The OPM Breach Two Years Later: Why We Need a Marathon

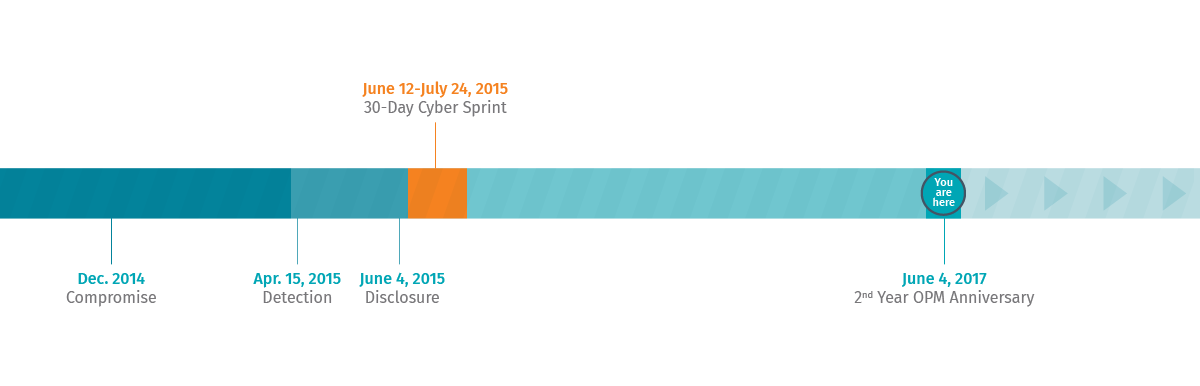
The White House called for a 30-day sprint in response to the devastating data breach at the Office of Personnel Management (OPM), discovered in April 2015. The immediate goal was to bring agencies’ cybersecurity up to an acceptable level. It directed agencies to implement a number of best practices, including scanning systems for known threats, patching critical vulnerabilities, managing privileged access and using multi-factor authentication. But is a sprint enough?
Two years after the breach, which exposed sensitive records and personal information of 21.5 million past, present and potential federal employees, the OPM Inspector General still found the agency was struggling to meet cybersecurity requirements. OPM is not the only agency facing these challenges. The Government Accountability Office has classified federal cybersecurity as a high-risk program for 20 years.
To address today’s cybersecurity challenges, the government needs a marathon
A sprint is fine if you need to quickly meet a short-term goal, but that’s not how the government or the world should be thinking about risk or security. To address today’s cybersecurity challenges head on, the government needs a marathon. Without a resilient and comprehensive cybersecurity strategy, agencies will struggle to understand their true level of exposure and to reduce their risk.
The changing world
The federal government is frequently criticized for maintaining legacy IT systems. The House Oversight Committee last year called agencies’ reliance on outdated and unsupported technology “a ticking time bomb.” Alongside these legacy systems, agencies are adopting new computing assets like cloud, DevOps/containers and the Internet of Things (IoT) that are disrupting the traditional network perimeter to create a dynamic and boundaryless IT environment.
Alongside legacy systems, agencies are adopting new computing assets
Operational technologies (OT) like SCADA/ICS are still a major part of the government’s critical infrastructure, and while designed for precision and reliability, were not built with security in mind. The rise of industrial IoT means critical devices such as medical devices, transportation systems and ICS have become internet accessible.
This convergence of IT and OT is expanding the already complex attack surface, creating additional security risks and safety concerns for chief information security officers (CISOs) who already struggle to gain visibility into their exposure areas.
Real modernization
Real modernization requires change in how systems are architected
Agencies must modernize IT systems if they are to improve their cybersecurity. But modernization requires more than merely updating or replacing legacy systems with new products and services. Real modernization requires change in how systems are architected. The systems must provide administrators with the visibility to fully monitor all assets—whether on-premises or in the cloud—in as close to real time as possible. Administrators must be able to manage them and to respond quickly to vulnerabilities, threats and attacks. This requires interoperability and the use of automation where possible, so that administrators and security personnel can apply their human intelligence where it is most needed.
Modernization will be a big job for agencies. The GAO reported to the House Oversight Committee last year that agencies spent more than 75 percent of their fiscal 2015 IT budgets on legacy equipment. Some systems still are using COBOL (the Common Business Oriented Language) for computers developed in the late 1950s and early 1960s.
Replacing these antiquated systems would be a step forward in improving cybersecurity. But completing the task of modernization will require a long-term commitment to change and will be realized only if it is prioritized by agencies, legislators and the administration. Initiatives such as President Trump’s recent Executive Order on cybersecurity can help point the way to needed changes and strategic planning. The Modernizing Government Technology bill that has been introduced in Congress would help by establishing a capital fund to help agencies finance new technology. This could jumpstart the modernization process and make it easier for agencies to make long-term plans and to respond quickly to evolving threats and technology.
Ultimately, each agency must establish and pursue its own strategic plans focusing on the long-term goal of manageable and secure information systems. Only then can the government be fully prepared to regain control of their networks and confidently manage cyber risk in today’s modern IT landscape.
More information
For more data about the OPM situation, visit the Tenable OPM web page and download the free whitepaper.
- Federal
- Government
- Security Policy