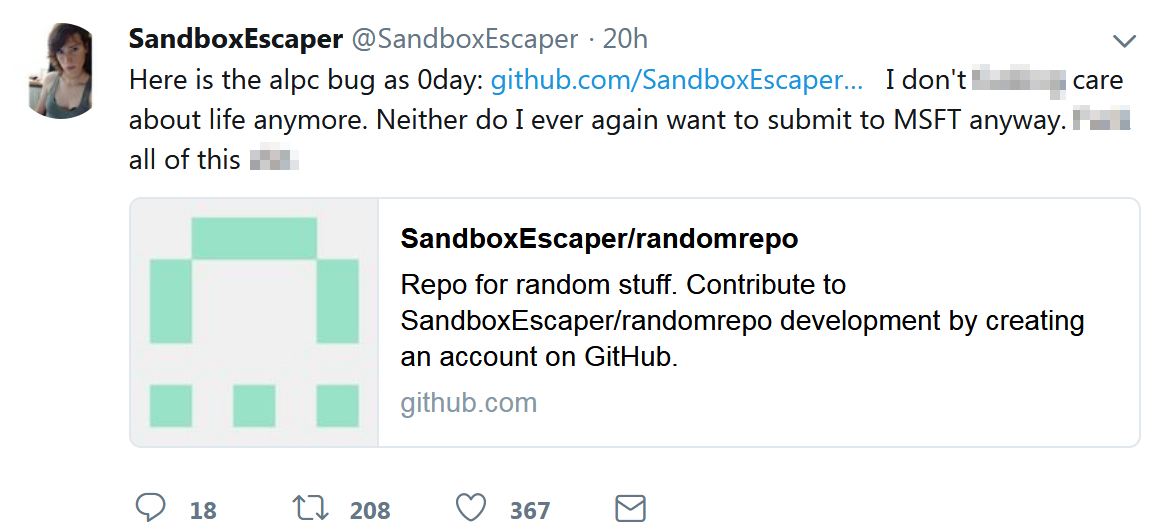
Vulnerability details
This public exploit impacts the Advanced Local Procedure Call (ALPC) interface in the Microsoft Windows Task Scheduler. It has been verified by Tenable and Will Dormann from CERT Research to work on fully patched Windows 10 and Windows Server 2016 systems. Because exploits like this are extremely dangerous in the wrong hands, Microsoft maintains a bug bounty program and has been known to pay researchers handsomely for responsible disclosure.
Impact assessment
Security professionals should track this situation and respond as soon as a patch or mitigation is available. This exploit not only gives standard Windows users the ability to raise their privileges, but malware authors will no doubt be leveraging this capability to enhance their toolkit.
Urgently required actions
Users should remain alert and use security best practices such as a robust password policy, malware mitigation, access control and network segmentation. Apply Microsoft patches as soon as they become available. Monitoring for unusual processes on the system, as well as anomalous behavior of users, might also help identify compromised systems.
Tenable is closely monitoring this situation and will provide updated protection as soon as patches become available.
Learn more:
Learn more about Tenable.io, the first Cyber Exposure platform for holistic management of your modern attack surface. Get a free 60-day trial of Tenable.io Vulnerability Management.
