Microsoft’s December 2025 Patch Tuesday Addresses 56 CVEs (CVE-2025-62221)

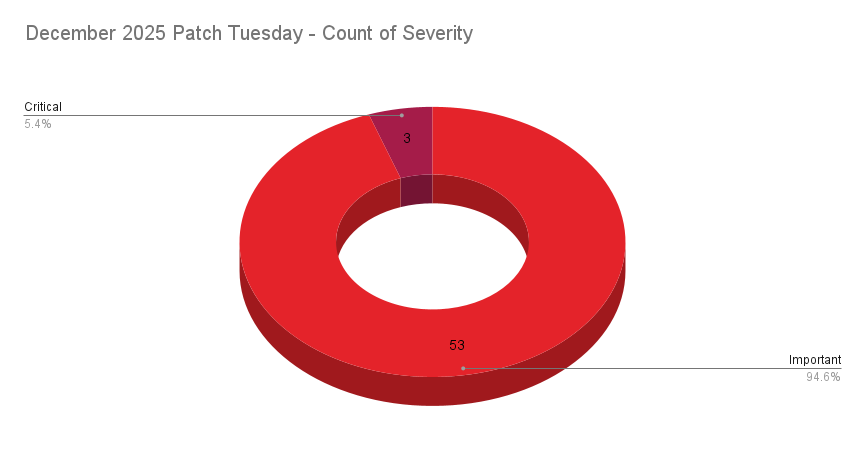
- 3Critical
- 53Important
- 0Moderate
- 0Low
Microsoft addresses 56 CVEs, including two publicly disclosed vulnerabilities and one zero-day that was exploited in the wild to close out the final Patch Tuesday of 2025
Microsoft patched 56 CVEs in its December 2025 Patch Tuesday release, with three rated critical, and 53 rated as important.
This month’s update includes patches for:
- Application Information Services
- Azure Monitor Agent
- Copilot
- Microsoft Brokering File System
- Microsoft Edge for iOS
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Word
- Storvsp.sys Driver
- Windows Camera Frame Server Monitor
- Windows Client-Side Caching (CSC) Service
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows DWM Core Library
- Windows Defender Firewall Service
- Windows DirectX
- Windows Hyper-V
- Windows Installer
- Windows Message Queuing
- Windows PowerShell
- Windows Projected File System
- Windows Projected File System Filter Driver
- Windows Remote Access Connection Manager
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Shell
- Windows Storage VSP Driver
- Windows Win32K - GRFX
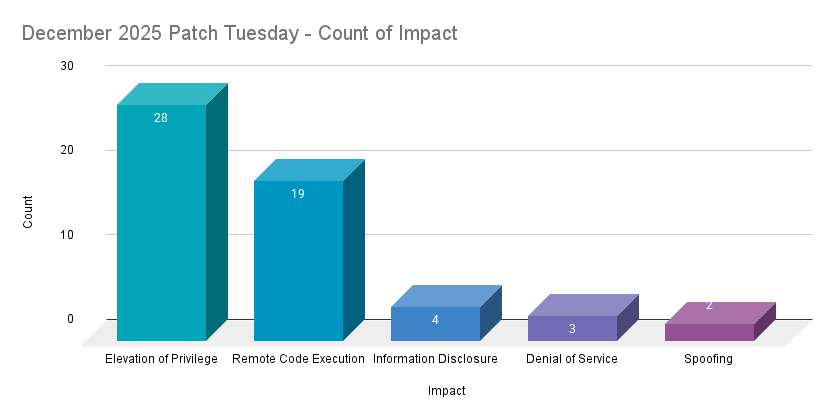
Elevation of privilege (EoP) vulnerabilities accounted for 50% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 33.9%.
CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2025-62221 is an EoP vulnerability in the Windows Cloud Files Mini Filter Driver. It was assigned a CVSSv3 score of 7.8 and rated as important. A local, authenticated attacker could exploit this vulnerability to elevate to SYSTEM privileges. According to Microsoft, this vulnerability was exploited in the wild as a zero-day.
Microsoft also patched two additional EoP vulnerabilities in the Windows Cloud Files Mini Filter Driver, CVE-2025-62454 and CVE-2025-62457. Both were assigned the same CVSSv3 score of 7.8 and rated important. However, CVE-2025-62454 was assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index while CVE-2025-62457 was assessed as “Exploitation Unlikely.”
CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability
CVE-2025-64671 is a RCE vulnerability in the GitHub Copilot Plugin for JetBrains Integrated Development Environments (IDEs). It was assigned a CVSSv3 score of 8.4, rated important and assessed as “Exploitation Less Likely” The issue stems from a command injection vulnerability in GitHub Copilot. An attacker could leverage a “malicious Cross Prompt Inject” either through an MCP Server or untrusted files. Successful exploitation would grant an attacker the ability to append unapproved commands onto existing allowed commands due to the ‘auto-approve’ setting in the terminal.
This vulnerability has been dubbed IDEsaster by security researcher, Ari Marzuk who is credited for reporting this vulnerability to Microsoft.
CVE-2025-54100 | PowerShell Remote Code Execution Vulnerability
CVE-2025-54100 is a RCE vulnerability in Windows PowerShell. This vulnerability was assigned a CVSSv3 score of 7.8 and is rated as important. According to the advisory, this RCE was publicly disclosed prior to a patch being made available. The advisory notes that after installing the update, a warning prompt will be displayed anytime the Invoke-WebRequest command is used.
This vulnerability was attributed to several researchers including Justin Necke, DeadOverflow, Pēteris Hermanis Osipovs, Anonymous, Melih Kaan Yıldız and Osman Eren. The researcher known as DeadOverflow has a YouTube video demonstrating how this flaw can be abused and links to a HackerOne report opened with the curl project by another researcher. According to the HackerOne report, the issue was not related to curl, but rather appeared to be related to the PowerShell curl alias that utilizes Invoke-WebRequest.
CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability
CVE-2025-62458 is an EoP vulnerability affecting Microsoft’s Win32k, a core kernel-side driver used in Windows. This vulnerability received a CVSSv3 score of 7.8, was rated as important and assessed as “Exploitation More Likely.” Successful exploitation of this vulnerability would allow an attacker to gain SYSTEM level privileges on an affected host.
Including CVE-2025-62458, this is the ninth EoP vulnerability affecting Win32k addressed by Microsoft in 2025, with 14 EoP flaws addressed in the driver throughout 2024.
CVE-2025-62554 and CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability
CVE-2025-62554 and CVE-2025-62557 are RCE vulnerabilities affecting Microsoft Office. Both received CVSSv3 scores of 8.4 and were rated as critical. An attacker could exploit these flaws through social engineering by sending the malicious Microsoft Office document file to an intended target. Successful exploitation would grant code execution privileges to the attacker.
Despite being flagged as “Less Likely” to be exploited, Microsoft notes that the Preview Pane is an attack vector for both vulnerabilities, which means exploitation does not require the target to open the file. According to the advisories from Microsoft, security updates for Microsoft Office LTSC for Mac are not yet available and will be released as soon as they are ready.
Tenable Solutions
A list of all the plugins released for Microsoft’s December 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's December 2025 Security Updates
- Tenable plugins for Microsoft December 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on Tenable Connect and engage with us in the Threat Roundtable group for further discussions on the latest cyber threats.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management



