SecurityCenter: Leveraging Vulnerability Data Collection for Incident Response

Note: Tenable SecurityCenter is now Tenable.sc. To learn more about this application and its latest capabilities, visit the Tenable.sc web page.
Prioritizing threat management and vulnerability remediation may be seen as a roadblock to effective incident response (IR) preparation, but in reality the efforts assist each other quite well. Fortunately, you can use SecurityCenter Continuous View® (SecurityCenter CV™) to improve your threat mitigation and vulnerability remediation efforts while more effectively preparing for, detecting, and preventing incidents in your environment. The steps you take with SecurityCenter CV to detect and remediate vulnerabilities can enable you to effectively and efficiently respond to incidents.
Preparation and data collection
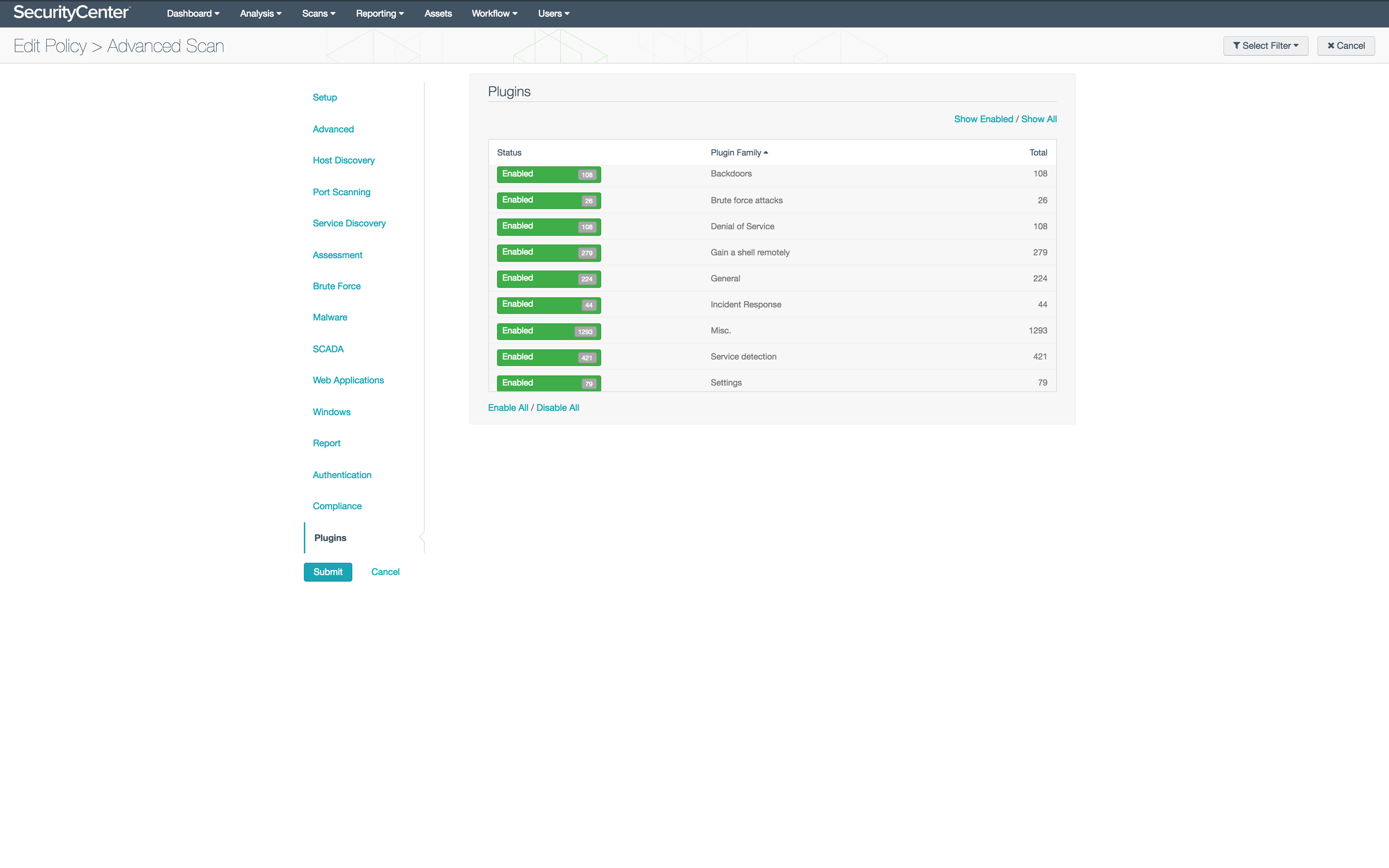
An important step in preparing SecurityCenter CV to assist in threat management and incident response efforts is to schedule routine credentialed scans of targeted endpoints. Credentialed scans analyze the targeted host in order to gather machine- and user-specific data. SecurityCenter CV has several built-in scan policies that are useful to gather the vulnerability data related to IR, such as the Malware Scan policy and the Credentialed Patch Audit policy. Additionally, a custom credentialed scan could be configured to be more inclusive, thereby gathering more data relevant to incident response. For an ideal threat management and incident response preparation scan, the following plugin families should be enabled:
- Backdoors
- Brute force attacks
- Denial of Service
