Tenable Integrates with AirWatch
Organizations have adopted mobile devices as essential part of their business and rely on MDM solutions like AirWatch to track and manage them as well as certain applications that run on them.
Both Nessus and SecurityCenter now integrate with the AirWatch Mobile Device Management (MDM) platform to pull in mobile device information and provide context to vulnerability data. This helps identify vulnerable mobile devices and prioritize the overall risk they pose to the organization. With this integration, Tenable now supports all major MDMs including Microsoft Exchange, Apple Profile Manager, Good for Enterprise, MobileIron, and now AirWatch.
Integration Benefits
The integration with AirWatch extends Tenable’s initiative to bring mobile device visibility and vulnerability assessment together to allow organizations to better capture and prioritize the risk that mobile devices introduce and to improve their overall security and compliance stature.
Tenable and AirWatch customers can connect Tenable solutions to the AirWatch on-premises or cloud-based MDMs and receive mobile device information including number of mobile devices, mobile device types, operating systems (OS), and more to assess risk.
The AirWatch integration identifies mobile devices that could not be captured during an active network security scan because the device was either not connected or was asleep. The integration takes the MDM information to feed Nessus and SecurityCenter’s auditing and security assessment. The information helps answer the following questions:
- Who and what types of devices are connecting to my network?
- Are the devices running vulnerable OS?
- Overall, how many such vulnerable devices connect to my network?
- Are there unmanaged devices connecting to my network?
AirWatch Background
Acquired in 2013 by VMware for $1.54 billion, AirWatch offers a complete MDM solution for managing mobile devices, applications, and content. It can be purchased as an on-premises or cloud offering and also offered within a suite that includes options such as application management, content management, and email management to name a few.
Configure in 3 Easy Steps
The configuration and setup of this integration is straightforward.
Step1: In the Nessus Policies tab, click “New Policy” and choose the “Mobile Device Scan” icon.
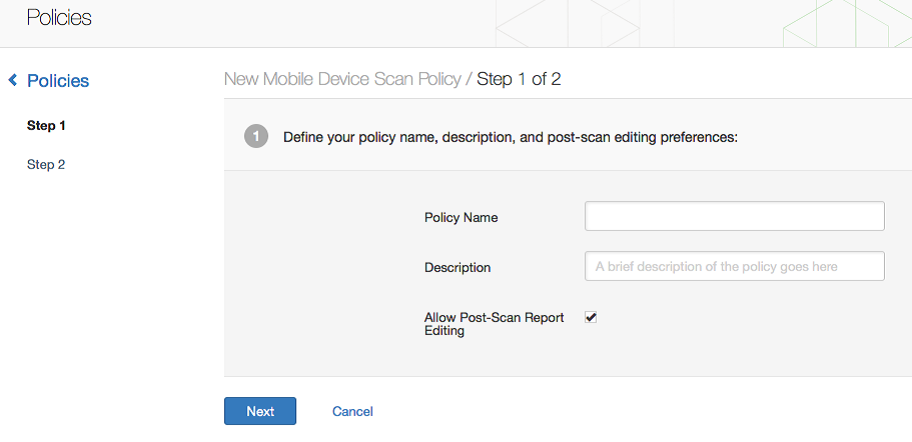
Step2: Enter a policy name, and click "Next".
Step3: Select "AirWatch" from the "Device managers" list, and fill in the required details.
