Personalizing Your Tenable.io Scans

Tenable.io™ Scan and Policy Templates allow you to set up scans with minimal configuration. There are templates for many tasks, such as Host Discovery, detecting the latest headline-grabbing malware, managing mobile devices and more. However, your network is constantly evolving. Eventually the predefined templates will not satisfy the needs of your network. With Tenable.io, you can optimize the management of your network’s cyber risk by designing and launching customized vulnerability scans that are tailored to your organization.
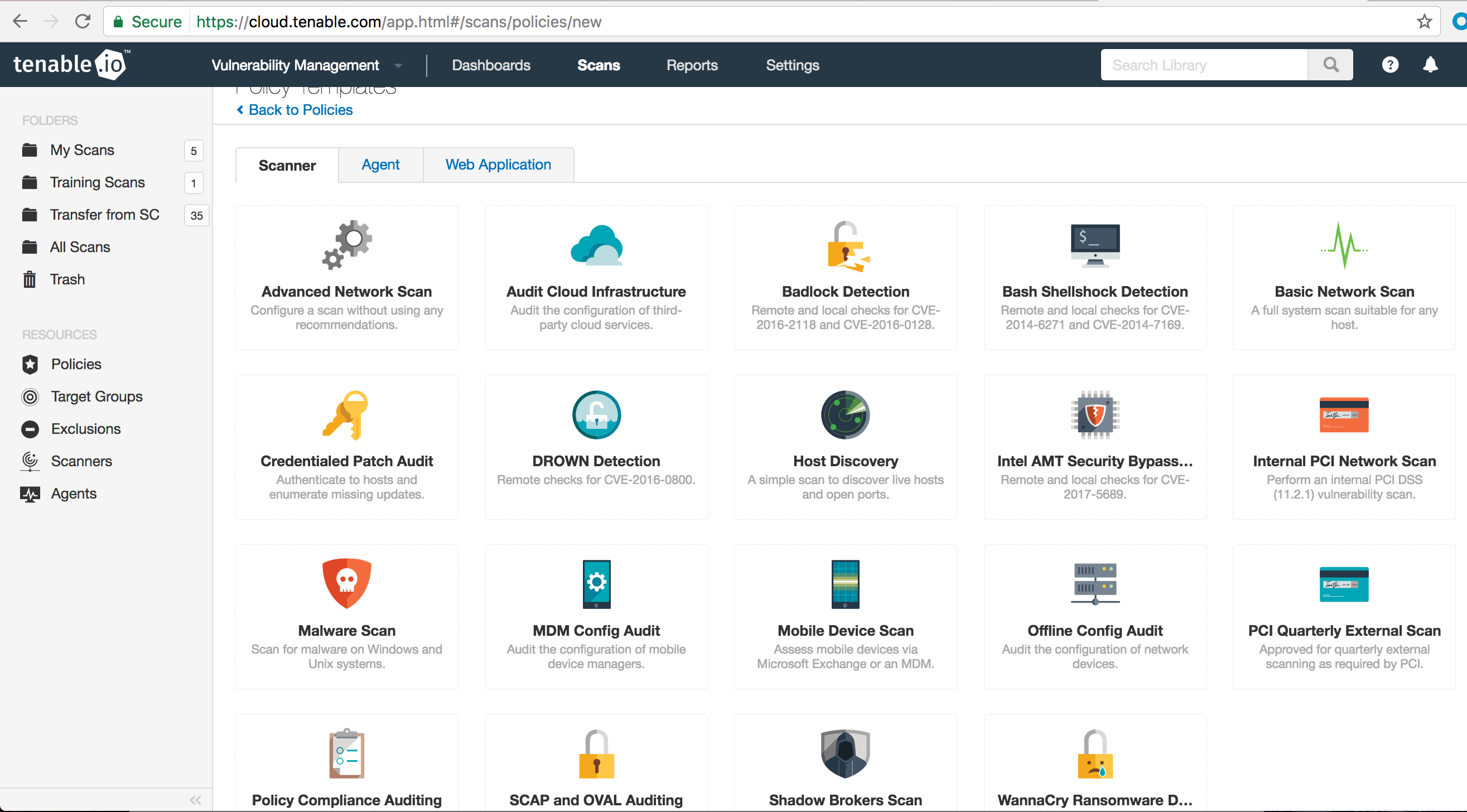
Each template enables a specific set of plugins, and each plugin performs a different security check. By choosing the “Advanced Network Scan” template, you can select your own plugins. Similar plugins are broken up into Plugin Families. These Plugin Families may include plugins that run local checks, which require authentication credentials and test for vulnerabilities specific to the host manufacturer or OS distribution, or remote checks that do not gain access to the host before running the test.
