Continuous Asset Discovery Requires Teamwork
Maintaining a current inventory of all the servers, wireless access points, personal computers, tablets, smartphones and web applications used by employees and business partners is not easy. Your networks and subnets can have hundreds of access points, a large number of connected devices not managed by group policy, roaming laptops and mobile devices that are often disconnected when scans occur. These challenges notwithstanding, if an unauthorized device is used to exfiltrate data from your network, “I didn’t know it was on our network” is not an acceptable excuse.
Blind spots
IT asset management tools that you may be using are optimized to detect assets such as PCs, servers, load balancers, firewalls and storage devices used to deliver enterprise applications to the business. But these management tools typically ignore assets not owned by the organization, such as bring-your-own-device (BYOD) endpoints, that can introduce significant risk to networks. BYOD laptops, tablets and smart phones may not be securely configured and uninfected by malware; protected/proprietary data can be transferred to these insecure devices, removed from the premises, and then exposed.
Perhaps even more troubling is the recent trend for protected/proprietary data to move to the cloud—often without IT’s knowledge—where it may be used with applications that offer minimal security. A Frost & Sullivan study reported that more than 80% of survey respondents admitted to using non-approved SaaS applications in their jobs. Typical SaaS unsanctioned applications include publishing, business productivity, social media, file sharing, file storage, and backup. CipherCloud reported that the average global enterprise uses more than 1,100 cloud applications, and that 86% of the cloud applications are unsanctioned by IT.
The blind spots created by BYOD and unauthorized SaaS applications not only increase security and compliance risk, they also can increase legal risk
The blind spots created by BYOD and unauthorized SaaS applications not only increase security and compliance risk, they also can increase legal risk because information retention policies designed to limit legal liability are very unlikely to be applied to electronically stored information (ESI) contained on unauthorized cloud, mobile, and virtual assets.
Expert advice
Maintaining an up-to-date inventory of the assets on your network is critical to good security. It’s common sense; if you don’t know it exists, you can’t know if it is secure. But knowing requires teamwork, and multiple technologies working together can give you the complete visibility you need.
Asset visibility is so important that it is a foundational part of most information security frameworks including:
- Tenable’s Critical Cybersecurity Controls: The first control is “Track your authorized inventory of hardware and software.”
- Council on CyberSecurity Critical Security Controls: Creating an inventory of authorized and unauthorized devices is the first control in the prioritized list of the Critical Security Controls, and creating an inventory of authorized and unauthorized software is the second control on the list.
- NIST Information Security Continuous Monitoring for Federal Information Systems and Organizations – SP 800-137: Information security continuous monitoring (ISCM) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions.
- NIST: Framework for Improving Critical Infrastructure Cybersecurity: The framework advocates a risk-based approach in which “Identify” is a core function.
- ISO/IEC 27001 Information Management Security System Requirements: The standard requires that all assets be clearly identified and an inventory of all important assets be drawn up and maintained.
Continuous visibility
Information security requires continuous asset discovery that uses a combination of active, passive and event-based technologies to ensure that all assets on the network are identified
Information security requires continuous asset discovery that uses a combination of active, passive and event-based technologies to ensure that all assets on the network are identified. Tenable’s SecurityCenter Continuous View™ (SecurityCenter CV™) delivers continuous asset discovery via all three technologies by integrating Tenable’s Nessus®, Passive Vulnerability Scanner™ (PVS™) and the Log Correlation Engine™ (LCE®) into one convenient solution. Additionally, SecurityCenter CV integrates with leading Mobile Device Management (MDM) platforms to obtain an inventory of managed Apple and Android devices that may not be identifiable with other means if they are in sleep mode or are using a 3G/4G connection.
Active scanning
SecurityCenter CV uses the Nessus vulnerability scanner for active network scanning. Active scanning periodically examines your network or a segment of the network for devices that are connected to the network at the time of the scan.
Advantages of active scanning include in-depth analysis of vulnerabilities, malware detection, and configuration and compliance auditing. Active scanning does have a shortcoming: because it is performed periodically, it may miss transient devices and vulnerabilities that arise between scheduled scans. This issue is addressed by a passive scanning capability.
Passive network monitoring
SecurityCenter uses Tenable’s Passive Vulnerability Scanner to continuously analyze network traffic at the packet layer to build a model of active devices and applications on your network. Because passive detection operates 24/7, it will detect transitory assets that may only be occasionally and briefly connected to your network and can send alerts when new assets are detected.
Advantages of passive network monitoring include:
- Identifying transient systems that may only be on the network for a brief time
- Not disturbing the network or sensitive devices on the network, such as industrial control systems
- Visibility into the Internet and cloud services being accessed from systems on the network
With passive network monitoring, passive detection sensors must be strategically deployed throughout the network so they can monitor all desired traffic; if the network is reconfigured without reconfiguring or deploying additional passive sensors, devices and applications may not be detected.
Event log analysis
Event log analysis is the third technique for identifying assets on your network. It can detect systems on network segments that are neither passively monitored nor actively scanned. Log events generated by firewalls, switches and routers will capture the IP addresses of all assets on the network that send and/or receive traffic that reaches the devices. The advantage of event log analysis is that typically the logs are already being generated, so asset identification is as simple as extracting the pertinent information from the log stream. Event log analysis can be like looking for a few needles in the proverbial haystack, but a tool like SecurityCenter’s Log Correlation Engine can automate this process.
