Do you have HVAC systems on your internal network?
If you have not heard the news yet, Brian Krebs has reported that the recent Target breach occurred when hackers broke into the network of a company that managed the company's heating, ventilation and air conditioning (HVAC) systems. The intruders leveraged the trust and network access granted to them by Target and then from these internal systems broke into the point of sale (POS) systems and stole credit and debit card numbers, as well as other personal customer information.
We can learn a lot from this incident. In this blog, we will discuss Tenable's approach to identifying HVAC systems, auditing their use, and looking for changes in trust relations and Internet connectivity that indicates abuse.
What is an HVAC system?
In the media, any type of computer associated with making power, managing the lights, or in this case keeping things comfortable for humans, has been referred to as critical infrastructure, a SCADA system, or a control system. In general, the devices are often Microsoft Windows based systems, which are in proprietary hardware formats or run proprietary software.
Previously we've blogged about detecting control systems on your network. Tenable's combination of active scanning with Nessus and passive network monitoring with the Passive Vulnerability Scanner (PVS) allows for real-time discovery of devices associated with HVAC operations.
What does it mean to be connected to my network?
Ideally, your HVAC computer operations and management are done entirely separate from your corporate network used for email, file sharing, video conferencing, etc.
However, Richard Warner, the CEO of OME Facility Solutions, says a trend of connecting a wide variety of critical infrastructure to corporate networks is widespread:
"The last decade has seen a tremendous increase in the number of facility systems connected via standard TCP/IP infrastructure. These systems include but are not limited to HVAC, Electrical, Lighting, Security, Video Surveillance, Fire and Life Safety. While this has precipitated the automation system installation firms to coopt the term 'systems integration', their resources lack the skill sets of resources in the IT domain.
Industry experts indicate that nearly 50% of all new construction projects have facility automation systems that share network infrastructure with the corporate or business LAN. For the remaining systems that are installed on independent infrastructure, a large percentage have a connection point to the corporate LAN to facilitate access or information connectivity."
There have also been instances where HVAC equipment has been connected directly to the Internet. There are many examples of security researchers who have leveraged tools like Shodan to look for web servers associated with SCADA and other control systems. If these Internet facing systems are connected directly to the Internet and the internal corporate network, it could be a potential attack path.
So what?
Having HVAC connectivity from a trusted third party may not present the same level of risk as one connected directly to the Internet, but if you don't know about either one, you can't manage the risk that comes with it.
HVAC Windows systems are often "unmanaged" and difficult to patch. For a user who has run Nessus, scanning an HVAC system could look like a very out of date Windows server that has very old or missing patches.
For attackers who leverage weak passwords, known HVAC passwords, or Windows exploits that are many years old, they can readily compromise these devices. HVAC systems that have embedded technologies like RuggedOS also have had a wide variety of security issues which can be exploited.