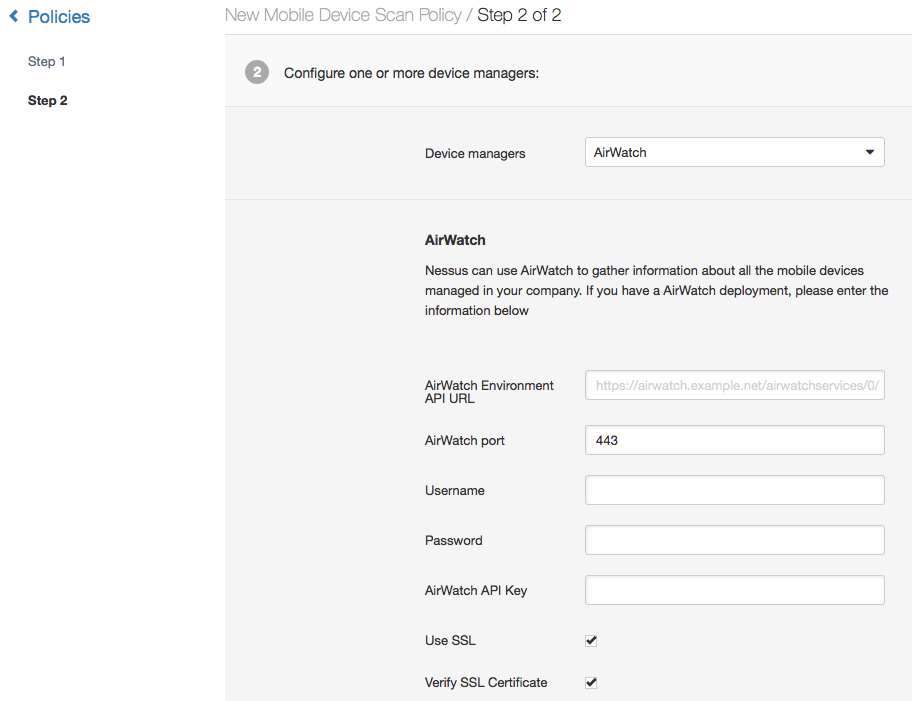
The integration allows Nessus to query the AirWatch API to gather information about all the mobile devices it manages. Using the credentials and the API key, Nessus authenticates to the server to directly query it for device information. This feature does not require any ports be specified in the scan policy. Optionally, communications over SSL can be specified, as well as verifying the SSL certificate.
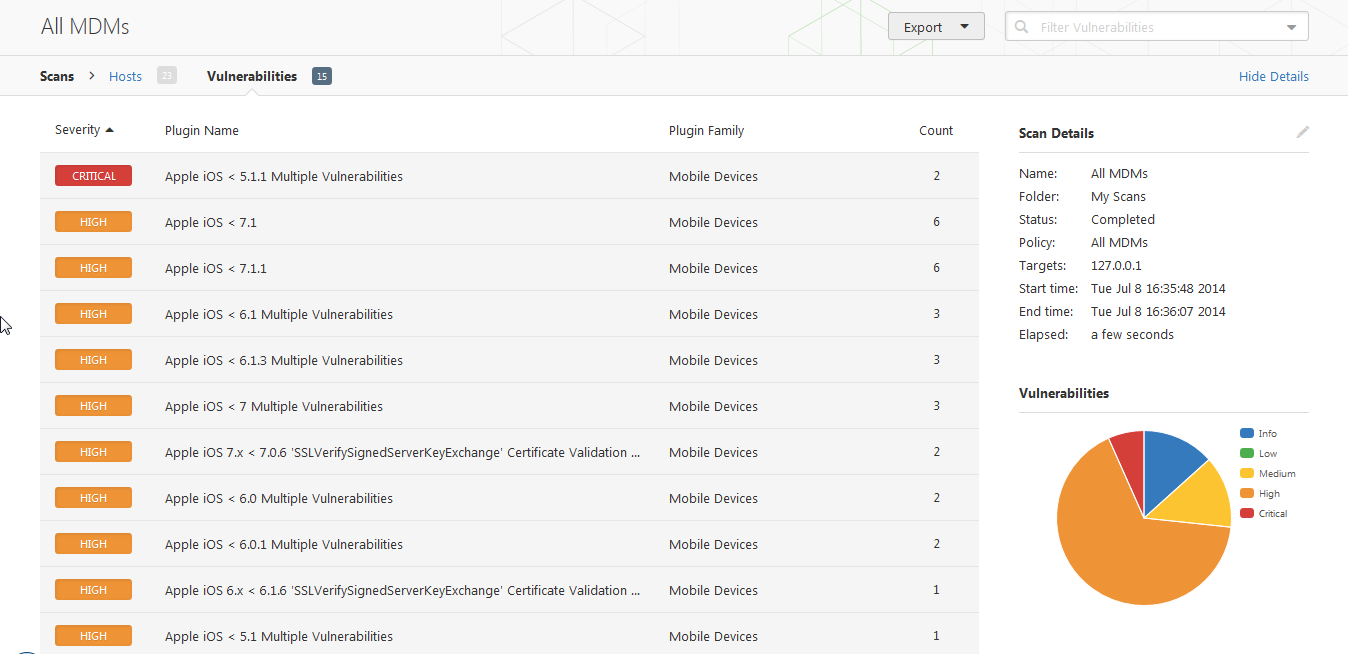
Resulting Output
The integration results can be viewed in the scan reports. Example excerpts from the reports are shown below highlighting detected vulnerable devices.
