CVE-2023-29357, CVE-2023-24955: Exploit Chain Released for Microsoft SharePoint Server Vulnerabilities

A proof-of-concept exploit chain has been released for two vulnerabilities in Microsoft SharePoint Server that can be exploited to achieve unauthenticated remote code execution.
Update October 2: The Identifying affected systems section has been updated to include additional Tenable product coverage.
Background
On September 25, STAR Labs researcher Nguyễn Tiến Giang (Jang) published a blog post outlining the successful chaining of CVE-2023-29357 and CVE-2023-24955 to achieve remote code execution (RCE) against Microsoft SharePoint Server. The exploit chain was demonstrated at the Zero Day Initiative’s (ZDI) Pwn2Own contest held in Vancouver in March.
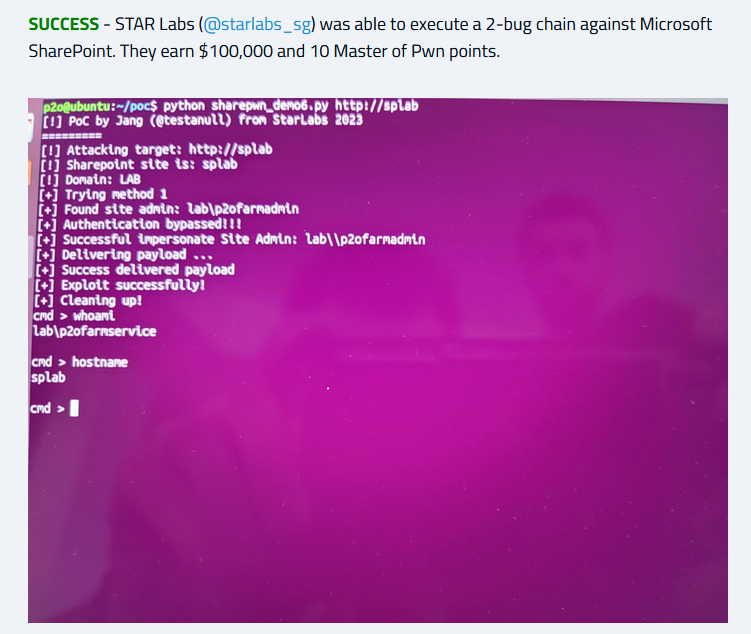
Image Source: Zero Day Initiative, March 2023
On September 26, a proof-of-concept (PoC) for the exploit chain was released on GitHub. The authors of the PoC point out that RCE is not achievable with the current PoC in order to “maintain an ethical stance.” However malicious actors often take advantage of public PoC code and incorporate them into attack tools, so we encourage patching these vulnerabilities as soon as possible.
Analysis
CVE-2023-29357 is an elevation of privilege (EoP) vulnerability in Microsoft SharePoint Server that was assigned a CVSSv3 score of 9.8 and rated critical. A remote, unauthenticated attacker can exploit the vulnerability by sending a spoofed JSON Web Token (JWT) authentication token to a vulnerable server giving them the privileges of an authenticated user on the target. According to Microsoft’s advisory, no user interaction is required in order for an attacker to exploit this flaw. This vulnerability was patched during Microsoft’s June 2023 Patch Tuesday release.
CVE-2023-24955 is a RCE vulnerability affecting Microsoft SharePoint Server. The vulnerability was assigned a CVSSv3 score of 7.2 and could allow an authenticated Site Owner to execute code on an affected SharePoint Server. This RCE was patched as part of the May 2023 Patch Tuesday release.
Both of these vulnerabilities are credited to Jang and were reported to Microsoft by ZDI in coordination with the researcher.
Creating the exploit chain
According to the STAR Labs blog post, nearly a full year of research efforts went into crafting the exploit chain. By combining an authentication bypass (CVE-2023-29357) with a code injection vulnerability (CVE-2023-24955), Jang was able to achieve unauthenticated RCE. A video demonstration of the attack chain can be found on YouTube.
Solution
Both of these vulnerabilities have been patched by Microsoft as part of the May and June 2023 Patch Tuesday releases. We recommend applying the patches as soon as possible. While the currently released PoC does not achieve RCE out of the box, it's likely that threat actors will be able to modify the exploit and weaponize it for malicious use.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here.
Additionally, two new subscriptions have been released for Tenable Attack Surface Management (formerly Tenable.asm):

For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- STAR Labs Blog:[P2O Vancouver 2023] SharePoint Pre-Auth RCE chain (CVE-2023-29357 & CVE-2023-24955)
- Tenable Blog: Microsoft’s June 2023 Patch Tuesday Addresses 70 CVEs (CVE-2023-29357)
- Tenable Blog: Microsoft’s May 2023 Patch Tuesday Addresses 38 CVEs (CVE-2023-29336)
Change Log
Update October 2: The Identifying affected systems section has been updated to include additional Tenable product coverage.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management