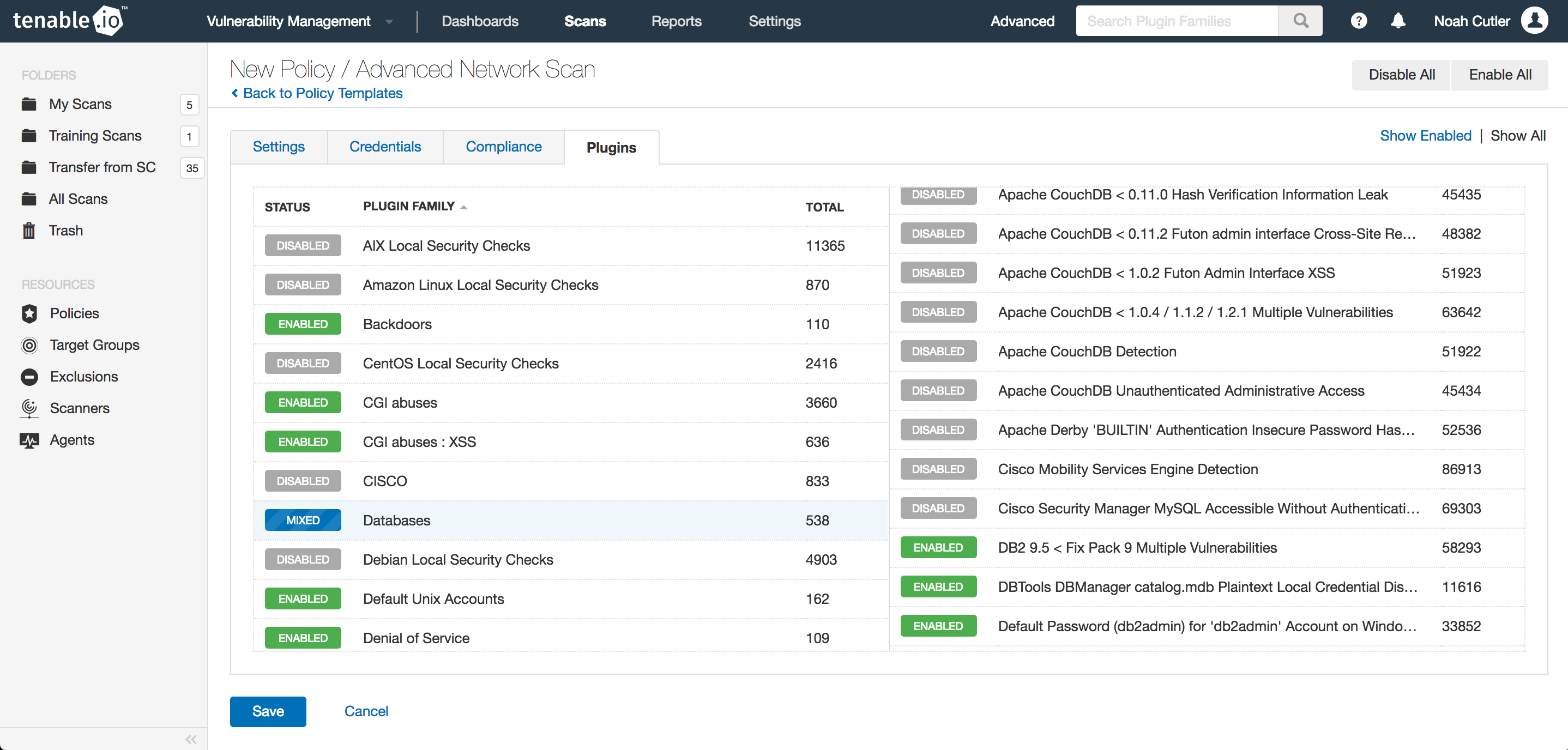
Creating a customized Advanced Network Scan policy is a good way to ensure that you receive the necessary information regarding your network’s cyber risk and exposure in a timely fashion.
Enumerating All the Windows User IDs
In the “Windows” section of “Assessment” tab, you have the option to Enumerate Domain Users and Local Users for a given range of User IDs (UIDs). The default range for both Local and Domain Users is between 1,000 and 1,200. When a new user is created, a new UID is assigned starting at 1,000, and automatically increases by one for each addition. UIDs are never reused. So, this range would cover the first 200 UIDs that were assigned to new users.
