How Vulnerable Are You To The Latest IE 0-Day?
Tenable customers can use a combination of active scanning, passive scanning and configuration auditing to gauge their level of risk, progress on workaround implementation and track the remediation process once a patch is released.
Internet Explorer Zero Day Vulnerability
Recently an unpatched vulnerability was discovered in Microsoft's Internet Explorer web browser (including versions Internet Explorer 6 through 11). This remote code execution bug takes advantage of how Internet Explorer handles Flash objects to gain control of the system in the context of the running user.
The new vulnerability hits a pain point for Windows XP users, as Microsoft has ended support, and if they stick to that, no patch will be issued for XP. Currently, Microsoft has not issued a patch for the vulnerability, but here are a few workarounds:
- Perhaps the most obvious is to switch to a different web browser (Such as Chrome or Firefox). However, this is not a viable option for some, as if you are tied to XP you could also likely be tied to Internet Explorer.
- Microsoft is recommending customers install and configure EMET 4.1 to mitigate this attack until such time a patch can be released. However, some mitigations available in EMET do not work on Windows XP (Reference)
- Configure Internet Explorer security zones to "High" - This setting will result in blocking of ActiveX controls, which protects the system from being exploited, but also causes many web sites to become unusable
- Other workarounds suggested are to uninstall Flash from the system and/or de-register select components of Internet Explorer which contain, or could trigger, the vulnerability. Of course, if the systems require Flash, this is not a viable workaround.
How Vulnerable Am I?
Tenable Passive Vulnerability Scanner (PVS) customers can use a host of plugins which provide information about web browsers. The advantage with PVS is this is done passively, and if you are sniffing packets as they go out across the Internet, you can effectively gauge risk. The PVS plugin Microsoft Internet Explorer detection reports on usage and the version of Internet Explorer. PVS also has the upper hand in this scenario as it can detect Internet Explorer in use, even if its running in a VM or an unmanaged system, allowing you to find the gaps in your patch management.
Tenable has several plugins across multiple products that will help you gauge just how vulnerable you are to the vulnerability. For example, you can use the dashboard to show existing web browsers which already have vulnerabilities:
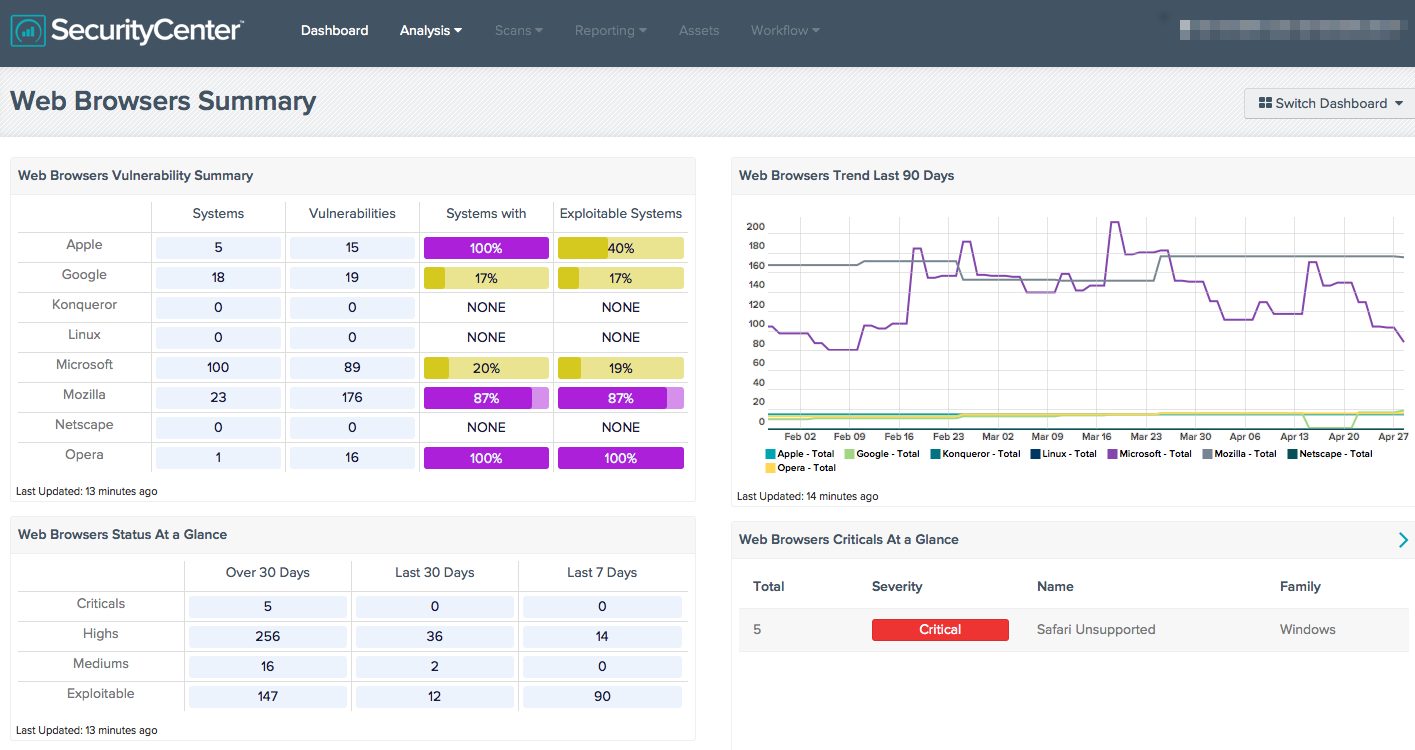
Once a patch has been released by Microsoft, the above dashboard will be extremely helpful in measuring how efficiently the patch is rolling out in your environment.
If you want to know which systems have EMET installed, to estimate the work involved in rolling out a workaround you can use the Nessus plugin titled Microsoft Enhanced Mitigation Experience Toolkit (EMET) Installed.
If you're curious just how many systems have Adobe Flash installed, there is the Nessus plugin titled Flash Player Detection.
Conclusion
Using multiple methods and sources for data collection, Tenable customers can accurately assess the state of the network when new threats are made public. Even though there is not currently a patch available for this vulnerability at the time of this writing, you can begin the remediation process. Whether you implement a workaround or not, having the right information to make the decision is key. Our products can help you gauge the level of effort and level of risk associated with vulnerability remediation and workarounds.
- Dashboards
- SecurityCenter


