Cisco and Tenable Integration Enables Swift Response to Vulnerable Hosts
About a month ago, I wrote a blog to understand customer interest in a unified framework that would enable multi-vendor, cross-platform collaboration for identity and access management along with vulnerability assessment. This would allow organizations to increase granularity of device and user visibility for identifying risk in their environment and help expedite review and response to critical issues.
The response I received indicated strong interest on this topic and the feedback revealed an overwhelming need for such capabilities.
Today, we are happy to announce the integration of Cisco Identity Services Engine (ISE) with Nessus Enterprise to enable organizations to address challenging questions such as:
- What systems in my network are at risk or out of compliance?
- Who are the users associated with those systems?
- What risk do these users pose to my network?
- Of these, which require immediate action?
Why is this needed?
Technologies such as BYOD, virtualization, cloud, and SDN are challenging the traditional security and access control models resulting in:
- Point Products: Organizations are deploying multiple point products to secure these technologies and to implement best of breed technologies
- Security Silos: Multiple teams must analyze and manage risk across these products, but can’t obtain relevant context from silos of product deployments
The end result is a lack of centralized security and compliance visibility that takes context from multiple platforms and solutions.
What is Cisco ISE?
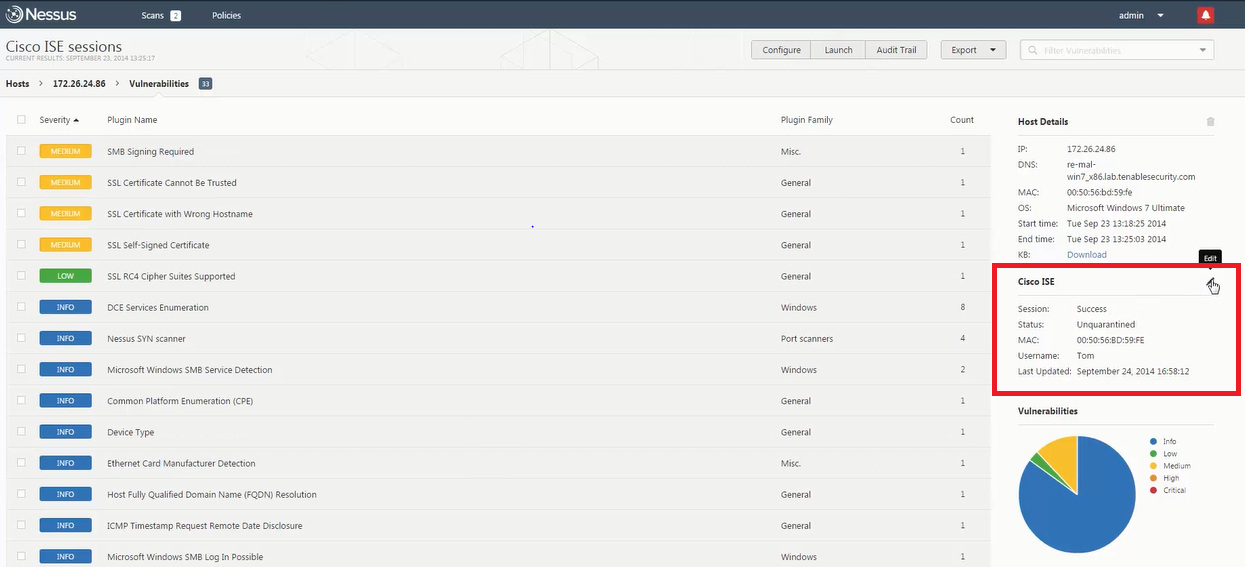
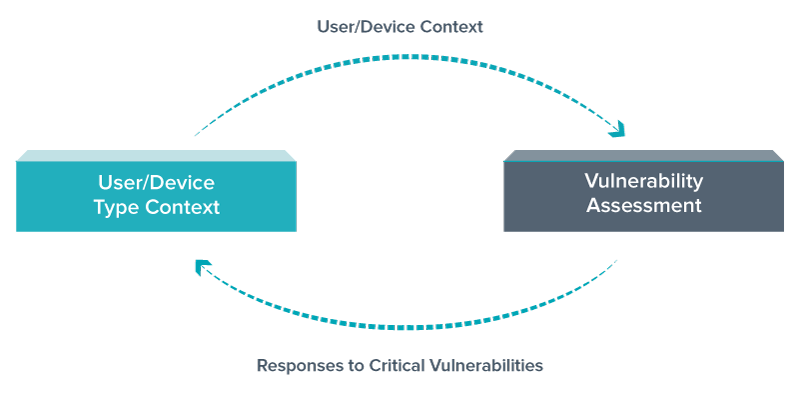
Cisco’s Identity Services Engine (ISE) shares end user and device context with ecosystem partner solutions, such as Tenable Network Security, to identify and mitigate threats. Based on this context, IT teams can then prioritize and remediate vulnerable hosts by initiating quarantine action directly from the Nessus interface.
