Securing Portable Devices and Sensitive Data in Healthcare
The high-profile healthcare breaches this year alone, as well as the growth of the lucrative market for healthcare information (“over $500 for a complete dossier”), are a testament that current security processes and solutions require a re-evaluation.
Organizations of all types are undergoing a structural transformation of their IT infrastructure, thanks to mobile devices and the growth of the mobile workforce. Particularly in the healthcare industry, IT networks are expanding well past the secure corporate walls. Doctors, nurses, and healthcare staff are demanding information access from multiple devices and multiple locations to enable faster and collaborative patient care. In addition, the lines between employees’ work and personal devices are blurring.
Hospitals lack the right tools to protect mobile devices
IT and healthcare industry trends
In a recent healthcare webinar, Renee Murphy, Sr. Forrester Analyst, and Craig Shumard, former healthcare CISO and principal with Shumard Associates, noted the following observations:
- Tablet and smartphone usage is outpacing traditional computers: Global information workers are using multiple devices (laptops, smartphones, tablets)
- 33% of healthcare employees are working outside of the office at least once a week
- Top 3 security risks for US healthcare security decision-makers are:
- Employee-provisioned devices (laptops, smartphones, and tablets for business use)
- Consumer-oriented communication and file-sharing tools run on resources
- Employee-provisioned applications (including software and web services like Facebook and Twitter)
- Hospitals lack the right tools to protect mobile devices: only 35% of surveyed global business and technology decision-makers in healthcare that allow employee use of smartphones have security policies and feel their tools are sufficient
- Employees are bypassing security to get work done: 50% of North American and European information workers surveyed will sometimes ignore or go around their company’s security policies to get what they need done
