CVE-2019-17558: Apache Solr Vulnerable to Remote Code Execution Zero-Day Vulnerability

Apache Solr remained vulnerable to a zero-day weeks after proof-of-concept code became public for CVE-2019-17558.
UPDATE 12/31/2019: The background and solution sections below have been updated to reflect the recent security update released by Apache.
Background
On October 29, a proof of concept (PoC) for a remote code execution (RCE) vulnerability in Apache Solr, a popular open-source search platform built on Apache Lucene, was published as a GitHub Gist. At the time this blog post was published, this vulnerability did not have a CVE identifier and no confirmation or indication of a solution available from Apache. However, Apache recently announced releases of Solr to address this vulnerability, which is now identified as CVE-2019-17558. Tenable Research confirmed that Apache Solr versions 7.7.2 through 8.3 were vulnerable at the time this blog post was originally published. After the announcement from Apache was released, we can now confirm versions 5.0.0 to 8.3.1 are affected.
Analisi
According to the PoC, an attacker could target a vulnerable Apache Solr instance by first identifying a list of Solr core names. Once the core names have been identified, an attacker can send a specially crafted HTTP POST request to the Config API to toggle the params resource loader value for the Velocity Response Writer in the solrconfig.xml file to true.
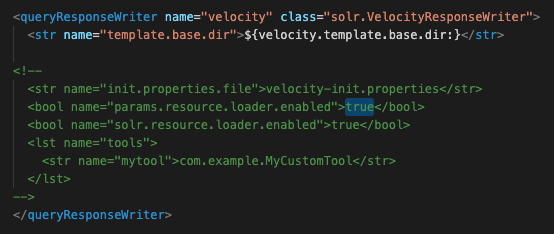
Enabling this parameter would allow an attacker to use the velocity template parameter in a specially crafted Solr request, leading to RCE.
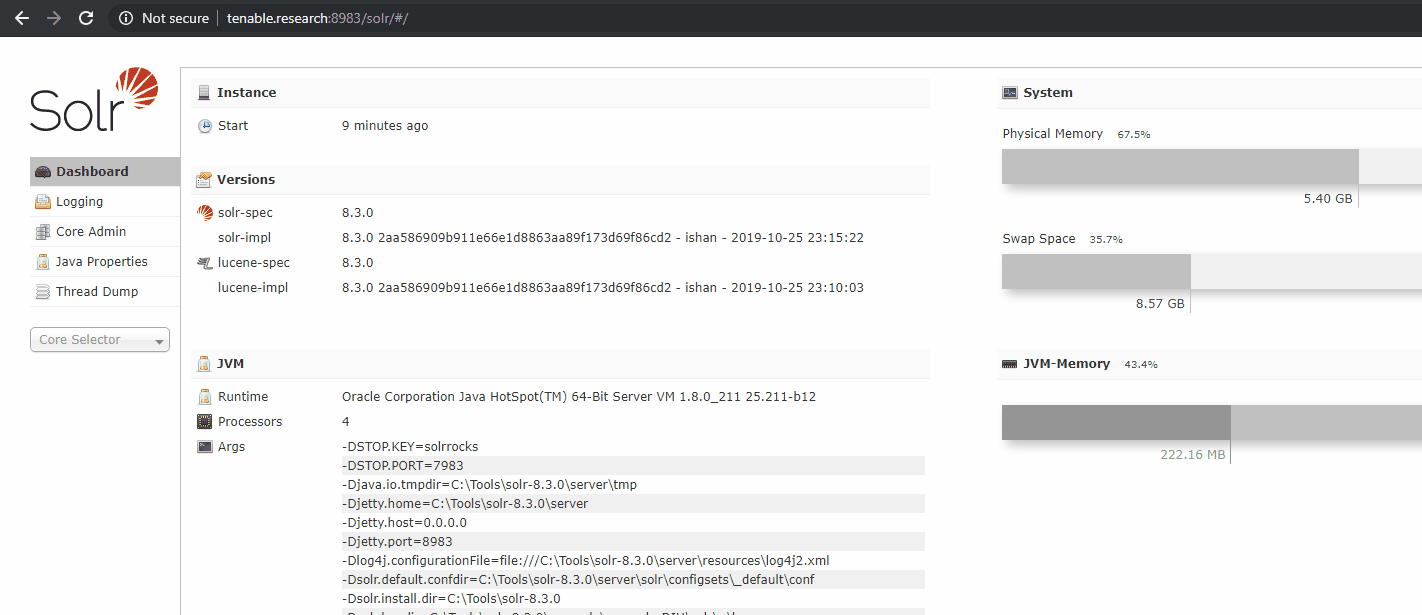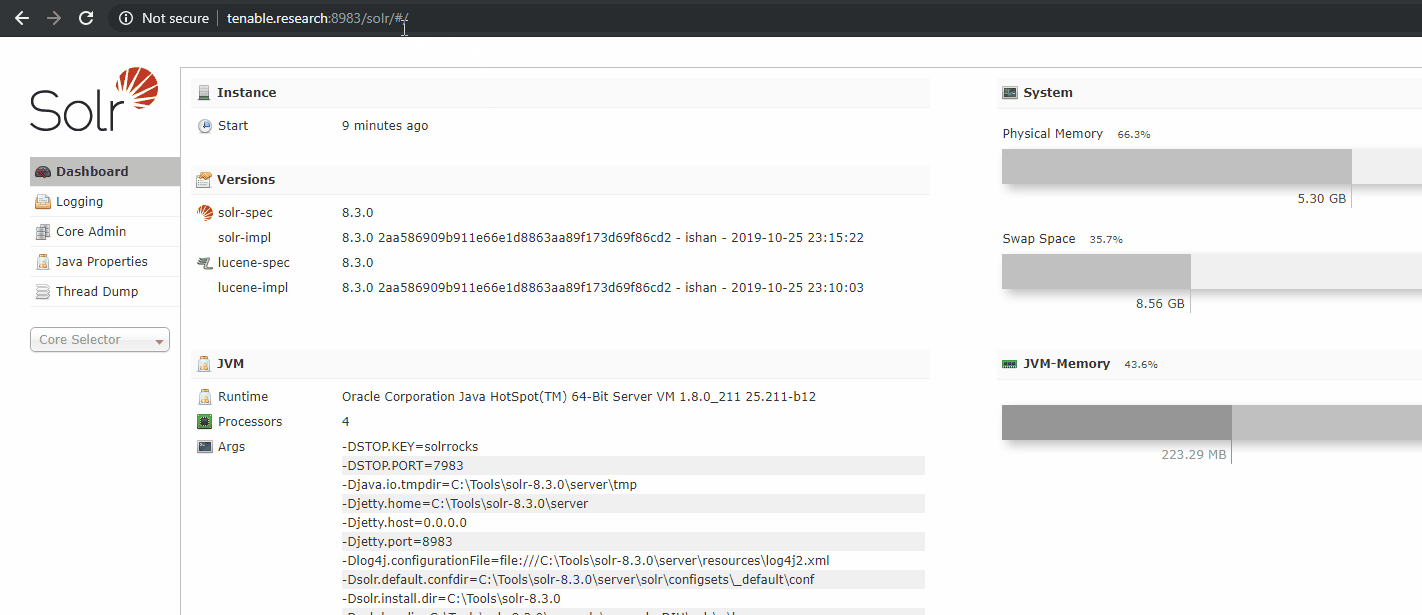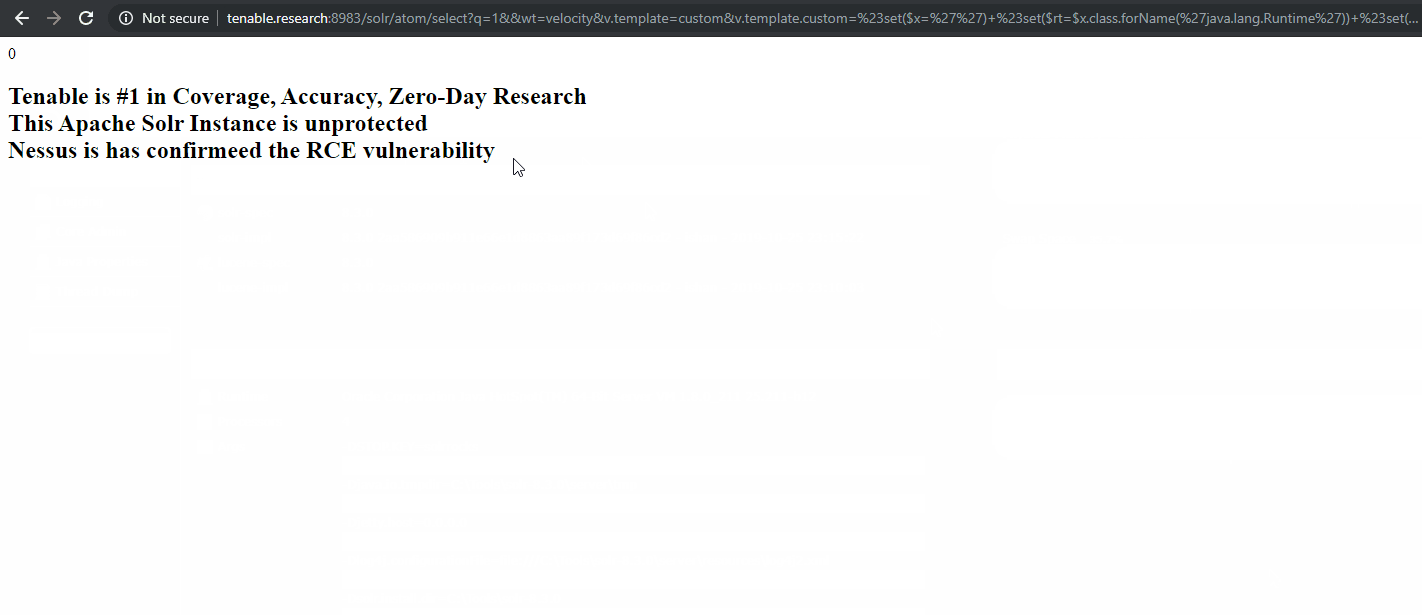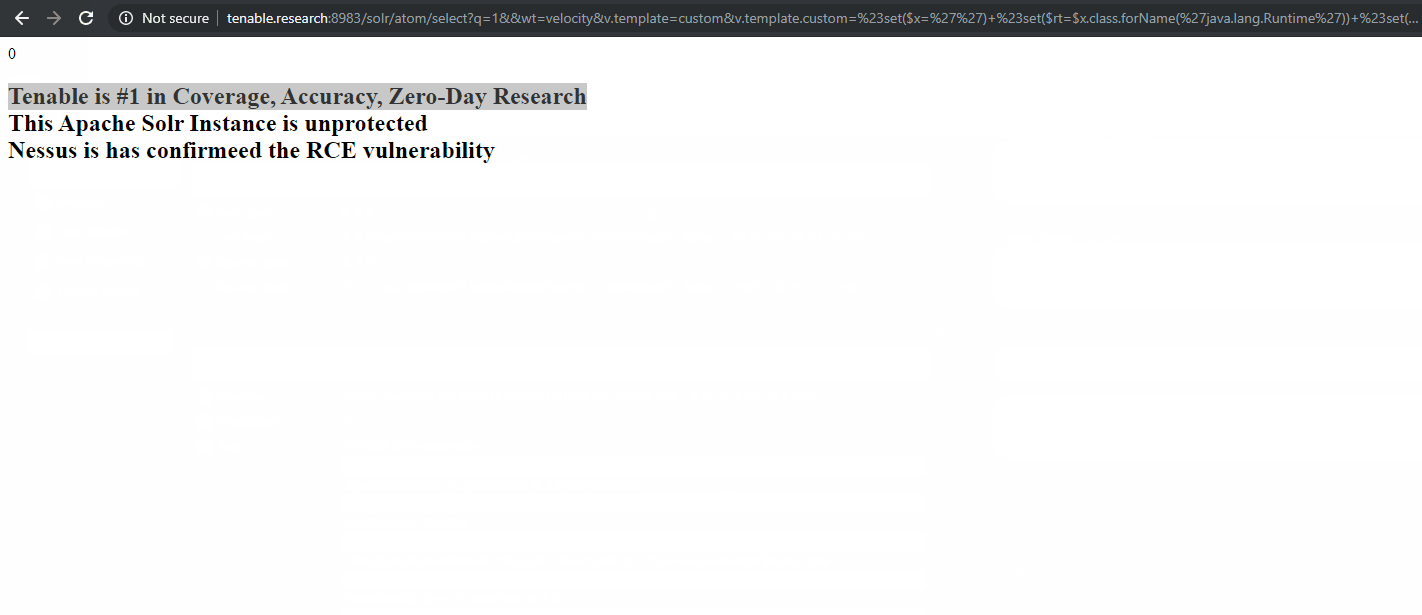
Despite the recent release of Apache Solr 8.3 that addresses a default configuration flaw that was reported back in July, this flaw remained a zero-day until December 29.
Proof of concept
As mentioned previously, a PoC was published on October 29 as a Github Gist. Days later, an exploit script was published to a GitHub repository.
Soluzione
On December 3, Apache released Solr version 8.3.1, which reportedly addressed CVE-2019-17558 as referenced in SOLR-13971. However, following the release of 8.3.1, researcher Peter Cseh of Cloudera reported the fix as incomplete to the Apache Solr team, resulting in the hardening of VelocityResponseWriter as part of Solr version 8.4. According to the advisory, “Solr 8.4 removed the params resource loader entirely, and only enables the configset-provided template rendering when the configset is `trusted` (has been uploaded by an authenticated user).”
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- s00py’s GitHub Gist for Apache Solr RCE (Velocity Template)
- jas502n's Exploit Script for Apache Solr RCE (Velocity Template)
- Apache Solr Security Notices
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

