New Nessus VMware vSphere/vCenter Audits Now Available
Nessus contained the ability to perform compliance audits against VMware ESX for some time. However, the methods used SSH credentials to log into the VMware platform and perform the audit checks. SSH has been disabled by default on newer versions of ESX/ESXi.
Tenable has now implemented new checks using the VMware SOAP API (which is already being used by existing plugins to pull information about VMware systems). Tenable has developed APIs for both ESXi (the interface available free of charge to manage virtual machines (VMs) on ESX/ESXi) and vCenter (an add-on product available from VMware at some cost to manage one or more ESX/ESXi servers). Supported versions are ESXi 4.x/5.x and vCenter 4.x/5.x.
Comprehensive Configuration and Compliance Auditing for VMware
Three new customizable compliance auditing files are now available on the Tenable Support Portal. The new .audit files provide more than twice the number of checks (over 200+) currently available in VMware's compliance checking tool. The audit files are:
VMware-hardening Compliance Audit
This compliance audit represents the industry-standard resource when it comes to hardening VMware infrastructure. The compliance auditing file uses the guides from VMware and provides you with a report to see how your configuration stacks up.
Tenable vCenter/vSphere Best Practices Configuration Audit
By interfacing with the VMware API, Nessus is able to go beyond the hardening guidelines provided by VMware. There is more information that Nessus is able to audit and report on that is useful to VMware administrators. For example, Nessus can report whether VMware Tools was installed, the heartbeat settings on VMs, Guest operating system listings, overall VM status, floppy/CD-ROM drives connected, and iSCSI device status.
DISA VMware ESXi/vCenter 5 STIG Audit
This audit implements the majority of the recommendations provided by the latest draft version of the DISA VMware ESXi/vCenter 5 Security Technical Implementation Guide (STIG).
Initiating VMware Compliance Auditing Scan
The first step is to create a new policy and enter the administrative credentials for the VMware ESX and/or vCenter server:
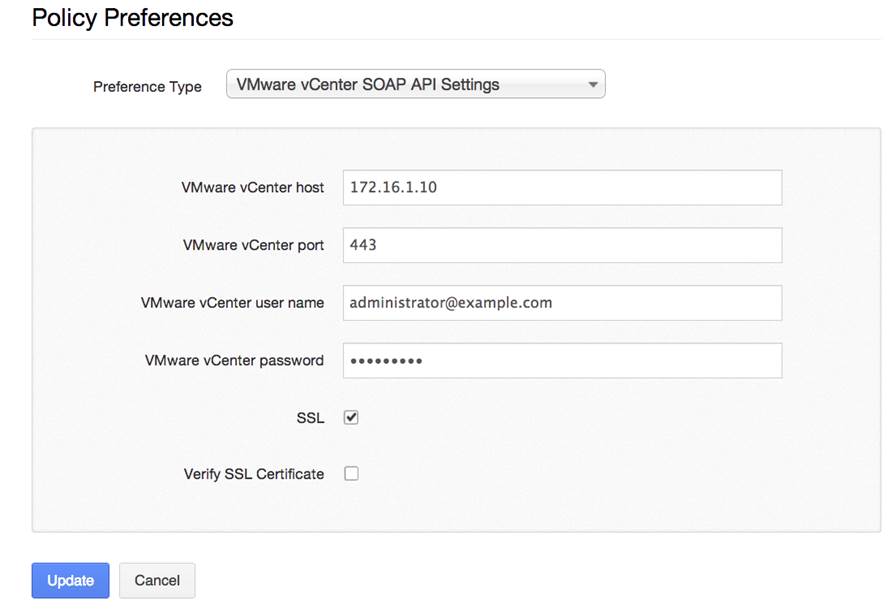
Next, be certain to enable Plugin ID #64455 (VMware vCenter/vSphere Compliance Checks):
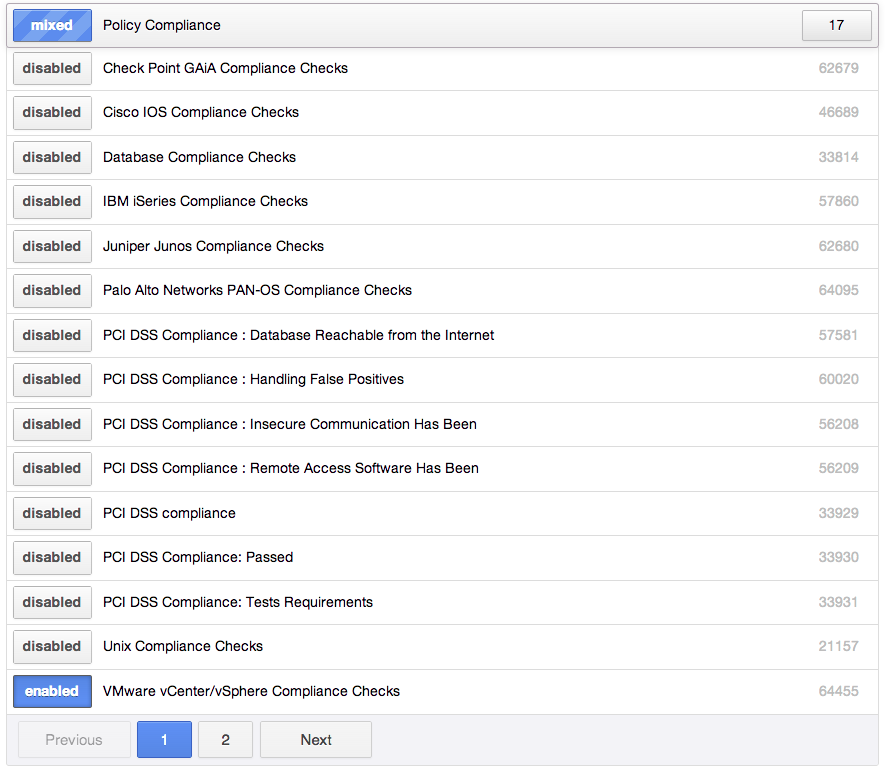
Next, upload one or more VMware compliance auditing files to the policy:
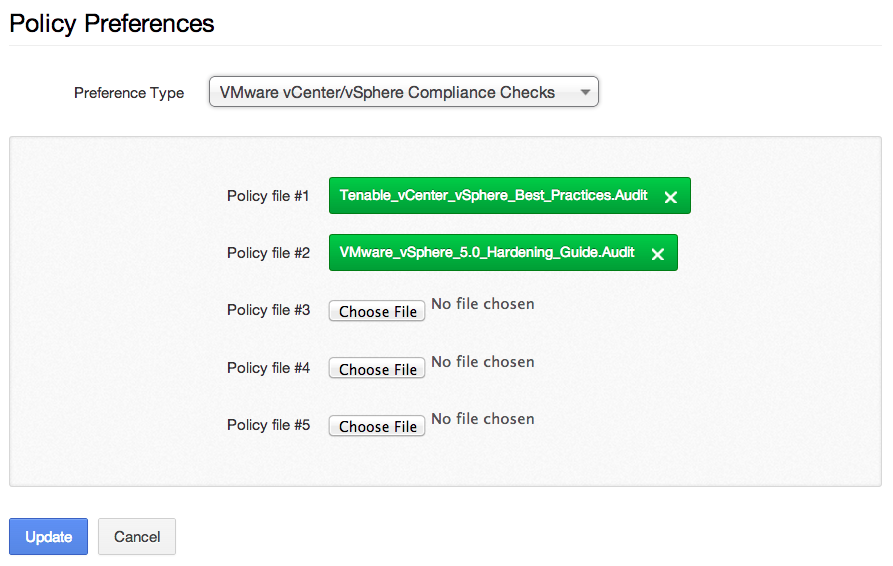
Finally, you can save the policy, create a scan template, and launch the scan.