A Live Example With Tenable SecurityCenter Continuous View
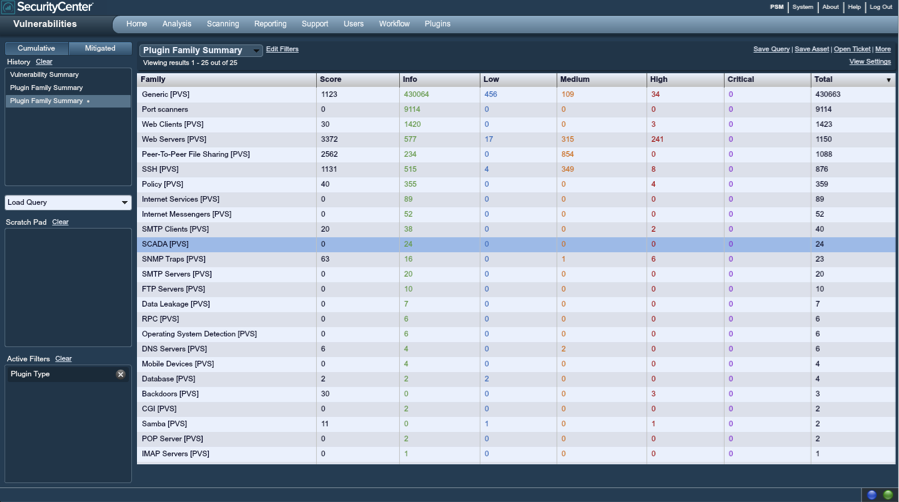
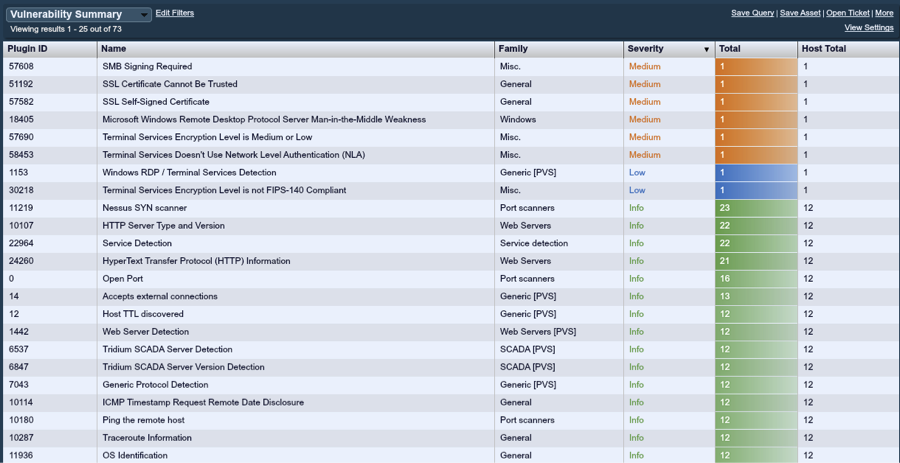
Below is a screenshot of a small enterprise that has deployed Tenable's Passive Vulnerability Scanner, Nessus, and the Log Correlation Engine (LCE). In this view, we've identified through passive network analysis that there have been 24 different "SCADA" plugins triggered on this network. This likely means that 24 different SCADA devices have been found by the PVS.
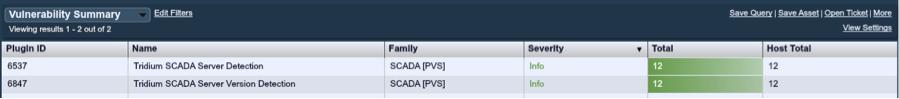
Summarizing these 24 SCADA plugins with the SecurityCenter Vulnerability Summary tool, we can see that 12 Tridium SCADA Server Detection plugins have fired, as well as an additional 12 Tridium SCADA Server Version Detection plugins.
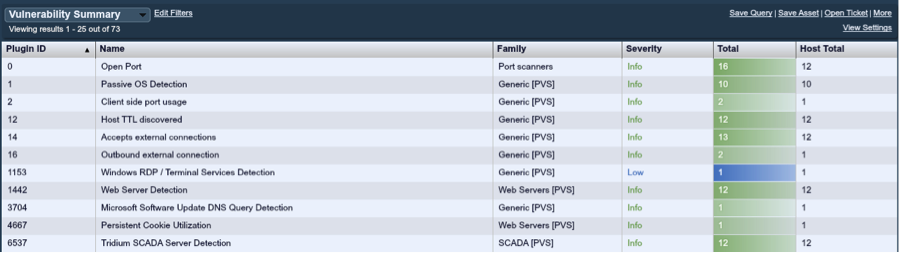
The PVS detects items based on network traffic. The more it learns about a service, the more accurate it can be at reporting plugins. In the case of these two plugins, one is a general detection of Tridium SCADA Servers, and the second reports the version of the actual web server found.