- Gain a shell remotely
- General
- Incident Response
- Misc
- Service Detection
- Settings
- Local Security Checks
- Debian, Mac OS X, Red Hat, VMWare ESX, and others
- Windows
- Windows, Windows : Microsoft Bulletins, Windows: User Management
The OS-specific and Incident Response families will attempt to gather detailed information about user accounts and behavior, as well as vulnerabilities exposed by missing patches. Plugins are added to the local security checks and Microsoft Bulletins families in response to emerging threats. These plugins are often also tied to CVE numbers in order to improve tracking and monitoring of the threat. Additionally, plugins are added to these families when OS-specific vulnerabilities are identified in an application so that the vulnerable instances of the application can be more easily identified.
In addition to running credentialed scans, relevant data can be gathered by the Tenable Log Correlation Engine® (LCE®) and the Tenable Passive Vulnerability Scanner® (PVS™). The passive data gathered by PVS is automatically stored in the vulnerability database. In addition to providing normalized events to the SecurityCenter CV events database constantly, LCE converts data from normalized events into event plugins and sends them to the SecurityCenter CV vulnerability database. The event plugins can be leveraged alongside active and passive vulnerability data to prevent and detect incidents, as well as manage and mitigate risk from vulnerabilities.
Analysis
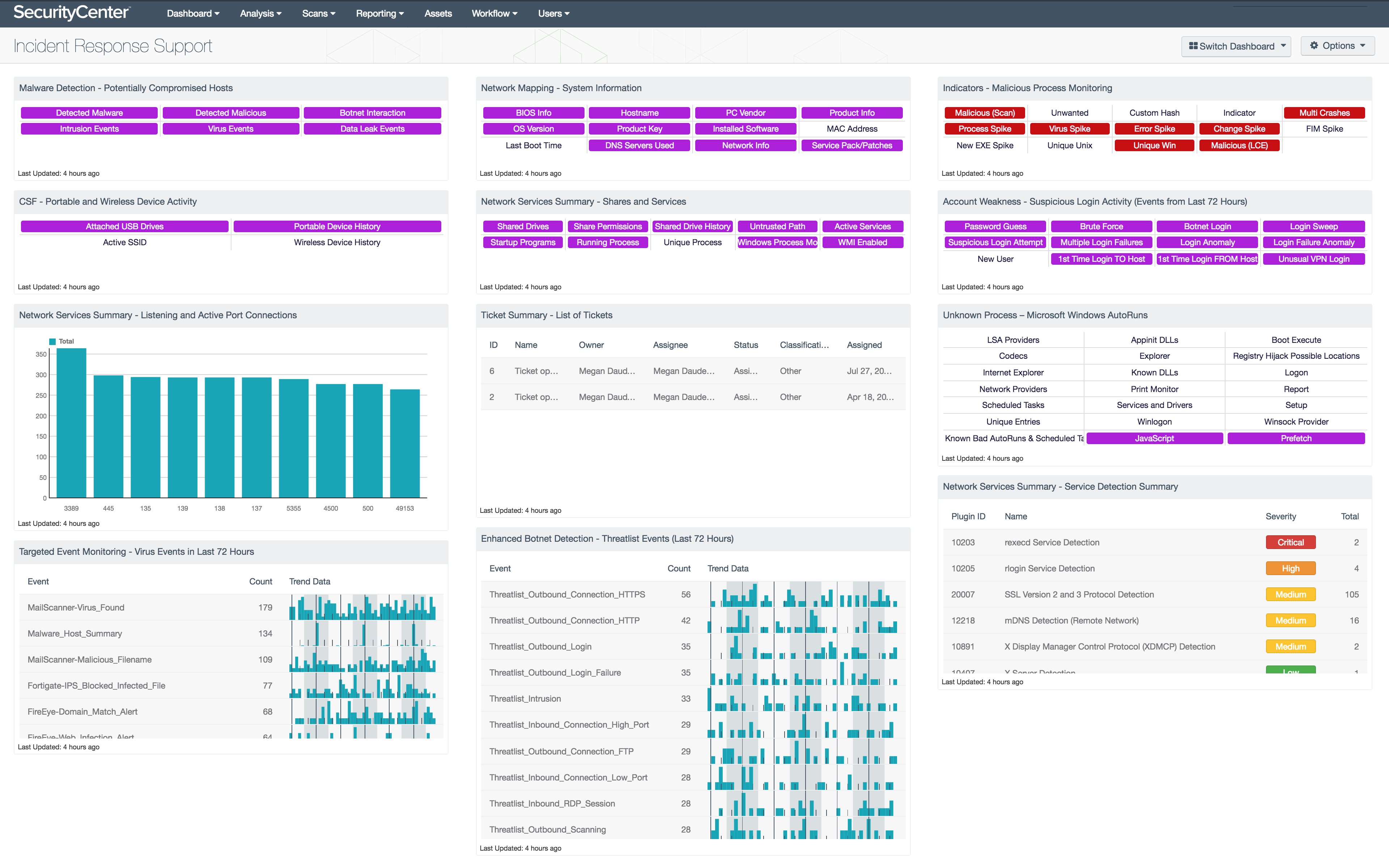