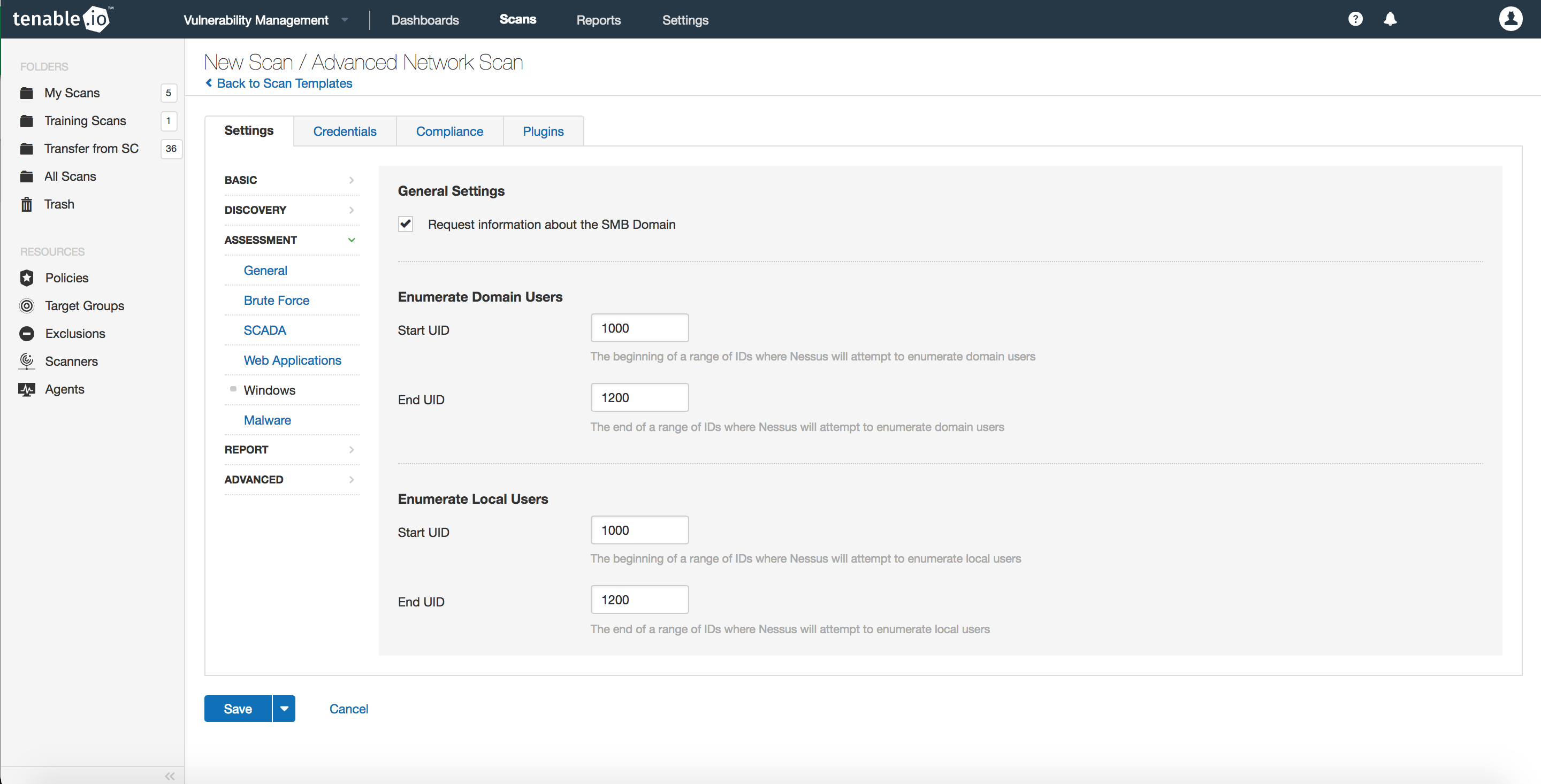
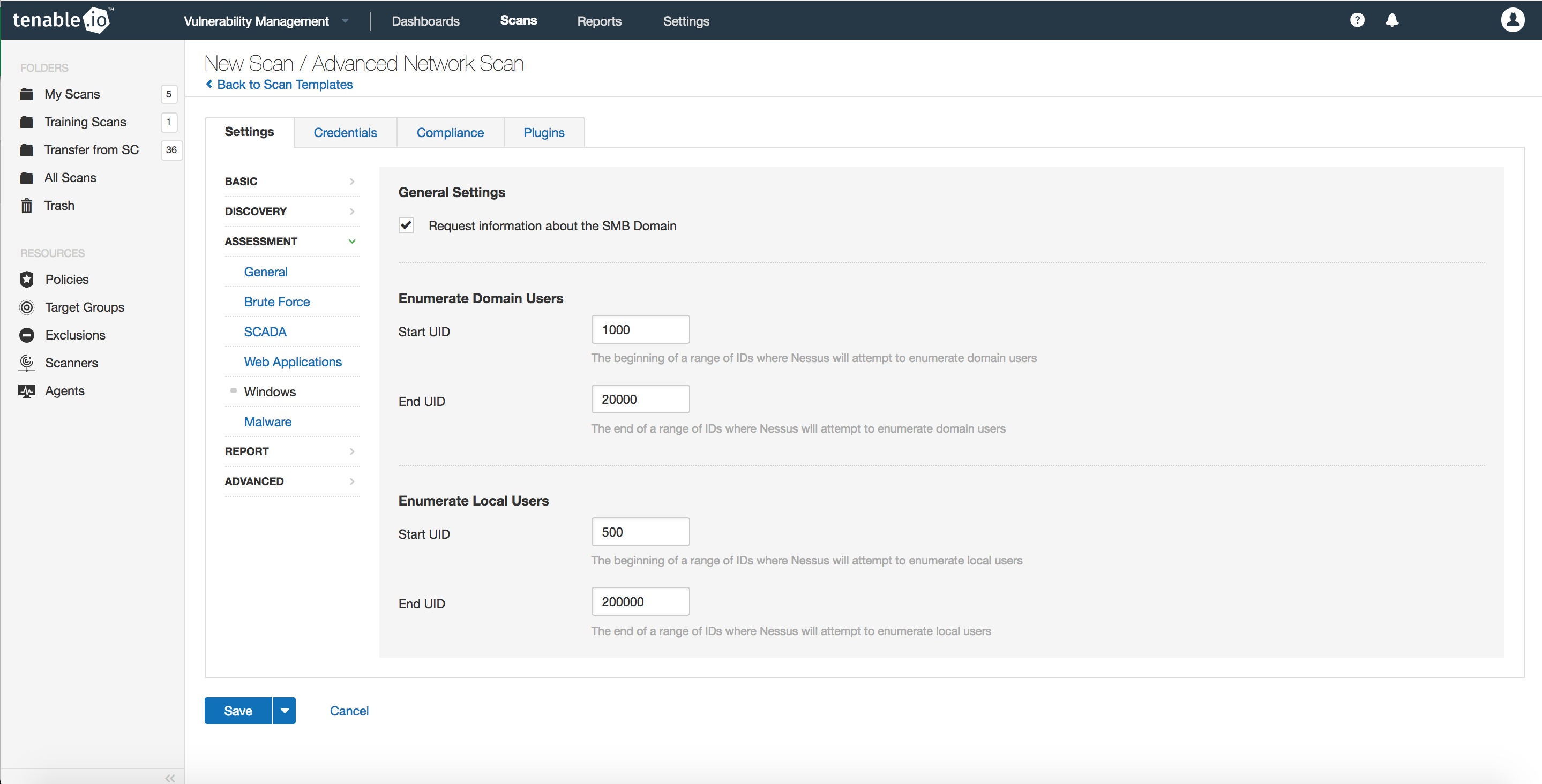
However, if you are part of a large organization in which more than 200 people have had user-level access to the network, then you may want to consider changing the “End UID” to 20,000 (or greater), thus ensuring all accounts are identified. Also, the default range does not account for UID 500, where the default local administrator account is enumerated.
Compliance Analysis
Tenable.io offers three different types of compliance checks. Standards-based auditing evaluates the configuration of your machines against standards set by third-party organizations, like the Center for Internet Security (CIS) or the Department of Defense’s Defense Information Systems Agency (DISA). Content auditing searches through file contents to look for sensitive information, like plaintext credit card numbers. Finally, network infrastructure auditing checks that configuration of routers, switches, firewalls and other devices are in line with internal policies.
When a compliance audit is conducted, an audit file is used to configure the check. There is a wide variety of compliance audit files available in Tenable.io. Audit files are available on Tenable.io directly through the Customer Support Portal, or you can write a custom audit file.