Employees are bypassing security to get work done
When considering the demand for access to healthcare data at any time, from anywhere, from any device, and by a multitude of workers, the need to protect ePHI (electronic protected health information) and PII (personally identifiable information) has never been greater. On the other hand, patients expect their healthcare providers to protect their privacy and to keep their health and personal information secure. Consequently, every healthcare organization faces this fundamental challenge — how to secure healthcare data on these portable devices and the applications on them, while continuously meeting compliance requirements?
New Tenable solutions to secure portable devices and data
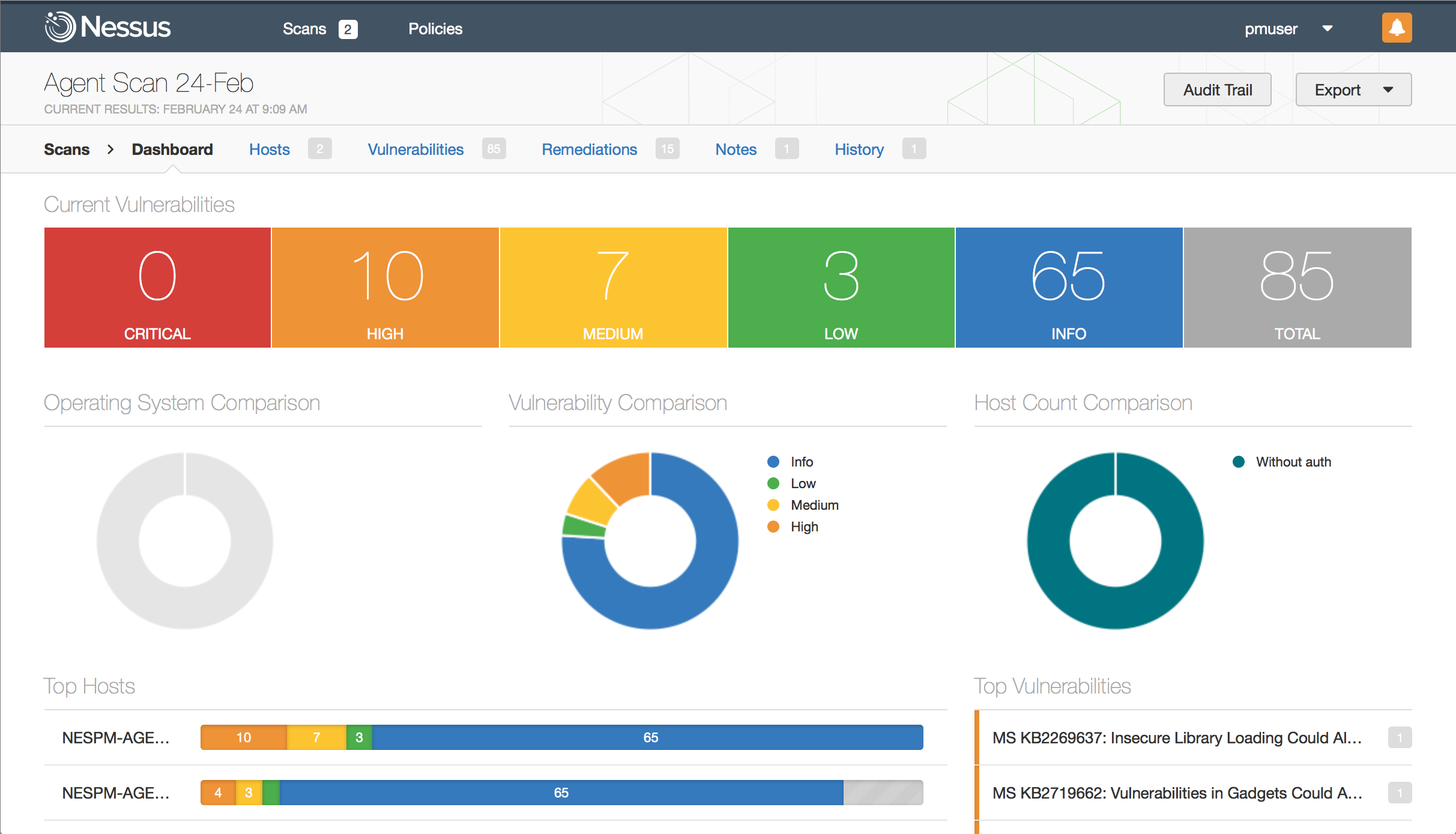
Tenable can help. Today, both Nessus and SecurityCenter Continuous View™ (SecurityCenter CV™) detect and audit networks and endpoints to identify and monitor sensitive healthcare data that’s stored or transmitted. Tenable recently extended these capabilities by partnering with Cisco and MobileIron to include user context as well as mobile device assessment. And, unlike other solutions, Tenable’s new Nessus Agents provide the option to monitor the security and compliance posture for portable systems even when disconnected from the network. Both solutions help healthcare organizations expand their scan coverage in different ways, for different types of assets.
Managing secure access, mobile device usage, and security
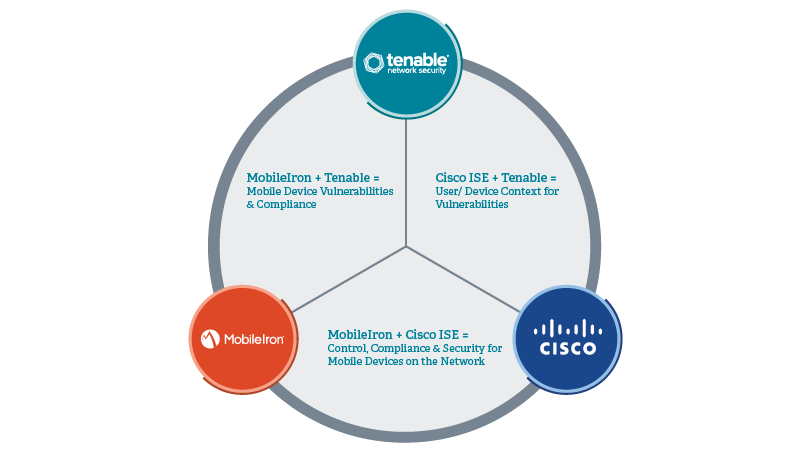
Visibility and context about users, devices, and data across solutions is essential for building secure access and risk management policies. The Cisco Identity Services Engine (ISE), MobileIron Enterprise Mobility Management (EMM), and Tenable Nessus and SecurityCenter solutions each provide essential capabilities that healthcare organizations require, but are more powerful when deployed together to provide visibility, access, and control over network users. Together, they also centralize, simplify, and expedite the detection and remediation of healthcare security and compliance issues.
