Tenable Research Discloses Multiple Vulnerabilities in Plex Media Server

Tenable Research discovered multiple vulnerabilities in Plex Media Server, a popular media streaming and sharing service, that could allow attackers to gain full system privileges and access to personal files. Plex has since administered patches and mitigations for these vulnerabilities.
Background
Tenable Research has disclosed three vulnerabilities in Plex Media Server, affecting versions prior to 1.18.2. The Plex application and service allows users to organize and stream their own media through a Netflix-like experience. Users can share personal media libraries among friends and discover related content from traditional streaming sources around the web. This type of service is very popular as people are homebound due to public health orders.
Vulnerabilities
CVE-2020-5742
This vulnerability is due to a weak cross-origin resource sharing (CORS) policy. The attacker would likely exploit this vulnerability through phishing. Since Plex users often share their media by way of email notifications, these phishing attempts may see higher than average success rates. After clicking through to the login screen, users cannot tell if they’re logging into their own Plex server or the attacker’s. Once the victim has logged into the attacker’s media server, the attacker can forge requests to the victim’s media server. For example, the attacker could download a private photo album from the victim’s server. This vulnerability impacts Windows, macOS and Linux versions.
CVE-2020-5741
Once a Plex user’s media server is exposed due to CVE-2020-5742, the attacker obtains access to an admin authentication token that would allow them to execute arbitrary code remotely with the same privileges as the media server. From there, the attacker could pivot to other machines on the network or install backdoors. This vulnerability impacts Windows.
CVE-2020-5740
This is a local privilege escalation to SYSTEM. Once the attacker has gained code execution, they would be able to exploit this vulnerability to elevate their privileges to the highest level. This vulnerability impacts Windows.
Attack Scenarios
By chaining these three vulnerabilities together, an attacker can move from a successful phishing attack to full SYSTEM privileges. To understand more about the technical details of how an attacker might chain this attack, read here.
With SYSTEM privileges, the attacker would have unlimited access to the underlying operating system and any local files. If the attacker was only able to get far enough in the chain to exploit CVE-2020-5741, they could still access the underlying operating and file system, but their level of access would be limited to the privileges of the compromised account.
Even if the attacker only exploits CVE-2020-5742 via phishing, they would still be able to access any media and services on the Plex media server. This is more concerning than a compromised Netflix account, since users store personal pictures, videos and audio files on Plex.
Vendor Response
Plex has released patches for CVE-2020-5740 and CVE-2020-5741 in a rolling process. Users should update to the latest version to address these two vulnerabilities. Plex Media Server will not automatically update by default but users can enable this within their settings. Users can always check the general settings page to see if new updates are available.
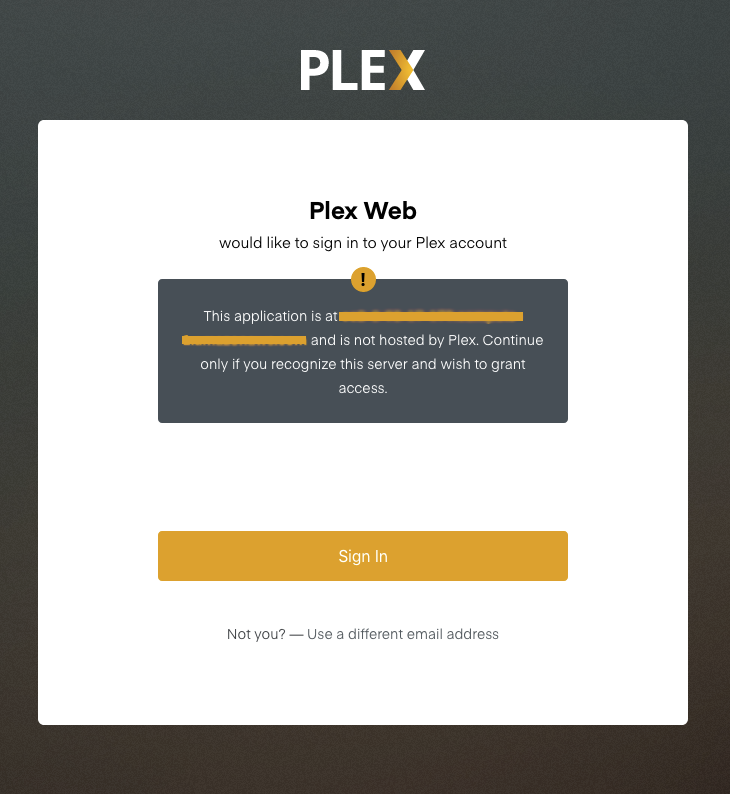
Plex also administered a mitigation for CVE-2020-5742 that alerts users when they are logging into a server that is not hosted by Plex.
Tenable has published plugins to detect vulnerable instances of Plex Media Server.
Get More Information:
- Visit the Tenable TechBlog on Medium to read more about researcher Chris Lyne's work uncovering these vulnerabilities.
- Tenable Research Advisory: CVE-2020-5740
- Tenable Research Advisory: CVE-2020-5741
- Tenable Research Advisory: CVE-2020-5742
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning

