Auditing Kubernetes for Secure Configurations

Over the last few years, container technology has gained traction in enterprise environments. And, as a result, use of containerized applications has exploded in the enterprise. Naturally, as its adoption increased, management platforms such as Kubernetes were developed to manage containerized applications. They’ve now become critical to any modern DevOps-focused infrastructure. Tenable recently released an audit to help customers secure this key piece of infrastructure in their environments.
What’s Kubernetes?
Kubernetes is an open-source orchestration platform for deploying, maintaining and scaling containerized applications. Kubernetes was originally developed by Google, and later donated to the Cloud Native Computing Foundation. By leveraging Kubernetes, organizations can:
- Deploy applications in a predictable manner
- Scale workloads up and down
- Limit resource utilization
- Increase availability through self-healing capabilities
Why use Kubernetes?
Organizations choose Kubernetes over other orchestration platforms for many reasons:
- Kubernetes is open source, and part of the Cloud Native Computing Foundation, which has an impressive list of member organizations
- Vendor lock-in is reduced, as deployments can leverage bare metal, virtual machines and public or private cloud – or a combination thereof
- Kubernetes can be used for all size deployments – from single cluster to a scaled-up, federated platform orchestrating multiple geographically diverse clusters
- Vanilla Kubernetes can easily be extended with enterprise-grade options such as Tectonic, Rancher and OpenShift
Why audit Kubernetes configuration?
Depending on the workloads run on Kubernetes, you may consider it a core piece of network infrastructure. After all, it could be hosting the external applications that generate revenue for your business, sensitive internal applications, customer information and more.
Auditing security configurations of such platforms should therefore be an important part of any organization’s security program. A secure configuration audit provides a level of assurance that an information system is configured based on industry standard best practice recommendations.
To protect an information system, you need to account for every flaw that may exist, while an attacker may only need to find a single flaw to exploit. As an example, a recommended configuration is to only allow https traffic to the API server. If the traffic was not encrypted, it may be possible for an attacker to obtain sensitive information such as secrets and keys, and potentially take over control of the cluster. The good news is that Tenable customers now have the ability to perform a configuration audit of your Kubernetes based on the Center for Internet Security (CIS) benchmark.
CIS Kubernetes Benchmark
The CIS recently released the CIS Kubernetes Benchmark, which provides detailed guidance to securely configure core components of Kubernetes, including the Master Node, Worker Node and Federated Deployments.
Master Node(s)
Responsible for managing the workload within the cluster. Services include:
- etcd: A key-value data store for cluster configuration
- API server: A REST service that provides an interface into Kubernetes; state is stored in etcd
- Scheduler: Intelligently determines which nodes workloads should be assigned to
- Controller manager: A process that controllers like the DaemonSet and Replication controller run in; controllers access the API to manage resources
Worker Nodes
Responsible for running workloads within the cluster. Services include:
- Kubelet: Responsible for monitoring the health of containers
- Kube-proxy: Acts as proxy and load balancer for the containers running on the node
- Container runtime: The service which runs the containers, such as Docker
Federated Deployments
Function similar to Master Nodes, except they manage clusters instead of worker nodes. Services include:
- Federation API server
- Federation Controller Manager
Federation is not required in all deployments, so this section may not apply to your organization.
How to get started
To get started, log into Tenable.io and create a new Policy Compliance Auditing scan. In your scan configuration, select the Compliance tab. Under UNIX, CIS Kubernetes Benchmarks are now available. Due to Kubernetes’ deployment flexibility, the audit utilizes variables to ensure the checks are specific to your deployment.
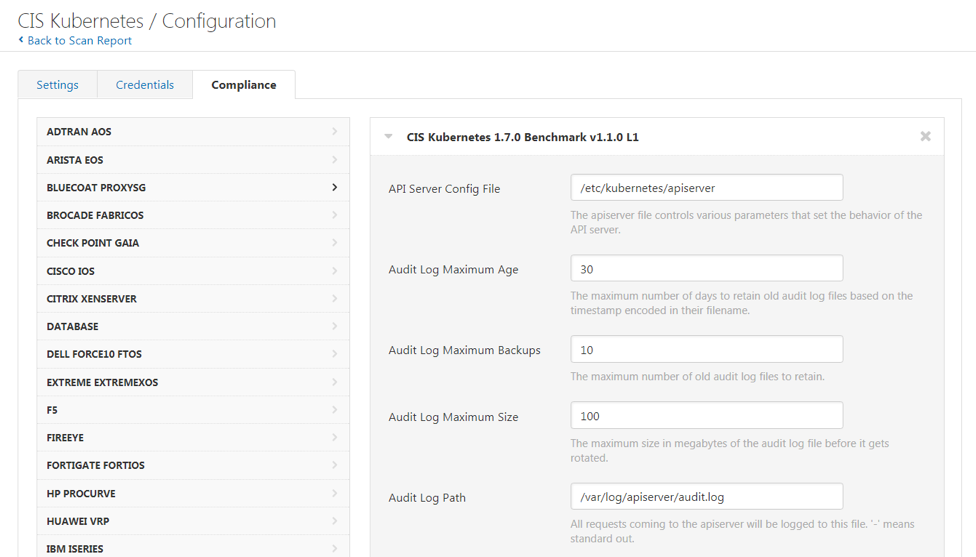
Once the configuration is saved, run the scan and review the results. Below is sample output from a scan. For simplicity, only results from the worker node are displayed.
