Cybersecurity Snapshot: Find MITRE ATT&CK Complex? Need Help Mapping to It? There’s an App for That!

Learn about a new tool that streamlines MITRE ATT&CK mapping. Plus, known vulnerabilities remain a major cyber risk – just ask LastPass. Also, discover why SaaS data protection remains difficult. Plus, a look at the U.S. National Cybersecurity Strategy. And much more!
Dive into six things that are top of mind for the week ending March 10.
1 - Struggling with the MITRE ATT&CK framework? New CISA ‘Decider’ tool aims to help
Do you use MITRE ATT&CK to help you better detect and respond to cyberattacks? If so, you might want to check out a new tool designed to help cyber teams map adversary behavior to this popular framework.
The free tool is a web app called Decider that organizations must host themselves. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) created it in partnership with the Homeland Security Systems Engineering and Development Institute (HSSEDI) and MITRE.

(Source: CISA, March 2023)
Decider is intended to help network defenders, threat intelligence analysts and security researchers use the MITRE ATT&CK framework more efficiently and effectively, and thus understand attacker actions faster and more precisely, according to CISA.
“Decider helps make mapping quick and accurate through guided questions, a powerful search and filter function, and a cart functionality that lets users export results to commonly used formats,” reads CISA’s announcement.
In a companion blog, Bonnie Limmer, CISA’s chief of production at the Joint Cyber Defense Collaborative, explained that many MITRE ATT&CK users experience difficulty mapping adversary behavior to the framework. Thus, Decider was built to be easy to use and understand “with minimal technical language.”
To get more details, check out the Decider fact sheet and this explainer video.
For more information about MITRE ATT&CK:
- MITRE ATT&CK main page
- “What is the MITRE ATT&CK framework?” (TechTarget)
- “The changing role of the MITRE ATT&CK framework” (CSO Online)
- “CISA updates MITRE ATT&CK framework mapping” (Tenable)
- “MITRE ATT&CK framework: Understanding attack methods” (CSO Online)
VIDEOS
MITRE ATT&CK Framework (MITRE)
What is Threat-Informed Defense? (MITRE)
MITRE ATT&CK: Benefits and Challenges (TechTarget)
2 - Tenable report highlights threats from years-old, known vulnerabilities
They’re the proverbial low-hanging fruit of the cyber world: Vulnerabilities disclosed months and years ago for which patches have long been available but that many organizations haven’t yet fixed.
Because attackers continue to exploit these known flaws in great numbers, Tenable’s Security Response Team (SRT) is shining a spotlight on them in its newly released “Threat Landscape Report” (TLR).

Specifically, SRT ranked first on its list of top vulnerabilities of 2022 a set of these flaws, some of which date back to 2017, including high-severity bugs in Microsoft Exchange, Zoho ManageEngine products and VPN solutions from Fortinet, Citrix and Pulse Secure.
“We cannot stress this enough: Threat actors continue to find success with known and proven exploitable vulnerabilities that organizations have failed to patch or remediate successfully,” the report reads.
Why does this problem persist? As Tenable Chief Security Officer and Head of Research Robert Huber explains in the report, security teams struggle with vulnerability remediation for multiple reasons, including having a plethora of siloed cybersecurity tools that offer a limited, fragmented view of their attack surface.
Because vulnerability management (VM) can no longer be performed in a vacuum, organizations must build an exposure management program that allows organizations to execute a risk-based workflow.
“Exposure management offers a way to operationalize risk reduction across an organization – and offers a vision of a future in which we no longer see five-year-old vulnerabilities continue to be exploited like a ‘greatest hits’ collection in the attacker playlist,” Huber wrote.
To get more details, you can check out the full report, read an SRT blog post and attend a webinar on March 16 at 11 am PT / 2 pm ET.
You can also find coverage of the Tenable TLR in Help Net Security, CSO Online, My Tech Decisions, BetaNews and GCN.
3 - And speaking of known vulnerabilities that haven’t been remediated …
More details have come out about last year’s massive breach of password manager LastPass, and the new information reinforces the danger from years-old, known vulnerabilities that are left unremedied.
Here’s the latest: An attacker breached the home computer of a LastPass DevOps engineer by exploiting a known vulnerability in the Plex Media Server. Plex had disclosed the bug in May 2020, at which time it also patched it by releasing a new version of the software. The bug (CVE-2020-5741) was reported to Plex by Tenable in March 2020.

At the time of the attack, the LastPass engineer reportedly hadn’t yet installed that Plex update nor any of the many other subsequent updates Plex released for the product in question in the interim.
“Unfortunately, the LastPass employee never upgraded their software to activate the patch. For reference, the version that addressed this exploit was roughly 75 versions ago,” a Plex representative told PCMag.
To get all the details about the two incidents that led to the data breach, including the theft of encrypted customer passwords, read the latest post mortem from LastPass, published last week.
Meanwhile, the details about the specific Plex vulnerability, which isn’t mentioned in the LastPass updates, were confirmed publicly by Plex to several technology publications, including PCMag, The Hacker News and ReviewGeek.
For more information about the LastPass issue:
- “LastPass aftermath leaves long to-do list for business customers” (Cybersecurity Dive)
- “LastPass says hackers stole customers’ password vaults” (TechCrunch)
- “LastPass breach exposes how US breach notification laws can leave consumers in the lurch” (CyberScoop)
- “The LastPass disclosure of leaked password vaults is being torn apart by security experts” (The Verge)
- “LastPass Shouldn't Be Trusted With Your Passwords” (Motherboard)
VIDEOS:
Anatomy of a Threat: 2022 LastPass Breach Was Caused by Known Plex Software Vulnerability (Tenable)
LastPass Incident Update March 2023: The Simple Mistake They Made (Lawrence Systems)
LastPass Hack Incident Update (TWiT Tech Podcast Network)
4 - Report: Organizations struggle with SaaS data protection
Protecting software-as-a-service (SaaS) data remains a challenge due in large part to organizations’ lack of understanding about who is responsible for it and how to do it.
Weak SaaS data protection is progressively becoming a bigger problem as organizations boost their adoption and usage of SaaS apps, relying on them for increasingly critical business processes.
That’s according to Enterprise Strategy Group’s (ESG) “Data Protection for SaaS” study, based on a survey of almost 400 IT pros in the U.S. and Canada who are familiar with and/or responsible for SaaS data protection technology decisions.
Key findings include:
- 33% of organizations rely on their SaaS vendors exclusively for protecting their SaaS data
- 55% have lost SaaS data in the past 12 months
- Two leading causes of SaaS data loss are SaaS service outages (cited by 35% of respondents) and cyberattacks (34%)
- Protecting SaaS applications is a top 5 priority for 89% of IT organizations over the next 12-24 months
“Do not confuse service uptime with your ability to recover data that has been corrupted. Based on our research, it is obvious that many IT professionals do not really understand what the roles and responsibilities actually are,” wrote ESG analyst Christophe Bertrand in the TechTarget article “Data protection for SaaS-based apps is a work in progress”.