Continuous asset discovery
Continuous asset discovery, a capability of continuous network monitoring, uses all these techniques to detect virtually all network assets. It de-duplicates assets detected by different technologies, highlights new assets on the network and provides a preliminary risk assessment, such as the number of known vulnerabilities, for each asset, so risk-based corrective action can be taken.
SecurityCenter CV’s continuous asset discovery capabilities give you comprehensive visibility into all connected devices and insight into vulnerabilities to remove risky blind spots
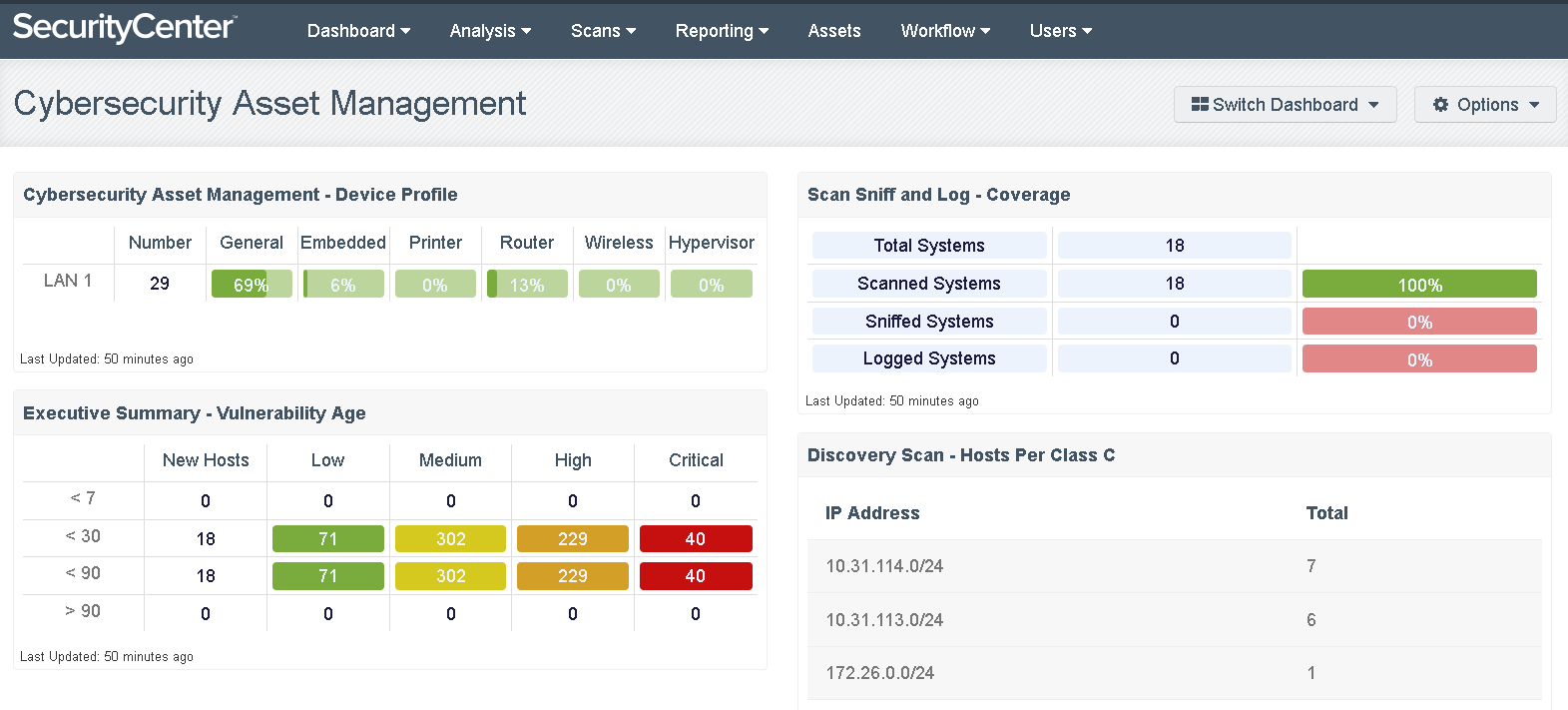
The following dashboard from SecurityCenter CV shows this information in a format consistent with NIST’s Cybersecurity Framework. It delineates assets discovered with active scanning (scanned systems), passive network monitoring (sniffed systems) and log event analysis (logged systems). It also shows vulnerability by age to help prioritize risk-based remediation.
SecurityCenter CV’s continuous asset discovery capabilities give you comprehensive visibility into all connected devices and insight into vulnerabilities to remove risky blind spots.
Learn more
To learn more about continuous asset discovery and SecurityCenter CV, consult these resources:
- Eliminating Cybersecurity Blind Spots whitepaper
- SecurityCenter 5.0 FAQ
- SecurityCenter 5.0 download for existing customers
- SecurityCenter 5.0 demo for new customers
- BYOD
- Vulnerability Management
- Vulnerability Scanning