Copy-Paste Compromises: Threat Actors Target Telerik UI, Citrix, and SharePoint Vulnerabilities (CVE-2019-18935)

Threat actors utilize publicly available proof of concept code and exploit scripts to target unpatched vulnerabilities within organizations and government entities.
Background
On June 19, the Australian Cyber Security Centre (ACSC) published Advisory 2020-008 in response to reports that threat actors were targeting Australian government agencies and companies. The full advisory includes information about multiple vulnerabilities the threat actors have been leveraging to target governments and organizations:
| CVE | Product | CVSSv3 |
|---|---|---|
| CVE-2019-18935 | Telerik UI for ASP.NET AJAX | 9.8 |
| CVE-2019-19781 | Citrix Application Delivery Controller (ADC) and Gateway | 9.8 |
| CVE-2019-0604 | Microsoft SharePoint | 9.8 |
The advisory states that this threat actor is leveraging public proof of concept (PoC) code as part of their attacks. It also highlights the spear-phishing campaigns along with insights into the tools, techniques and procedures (TTPs) utilized by this particular threat actor.
Analysis
Telerik UI for ASP.NET AJAX
CVE-2019-18935 is an insecure deserialization vulnerability in Telerik UI, a tool to build forms for apps in ASP.NET AJAX. The vulnerability exists within RadAsyncUpload, a file handler in Telerik UI used for uploading files asynchronously. The discovery of the vulnerability was credited to Markus Wulftange, a senior penetration tester at Code White GmbH, and Paul Taylor, managing consultant at NCC Group, who was responsible for further development of exploit code for the vulnerability.
Researchers at BishopFox published a blog post in December 2019 on CVE-2019-18935. According to their post, CVE-2019-18935 was a continuation of work from Wulftange and Taylor, who were also credited with discovering CVE-2014-2217 and CVE-2017-11317, two vulnerabilities in RadAsyncUpload. Both of these previously discovered vulnerabilities allow for unrestricted file upload through two different attack vectors. Telerik took measures to address them, but each time they did, the vulnerability evolved further and eventually resulted in CVE-2019-18935.
CVE-2014-2217 is an absolute path traversal vulnerability in the RadAsyncUpload control in the RadControls in Telerik UI for ASP.NET AJAX. Telerik’s response to CVE-2014-2217 was to add encryption to “rauPostData,” the POST parameter in the file upload request that contains the file handling configuration details within a serialized object. The issue with the encryption implementation was that the encryption key in RadAsyncUpload's AsyncUploadHandler was hard-coded with a default value of PrivateKeyForEncryptionOfRadAsyncUploadConfiguration. The presence of this hard-coded encryption key was designated as CVE-2017-11317. This vulnerability allows for the modification of the TempTargetFolder variable within the configuration file to define the upload location anywhere on a vulnerable server where the application has write permissions.
In 2019, Wulftange discovered CVE-2019-18935 when he noticed the rauPostData parameter contains not just the serialized configuration object but also the object’s defined type. This defined type is used by AsyncUploadHandler to “prepare .NET's JavaScriptSerializer.Deserialize() method to properly deserialize the object.”
During deserialization, the JavaScriptSerializer class calls on a setter method to define the object type. If an attacker were to specify the object type as a remote code execution (RCE) gadget rather than the expected Telerik.Web.UI.AsyncUploadConfiguration type, it would allow for special properties during deserialization that could facilitate the execution of arbitrary code.
An attacker could combine the previously mentioned unrestricted file upload vulnerability to upload a malicious file with CVE-2019-18935 to define an object type that could execute this code during deserialization. An example of this would be the uploading of a malicious mixed mode assembly DLL followed by setting a deserialization of object type System.Configuration.Install.AssemblyInstaller and defining the path to the malicious file.
Citrix Application Delivery Controller (ADC) and Gateway
CVE-2019-19781 is a path traversal vulnerability in Citrix Application Delivery Controller (ADC) and Gateway that was patched by Citrix in December 2019. At the time, little was known about the exploitability of this vulnerability, but the flaw was severe enough that Tenable Security Response posted a blog post around the vulnerability. In mid-January 2020, Tenable Security Response wrote another blog post detailing active exploitation attacks that had been detected by the security community, which was identified by SANS Internet Storm Center (ISC). At the end of January, another Tenable Security Response blog post was written detailing an increase in attacks observed in the wild.
