Auditing a Salesforce.com Account with Nessus

Imagine you woke up one day and realized that your top competitor had siphoned off a list of all your customers, sales leads, future customers, and product pricing. You might think that couldn’t happen on your watch, right? Or perhaps you would shrug it off as a bad dream.
Now imagine what would happen if someone broke into your salesforce.com account. Suddenly that bad dream would become a reality.
As the IT landscape evolves from on-premises to co-location, to public clouds, to software-as-a-service (SaaS), and even to a combination of all these architectures, the attack surface is growing and evolving along with it. It’s no longer sufficient to just scan/audit your on-premises deployments and call it a day. This is especially true of SaaS applications which are hosted by a third party in the cloud and over which you, as an end user/administrator, have no physical control.
When it comes to securing services in the cloud, there are two commonly held beliefs. First, if it’s hosted in the cloud then it is already secure; it’s "Fort Knox" secure. And second, a diametrically opposite view that if it’s hosted in the cloud, then it is not secure, trustworthy, or reliable. Needless to say, both extremes are incorrect, and reality lies somewhere in the middle.
So if you are in a position that requires you to secure SaaS applications such as Salesforce, what should you do?
Luckily in this case, Salesforce already does most of the work for you, such as encrypting your data, enabling SSL on the servers, and making sure the physical environment where your application is hosted is secure. But you are still expected to do your part by making sure that access to the application itself is locked down from your end.
The Nessus Salesforce Best Practices Audit verifies over 100 different configuration settings in support of hardening your Salesforce.com deployment.
With the release of Nessus v6, Tenable has provided a new feature that allows Nessus users to do just that. The Salesforce Best Practices Audit verifies over 100 different configuration settings in support of hardening your Salesforce deployment. The Tenable Salesforce best practices are based on guidance in the Salesforce Security Implementation Guide. When you think of Nessus, you probably think of it as a vulnerability scanner, which of course, is its forte. But Nessus can do so much more for your security program: asset discovery, malware detection, patch management integration, actionable alerting, and configuration auditing. The Salesforce Best Practices Audit falls into that last category; it examines the configuration of your corporate Salesforce account and reports back on hardening advice and guidance, rather than looking for vulnerabilities such as open ports on the salesforce.com website.
Here are some high level items verified by the audit:
Trusted IP Ranges
Make sure Trusted IP Ranges is configured for your account so that users can only log in from specific IP address ranges. This is the most important setting you can configure on your account. Once you lock down the IP ranges, the attack surface is instantly limited.
Password Policies
Once you lock down the IP address ranges, the next step is to ensure that the appropriate Password Policies are set. This prevents intruders from guessing passwords and brute forcing their way into your account.
Session Security
Make sure sessions expire/timeout after prolonged inactivity. This protects unauthorized access if the account is left unattended.
User Account Review
And finally, make sure you have a good handle on which users are authorized to access your Salesforce account. The Salesforce Audit provides insight on active users, inactive users, users who haven't changed passwords, new users added in last 7 days, and other relevant activity.
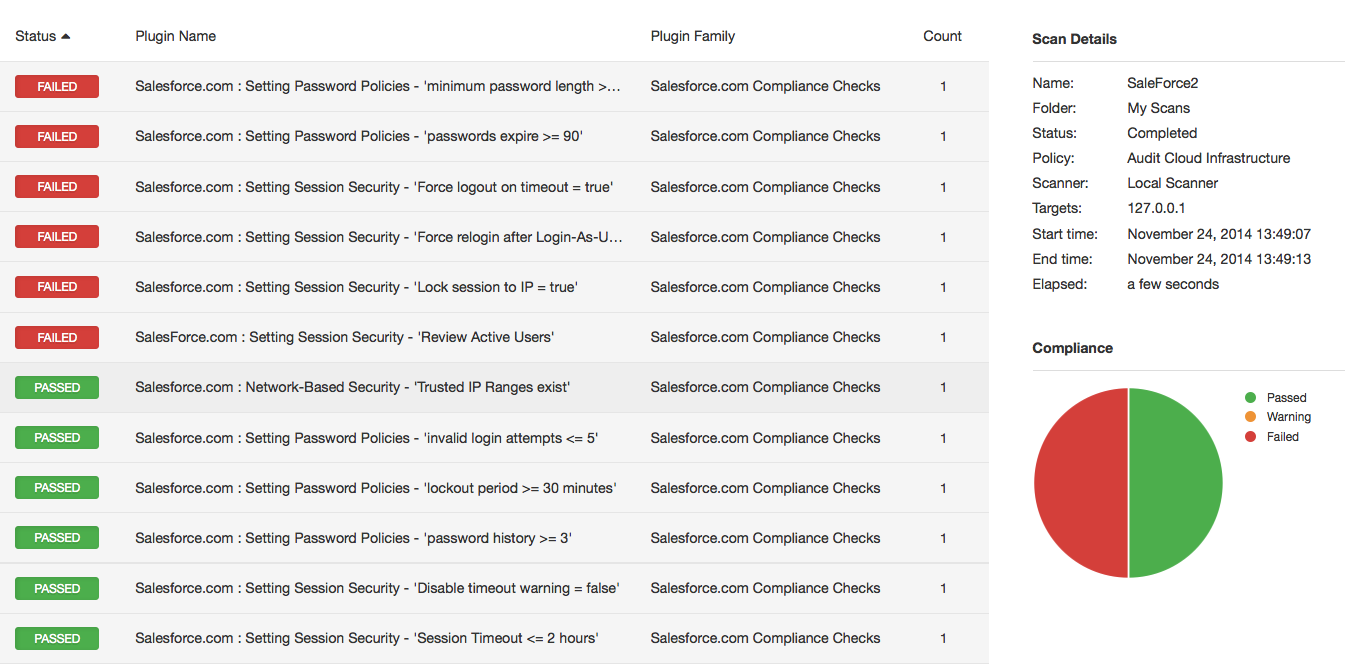
Sample Result
When you run a Salesforce audit, Nessus reports on over 100 checks in a format similar to the following:
To learn more about the Nessus Salesforce Audit functionality, consult the article about TNS Salesforce Best Practices Audit on the Tenable Discussion Forums.
More to come
Hopefully this post has provided good reasons to justify an audit of your Salesforce account. As new technologies emerge, it’s also essential to update your security policies to account for those changes. More importantly it’s crucial that the tool set you use is adapting to the ever-changing landscape. With the addition of both the TNS Salesforce Audit and the ability to scan/audit Amazon AWS accounts, Nessus has a comprehensive library of plugins and audits for both your on-premises and cloud deployments. Over the next several weeks, watch the Nessus feed update for more audits of other cloud-based services and on-premises deployments. We will continue to add more plugins and audits to make the Nessus experience the best in the business.
- Cloud
- Nessus
- Plugins
- Security auditing