How does it work?
Here’s how the Nessus + ISE integration works:
- Cisco ISE provides user identity and device information to Nessus via specific APIs.
- Nessus uses this contextual data to provide a comprehensive view of the vulnerability event, user and device data along with vulnerability severity. This helps staff prioritize vulnerability events and leads to a quick response.
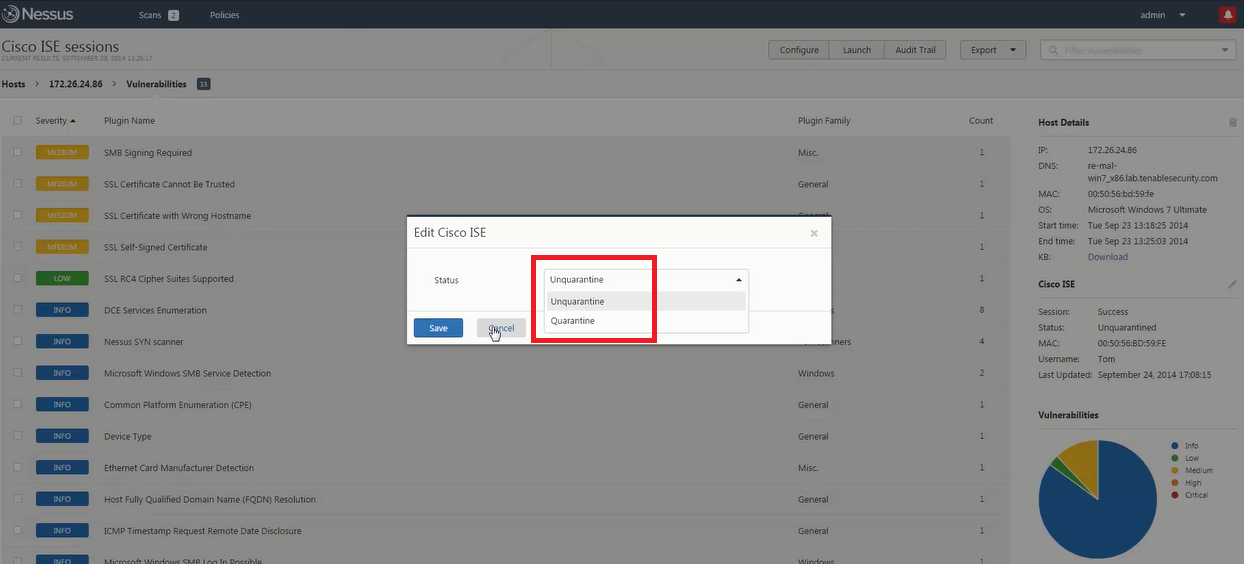
- If the severity of the vulnerability justifies a response, a security specialist can initiate network quarantine action via ISE from the Nessus management console. This provides closed loop management of the event.
What are the benefits?
The integration of Tenable Nessus with Cisco ISE provides the following capabilities:
- Identifies vulnerabilities of your hosts with added insight into the associated users
- Prioritizes vulnerability events through added context
- Enables IT staff to respond to the offending user or device by initiating quarantine actions from within the Nessus interface
For more information on this integration, please visit the Nessus integration page.
- Announcements
- Integrations
- Nessus