All of the data gathered by the sensors included in SecurityCenter CV can be effectively and efficiently interpreted through the use of dashboards and reports. The Incident Response Support dashboard and report present detailed information about areas of concern, such as detected services, host compromise, and suspicious activity.
When the alerts are triggered and the alarms go off, panic often ensues. When the alerts and alarms are triggered by a network incident, analysts can have difficulty determining where to start remediation efforts. The data gathered by SecurityCenter CV can be invaluable after an incident in order to determine the source, cause, and scope:
- If the source IP address is known, filtering vulnerability data for that address can provide detailed information about the potential exploitation opportunities, user accounts accessing that host, and connections between that host and others.
- If the incident was the result of an exploited vulnerability, a search for that vulnerability will provide a list of similarly exploitable hosts.
- Additional details about host activity is available from active plugins tracking host information, running processes, and user activity.
- Identifying running and malicious processes can be useful when dealing with anything from user activity to malware infections.
- The data gathered about Autoruns, prefetch files, and startup applications on Windows can help to identify, track, and contain malicious activity.
- Leveraging the known data about an incident to identify the full impact is an especially effective way to contain the issue at hand and prevent recurrence.
- Preconfigured content from the SecurityCenter Feed, such as dashboards and reports, can be useful in visualizing information related to an incident.
