Twitter Crypto Scams: Bored Ape Yacht Club, Azuki and Other Projects Impersonated to Steal NFTs, Digital Currencies
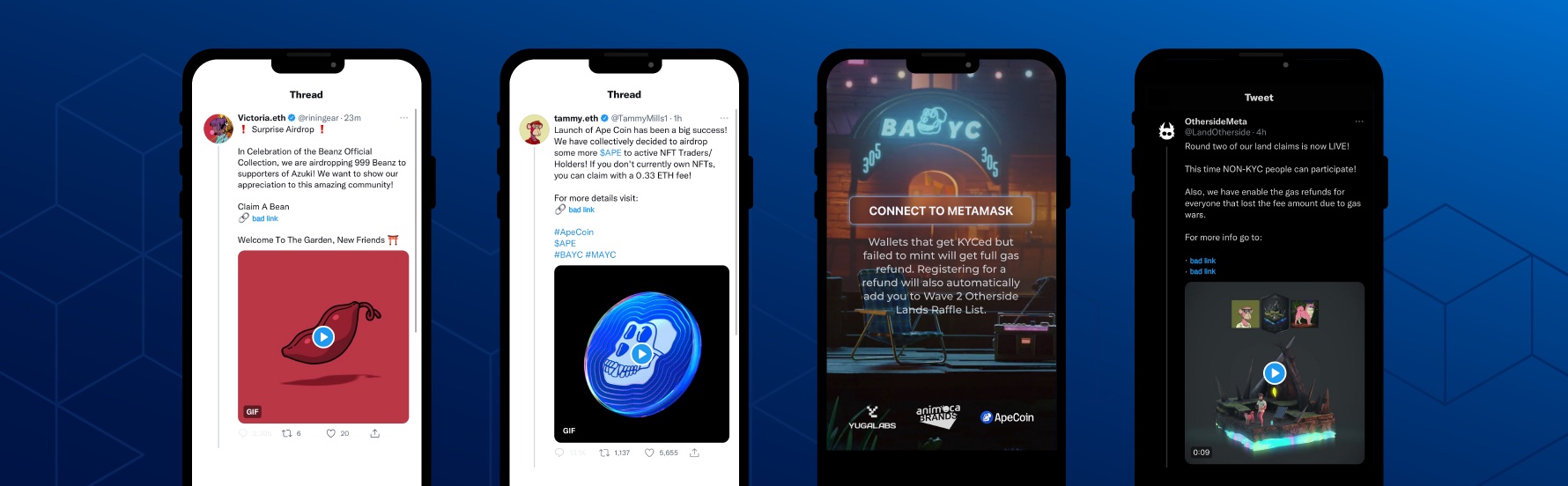
Scammers are using verified and unverified accounts to impersonate notable NFT projects like Bored Ape Yacht Club and others, tagging Twitter users to drive them to phishing websites.
Background
Over the last few months, a variety of non-fungible token (NFT) projects including Bored Ape Yacht Club (BAYC), Azukis, MoonBirds and OkayBears have been impersonated on Twitter in order to steal users’ NFTs and digital currencies like Ethereum and other altcoins. To create hype, many of these projects have been promoting upcoming integrations with their own metaverses, giving scammers ample opportunity to capitalize on new or rumored announcements in association with these projects.
Cryptocurrency scams on Twitter, which have been prevalent since at least 2018, have persisted on the platform through bull and bear markets. If there is one thing that is certain about cryptocurrency scams it is that scammers are determined to find creative ways to capitalize on the fervor in cryptocurrency and maliciously profit from it.
Scammers leverage Twitter mentions to capture attention
Recently, Twitter users with an interest in NFTs and cryptocurrency are likely to have received notifications in their Twitter Mentions. The cryptocurrency scammers are tagging users in replies across hundreds of tweets. By mentioning these Twitter usernames, they’re trying to pique their curiosity in a bid to trick some users into falling for their scams.
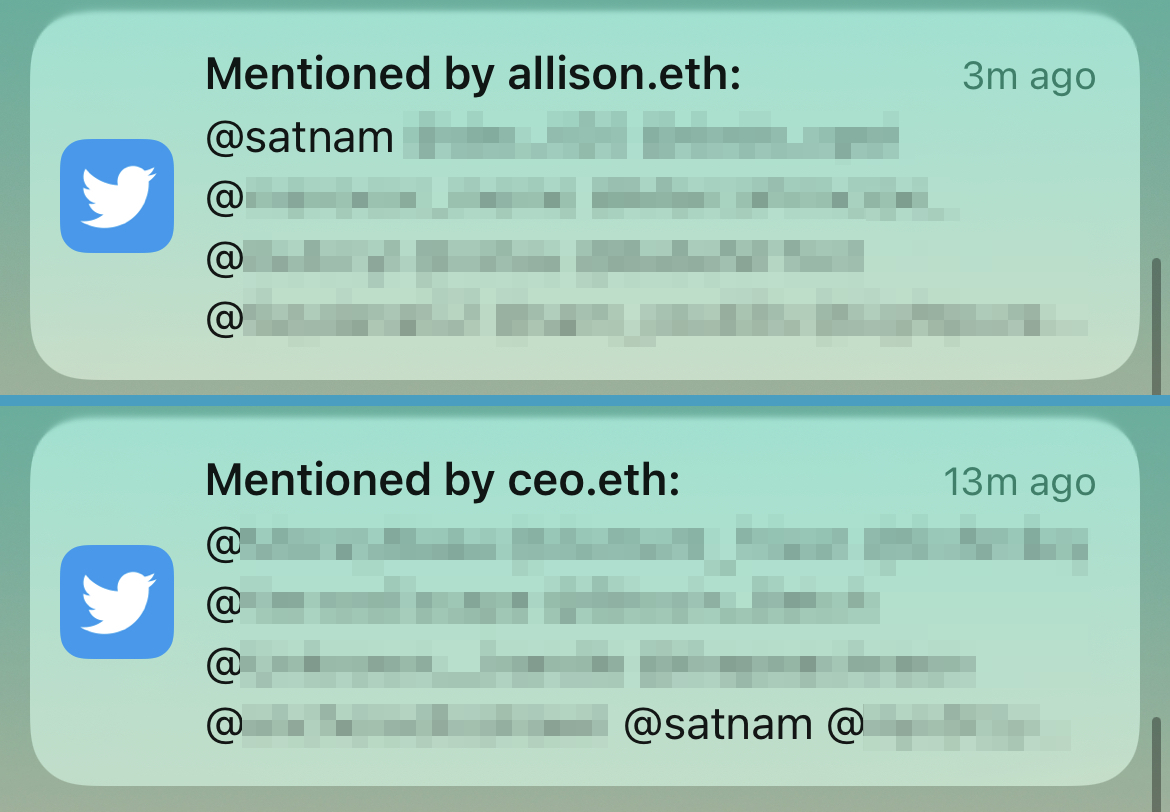
Image Source: Tenable, March 2022
Airdrops and free NFTs are the perfect vehicle for cryptocurrency scams
BAYC, one of the blue chip NFT projects in the space that has seen exponential growth since its launch in April 2021, announced earlier this year an Airdrop of ApeCoin to holders of its various NFT projects such as BAYC, Mutant Ape Yacht Club and Bored Ape Kennel Club. Naturally, scammers saw this announcement as a ripe opportunity to target the interest in this upcoming airdrop and began creating campaigns by hijacking verified Twitter accounts to drive users to phishing sites.