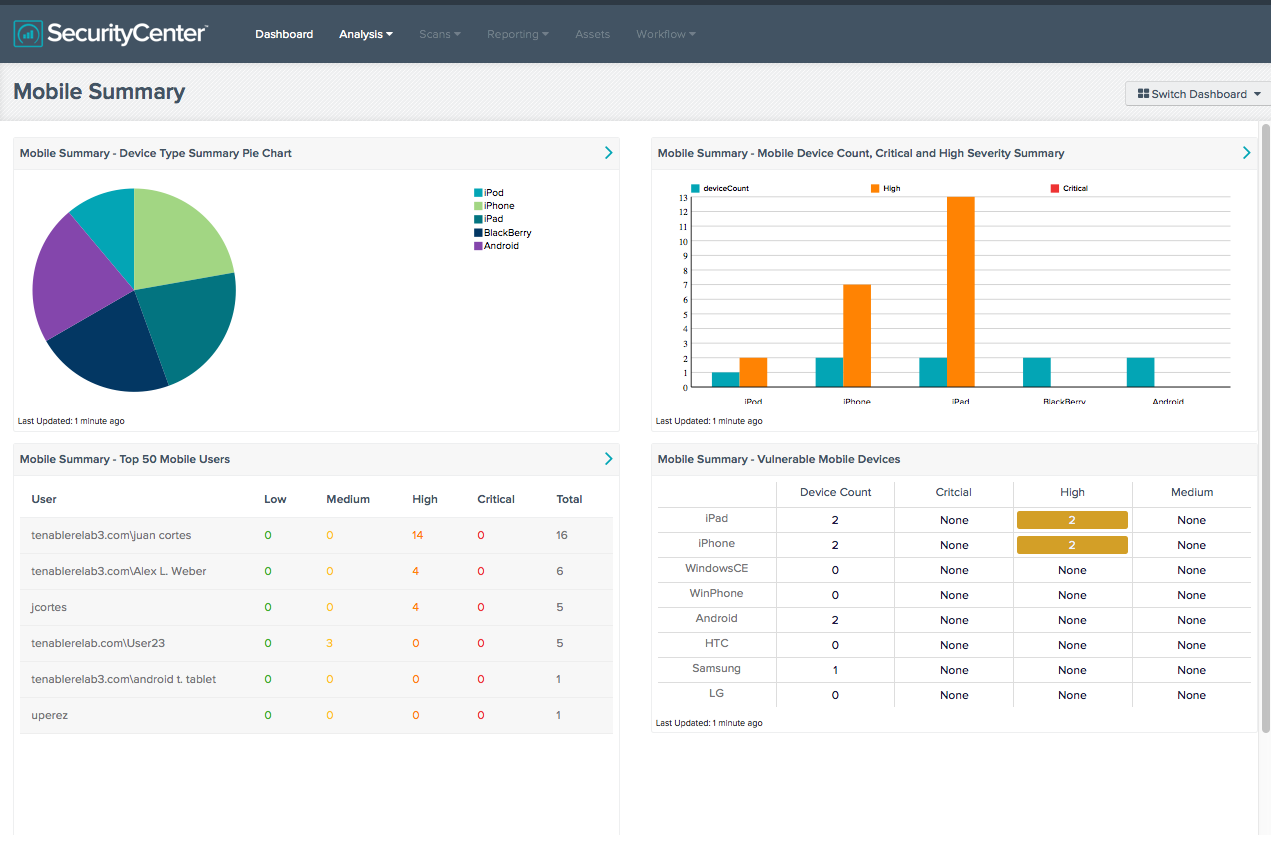
Device Control: MobileIron captures smartphone and tablet details such as device type, software version, and OS version. When integrated with Tenable solutions, the MobileIron data is used to identify vulnerabilities and compliance violations from mobile devices. In addition to MobileIron, Tenable also supports other major MDMs including Microsoft Exchange, Apple Profile Manager, AirWatch, and Good for Enterprise.
