How to Take Vulnerability Management to the Next Level and Supercharge Your Career

At Tenable, we believe the next generation of great CISOs and security leaders will arise from those vulnerability management professionals who are driving the shift to exposure management today.
Punti principali
- Vulnerability management is crucial for the evolution toward a more strategic, business-aligned approach to cybersecurity — that’s why these professionals are best positioned to lead the shift to exposure management.
- As the primary source of exposure insights for CISOs, chief risk officers, business leaders, and IT and security teams, you will play the pivotal role in improving communication, driving efficiency, guiding investments, and strengthening the organization's risk posture.
- The deep understanding of assets, risks, and prioritization you get with exposure management puts you in line to be a next-generation security leader.
As a vulnerability management professional you already possess deep knowledge of assets and risk across the attack surface. Add in the ability to provide rich exposure context, and suddenly you’re in a position to deliver strategic, business-aligned insights that can help the entire organization improve risk posture and drive better outcomes. You are better equipped than other security professionals to lead this evolution toward holistic exposure management.
With all the instruments at play, security organizations are a lot like an orchestra. When separate musicians, each one reading their own sheet music, play without awareness of each other, it sounds like a cacophony. There's music in there somewhere, but it's impossible to hear through the noise.
Think about each one of those musicians as a different security silo in your organization. They have their own skills and “instruments” — but lack relational context — so the outcome is less than ideal.
Consider the common attack chain. A simple misconfiguration in a cloud environment may seem harmless in isolation. But if it directly leads to a critical database vulnerability, it exposes sensitive client records. Similarly, a basic web application flaw that provides access to an administrator account without multi-factor authentication (MFA) can give away the keys to the entire kingdom. Attackers expertly exploit these gaps in visibility and context.
As a vulnerability management professional, you know the drill. You may have paved the way for richer context through risk-based vulnerability management (RBVM), factoring in external accessibility, exploitability, and asset criticality. This experience uniquely positions you to step up and orchestrate the future of security.
By becoming an exposure management expert, you can take center stage as the conductor. Exposure management platforms allow you to unify data across siloed tools and access deep relationship context — the connections between assets, identities, risks, and the business.
Armed with the attacker’s view of viable attack paths leading to your organization’s most critical assets, you can help your colleagues in security and IT to focus their remediation efforts on closing off critical choke points.
This context empowers you to deliver business aligned exposure metrics, streamlining communication across constituents — your peers, your department leaders, your CISO, and your business-side colleagues. Everyone will be able to understand how security investments can best improve risk posture. These are essential elements in the toolkit of tomorrow’s security leaders.
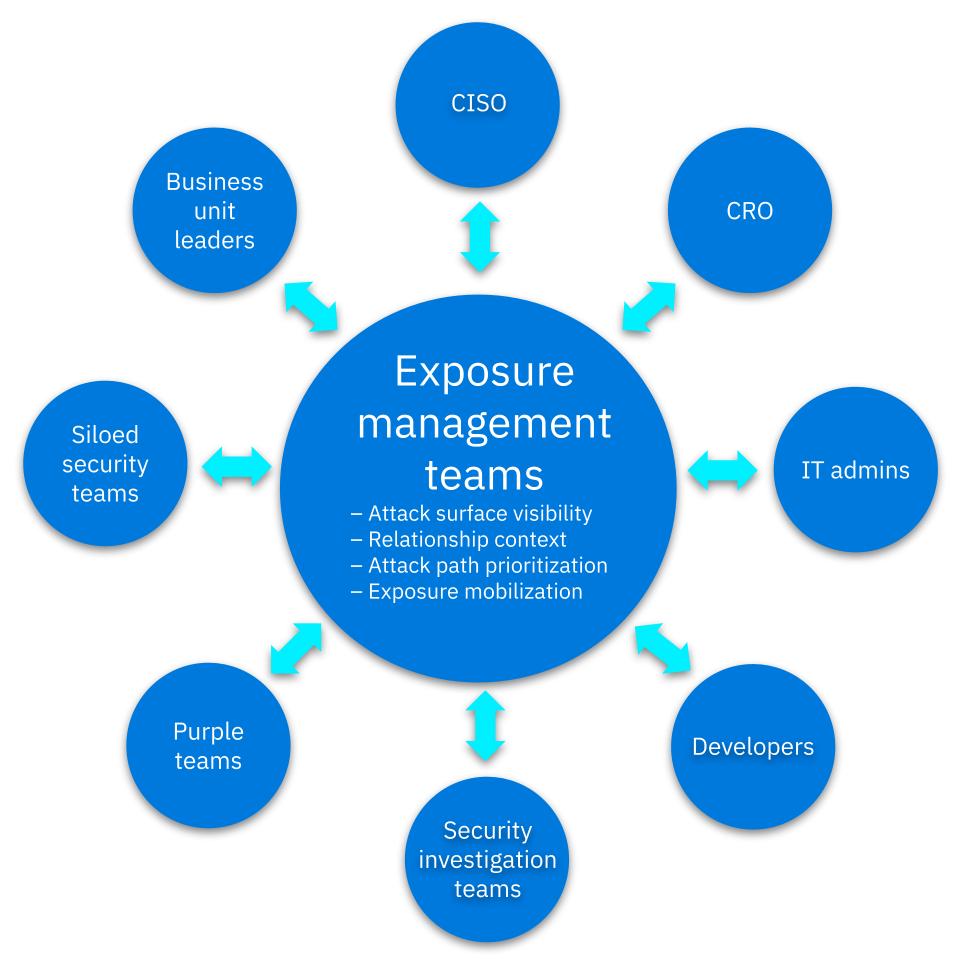
As the conductor, you’ll expand your value, influence, and expertise
It’s easy to talk about how exposure management evolves the scope and focus of vulnerability management teams. But what does that really mean for you and your relationships with security and IT peers, the business, and other leaders?