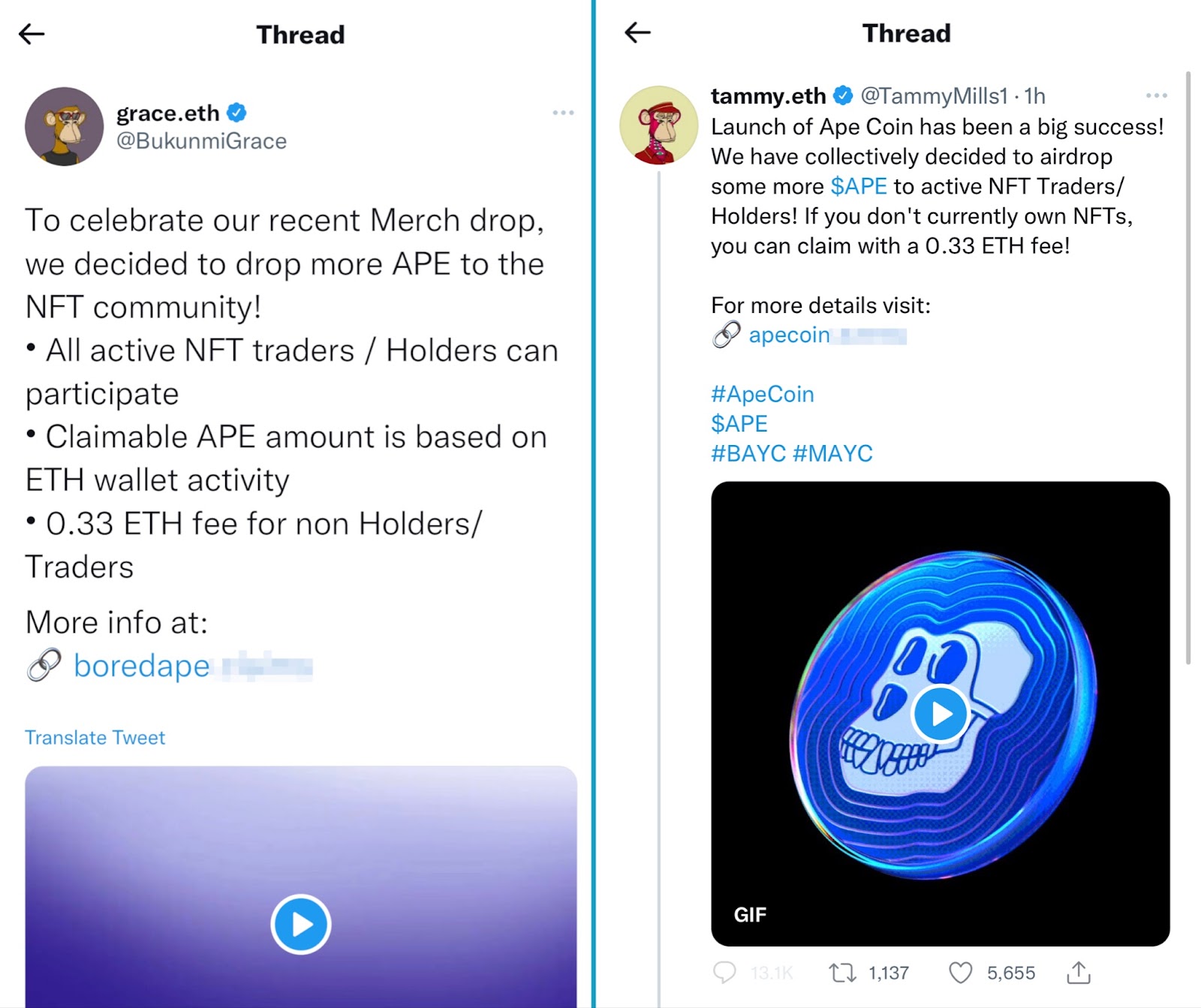
Image Source: Tenable, March 2022
These hijacked verified accounts were pivoted to use profile pictures (PFPs) of BAYC NFTs to lend legitimacy to their claims of airdrops of $APE tokens. Additionally, the scammers used these verified accounts to mention users en masse to capture their attention.
