Do Not Take an IP-centric Approach to Attack Surface Mapping

Relying on IP data to identify assets means you're likely missing critical information needed to map your attack surface.
While many security tools scan and produce data based on IP addresses, it is an arduous process. It relies on companies knowing the IPs of all of their assets, including legacy and shadow assets. Many vendors and tools pass off the hidden cost of finding each of these assets' IP to companies employees by forcing them to identify the IPs in question.
IP data misses vital asset information
The easiest way to gather HTTP data on a wide swath of IP addresses is to connect to the IP addresses and issue a GET request. However, depending on how you connect and send the request it will yield widely different and unhelpful results. Let’s walk through a few examples:
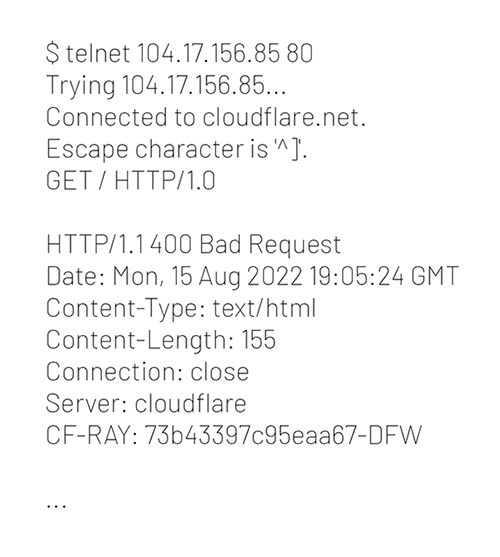
- Connect to an IP address and do not send "Host" header. Without sending the "Host" header, the application server does not know what to do, or what you would like to contact. Below is an example:
- Complete the same request, but send "Host" headers. Including the "Host" header and the cloud-based web application firewall (WAF) it's now possible for the request to understand that you want to reach the server that the WAF is protecting. Here's what that may look like:
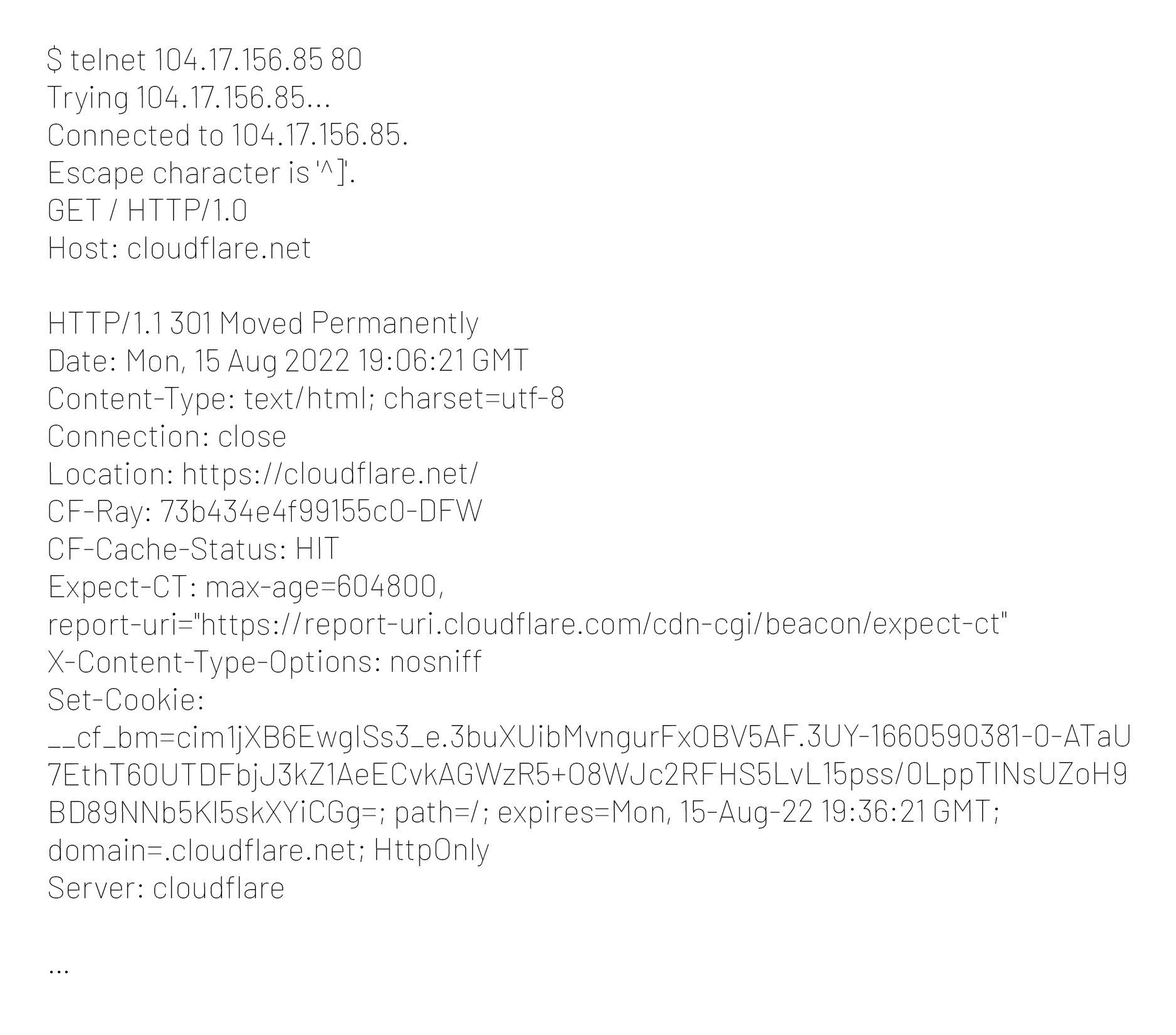
The above example is a very popular cloud-based WAF called Cloudflare that protects millions of machines. Now, those millions of machines are missed in your collection process.
When a scanner connects to an IP address, it only knows what you tell it. If you connect to an IP address without sending a "Host" header, the system will not elicit useful application logic.
Content Delivery Network (CDN) and WAF providers use a minimal amount of IP space. Many leverage tricks with "Host" headers and SSL/TLS certificates to host enormous amounts of web applications from a disproportionately small amount of IP space. This practice aims to relieve administrative constraints and reduce the costs of buying up large swaths of IP space.
However, even smaller organizations and completely unknown applications leverage VirtualHosts to host two or more web applications on the same IP address. That means there is a significant amount of application logic not exercised by the average IP scanner.
Adopt a DNS-based scanner
As a result, most of your attack surface is hidden from an IP-based (versus DNS-based) scanner, including dangerous application logic, insecure cookies, links to old social profiles, out-of-date JavaScript libraries and more. Attackers can leverage these overlooked assets while moving through your architecture.
Utilize DNS to make numerous requests to a singular IP address gathering detailed information. In the case of round-robin DNS, it's essential to make the requests to all the IP addresses helping the scanner identify each asset's application logic.
Using IP data alone is ineffective at identifying what type of application logic and services are running on IP addresses. While IP data is relevant it should only be used as a supplement to find shadow IT.
If organizations happen to know their IP space they should upload it, to get the most coverage, but only after they've uploaded their domains. Don't miss out on critical assets by relying on an IP-only approach for attack surface mapping.
Learn more
Gain visibility across your entire attack surface with Tenable.asm.
- Attack Surface Management