SANS ISC detected exploitation attempts and detailed the indicators of compromise (IoCs) of the exploit script. These exploits were leveraged by attackers to deploy ransomware on vulnerable targets. In the May 2020 Cybersecurity Infrastructure Security Agency (CISA) top 10 report, CVE-2019-19781 received a mention as one of the most exploited vulnerabilities of 2020.
Sophisticated attackers have created simple exploit scripts that, with little modification, can exploit the directory traversal vulnerability to establish a reverse shell. Once established, an attacker can target additional assets that are otherwise unexposed to the internet.
Microsoft SharePoint
CVE-2019-0604 is an RCE vulnerability in Microsoft SharePoint due to improper input validation in checking the source markup of an application package. At the time the patch was initially released in February 2019, it was assigned a CVSSv3 score of 8.8. Tenable Security Response published a blog post for this vulnerability in December 2019 noting its active exploitation in the wild, which at the time was over nine months after it had been initially patched by Microsoft.
Security researcher Chris Doman published a tweet in May 2019 highlighting reports from the Canadian Centre for Cyber Security (Cyber Centre) and National Cyber Security Centre (NCSC) in Saudi Arabia of active exploitation in the wild.
SharePoint CVE-2019-0604 now being exploited in the wild - reports by Saudi (https://t.co/m6VmF7n2Js) and Canadian (https://t.co/yhzY8qgxi8) National Cyber-Security Centres. Some additional IOCs @ https://t.co/gsGOoh6h9r pic.twitter.com/70LQCOmuTn
— chris doman (@chrisdoman) May 9, 2019
The initial CVSSv3 score of 8.8 was increased to 9.8 after additional analysis from researchers at Cloudflare and security researcher Kevin Beaumont. Cloudflare researchers recommended an increase in the CVSSv3 score based on the findings which was published on their blog in late May 2019. The blog post highlighted that the flaw could be exploited without authentication as “there were paths which could be reached without authentication.” Kevin Beaumont further backed Cloudflare’s evidence of pre-authenticated exploitation in a tweet he published in November 2019, after observing attacks against his honeypots that were modified to support SharePoint.
Yesterday I modified BluePot to support SharePoint honeypots. Today, the attackers arrived. Organisations should put serious focus on patching CVE-2019-0604. Also, the CVE is scored wrong, it should be CVSS 9.8 as it works without authentication. pic.twitter.com/SV5Oq61Ftr
— Kevin Beaumont (@GossiTheDog) November 26, 2019
Over a year later, CVE-2019-0604 continues to be actively exploited in the wild. This flaw has been the source of some prominent and high profile breaches. The Initial reports by the NCSC and the Canadian Centre for Cyber Security both noted the attackers deploying a version of the China Chopper web shell to compromise SharePoint servers. Researchers at Palo Alto Networks have linked attacks exploiting CVE-2019-0604 to APT27 (Emissary Panda), a hacking group reportedly associated with the Chinese government. APT27 would use the SharePoint vulnerability to first compromise a server followed by the installation of a web shell, a trend that was observed by other organizations. The web shells implemented by APT27 included vulnerability scanners, tools to steal credentials, and backdoors. Once APT27 gained the initial foothold on a server they would exfiltrate data, scan the network for vulnerable systems and attempt to pivot to other systems. In May 2020, CVE-2020-0604 was also featured in the CISA top 10 report as one of the top vulnerabilities exploited between 2016 and 2019.
Proof of concept
The following is a list of PoCs for each of these three vulnerabilities.
| CVE | Type | URL |
|---|---|---|
| CVE-2019-18935 | Exploit Script | GitHub Repository |
| CVE-2019-18935 | Exploit Script | GitHub Repository |
| CVE-2019-18935 | Exploit Script | GitHub Repository |
| CVE-2019-19781 | Exploit Script | Github Repository |
| CVE-2019-19781 | Exploit Script | Github Repository |
| CVE-2019-19781 | Exploit Script | Github Repository |
| CVE-2019-0604 | Exploit Script | GitHub Repository |
| CVE-2019-0604 | Proof of Concept | GitHub Repository |
Solution
The “Copy Paste Compromises” advisory from ACSC highlights the fact that attackers are literally copy-pasting proof of concept code and exploit scripts for known vulnerabilities to launch their attacks against unpatched systems. This underscores the importance of applying patches as soon as possible, as attackers will exploit flaws months after patches become available.