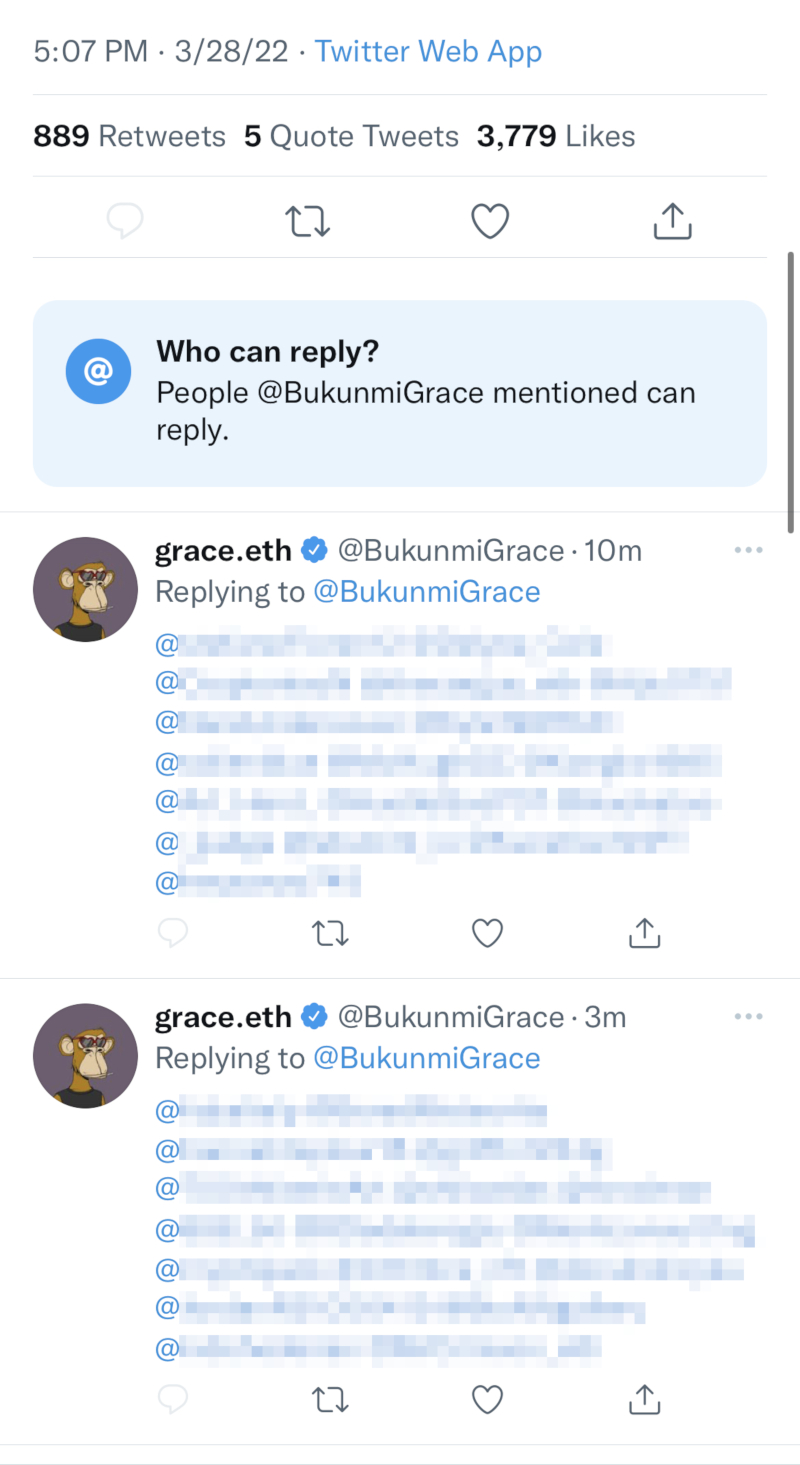
Image Source: Tenable, March 2022
Other noteworthy NFT projects impersonated
Besides BAYC, scammers have been impersonating a variety of other notable NFT projects including Azukis, Moonbirds, Invisible Friends and emerging projects on the Solana blockchain like OkayBears.
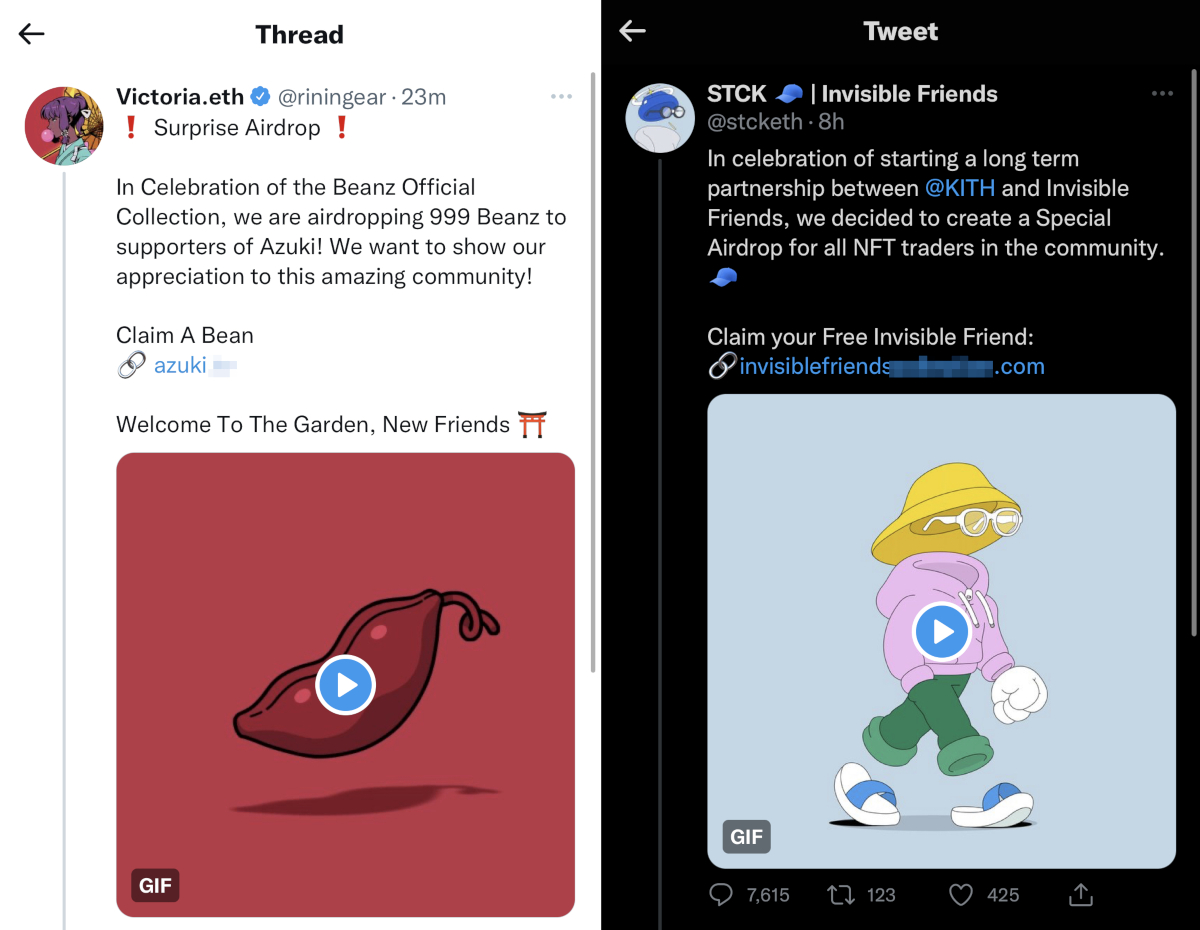
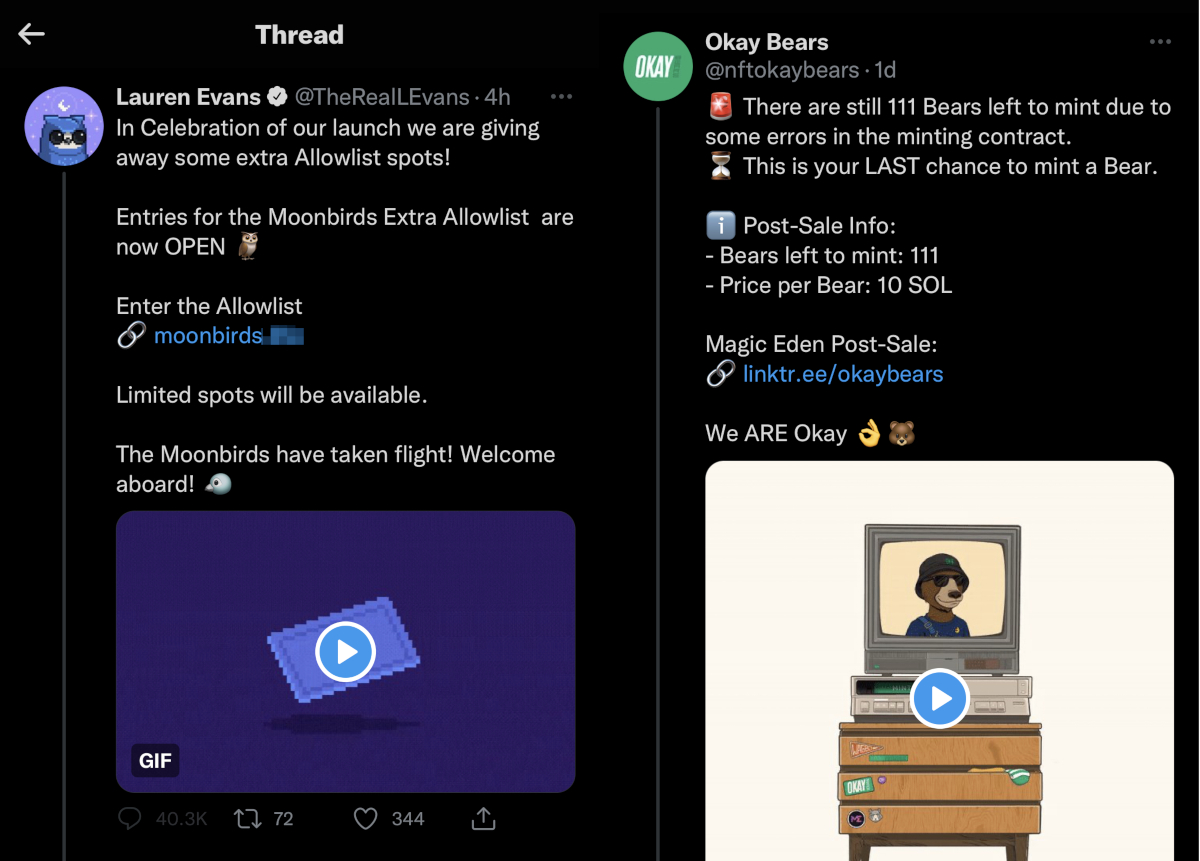
Backlash of BAYC’s Otherside Metaverse launch leveraged by scammers
On April 30, Yuga Labs launched its Otherside metaverse project, a way for BAYC NFT holders to purchase deeds (“Otherdeeds”) of land in their metaverse. This launch overwhelmed the Ethereum network, resulting in high gas fees for enthusiasts trying to mint a piece of land in the metaverse. This led to significant backlash from some of the project’s most vocal supporters. To capitalize on the frustration felt by these enthusiasts, scammers quickly moved to create fake OthersideMeta accounts on Twitter, promoting phishing pages not just for minting Otherdeeds, but also pages for those wanting to get a refund of the excessive gas fees they paid attempting to acquire the Otherdeeds.
