Tenable Responds to CVE-2015-0235: GHOST (Updated)

A major vulnerability was disclosed today in the GNU C Library (“glibc”). CVE-2015-0235, known as “GHOST” in the media, affects Linux systems that use versions of the library prior to glibc-2.18, which was released on August 12, 2013. The GNU C Library is commonly used for standard system calls by programs written in C and C++. The vulnerability is a heap-based buffer overflow which affects the gethostbyname() and gethostbyname2() glibc function calls. A remote attacker who is able to make an application call with either of these functions could use this flaw to execute arbitrary code with the permissions of the user running the application.
Update: Nessus plugins
Impacted operating system vendors are making updates available, and Tenable has released a series of local Nessus® plugins to detect the presence of affected versions of glibc:
| Distribution | Plugin |
|---|---|
| Amazon Linux AMI | 81024 |
| CentOS 5 | 81025 |
| CentOS 6 & 7 | 81026 |
| Debian 7 | 81029 |
| FreeBSD | 81062 |
| OracleVM 2.2 | 81119 |
| OracleVM 3.2 | 81118 |
| OracleVM 3.3 | 81103 |
| Oracle Linux 4 | 81099 |
| Oracle Linux 5 | 81044 |
| Oracle Linux 6 & 7 | 81031 |
| Red Hat Enterprise Linux 4 | 81104 |
| Red Hat Enterprise Linux 5 | 81033 |
| Red Hat Enterprise Linux 6 & 7 | 81034 |
| RHEL 5.6/5.9/6.2/6.4/6.5 Long Life/Advanced Support/Extended Support | 81068 |
| Scientific Linux 5 | 81037 |
| Scientific Linux 6 & 7 | 81038 |
| Slackware 13.0/13.1/13.37/14.0/14.1/current | 81075 |
| SUSE Linux Enterprise 11 | 81039 |
| Ubuntu 10.04 & 12.04 | 81042 |
You can also watch a video about Detecting GHOST with Nessus.
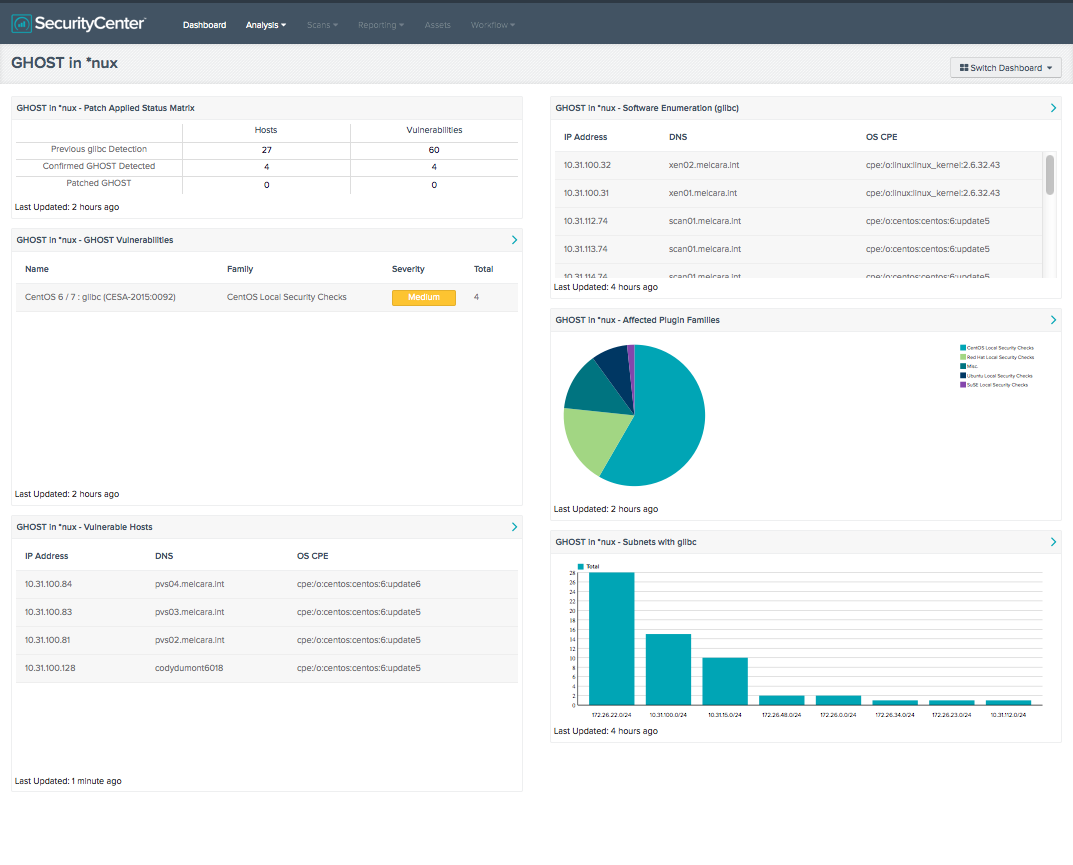
Update: SecurityCenter dashboard
A customized SecurityCenter™ dashboard to monitor, track and remediate critical assets affected by CVE-2015-0235 is available via the feed to provide insight on the impact to your environment and the progress of your efforts to remediate the issue.
You can also watch a video about Detecting GHOST with SecurityCenter.
This blog will be updated as events occur. And visit Tenable's GHOST Vulnerability page for more information.
- Dashboards
- Nessus
- Plugins
- SecurityCenter