Nessus Now Audits Huawei VRP Configurations
As part of Tenable's Continuous Monitoring Solution, Nessus, Nessus Enterprise and Nessus Enterprise Cloud users can now perform configuration audits against Huawei devices running the Versatile Routing Platform (VRP).
Huawei (pronounced "wah-way") is a manufacturer of several different types of networking and telecommunications hardware and software. Huawei products are more popular in Asia and Europe than in the U.S. This new plugin supports devices running Huawei Versatile Routing Platform VRP (R) software. The 'display version' command can be run on the target to obtain the release information and determine if it’s supported by the Nessus audit files.
Scan Configuration Details
To perform configuration audits against Huawei devices in your environment you will need:
- Remote admin credentials for Huawei device
- SSH services running on the device
- Enable Plugin ID #73157 (Huawei VRP Compliance Checks)
- Download the Audit File for Huawei (TNS_Huawei_AR-Series_Best_Practices.audit) from the Tenable Support Portal and upload it into your new policy
What Can I Discover?
The audit file covers several configuration items on Huawei devices, including:
- Password policies
- Banner configuration
- Inactivity timeout
- Logging and auditing settings
- Insecure services
- General device and license information
- SNMP settings
Below are some example results:
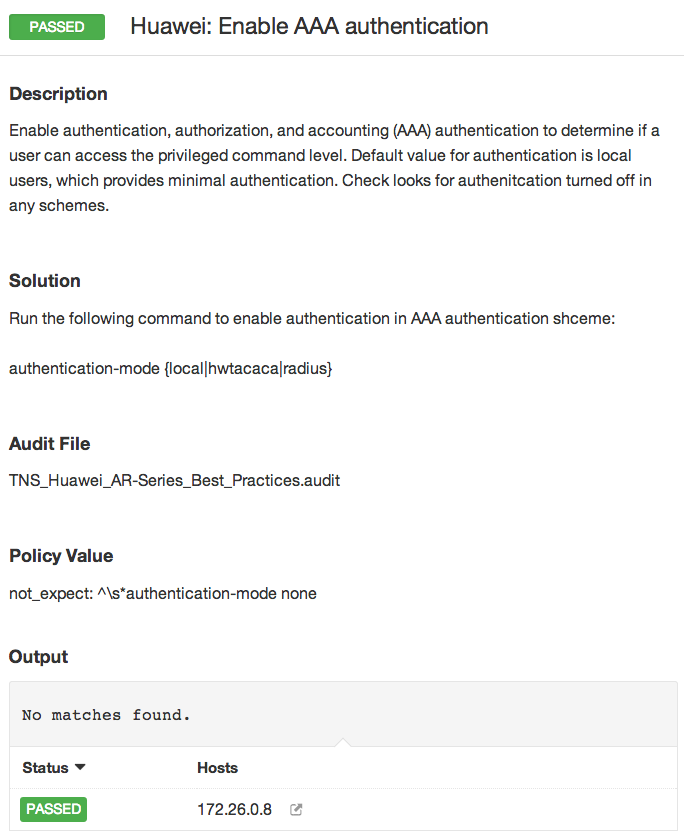
A Huawei device passes the check because AAA authentication is enabled.
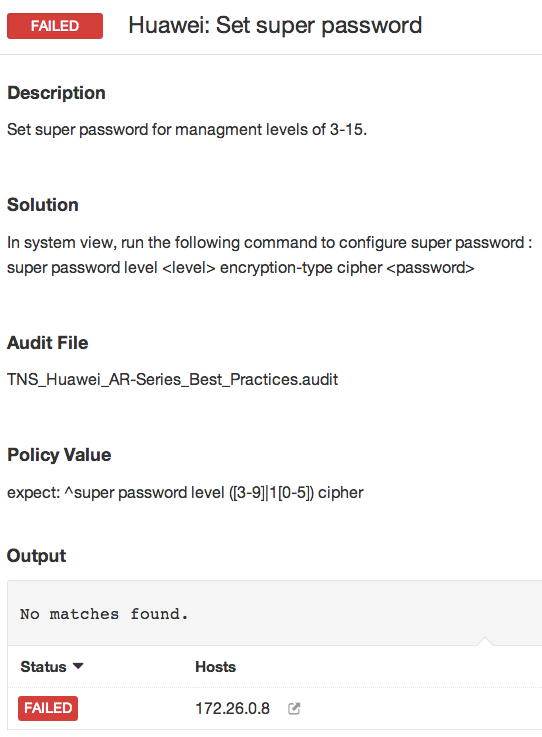
The device has failed the check for a "super password", similar to a Cisco "enable" password.
Offline Configuration Auditing
Nessus adds support for Huawei to a growing list of network devices for which offline configuration auditing can be performed. This eliminates the need for Nessus to use SSH and directly access the device(s), as you will upload the configuration and the associated audit file to Nessus. This provides another way to get the same results without having to run Nessus scans against your network devices directly. To obtain the configuration file on Huawei devices you can use the command:
display current-configuration all
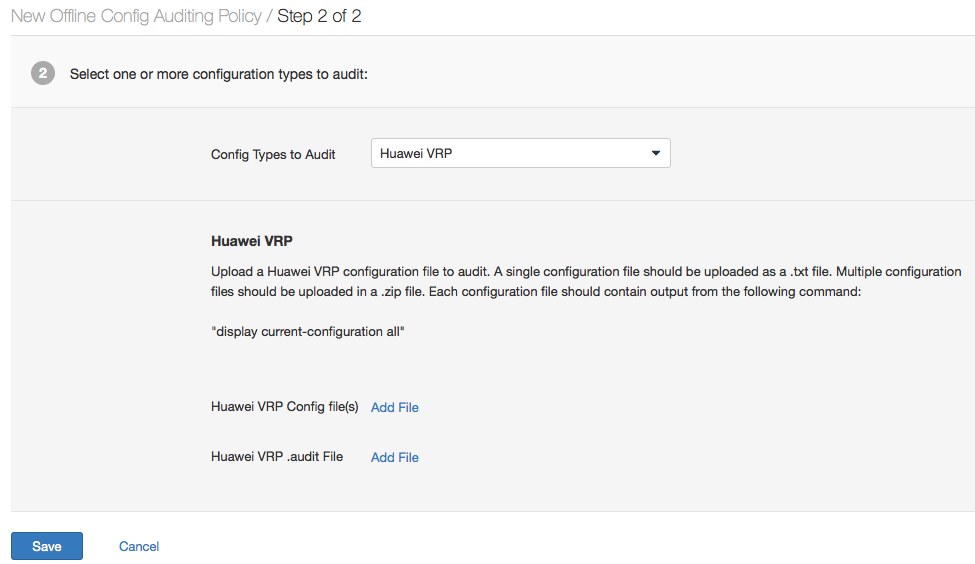
Save that output to a text file, then using the Offline Configuration Auditing Policy Wizard, initiate the configuration checking and review the results. Below is a screen shot of the wizard in action:
Configuration auditing Huawei devices allows you to conform to compliance standards such as SANS-CSC, PCI, CSF 800-53, and HIPAA.
For more information about this feature please refer to the Tenable Discussions Forum entry that contains more technical details about the checks themselves. Tenable customers can go to the Tenable Support Portal and download the new audit file which can be implemented in all Nessus and SecurityCenter Continuous View products.
- Vulnerability Management
- Vulnerability Scanning