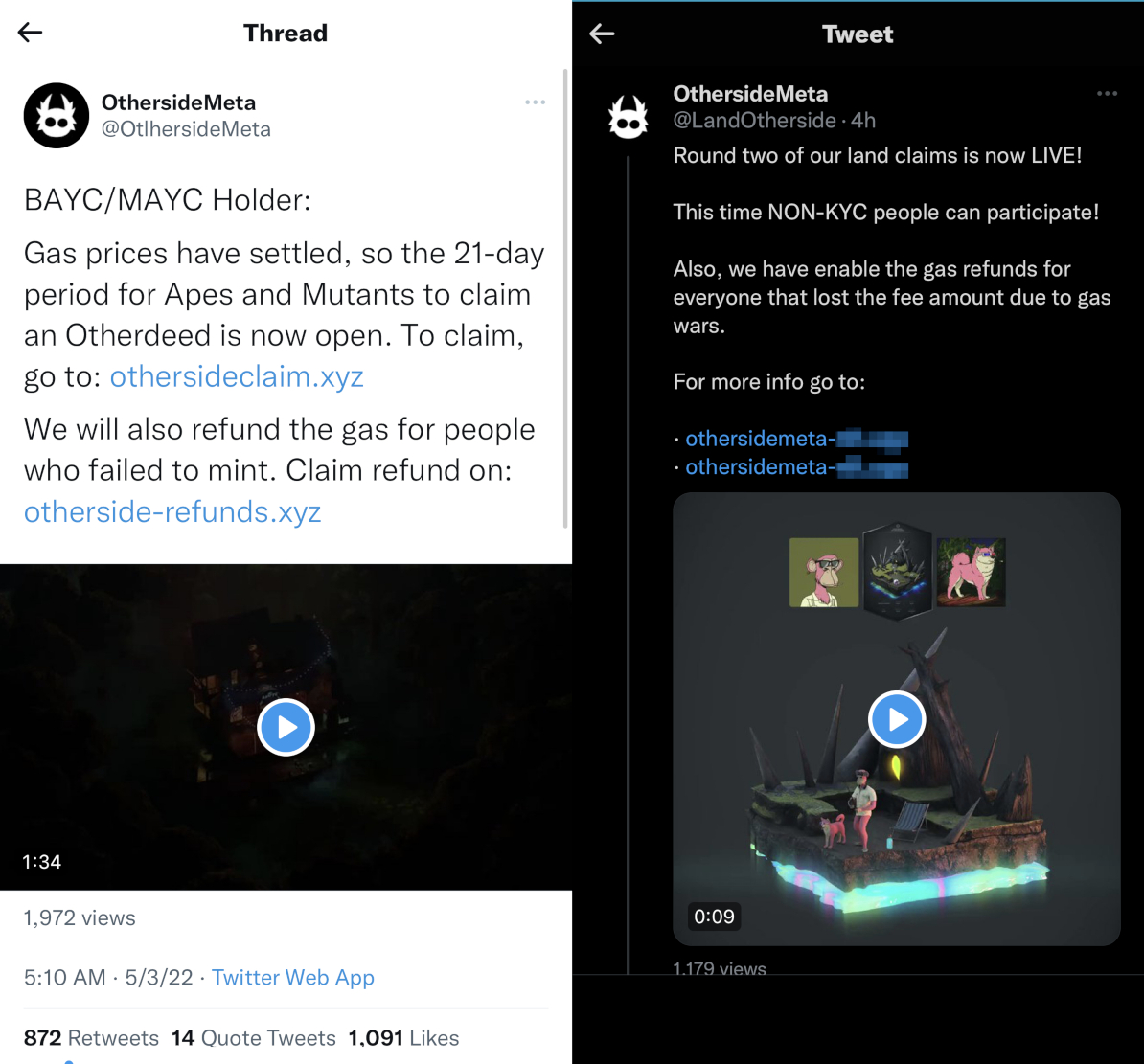
Image Source: Tenable, May 2022
Scammers ironically warn of scammers, use fake accounts to add legitimacy to tweets
Conveniently, scammers will use the threat of potential scammers as justification for why they “clean” or “close” comments or replies to their tweets.
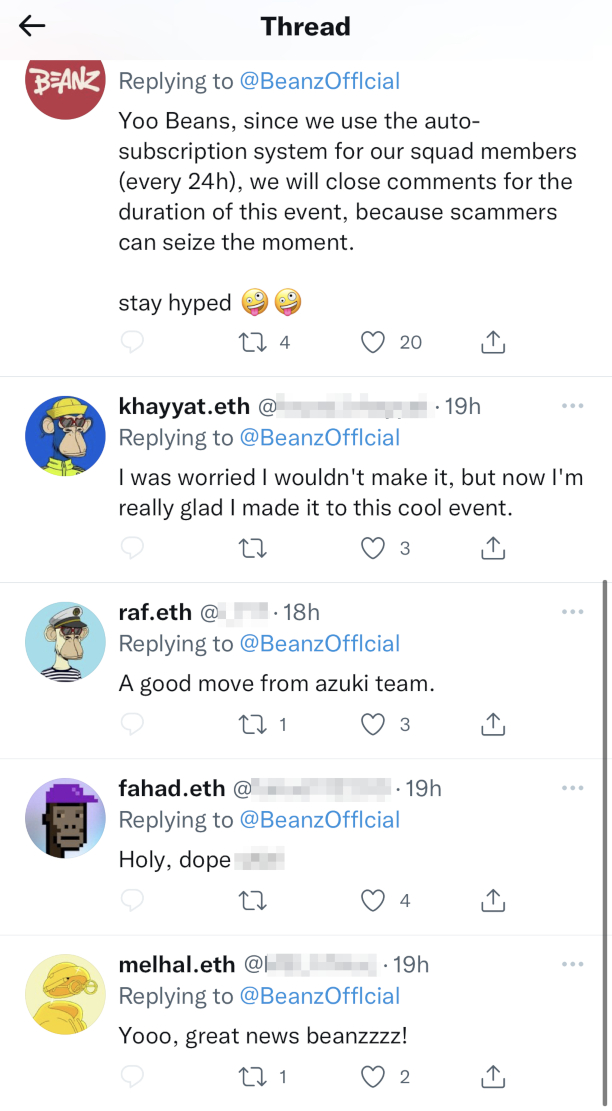
Image Source: Tenable, April 2022
They then leverage fake accounts that respond to the tweet to make it appear legitimate. Once they’ve seeded a few of these fake tweets, they leverage a built-in Twitter feature for conversations to restrict who can respond to their tweets, which prevents users from warning others of the potential fraud that lies ahead.