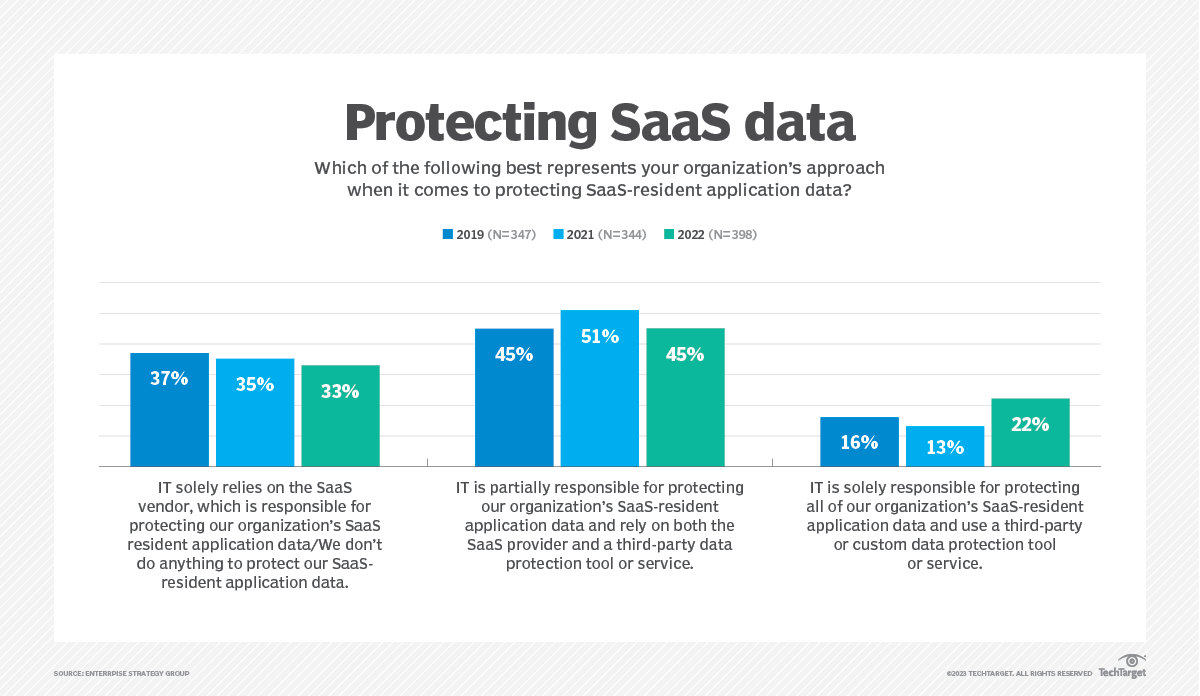
(Source: Enterprise Strategy Group’s “Data Protection for SaaS” report, February 2023)
Some of Bertrand’s data-protection recommendations to SaaS customers include:
- Be clear what falls under your responsibility and what’s the responsibility of your vendors
- Understand the business and compliance consequences of a SaaS service outage or data loss
- Have storage backup and recovery in place for your SaaS applications, especially those used for critical business processes
For more details, view a report infographic and check out the report’s summary page.
To get more information about SaaS security:
- “SaaS Security Risk and Challenges” (ISACA)
- “SaaS Governance Best Practices for Cloud Customers” (Cloud Security Alliance)
- “Cloud Security: 3 Things InfoSec Leaders Need to Know About the Shared Responsibility Model” (Tenable)
- “Best practices for negotiating a SaaS SLA” (TechTarget)
- “Cloud Security Basics: Protecting Your Web Applications” (Tenable)
VIDEOS
6 Steps to SaaS Security (Steve Murphy)
Untangling SaaS Security in the Enterprise (RSA Conference)
5 - Staying on the cloud security topic …
At a recent Tenable webinar about assessing multi-cloud environments for security policy violations, we polled attendees on their main cloud compliance concerns and on their cloud security audit methods. Check out the results!
