Master Your Security Foundation: Know Your Software

Inventorying and managing the software on your network is foundational to your security. Unmanaged and unauthorized software is a blind spot that increases risk and IT support costs. What you don’t know will hurt you.
Note: The CIS Controls were formerly known as the Center for Internet Security Critical Security Controls (CSC).
According to the Center for Internet Security (CIS) Controls, conducting an Inventory of Authorized and Unauthorized Software is a foundational cyber hygiene control that should be implemented immediately after you Inventory Authorized and Unauthorized Devices. In explaining this second most important control, the CIS instructs organizations to:
Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution.
Other security frameworks and compliance standards share a common thread that recommends identifying all of your software so you can manage it
The CIS is not alone in this recommendation. Other security frameworks and compliance standards echo the importance of knowing your software, sharing a common thread that recommends identifying all of your software so you can manage it. Knowing your software enables you to identify and manage high risk or vulnerable software, block malware and audit license compliance.
|
Standard |
“Know Your Software” Control Objective |
|
PCI DSS |
2.4: Maintain an inventory of systems that are in scope for PCI DSS. |
|
NIST Cybersecurity Framework |
ID.AM-2: Software platforms and applications within the organization are inventoried |
|
ISO/IEC 27002:2013 |
A.12.5.1: Installation for software on operational systems A.12.6.2: Restrictions on software installation |
|
NIST 800-53 rev 4 |
CM-8: Information system component inventory CM-11: User installed software |
Knowing and controlling your software is certainly a control that increases security – detecting and blocking malware and high risk applications reduces your attack surface and can prevent incidents. However, the benefits of knowing and controlling your software extend beyond security. For example, identifying and updating unsupported software versions reduces IT support costs, and can even increase user productivity and license compliance.
Tenable knows your software
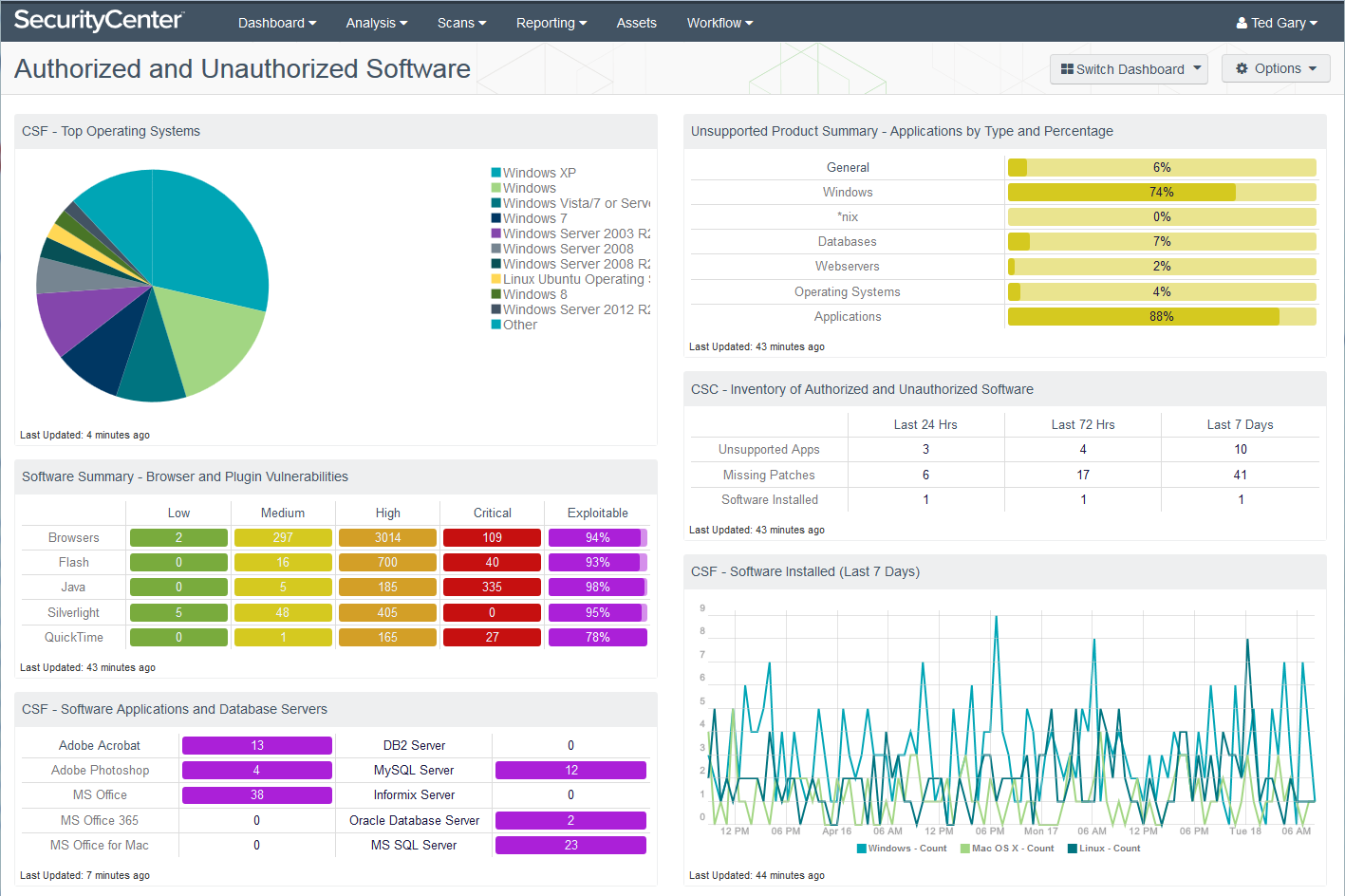
SecurityCenter Continuous View® inventories the software that is installed and running on your network and can identify unsupported software that should be upgraded or removed. I created the custom dashboard shown below using components from two dashboard templates: CIS CSC: Software and Applications and CSF Asset Management - Software. These templates are published by the Tenable research team, and you can use them as is or tailor them, as I have done.