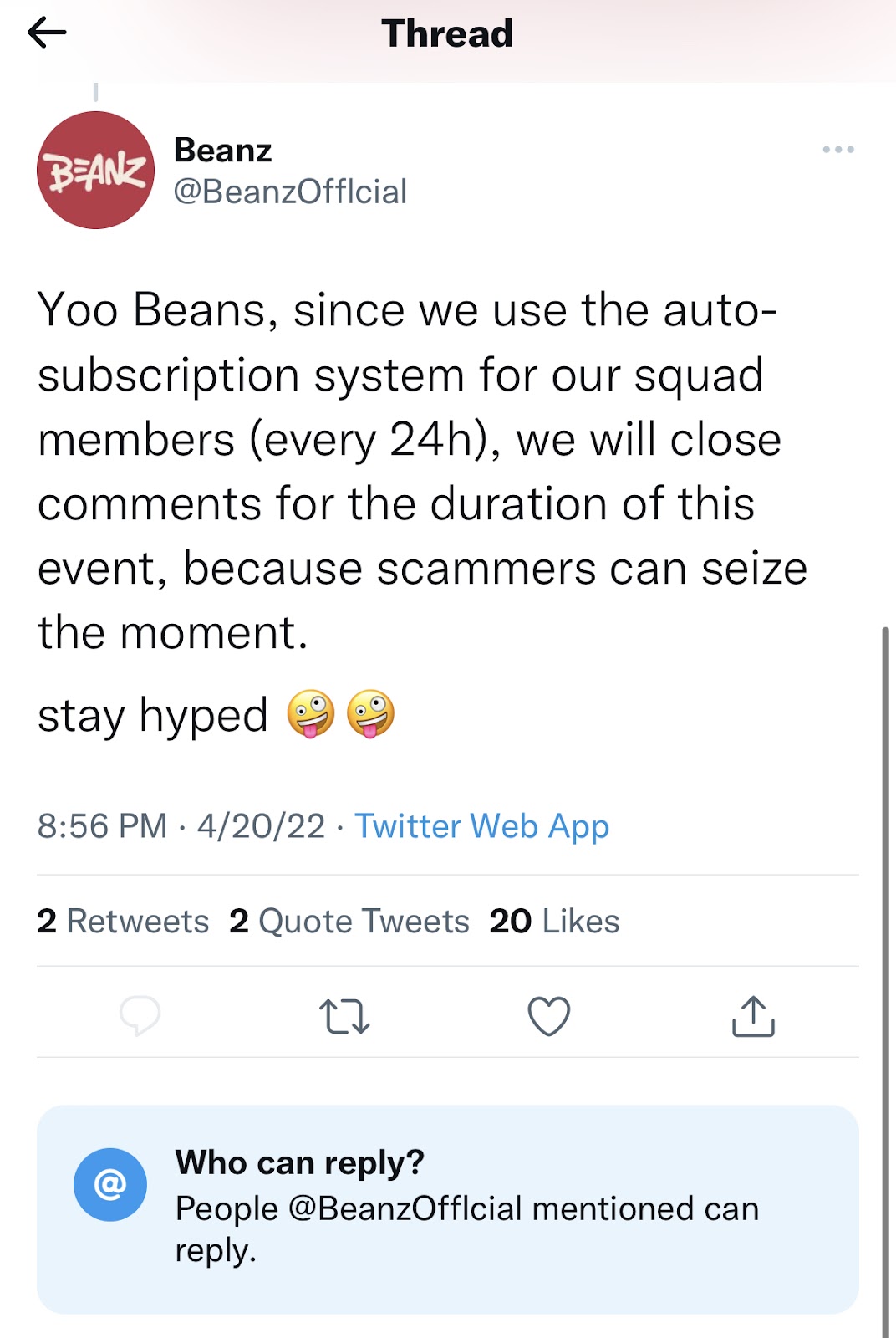
Image Source: Tenable, April 2022
Phishing sites are indistinguishable from the legitimate NFT project sites
The scammers leverage assets from the legitimate NFT project sites in order to craft their phishing sites, which would make it difficult for the average cryptocurrency enthusiast to tell them apart.
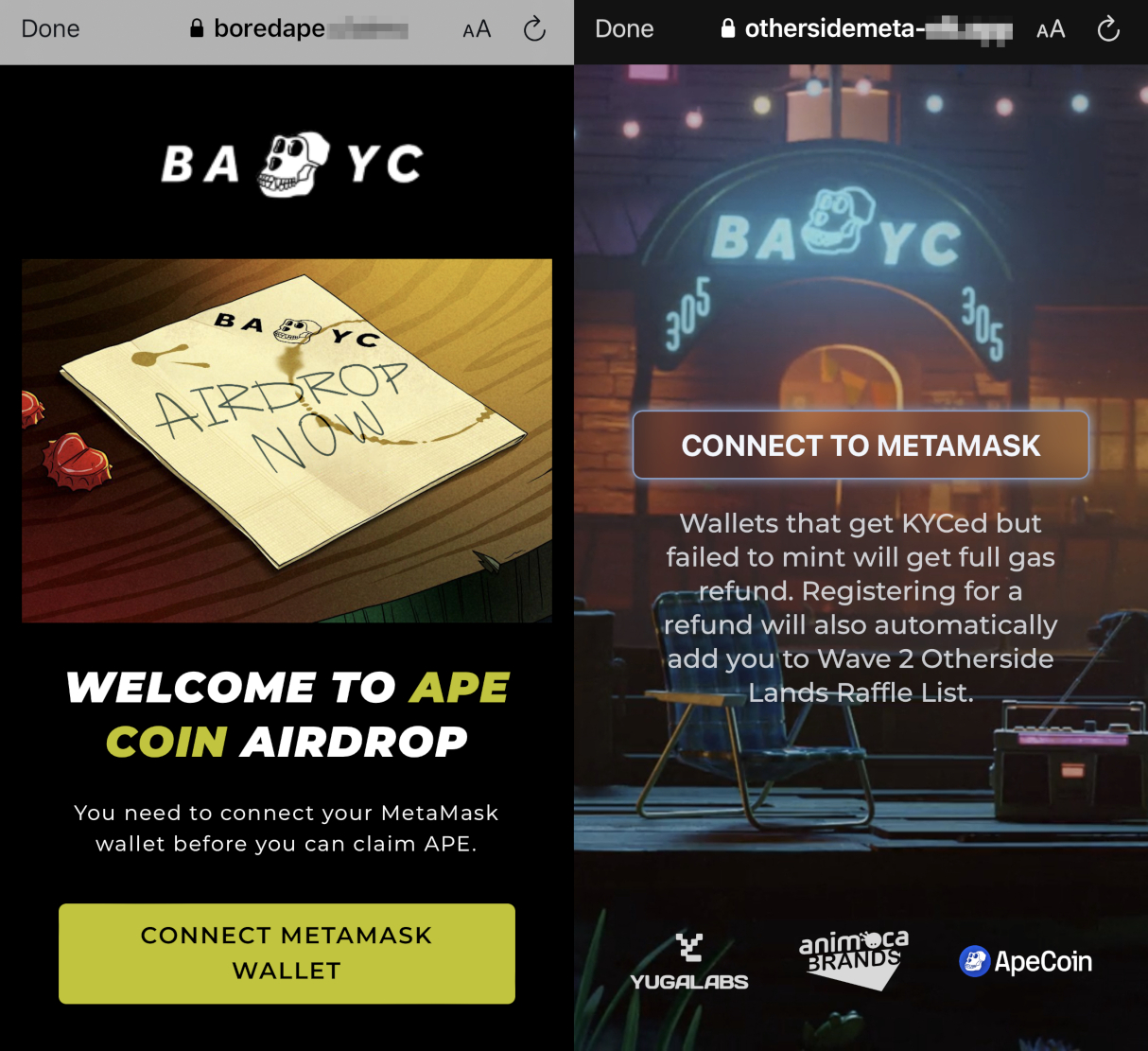
Image Source: Tenable, May 2022
The scammers will also use popular services like Linktree to drive users to fake pages mimicking NFT marketplaces like OpenSea and Magic Eden.