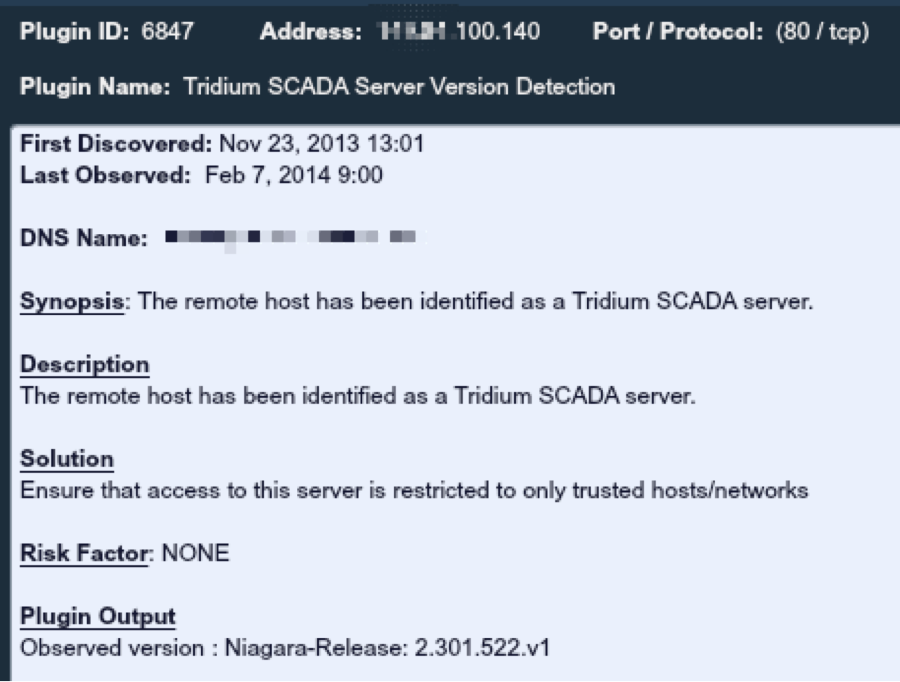
Below is a sanitized screenshot of one of the detailed reports of the device:
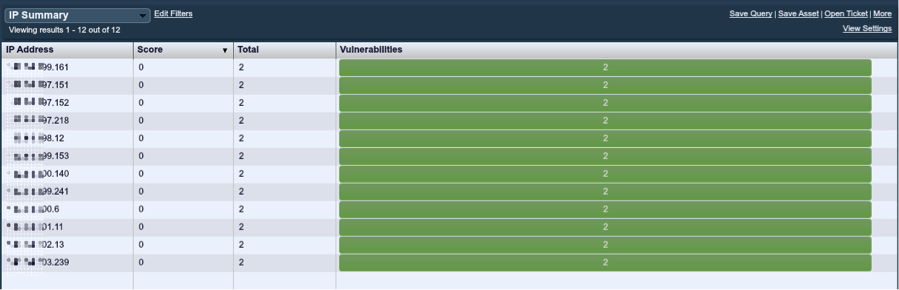
Leveraging the IP Summary tool, we can see the sanitized list of the Tridium systems in question below:
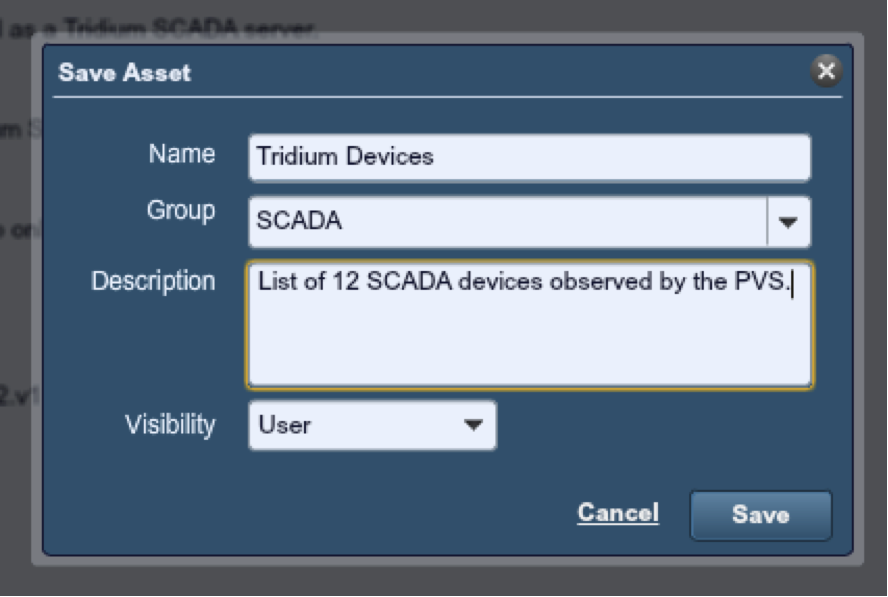
To perform some more analysis, we saved this list of IP addresses as an asset list and named it "Tridium Devices". SecurityCenter can be configured to automatically create an asset list based on plugins like this such that the list is updated in real-time as Nessus, the PVS or the LCE find new information.