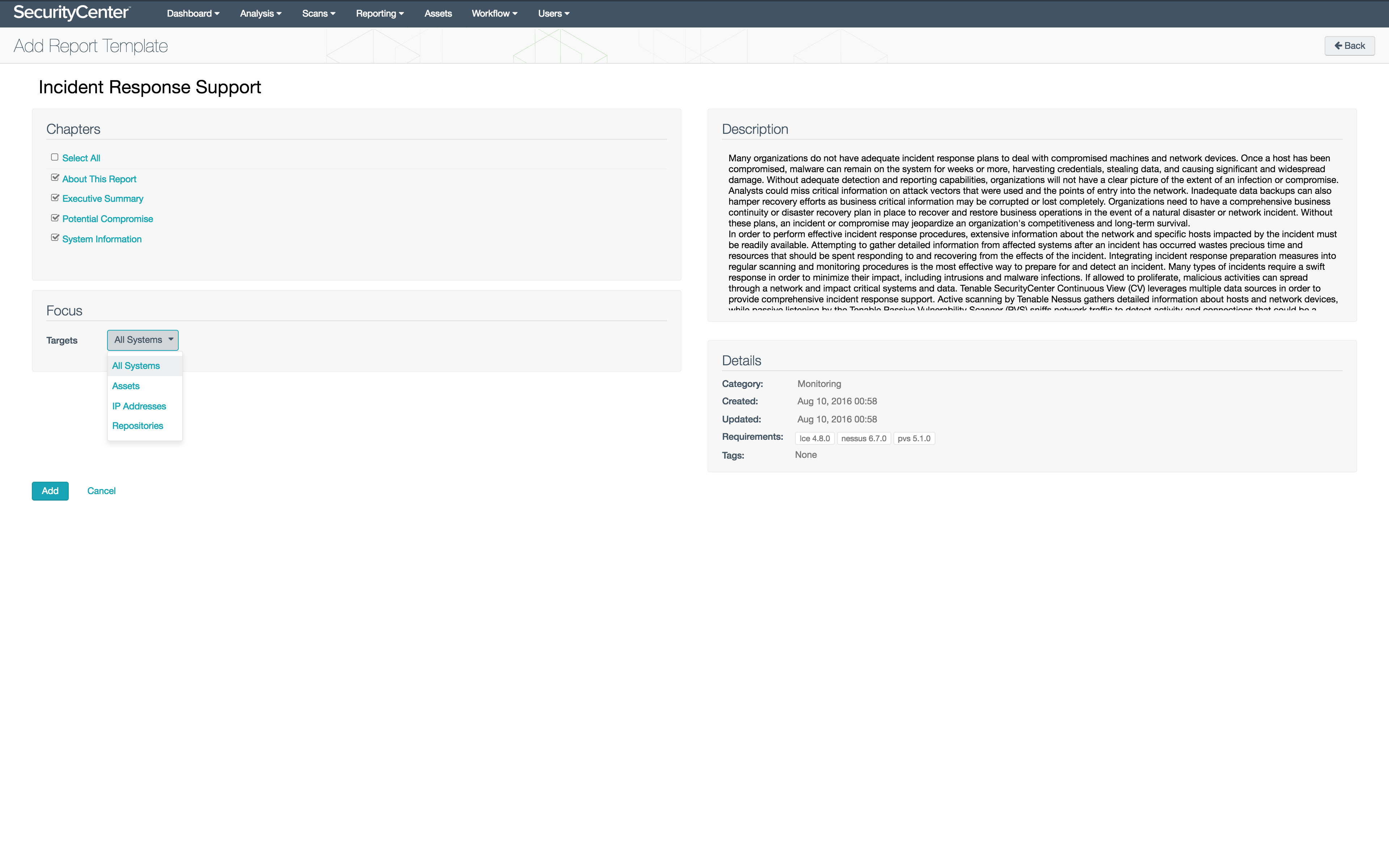
Preconfigured dashboards and reports can be added from the SecurityCenter Feed to support threat management and incident response efforts:
- From the Dashboard tab, click the Options menu on the right then choose Add Dashboard to search the Feed for relevant dashboards.
- From the Reports tab under the Reporting menu, click the Add button to bring up the Feed and search also.
- When content is added from the SecurityCenter Feed, the Targets filter in the Focus section can be set so that specific targets will be added automatically as filters. Setting this filter will enable your security team to more efficiently gather information about specific targets when responding to incidents on the network.
- For custom content, filters related to plugin families or names can help focus results on areas of concern, while filtering for assets or IP address ranges can focus the content on specific parts of the network.
Next steps
Now that you know more about how to leverage SecurityCenter Continuous View in your threat management and incident response preparation initiatives, you can start applying the knowledge to your own environment. Configure credentialed scans to run regularly, gather data from as many hosts as possible, and investigate incidents when they occur. All of those steps will enable you to take advantage of the integrated capabilities of SecurityCenter CV in order to improve your threat management, vulnerability remediation, and incident response efforts.
- Dashboards
- Incident Response
- SecurityCenter
- Vulnerability Management