Let’s look at a variety of roles and their struggles. Equally important, we’ll contrast that with how you, as the conductor, can transform the daily lives of your colleagues while increasing your value, visibility, and impact across the organization.
| Role | Strategic challenge | Your impact |
| Chief information security officer (CISO) | CISO board reporting is often hampered by confusing CVE metrics and patch counts that lack business relevance. | You empower CISOs to communicate business-aligned risk posture and exposure metrics the board easily understands. |
| Chief risk officer (CRO) | CROs are forced to rely on fragmented technical reporting that lacks risk and compliance alignment. | You provide the unified, business- and framework-aligned reporting CROs need to maintain the effectiveness of their governance, risk, and compliance program. |
| Business unit leaders | Leaders struggle to understand security exposure and where to place limited staff and funds. | You provide business unit leaders access to transparent exposure metrics and business-aligned views to justify and prioritize their security investments. |
Siloed security teams (including cloud, operational technology, identity, etc.) | Siloed teams are inundated with endless low-priority findings, which leads to alert fatigue. | You give siloed teams the tools they need to surface the most exploitable and impactful exposures first. |
| IT admins | Admins are overwhelmed by excessive tickets that are siloed and lack context and remediation guidance. | You reduce IT admin ticket noise with choke point prioritization and clear AI-driven remediation guidance. |
| Sviluppatori | Developers receive vague fix requests without understanding urgency or business impact. | You provide clear guidance on priority and business-impacting exposures, along with needed remediations-as-code. |
| Security investigation teams | Teams manually stitch together telemetry data from countless different security and IT tools during investigations. | You provide high-fidelity technical and business context in one place, so teams can speed up investigations and disrupt ongoing attacks. |
| Purple teams | Purple teams have no visibility into asset and risk relationships, and the high-value targets they need to prioritize for testing. | Teams gain a prioritized view of actual attack paths that lead to crown jewels for focused testing of the things that matters most. |
Fonte: Tenable, October 2025
Where do I start? The key to becoming the next great security leader
This moment represents a defining opportunity for vulnerability management professionals. By driving the evolution to holistic exposure management, you become the conductor of the “security orchestra.” The guidance you provide can align security and IT teams, business leaders, and executives with the shared goal of reducing actual business exposure.
We recognize change isn’t easy and building a career path takes time. So, where do you start? Here are two actions you can take beginning today that can help you lead the way from vulnerability management to exposure management:
1. Reframe the problem for security leadership
Tip: Traditional vulnerability management focuses on volume — patch counts, CVSS scores, SLA metrics — without clearly surfacing what truly matters. Exposure management flips the script by prioritizing exploitable risks with real business impact. Use attack path visualizations, crown jewel targets, and risk-to-business narratives to shift the conversation from noise to clarity. Show how exposure management enables board-level reporting with exposure metrics that align with continuity, trust, and regulatory pressure.
2.Connect exposure management to strategic objectives
Tip: Executives care about outcomes: reducing risk, boosting efficiency, supporting compliance, and enabling transformation safely. Exposure management isn’t another tool.It’s a strategic capability that integrates siloed data, applies shared risk context, and drives informed action across teams. Position exposure management as an evolutionary step that respects existing investments while empowering smarter decisions through unified, business-aligned context.
The next post in this series will show you how to apply this strategy pragmatically. We’ll address four of the most pressing challenges facing security programs today: tool and vendor sprawl, blind spots across the external attack surface, unmanaged risks from rapid tech adoption, and the growing burden of alert fatigue.
Scopri di più
See how an exposure management platform like Tenable One can help you overcome these issues by balancing immediate priorities with long-term objectives — without blowing up your budget or disrupting your teams, tools, and processes.
- Exposure Management
- Exposure Management Academy