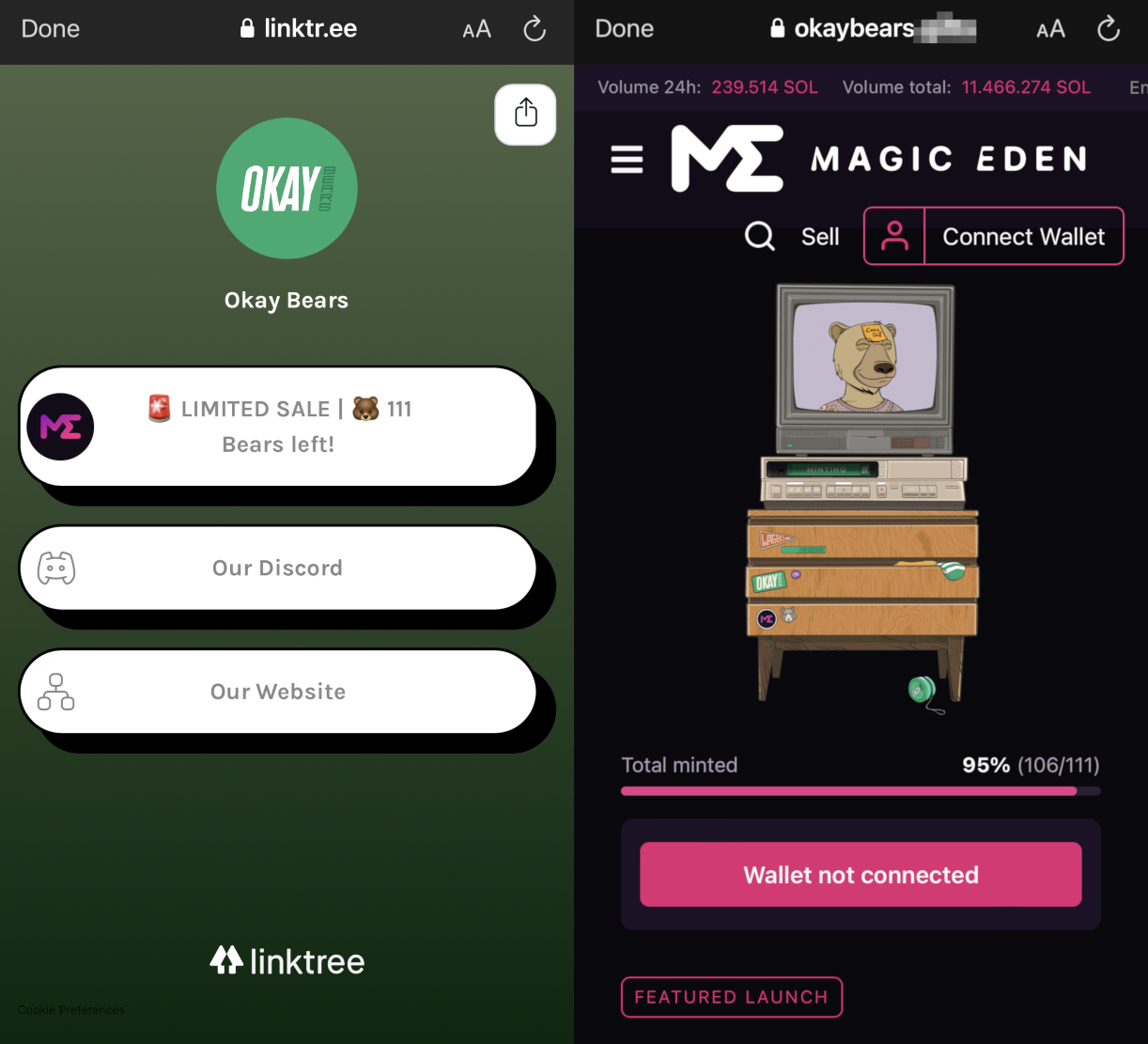
Image Source: Tenable, May 2022
Connecting your wallet to untrusted sites is a dangerous prospect
These phishing sites don’t rely on stealing users’ traditional usernames and passwords. Instead, they seek to convince users to connect their cryptocurrency wallets, typically browser-based wallets such as MetaMask or Phantom (Solana) to the phishing sites. Unsuspecting users explicitly need to grant these phishing sites permission to access their wallets. By doing so, scammers are able to then transfer out the digital currencies like Ethereum ($ETH) or Solana ($SOL), as well as any NFTs being held in these wallets.
These NFT-based scams are extremely successful
A fellow researcher who goes by the pseudonym Zachxbt recently noted that the BAYC Otherside phishing sites were so successful that they were able to locate three cryptocurrency addresses that had stolen several NFTs from Mutant Ape Yacht Club (MAYC), BAYC, Azuki and others to the tune of $6.2 million dollars.
1/ As we all anticipated Otherside phishing sites would appear
— ZachXBT (@zachxbt) May 1, 2022
Today 0xb87 stole $1.03m (369 ETH) worth of NFTs. Most notably 4 MAYC, 1 BAYC, & 30+ SandboxNFT
This lead to 0xa8 & 0x5d which have $5.1m worth of stolen NFTs! 4 BAYC, 19 Azuki, 2 MAYC, 2 WOW & more
$6.2m in total! pic.twitter.com/FbzxoXWEC8
The NFT scammers Twitter playbook
The projects impersonated here are just the few examples I’ve encountered over the last few months. However, future NFT projects or announcements from existing projects that have yet to launch or have launched recently will likely be capitalized by scammers following the same playbook:
- Hack or purchase a verified Twitter account or an account with hundreds of thousands of followers
- Pivot the account to impersonate notable NFT projects or their members by using PFPs and other images from the project
- Tweet about upcoming or recently held airdrops or mints for the projects with links pointing to phishing websites
- Tag users directly from the impersonated account or utilize an army of fake accounts to tag users across hundreds of tweets
- Wait for users to click on the phishing links and grant access to their cryptocurrency wallets in order to begin stealing NFTs and digital currencies
There may be some slight variations to the steps above, such as compromising the Twitter account of an existing figure within the cryptocurrency space, but chances are they will continue to use the same approach until something disrupts the playbook.