Now that we have the asset list, we can ask some very interesting questions.
Does the Tridium Devices asset list contain any vulnerabilities?
To determine this, we would ask SecurityCenter to list all vulnerabilities associated with the IP addresses on this list as shown below.
This display combines results from both the PVS and Nessus. It shows a variety of Nessus scan results, which indicate Windows Terminal Services and some medium level SSL and SMB issues.
Do these Tridium devices have connectivity to the Internet?
The PVS records a variety of network connectivity information about each system it has observed, with specific plugin reports:
For this particular asset, there are three plugins that are of interest:
- #2 Client Side Port Usage – This plugin records on which ports a system has been seen browsing the local network or Internet. The fact that there are two of these plugins on one host means that this host has browsed other systems on two unique ports. The ports in question were 20480 and 47873.
- #14 Accepts External Connections – This plugin records when a system has been observed accepting a connection from a source outside of the local network. In this case, all 12 SCADA systems had this plugin yet there were 13 plugins, meaning that one system had connectionections on more than one port.
- #16 Outbound External Connection – This plugin is similar to plugin #2, but only records Internet outbound connections and not internal ones. Since this plugin has the same host count and plugin count as #2, this indicates that all of the connectivity on this device is Internet-facing and not internal to the network.
Do these Tridium devices have any internal connections?
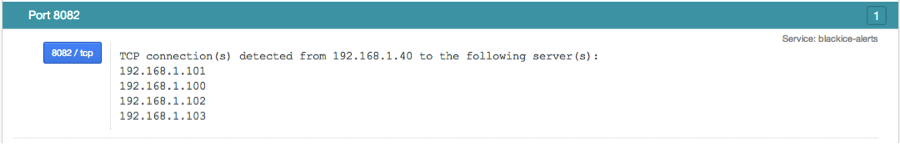
PVS also has a set of plugins that track the list of all IP addresses each host connects to per port. For example, in my lab, host 192.168.1.40 connects to four other IP addresses:
PVS tracks client–to-server and server-to-client relationships for each unique TCP port. This data is reported in plugins #3 "Internal client trusted connection" and #15 "Internal server trusted connection".
Since neither of these plugins were present for the Tridium devices we've been monitoring, we know that there have not been any internal connections observed by the PVS.
Performing this type of analysis is covered extensively in the paper, "Predicting Attack Paths". This paper identifies a wide variety of techniques to track which sets of assets connect to other sets of assets as a form of risk prioritization. For example, the paper shows how to identify which assets are administrator desktops, and which systems they perform administration for and could in turn be compromised if an administrator desktop was also compromised.
Conclusion
Tenable's scanning, sniffing and logging solutions can comprehensively identify a wide variety of protocols, including those associated with SCADA devices. The SecurityCenter Continuous View solution can further automate the detection of SCADA devices and alert if there are connections to your internal network or other attack paths which may allow attackers to bypass your firewall and malware defenses.
- Plugins
- SCADA
- SecurityCenter