New Nessus Report Consolidates Missing Patches
Ensuring that patches are applied to systems is a complex problem. Pinpointing those patches that must be applied to become current requires careful analysis. The new Nessus consolidated “Patch Report” plugin identifies which patches to apply to protect your systems.
The Challenges of Patching
Regardless of platform, there are a plethora of patches to be applied. I tend to break them up into three general categories:
- Operating System (OS) Patches - These are patches made available by your OS vendor. In the case of Microsoft Windows and Apple OS X, it's fairly straight forward as patches are released that apply primarily to the software which comes with the OS. Microsoft also provides regular patch updates for Microsoft Office as well.
- 3rd-party Applications - Software installed by the user (outside of any package management system) is classified as third-party. Popular software, such as web browsers and related add-ons (Oracle Java, Adobe Flash), plague this category, making it challenging to manage and keep up-to-date.
- Packages Offered by the Distribution - In the case of Linux/UNIX, the OS patches are extended by the package management system and offer patches for your kernel, core software, and other software installed by the distribution. This software sits somewhere between the OS and third-party software.
Systems will often become out-of-date rather quickly, especially those that may have fallen outside your patch management strategy. When these hosts are scanned by Nessus, sometimes more than 100 different missing patches will be reported. For example, you can get a complete report of missing Microsoft patches for each host:
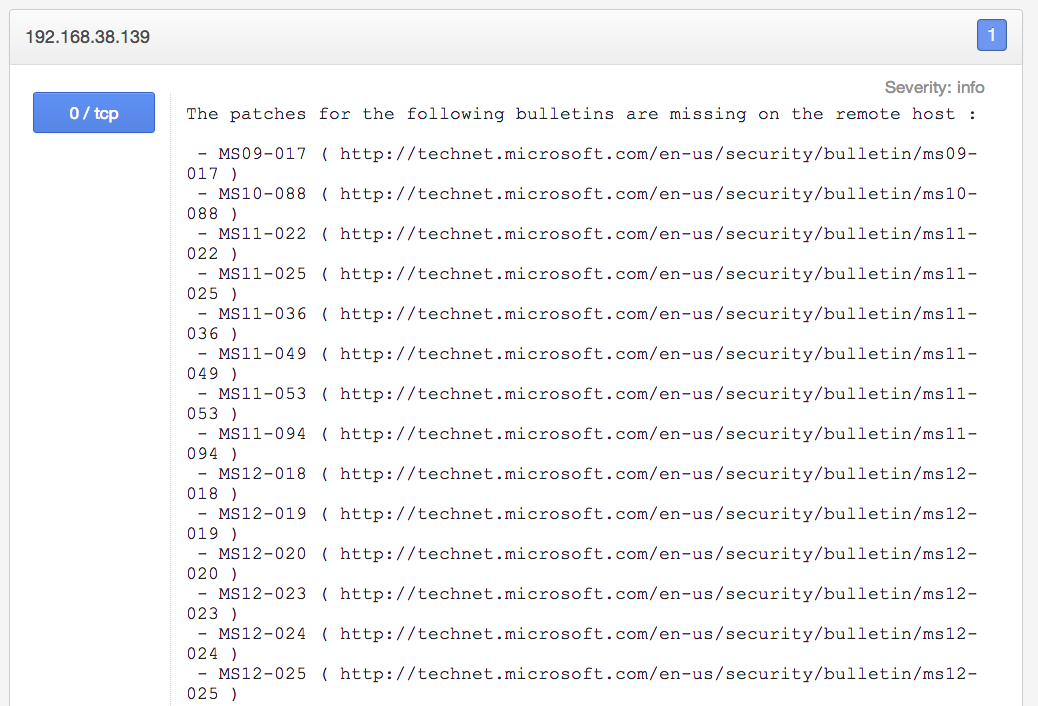
Consolidated OS Patches
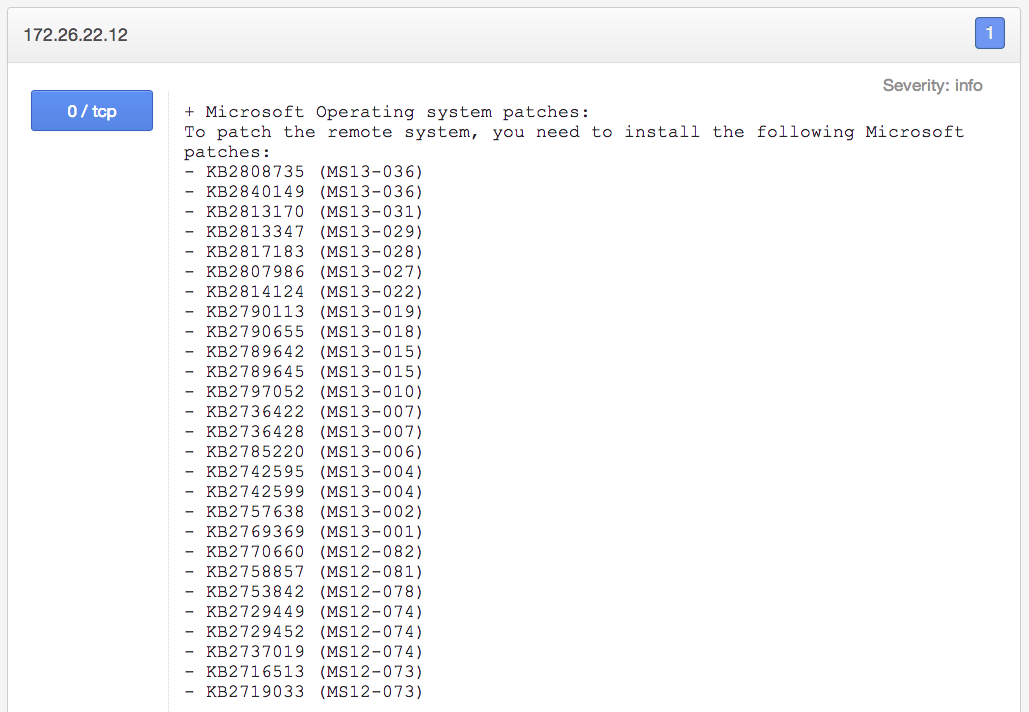
Nessus now helps with patch consolidation. The new Nessus “Patch Report” plugin (ID #66334) will display a list of consolidated patches, only showing the patches that need to be applied and omitting superseded patches:
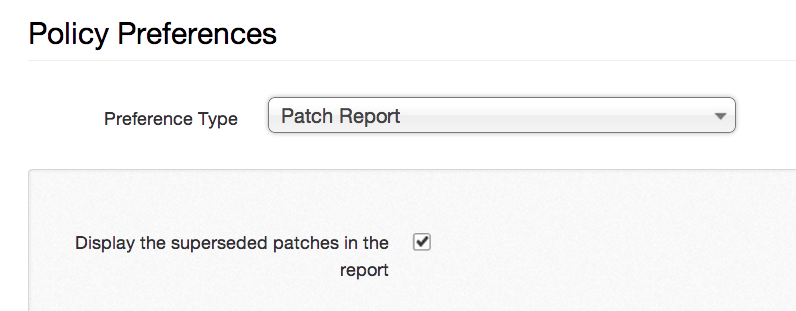
The new plugin can also exclude superseded patches from the results. The following option allows the user to control this behavior:
Consolidated Third-party Application Patches
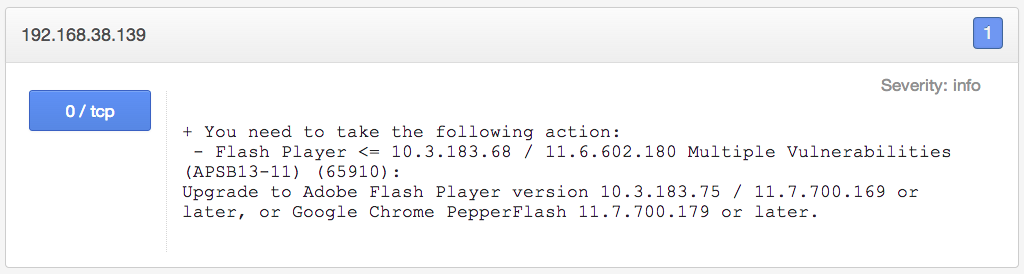
The "Patch Report" will also summarize patches for third-party software. For example, let's say that you've scanned a target that's running an outdated version of Adobe Flash. The missing patches are represented as follows:
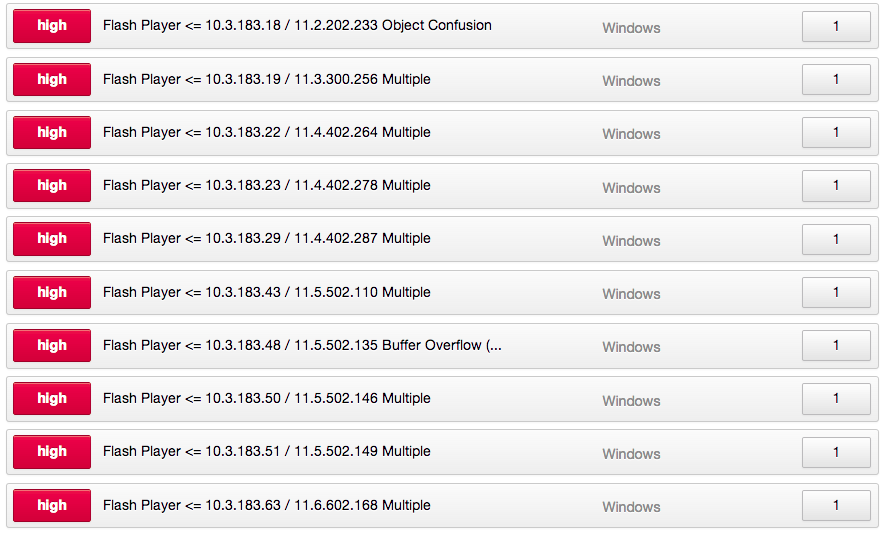
In order to keep this system up-to-date, not necessarily all of the patches listed above need be applied. It's more likely that applying one Adobe Flash update will install all of the missing updates. The Nessus "Patch Report" plugin now reports this information and presents a consolidated list of patches that must be applied:
Platform Support
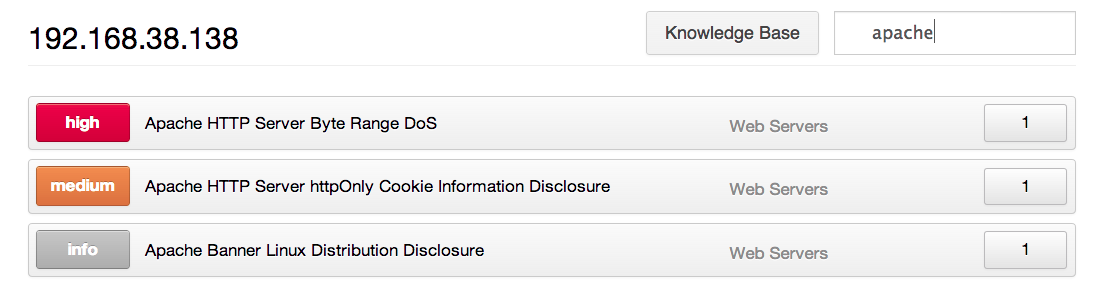