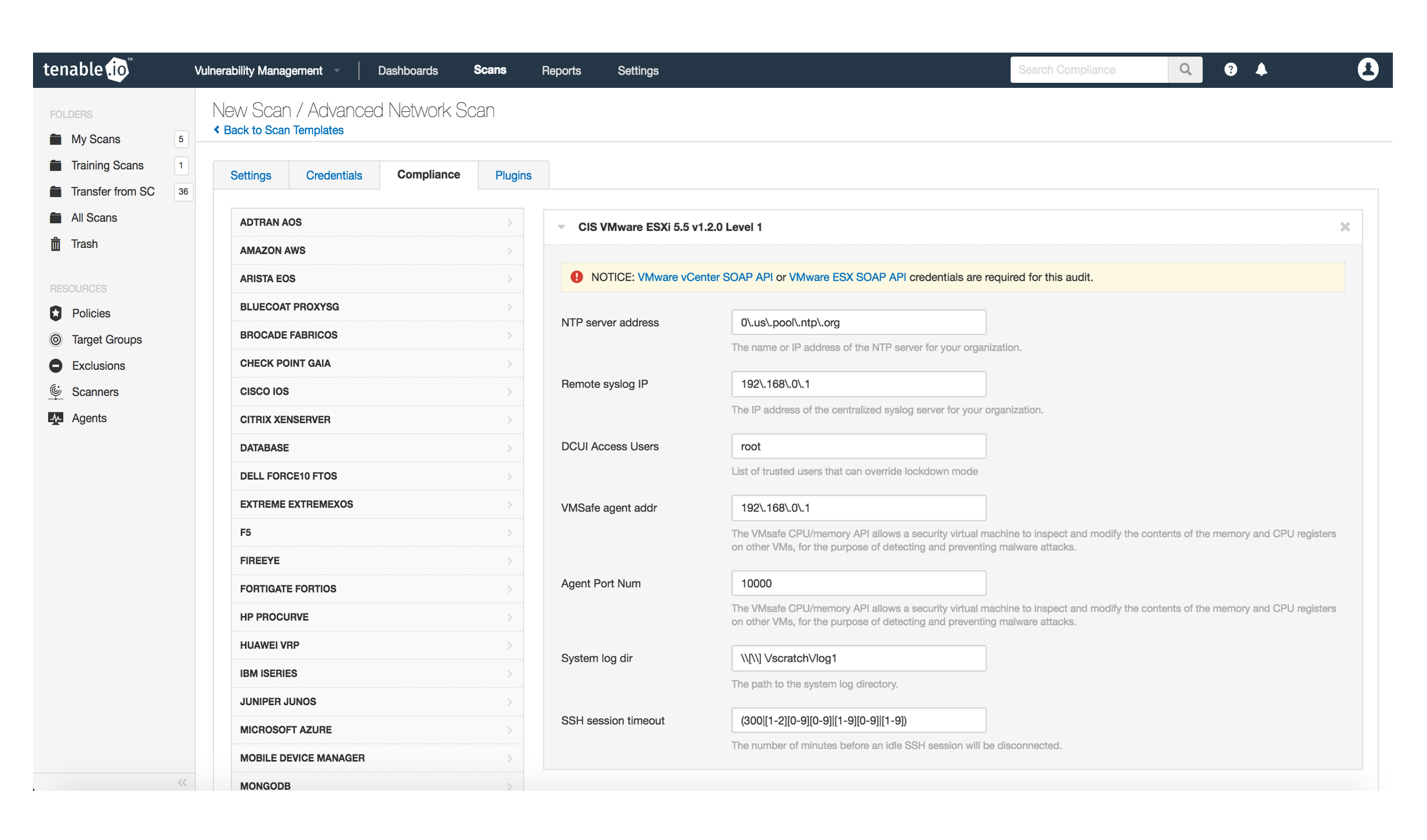
For example, the CIS VMware ESXi 5.5 v1.2.0 Level 1 audit file lets you set the NTP server address, designate privileged users and more. Under “DCUI Access Users” in the settings of compliance audit, you can list trusted users that are able to override the lockdown mode initiated by the scanner. The “DCUI Access Users” list is useful if there is more than one privileged account to ensure that the override lockdown mode is not bestowed upon just one user. The field labeled “SSH session timeout” allows you to restrict the scanner to a designated number of minutes after which an idle SSH session will terminate. Setting a shorter SSH session timeout limit can increase scan efficiency, otherwise scanners can waste a lot of time in an idle session. Note that this compliance check requires credentials to complete the audit. However, not every compliance audit requires credentials.
Preparing for the Future
By choosing appropriate scan settings, you can streamline the scans on your network to be as comprehensive or lightweight as needed. With the proliferation of IoT, the average size of networks is growing quicker than ever before. By 2020, there will be an estimated 70+ billion internet-connected “things” across the world. To prepare, you’ll need to understand all of the nooks and crannies of your network. Then, you can plan your scans accordingly.
Tenable.io is an easy-to-use platform with preconfigured templates that allow you to hit the ground running. However, to comprehensively manage your network’s elastic attack surface, you must optimize the tools for the particular needs of your network.
- Tenable Vulnerability Management