Nessus Agents provide the option to monitor the security and compliance posture for portable systems even when disconnected from the network.
Access Control: Cisco ISE provides endpoint access profiling along with user identity and device context. When integrated with MobileIron, access control can be extended to cover mobile devices so that only authorized devices are granted access. It also allows healthcare security and compliance teams to create access policies for mobile devices with user context. When combined with Tenable solutions, this can be further refined to provide or deny access to systems based on their security or compliance posture.
User Control: Cisco ISE captures user identification and device type context in order to provide role-based network access policies. When integrated with Tenable solutions, it allows healthcare organizations to not only identify risk introduced by devices that connect to the network, but also merges context about the users associated with those devices. This enables healthcare teams to make informed decisions about initiating appropriate responses.
Data Control: In addition to identifying all connected devices, Tenable solutions can also detect unencrypted sensitive data and medical information, such as PII or ePHI, that are stored or transmitted by these systems. The context from MobileIron provides mobile device information if sensitive data is transmitted from critical systems to mobile devices. The user identity information from Cisco ISE can further help in identifying users who are associated with the transmittal systems.
Securing laptops and other transient devices
Many healthcare organizations have employees who are not regularly connected to the corporate network – doctors who have privileges at multiple hospitals, “road warrior” home healthcare nurses, remote workers, telecommuters, or those who bring work home with them on their laptops. If those laptops aren't connected to the VPN when a scan is happening, they don't get scanned. Many of those laptops could be compromised, especially if these healthcare workers are conducting personal activity on them — directly exposing the laptops to malware and other types of threats.
Nessus Agents can provide visibility into parts of a healthcare organization’s network that would have previously been difficult or impossible to scan
Using the new Nessus Agents, hosts (e.g., laptops, desktops, virtual systems, or servers) can run local Windows, compliance, or advanced (a combination of Windows and compliance) scans while they’re not on the network, and then call back in to Nessus Manager once they obtain their results. Nessus Agents can provide visibility into parts of a healthcare organization’s network that would have previously been difficult or impossible to scan using traditional methods. Also, because agents are installed similarly to other Windows applications, there is no need to create additional user accounts or manage system account passwords.
Continuously managing risk in healthcare and mobile devices
Nessus Agents and the joint Cisco, MobileIron, and Tenable solution complement the existing healthcare and mobile device risk management and compliance capabilities of Tenable’s SecurityCenter CV. SecurityCenter CV delivers powerful results for healthcare organizations including medical and mobile device discovery, inventory, and automated vulnerability assessment, as well as dashboards and reports to easily display and distribute findings.
SecurityCenter CV’s passive network monitoring component, Passive Vulnerability Scanner (PVS), is especially helpful to healthcare organizations. By continuously monitoring network traffic, PVS identifies server- and client-side vulnerabilities in new and transient assets (including BYOD/mobile devices), detects and tracks sensitive medical devices that can’t be actively scanned, identifies mobile operating systems (OS), and detects application and OS vulnerabilities. In addition, PVS detects unencrypted ePHI and PII in motion.
Resources
For more information on how Tenable solutions can help secure the portable devices and sensitive data in your healthcare organization, see the resources below or contact us or your local authorized Tenable reseller.
Related Articles
- BYOD
- Healthcare
- Integrations
- Security Frameworks
- Vulnerability Management