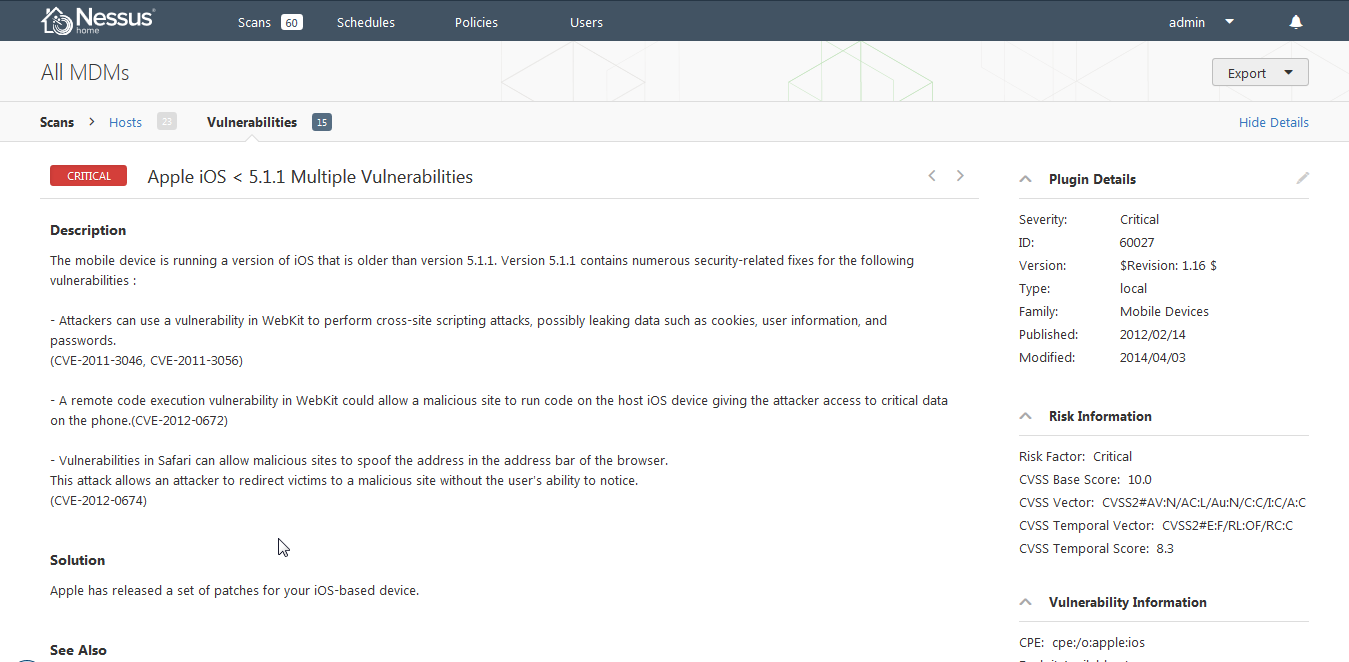
Learn more about how Tenable solutions aid in securing your mobile devices and infrastructure and learn more about Nessus.
Reference Gartner’s research “Four Ways to Close the Gap Between Enterprise Mobility and Vulnerability Management” for additional insight on mobile device assessment.
Implement Continuous Monitoring
For even more in-depth monitoring of mobile devices, vulnerabilities, and their interaction with the other assets in your environment, Tenable's SecurityCenter Continuous View provides continuous passive monitoring and log analysis that add additional insight into mobile devices. For example, without even scanning, SC CV identifies which mobile devices are connecting via passive traffic monitoring; it identifies what other systems vulnerable devices are communicating with, what applications they are communicating with, and what users are connecting to vulnerable assets. Learn more about SecurityCenter CV.
- Announcements
- Integrations
- Mobile Security
- Nessus
- SecurityCenter

