Microsoft’s June 2020 Patch Tuesday Addresses 129 CVEs Including Newly Disclosed SMBv3 Vulnerability (CVE-2020-1206)

Microsoft continues its streak of patching over 100 CVEs, addressing 129 CVEs in June, including a fix for a new SMBv3 vulnerability dubbed SMBleed.
For the fourth month in a row, Microsoft has patched over 100 CVEs, addressing 129 in the June 2020 Patch Tuesday release. The updates this month include patches for Microsoft Windows, Microsoft Edge, ChakraCore, Internet Explorer, Microsoft Office, Microsoft Office Services and Web Apps, Windows Defender, Microsoft Dynamics, Visual Studio, Azure DevOps and Adobe Flash Player.
CVE-2020-1226 and CVE-2020-1225 | Microsoft Excel Remote Code Execution Vulnerability
CVE-2020-1226 and CVE-2020-1225 are remote code execution (RCE) vulnerabilities in Microsoft Excel. Exploitation of these vulnerabilities could result in arbitrary code execution with the same permissions as the current user. An attacker would need to convince a user to open a malicious Excel file in order to exploit these vulnerabilities.
CVE-2020-1194 | Windows Registry Denial of Service Vulnerability
CVE-2020-1194 is a denial of service (DoS) vulnerability due to the Windows Registry improperly handling filesystem operations. An attacker would need access to the system in order to launch a crafted application to exploit this flaw. While the details on this vulnerability are vague, Microsoft notes that the patch corrects how the Windows Registry handles filesystem operations and only allows the tracing to be captured under the default path.
CVE-2020-1284 | Windows SMBv3 Client/Server Denial of Service Vulnerability
CVE-2020-1284 is a DoS vulnerability that exists due to the manner in which the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. This flaw can be exploited on an authenticated server or against an SMB client. Successful exploitation of this vulnerability will cause the target system to crash. An authenticated attacker would need to send a specially crafted packet to exploit this vulnerability against a vulnerable SMB server. To target an SMB client, an attacker would need to host a maliciously configured SMBv3 server and convince the client to connect to it.
CVE-2020-1206 | Windows SMBv3 Client/Server Information Disclosure Vulnerability
CVE-2020-1206, dubbed SMBleed, is an information disclosure vulnerability in Microsoft Server Message Block 3.1.1 (SMBv3) protocol due to the way it handles certain requests. Successful exploitation of this vulnerability could lead to information disclosure from a target system which could reveal further attack vectors. Exploiting this vulnerability on a server would require an unauthenticated attacker to send a specially crafted packet to the target SMBv3 server. Exploiting this vulnerability against a vulnerable SMB client would require an attacker to host a maliciously configured SMBv3 server and convince the client to connect to it.
Both of these SMBv3 vulnerabilities follow in the footsteps of CVE-2020-0796, an unauthenticated RCE vulnerability in SMBv3 that was patched in March 2020 as part of an out-of-band update.
CVE-2020-1301 | Windows SMB Remote Code Execution Vulnerability
CVE-2020-1301 is an RCE vulnerability in Microsoft Server Message Block 1.0 (SMBv1) protocol due to the way it handles certain requests. Successful exploitation of this vulnerability could allow an attacker to execute arbitrary code on a target system. Exploitation of this vulnerability would require the attacker to be authenticated and send a specially crafted packet to the target SMBv1 server.
CVE-2020-1286 | Windows Shell Remote Code Execution Vulnerability
CVE-2020-1286 is an RCE vulnerability due to the Windows Shell not properly validating file paths. An attacker could exploit this flaw to execute arbitrary code on a host, subject to the privileges of the current user account. An attacker must entice a user to open a specially crafted file or visit a malicious website designed to exploit this vulnerability.
CVE-2020-1208 and CVE-2020-1236 | Jet Database Engine Remote Code Execution Vulnerability
CVE-2020-1208 and CVE-2020-1236 are RCE vulnerabilities in the Windows Jet Database Engine due to improper handling of objects in memory. Successful exploitation of this vulnerability could execute arbitrary code on a target system. Exploitation of this vulnerability would require an attacker to convince a victim to open a specially crafted file or visit a malicious website.
CVE-2020-1248 | GDI + Remote Code Execution Vulnerability
CVE-2020-1248 is an RCE vulnerability found in the Windows Graphics Device Interface (GDI). The flaw is a result of how GDI handles objects in memory and would allow an attacker to take control of an affected system. Microsoft rates the flaw as “Exploitation Less Likely” and notes that an attacker would need to convince a user to open a crafted file or visit a malicious website in order to exploit this vulnerability.
CVE-2020-1213, CVE-2020-1214, CVE-2020-1215, CVE-2020-1216, CVE-2020-1230, CVE-2020-1260 | VBScript Remote Code Execution Vulnerability
CVE-2020-1213, CVE-2020-1214, CVE-2020-1215, CVE-2020-1216, CVE-2020-1230, and CVE-2020-1260 are RCE vulnerabilities due to the way that the VBScript engine handles objects in memory. Exploitation of these vulnerabilities could result in arbitrary code execution with the same permissions as the current user. There are multiple scenarios where an attacker could exploit these flaws. They include convincing a user to visit a malicious or compromised website, or open a malicious Microsoft Office document.