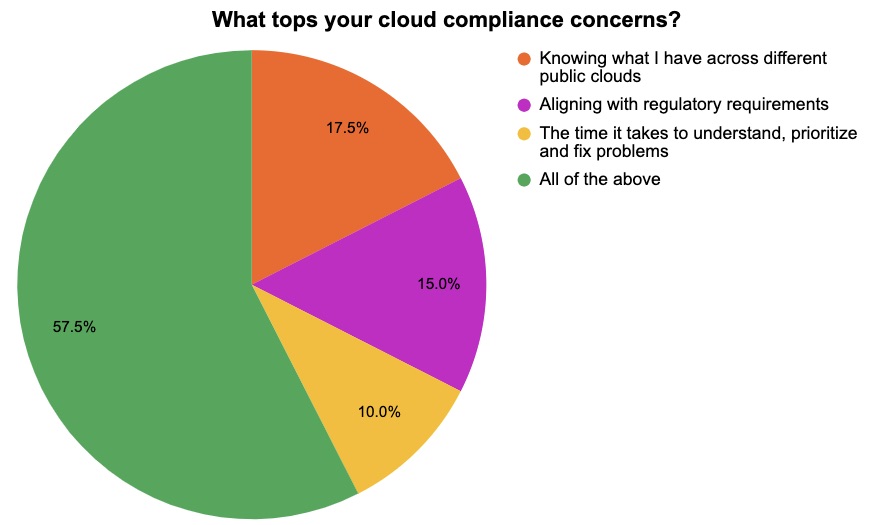
(40 webinar attendees polled by Tenable in February 2023)
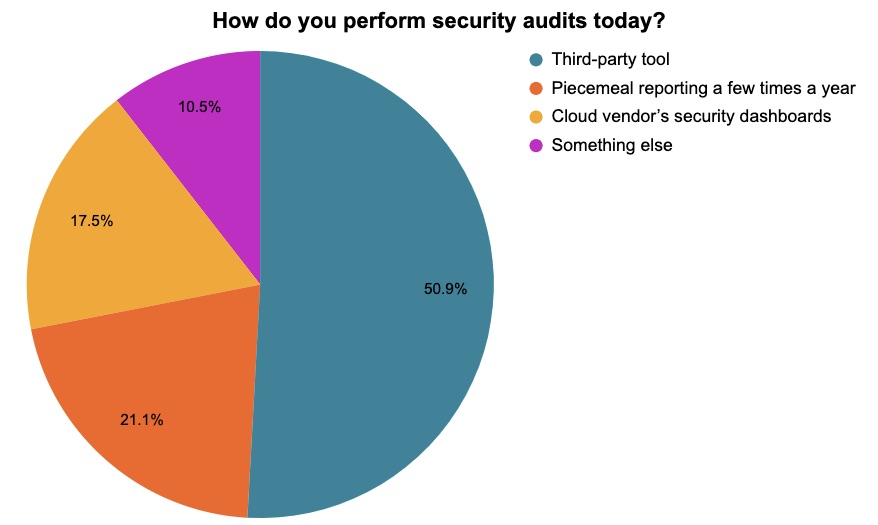
(57 webinar attendees polled by Tenable in February 2023)
6 - U.S. national cybersecurity plan seeks to make tech vendors more accountable
The White House has released its much-awaited National Cybersecurity Strategy, a 35-page policy document whose call to shift more cyberdefense responsibility onto system operators and technology providers has gotten the most attention.
The White House states that end users – individuals, small businesses, infrastructure operators, and state and local governments – currently carry too much of the burden regarding cyber risk mitigation, given their limited resources and their other priorities.
“A single person’s momentary lapse in judgment, use of an outdated password, or errant click on a suspicious link should not have national security consequences,” the White House document reads.

Instead, when it comes to protecting data and securing critical systems, the onus should be on the “most capable and best-positioned actors” in both the public and private sectors – namely system owners and operators, as well as technology providers.
The document specifically calls out software makers, saying they should be held legally accountable when they release products or services that were developed without following security best practices.
Overall, the National Cybersecurity Strategy identifies five pillars for enhancing the cybersecurity of the U.S. “digital ecosystem”:
- Defend critical infrastructure
- Disrupt and dismantle threat actors
- Shape market forces to drive security and resilience
- Invest in a resilient future
- Forge international partnerships
For more information, check out the full National Cybersecurity Strategy document as well as a White House fact sheet, along with coverage from Enterprise Security Tech, Dark Reading, Inside Cybersecurity, FCW and CyberScoop.
VIDEOS
The Biden-Harris Administration’s National Cybersecurity Strategy (Center for Strategic & International Studies)
Biden administration rolls out new cybersecurity strategy (Yahoo Finance)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Threat Intelligence
- Threat Management
- Vulnerability Management