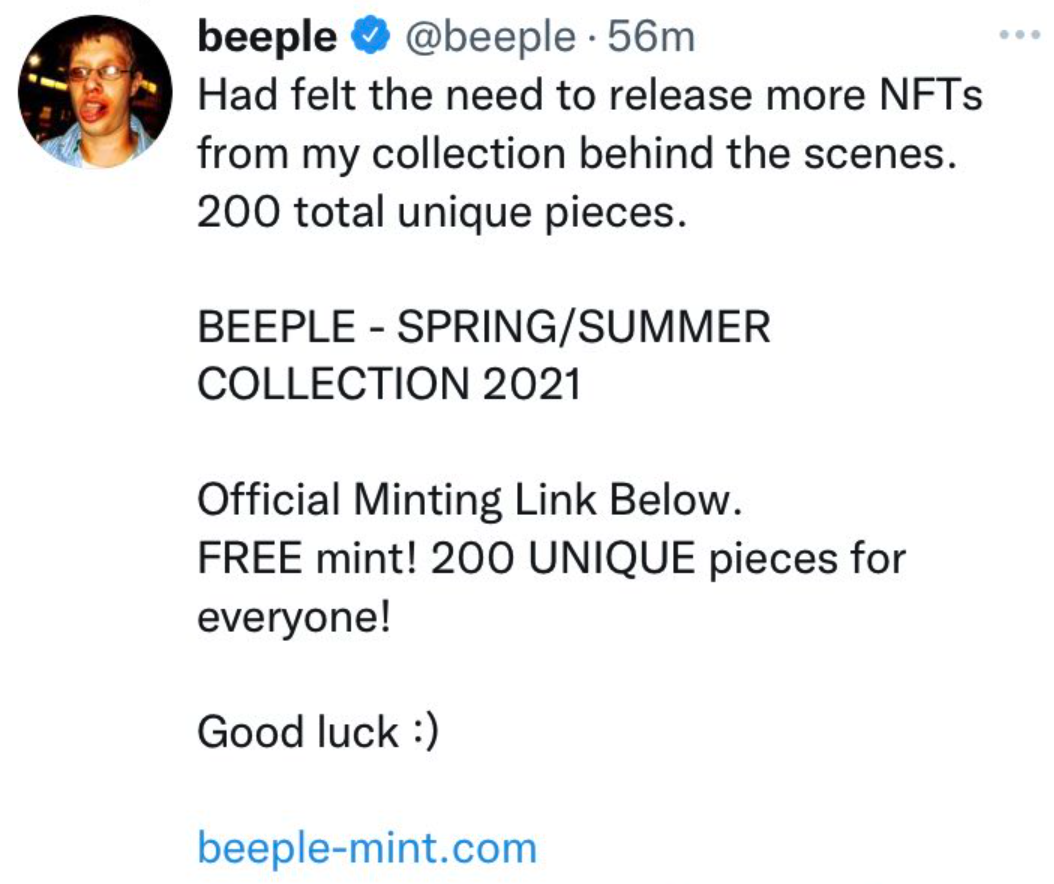
Twitter account for digital artist Beeple was hacked to promote a phishing scam
Image Source: xBenJamminx (Twitter)
How Twitter could curtail many of these NFT cryptocurrency scams
There are a few ways Twitter could intervene to make things harder for scammers when it comes to these impersonations.
- Make the NFT profile pictures feature available to all users instead of just to paying members of Twitter Blue. Because blockchains are meant to help provide a way to verify trust, allowing everyone to utilize this feature will provide a mechanism by which users can verify the authenticity of the tweets from someone using a BAYC profile picture.
- Temporarily hide tweets and profiles for verified accounts that change their profile pictures and names. Scammers that successfully hijack verified Twitter accounts will pivot them to brands, notable individuals or NFT projects. By temporarily hiding these tweets and profiles when they make such a change to their profiles, Twitter would give its abuse team a chance to manually review these changes before the scammers wreak havoc.
- Create warnings for profiles and links shared by verified Twitter accounts that recently changed their names and profile pictures. If #2 is not feasible, then put up a roadblock that creates warnings for end users when they are tagged in tweets from newly updated verified profiles or in the links that have been shared. Use transparency to help inform end users. Since Twitter accounts are tagged by a user_id, add a warning bubble next to a tweet saying “This profile recently changed its name and profile photo from (x) to (y). If this profile seems suspicious, report the account.”
- Watch for signals such as mass tagging on tweets. To gather the attention of users, the scammers are relying on tagging many users in replies to tweets. If a tweet begins to receive replies that are tagging multiple users, flag the original tweet/account and subsequent replies as suspicious. Twitter “canoes” – as they were once referred to – are anomalous, so such replies, even if from a number of Twitter accounts not related to the original tweet, should be another potential signal for flagging.
Twitter users interested in cryptocurrency need to remain skeptical
It’s a common refrain from me, but operating from a place of skepticism is likely going to provide some cover for users when it comes to such scams. If you’re proactively tagged in a tweet, you should be highly suspicious of the motivations behind it, even if it comes from a verified Twitter account. Seek out the original project’s website and cross-reference links that you see being shared on Twitter with the ones on their official website. Scammers will also rely on urgency to try to add pressure to users in this space. If an NFT mint is happening, they’ll say that there are a limited number of spots left. This urgency makes it easier to take advantage of users not wanting to miss out on the opportunity.
Much of the advice here is temporarily valuable because ultimately, scammers in this space are crafty and will continue to innovate their way into your MetaMask or other cryptocurrency wallets, which is why the oldest but most salient idiom remains valid: if it sounds too good to be true, it is.
Ulteriori risorse
- Elon Musk and SNL: Scammers Steal Over $10 Million in Fake Bitcoin, Ethereum and Dogecoin Crypto Giveaways
- Cryptocurrency Scams: Fake Giveaways Impersonate Followers of Political and Other Notable Figures
- Fake Bitcoin, Ethereum, Dogecoin, Cardano, Ripple and Shiba Inu Giveaways Proliferate on YouTube Live