CVE-2020-1181 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2020-1181 is an RCE vulnerability found in Microsoft SharePoint Server. The vulnerability exists in the way that SharePoint Server mishandles ASP.net requests, allowing an authenticated attacker to execute code as the application’s pool process. The attacker would need to invoke a malicious page from the SharePoint server in order to exploit this vulnerability.
CVE-2020-1300 | Windows Remote Code Execution Vulnerability
CVE-2020-1300 is an RCE vulnerability that exists in Microsoft Windows due to improper handling of cabinet files. Successful exploitation of this vulnerability could allow an attacker to execute arbitrary code on a target system. Exploitation of this vulnerability would require an attacker to convince a victim to open a specially crafted cabinet file or alternatively spoof a network printer and convince a user to install a malicious cabinet file by disguising it as another file, such as a printer driver.
Tenable solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains June 2020.
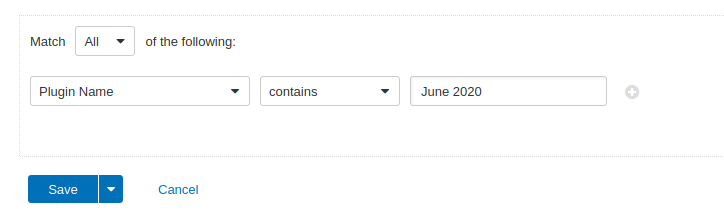
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
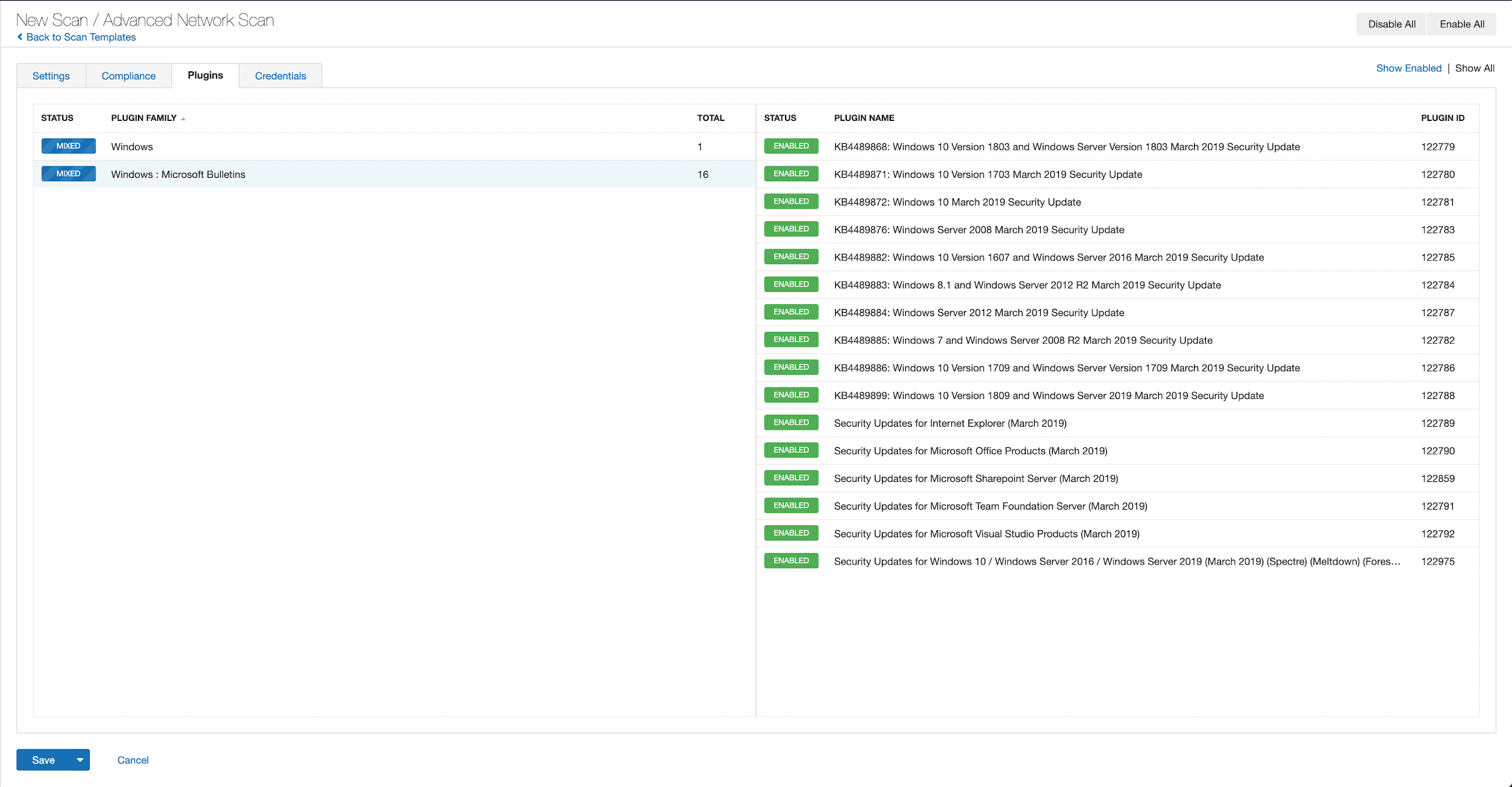
A list of all the plugins released for Tenable’s June 2020 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
- Microsoft's June 2020 Security Updates
- Tenable plugins for Microsoft June 2020 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