The new "Patch Report" plugin supports all major platforms (Windows, OS X, UNIX, and Linux) and includes both OS and third-party software patches. Linux local patch checking is still in the works; however, if Nessus finds vulnerable software remotely (without credentials), a consolidated patch report is still issued. For example, Nessus found two vulnerabilities (and one informational level result) in the running Apache web server:
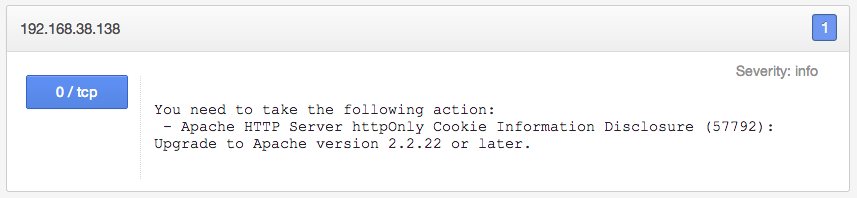
The solution for the "Apache Byte Range DoS" vulnerability is to upgrade to Apache version 2.2.21 or later. The solution for the "httpOnly Cookie Information Disclosure" vulnerability is to upgrade to 2.2.22 or later, resulting in the following patch report:
Conclusion
Systems administrators are already overwhelmed with their daily tasks. When security assessments are performed, it can be perceived as added work to sift through vulnerabilities and figure out what needs to be done to remediate the issues. The new Nessus "Patch Report" plugin will foster better communication and teamwork between the security and systems administration groups, allowing Nessus to make an actionable report.
Resources
- If a Security Control Falls in the Forest... - "Many guidelines and compliance standards state that in order to be "secure" or "compliant," all of your systems must be patched. Turns out that this is easier said than done. Just when you believe your systems to be patched, something fails and patches seemingly disappear."
- Nessus
- Patch Auditing

