by Cody Dumont
July 1, 2020
The Cybersecurity Maturity Model Certification (CMMC) was developed to create a framework to assess an organization's implementation of cybersecurity practices evenly across the defense industrial base. Using NIST 800-53 and NIST 800-171 as the baseline, the primary objective of CMMC is to consolidate the two security catalogs into a single measurable framework. Over the next 5 years, starting in June 2020, organizations that create Government off-the-shelf (GOTS) products, handle Federal Contract Information (FCI), or Controlled Unclassified Information (CUI) will need to show compliance at 1 of the 5 levels. Only Certified 3rd Party Assessment Organizations (C3PAO) will be able to certify an organization as compliant or not. Tenable.sc provides on-prem solutions for assessing Cyber Exposure practices and maps these practices to known assessment regulations such as NIST, CSF, and others. Tenable.sc provides on-prem solutions for assessing Cyber Exposure practices and maps these practices to the CMMC security domains: Media Protection (MP), System & Communications Protection (SC), System & Information Integrity (SI).
The security operations team works diligently every day to protect data and ensure that only the authorized users have access to data. However, data breaches happen daily, not due to a lack of effort. When a user arbitrarily uses applications that don’t protect data, or saves an attachment to their desktop, data may bypass even with the best controls. Tenable.sc uses Nessus Network Monitor (NNM) to monitor traffic that passes through the network. NNM assists the security operations team with controls related to “SC.3.185: Implement cryptographic mechanisms to prevent unauthorized disclosure of CUI during transmission unless otherwise protected by alternative physical safeguards.” By passively detecting data exfiltration, NNM can detect open passwords, SSN, and other PII that could be passing in the clear.
There are many other SC controls that discuss controlling how data at rest is stored, or that discuss USB or removable media. Tenable.sc comes with several audit files that search systems for Personal Identifiable Information (PII). These audit files are designed to look for different categories of PII, for example Social Security Number (By State), Phone No. and Address Info, Financial Statement, and many more. In combination with other configuration audits, the security operations team can thoroughly check all systems on the network for unauthorized data, and configurations that are out of compliance with data leakage prevention regulations.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective cybersecurity practices prescribed by CMMC standard.
Components
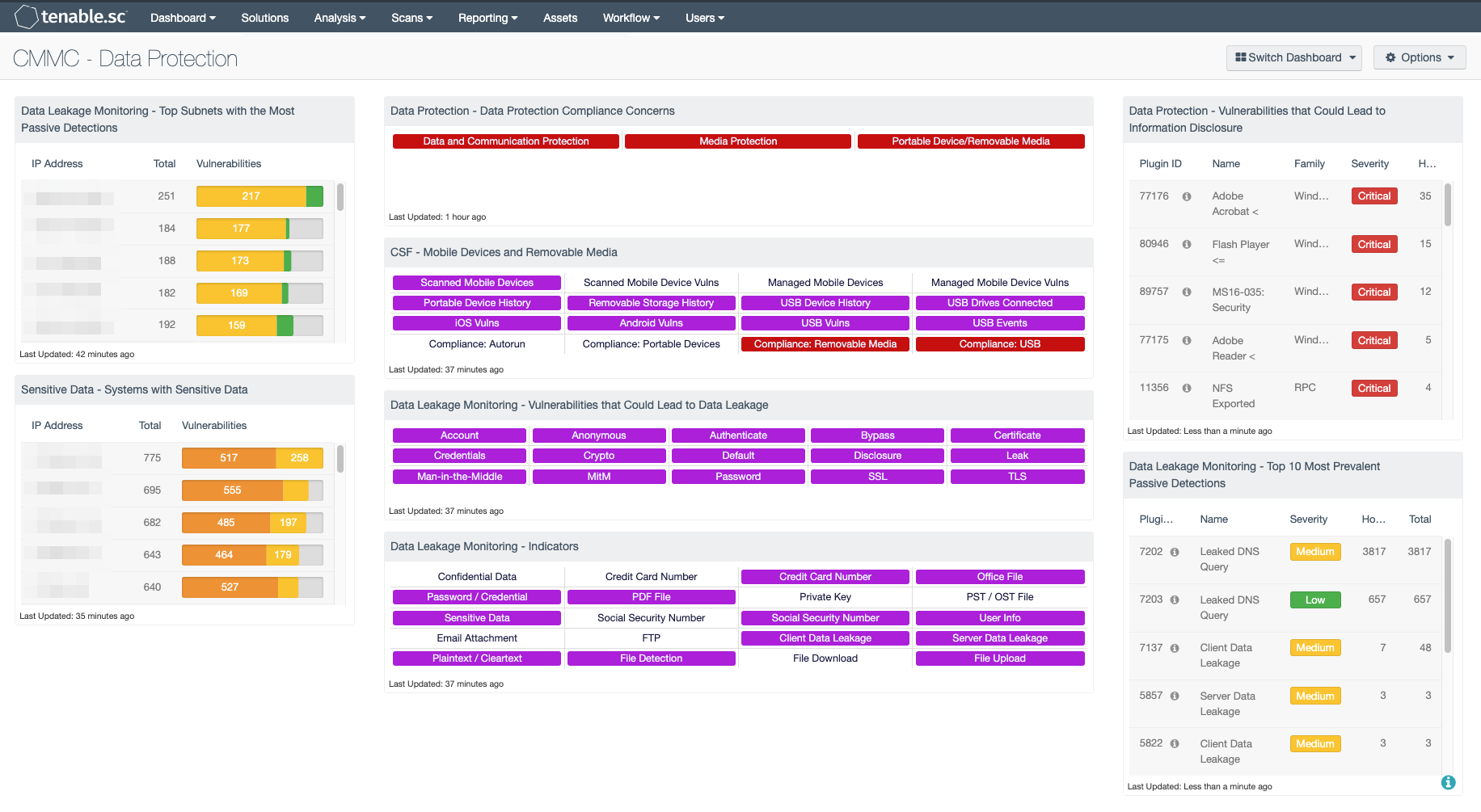
Data Leakage Monitoring - Top Subnets with the Most Passive Detections: This table presents the top Class C subnets with the most passive detections of data leakage. These passive detections are vulnerabilities reported by the Nessus Network Monitor (NNM) in the “Data Leakage” plugin family. The list is ordered so that the subnet with the highest number of detected data leakage activity is at the top. Activity highlighted within this component may include leakage of user credentials, Social Security numbers, file uploads, clear text transmission of credit card numbers, and more. A count of detections and a bar graph indicating the severity of the detections are given for each subnet.
Sensitive Data - Systems with Sensitive Data: This component presents a summary of systems with files that contain sensitive data. In order to identify systems with sensitive data, audit files from the Windows and Unix File Content Template folders are required. Information presented within this component will detect systems with credit card data, Social Security numbers, corporate source code, and other forms of Personally Identifiable Information (PII) stored on them. Systems with the highest number of detections of sensitive data stored on them are at the top of the list. Analysts can modify the component to include additional or specific information per organization requirements.
Data Protection - Data Protection Compliance Concerns: This component presents indicators that highlight compliance concerns associated with data, communication, and media protection. Red indicators are triggered when one or more compliance concerns have failed the compliance check or are out of the compliance range. Clicking on the indicator will bring up the vulnerability analysis screen to display details on the compliance concerns. Compliance issues highlighted within this component may indicate services that need to be disabled, permission changes, and other system hardening controls. The data should be reviewed by security teams to determine the level of risk to the organization.
CSF - Mobile Devices and Removable Media: This component assists an organization in monitoring mobile devices and removable media. Indicators are highlighted purple for mobile devices detected through active and passive scans, and for mobile devices managed through an MDM server. Indicators are also presented for device connection histories, vulnerabilities, and USB events. Additional indicators are highlighted red for compliance failures related to portable devices and removable media. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
Data Leakage Monitoring - Vulnerabilities that Could Lead to Data Leakage: This component presents indicators by keyword for actively and passively detected vulnerabilities that could lead to data leakage. Vulnerabilities at all severity levels except Informational are included. The keywords cover disclosures, cryptographic issues, man-in-the-middle vulnerabilities, and weak authentication concerns. A purple indicator means that one or more vulnerabilities contain the keyword. Clicking on the indicator will bring up the analysis screen to display details on the vulnerabilities. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. This component can be used to investigate vulnerabilities that could lead to data leakage.
Data Leakage Monitoring - Indicators: This component presents warning indicators to draw attention to types of data that may have been leaked and methods whereby data may be leaking. These indicators make use of both passive detections and events logged within the last 72 hours. A purple indicator highlights a vulnerability/event detection. In two cases (Credit Card Number and Social Security Number), there are two indicators: one to highlight data leakage detected passively and one to highlight data leakage detected through logged events. Clicking on a highlighted indicator will bring up the analysis screen to display details on the vulnerabilities/events. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities/events are present. This component can be used to further investigate any data leakage.
Data Protection - Vulnerabilities that Could Lead to Information Disclosure: This component presents a list of actively and passively detected vulnerabilities that could lead to data disclosure. Vulnerabilities at all severity levels except Informational are included. The keywords cover disclosures, cryptographic issues, man-in-the-middle vulnerabilities, and weak authentication concerns. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to allow further investigation of the vulnerabilities. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. This component is used to strengthen security controls and better protect data.
Data Leakage Monitoring - Top 10 Most Prevalent Passive Detections: This table presents the top 10 most prevalent passive detections of data leakage. These passive detections are vulnerabilities reported by NNM in the 'Data Leakage' plugin family. A count of detections is given for each vulnerability; the list is ordered so that the vulnerability with the greatest number of detections is at the top. The severity of the vulnerability and a count of hosts on which the vulnerability was observed are also given for each vulnerability.