VMware Compliance Auditing Results
Once the scan completes, you can find the results in the "Compliance" tab:
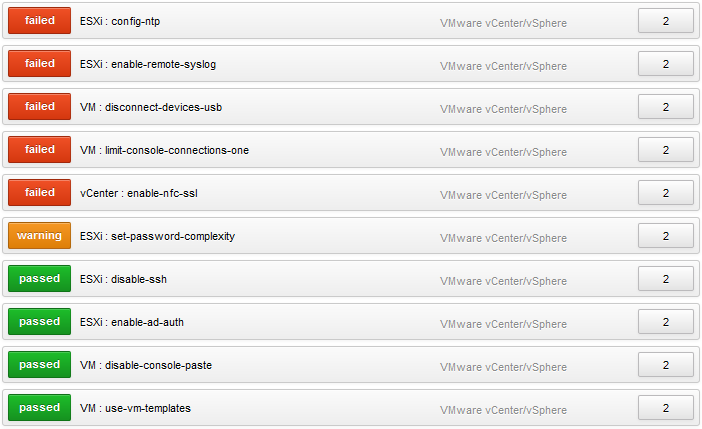
This is a great example as it highlights some of the configuration settings detected by Tenable’s best practice audit. For example, the target host has not implemented remote syslog monitoring.
Below is an example of a passed compliance check that lists the operating systems of the VMs installed on the ESXi target:
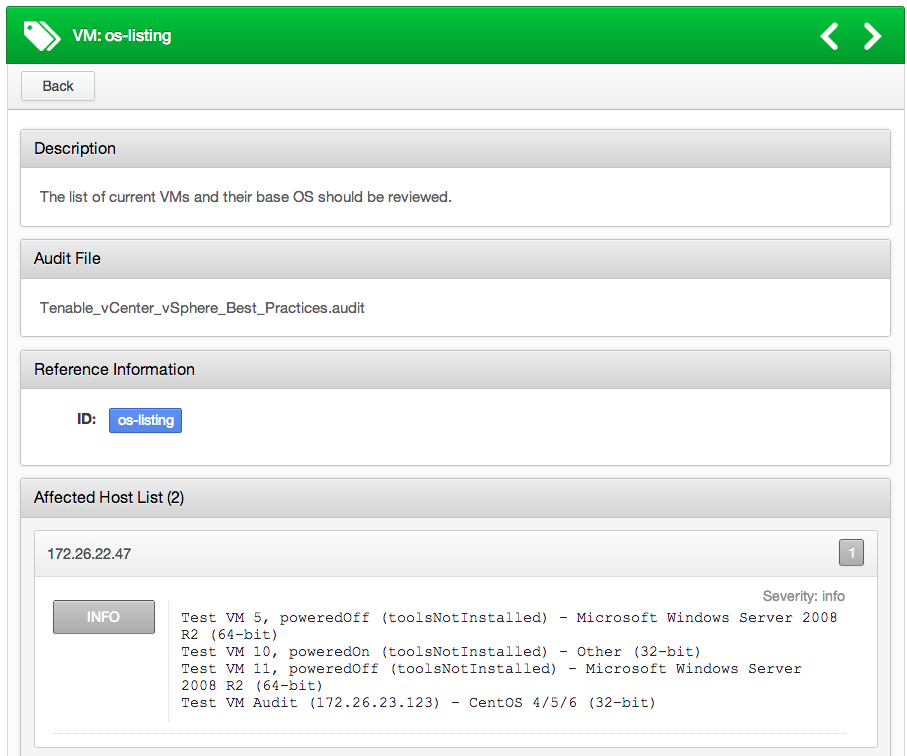
If a check passes, this plugin reports all the VMs that matched the policy. The .audit supplied by Tenable will report both the VM name and IP of the target. However, note that the IP address for a VM is not available unless VMware Tools is installed.
Conclusion
Hardening your systems is one of the most effective ways to prevent systems from becoming compromised. Not only must you consider operating system hardening, but also the virtualization platform they are running on. Nessus now offers a comprehensive way to audit your VMware environment.
For more information on the .audit file syntax, please view the post on the Tenable Discussion Forum.
Related Posts
For information related to additional enterprise configuration and compliance audits, please see the following blog posts.
- Nessus
- Vulnerability Management

