When Host Security Falls Down

In today’s chess game of malware author versus network defender, often times the last line of defense is the target itself—your security application. Malware that specifically targets host security applications has been on the rise for the last ten years.
Malware that specifically targets host security applications has been on the rise for the last ten years.
This type of attack—disabling host security products, including anti-virus software—has been one of the most successful strategies used by malware. While some anti-virus software has its own control panel for managing host security, reports from the software can be spoofed back to end users and system administrators. With more recent malware, the host protection isn’t completely removed—it is disabled—so that central monitoring software doesn’t alert on missing or non-responsive security software. Cases like this have led to infections being on a network for prolonged periods of time, even years. Essentially, this becomes a security administrator’s nightmare; they have reported that everything is fine according to the reports coming from the security applications, and they have followed best practices and due diligence, yet the system seems to have failed them.
The attackers
Today’s threats are being created by organizations such as nation states and organized crime groups, with massive resources behind them. These groups perform a professional-style software development cycle, including QA, against known host security products. By knowing this, we also know that the adage “time favors the attackers” applies. If we can’t trust our own security software to report honestly to us, how can we state with certainty that we are compliant and performing our due diligence?
Redundancy
Many early practitioners of network security have long advocated for redundancy. This can be difficult in a time when we’re expected to do more with less and have tighter budgets, but there are tools available that can complement and augment existing traditional host security products. Some of these tools may already be in your environment.
Tenable solutions
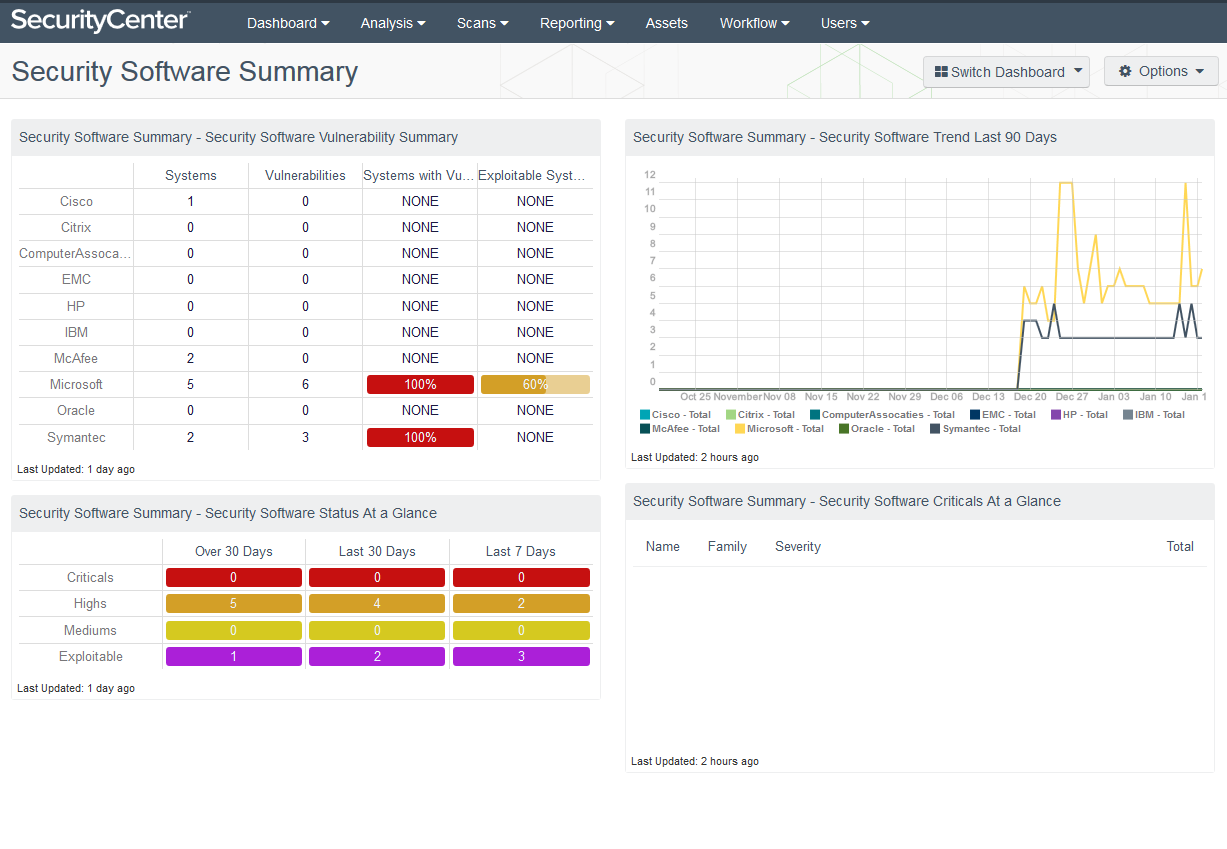
The short answer to attacks against host security products is to have an independent off-host sanity check of host security software. By doing this, we are getting a “second opinion” on the software status and validating the findings of organic reporting provided by the products’ consoles. Tenable’s SecurityCenter™ includes a dashboard that provides a Security Software Summary:
You will notice that this dashboard is not limited to the Host Security family; it includes other security software as well. In the example above, Microsoft and Symantec host security software are covered, both reporting in with 100% compliance. The dashboard also includes other security applications, such as Trend Micro, McAfee, BitDefender, Sophos and more. If you have already verified that the console reports are accurate, you get a “second opinion” here to corroborate the results and provide peace of mind – malware hasn’t infected these apps.
While we’ve talked about SecurityCenter so far, Nessus® also enables validation and has been written about twice before on the Tenable Blog by Ron Gula:
While some anti-virus products have been added to the checks performed by Nessus since those blogs were written, the method for leveraging Nessus has not changed.
You can find greater detail about using Nessus and SecurityCenter to validate your anti-virus posture and other malware hunting techniques in Tenable’s Whitepapers library. Whitepapers help you delve deeper into our solutions and even discover ways to use our software that you wouldn’t normally imagine.
Staying out of the news
Not only do we need to monitor logs and reports from our security software, we need to monitor the software itself.
With the sophistication of threats constantly changing and evolving, it is more important than ever that data security be a mesh of solutions supplementing and supporting each other. The time that we could design, deploy, and forget about security infrastructure is long past. Not only do we need to monitor logs and reports from our security software, we need to monitor the software itself. While malware and attackers would love to remove all instances of security software from our networks, by watching specifically for those attacks that disable the security products, organizations will remain out of the press for being the ones that had malware dormant on their systems for several years.
- Malware
- Threat Intelligence
- Threat Management
- Vulnerability Management