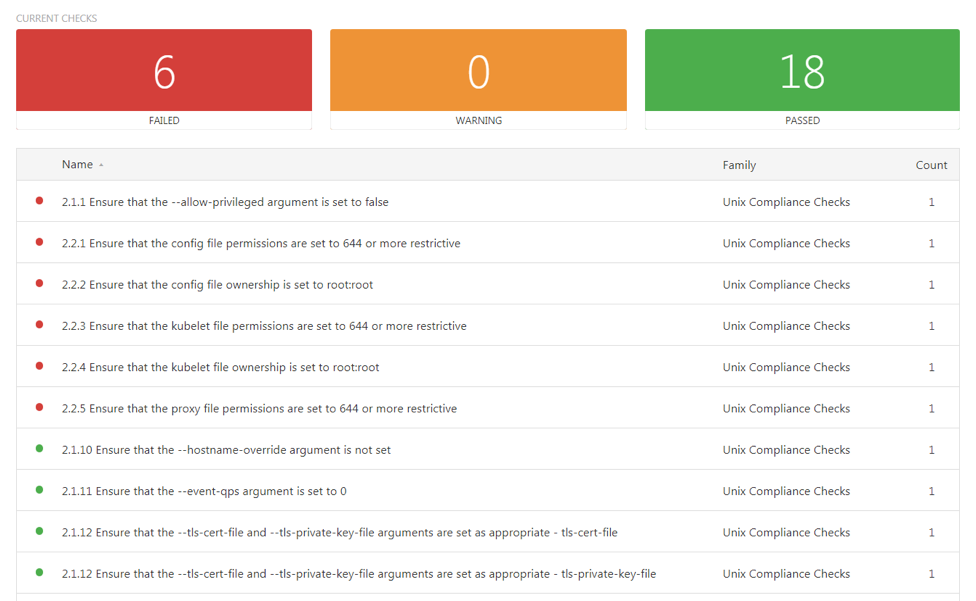
Below is a closer view of one of the results. This page shows:
- Pass/fail status
- Remediation steps, if necessary
- Individual results from the systems scanned
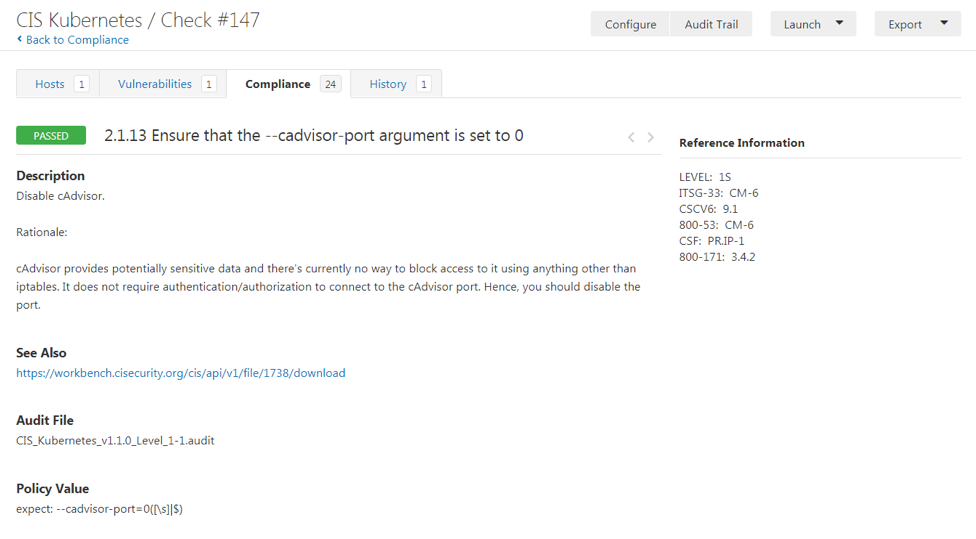
Also, note the reference to cybersecurity frameworks and standards on the right (in the Reference Information section). In this example, the controls listed are:
- ITSG-33: CM-6 – configuration settings
- CIS CSCv6 - 9.1 – ensure that only ports, protocols and services with validated business needs are running on each system
- NIST 800-50: CM-6 – configuration settings
- NIST CSF: PR.IP-1 – a baseline configuration of information technology/industrial control systems is created and maintained
- NIST 800-171: 3.4.2 – establish and enforce security configuration settings for IT products employed in organizational information systems
Depending on the cybersecurity framework your organization follows, you can map these compliance results to the controls to assist you in demonstrating compliance.
Wrap-up: Planning a Kubernetes deployment
When planning a Kubernetes deployment, it’s important to:
- Create or adopt a secure configuration
- Determine how you’ll monitor the configuration
- Establish how frequently you’ll review the configuration
At Tenable, we regularly update our policy compliance audits to match the newest versions by Center for Internet Security (CIS) and Defense Information Systems Agency (DISA). In some cases, we produce our own best practice audits. We also realize there are many cybersecurity frameworks available for organizations to follow, so we regularly map the checks in the policy compliance audits to various framework controls.
- Center for Internet Security (CIS)
- Container security
- Security auditing