Below is a list of patches available for the three vulnerabilities listed in the ACSC advisory.
| Product | Vulnerable Versions/Branches | Fixed Versions |
|---|---|---|
| Telerik for ASP.NET AJAX | v2019.3.917 and below | v2019.3.1023 and above |
| Citrix ADC and Gateway | 10.5 | 10.5.70.12 and above |
| Citrix ADC and Gateway | 11.1 | 11.1.63.15 and above |
| Citrix ADC and Gateway | 12.0 | 12.0.63.13 and above |
| Citrix ADC and Gateway | 12.1 | 12.1.55.18 and above |
| Citrix ADC and Gateway | 13.0 | 13.0.47.24 and above |
| Citrix SD-WAN WANOP | 10.2.6b | 11.1.51.615 |
| Citrix SD-WAN WANOP | 11.0.3b | 11.1.51.615 |
| Microsoft SharePoint Enterprise Server 2016 | KB4462211 | |
| Microsoft SharePoint Foundation 2010 Service Pack 2 | KB4461630 | |
| Microsoft SharePoint Foundation 2013 Service Pack 1 | KB4462143 | |
| Microsoft SharePoint Server 2010 Service Pack 2 | KB4462184 KB4461630 |
|
| Microsoft SharePoint Server 2013 Service Pack 1 | KB4462202 KB4462143 |
|
| Microsoft SharePoint Server 2019 | KB4462199 |
Identifying affected systems
A list of Tenable plugins to identify these three vulnerabilities can be found here.
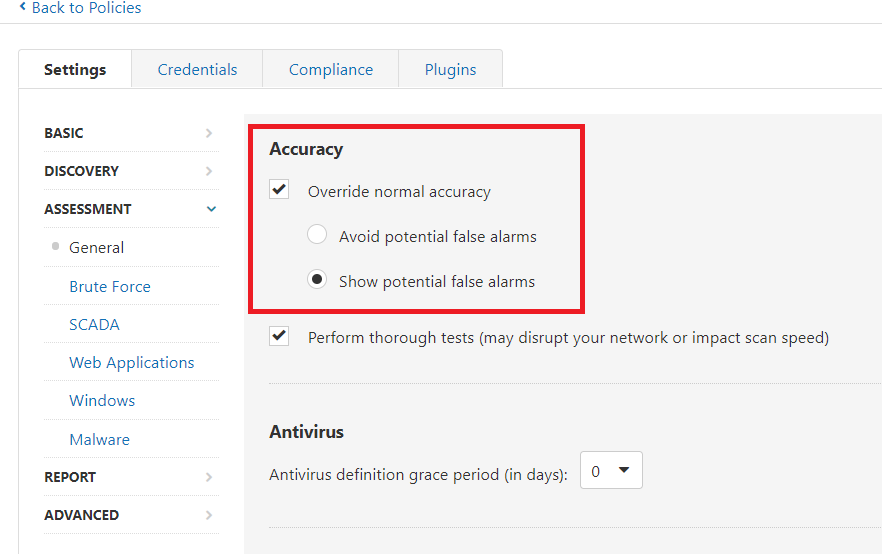
Please note that plugin ID 135970, Telerik UI for ASP.NET AJAX RadAsyncUpload .NET Deserialization Vulnerability, may require “Show false alarms” (also known as Paranoid Mode) to be enabled in your scan configuration. This plugin does not check for an opt-in configuration in Telerik UI for ASP.NET, which prevents the application from being exploitable. Because certain versions may have this workaround enabled, the Nessus scan configuration “Show false alarms” setting is required in order to report on versions of the application which are vulnerable based solely on the version identified.
To enable Paranoid Mode in your scan policy, navigate to “Policies,” select the policy you would like to configure, then navigate to ”Settings,” ”Assessment” and ”General.” Under the “Accuracy” section, select “Override normal accuracy” and then select “Show potential false alarms."
Get more information
- Advisory 2020-008 from Australian Cyber Security Centre
- CISA: Top 10 Routinely Exploited Vulnerabilities
- Bishop Fox blog for CVE-2019-18935
- Tenable's Initial Blog for CVE-2019-19781
- Tenable's Initial Blog for CVE-2019-0604
- CloudFlare: Stopping SharePoint’s CVE-2019-0604
- Palo Alto Unit 42: Emissary Panda Attacks Middle East Government SharePoint Servers
- TrustedSec blog for CVE-2019-19781
- Tenable Blog for Continued Exploitation of CVE-2019-19781
- Tenable Community Instructions for Scanning for CVE-2019-19781
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.