The dashboard contains the following components:
CSF - Top Operating Systems: The list of discovered operating systems shows the most frequently discovered operating system at the top. Unfortunately for me, Windows XP is my most common OS. Obviously I need to upgrade! My demo environment doesn’t include mobile devices, but if it did, they would be listed here.
Software Summary - Browser and Plugin Vulnerabilities: This component helps me determine which browsers and plugins have the most vulnerabilities. Java stands out as having the most critical vulnerabilities and as being the most exploitable. If this happened in your organization, it could indicate you need a stronger policy limiting Java’s use or at least limiting the use of old versions.
CSF - Software Applications and Database Servers: When a software application or database server is detected on the network, the indicator will be highlighted in purple, along with the total number of installations by count. This component can assist you in tracking software licenses for inventory and compliance purposes. Because the range of software applications and database servers can vary among organizations, you can modify this matrix to fit your specific business requirements.
Unsupported Product Summary - Application by Type and Percentage: This bar chart shows the percentage of unsupported applications and operating systems in my demo environment sorted by product type, such as database servers, web servers, operating systems or applications. Again, those pesky Windows XP systems stand out.
CSC - Inventory of Authorized and Unauthorized Software: This table displays software installs, unsupported applications and missing patches within the last 24 hours, 72 hours and 7 days.
CSF - Software Installed (Last 7 Days): This chart presents a trend of software installations within Windows, Linux and Mac OS X operating systems. It reports the number of installations on an OS by count over the last seven days.
Whitelist your applications
The CIS control, Inventory of Authorized and Unauthorized Software, includes a subcontrol (2.2):
...deploy application whitelisting, that allows systems to run software only if it is included on the whitelist and prevents execution of all other software on the system.
Whitelisting is definitely an important control and is described in an excellent publication, NIST SP 800-167: Guide to Application Whitelisting.
Although Tenable does not offer application whitelisting software, we can audit the presence of two popular whitelisting applications:
- Nessus plugin 73149 detects the installation of Microsoft Windows AppLocker
- Nessus plugin 73946 detects the installation of Symantec Critical System Protection
SecurityCenter Continuous View can inform you about systems that are expected to have one of these whitelisting applications installed, but do not.
Learn more
The CIS Controls include four sub-controls that support Inventory of Authorized and Unauthorized Software. A detailed discussion of these sub-controls is beyond the scope of this blog – but we can help you learn more. Tenable is hosting a webinar on May 24th, when we will dive into the control details, show you how Tenable can help and answer your questions. This webinar is the second of a five-part series that will explore each of the CIS Foundational Cyber Hygiene controls. Brian Ventura, a SANS community instructor, will be our expert guest presenter. Brian teaches a 2-day course, Critical Security Controls: Planning, Implementing and Auditing. He has also taught a 5-day course, Implementing and Auditing the Critical Security Controls – in Depth. In addition to presenting valuable content, we will reserve time for questions and answers.
Look for future blogs where I will discuss the remaining Foundational Cyber Hygiene controls:
- Secure configurations for hardware and software
- Continuous vulnerability assessment and remediation
- Controlled use of administrative privileges
- Executive Management
- Security Frameworks
- Center for Internet Security (CIS)
- Threat Management
- Vulnerability Management
- Vulnerability Scanning
- Webinars