Putting OSVDB to work for Nessus Vulnerability Management
A customer recently asked us to provide a count of patches issued in 2009 for various Unix and Linux-based operating systems. To honor their request, we turned to OSVDB, the Open Source Vulnerability Database. OSVDB covers over 60,000 vulnerabilities, spans over 26,000 products and has a powerful search engine that can produce search results based on disclosure date(s), vendor and/or product, CVSSv2 scores, references, vulnerability classifications and more. When generating any statistic regarding vulnerabilities, it is important to qualify the statistics and understand they are only as good as the data set that generated them. While OSVDB does not have a complete data set, it is the only Vulnerability Database (VDB) that provides powerful and flexible search capabilities.
Searching through 2009 vulnerability disclosures, we gathered some rather interesting numbers:
Title search by OS name:
| Operating System | Vulnerabilities |
| Solaris | 84 (69 *) |
| AIX | 15 |
| HP-UX | 9 |
| Debian | 6 (3 **) |
| Red Hat | 7 (5 **) |
| Linux Kernel | 107(***) |
* Solaris results need to be altered after visually scanning the results to account for 15 titles that contain ‘Solaris’, but pertain to OpenSolaris or vulnerable software when run on Solaris.
** The Debian and Red Hat results need to be altered after visually scanning the results to account for titles indicating third-party software that is vulnerable when run on a specific distribution, but not necessarily software authored by Red Hat. It is easily debated if these vulnerabilities should be factored in, as Red Hat or Debian may have introduced configuration-based vulnerabilities.
*** Linux kernel vulnerabilities will affect both Debian and Red Hat.
Using title and the classification system, it is possible to filter results based on patch or upgrade availability:
| Operating System | Patch Available | Upgrade Available | Patch + Upgrade Total * |
| Solaris | 64 | 0 | 64 |
| AIX | 11 | 1 | 12 |
| HP-UX | 9 | 1 | 10 |
| Debian | 4 | 1 | 5 |
| Red Hat | 0 | 0 | 0 |
| Linux Kernel | 73 | 21 | 94 |
* These numbers may be misleading as a vulnerability can have both a patch and upgrade solution.
As shown below, when we ran a search for the “OS upgraded” category, we performed a title search for each individual OS, a date range of December 31, 2008 to December 30, 2009, and selected “Upgrade” under “Solution”:
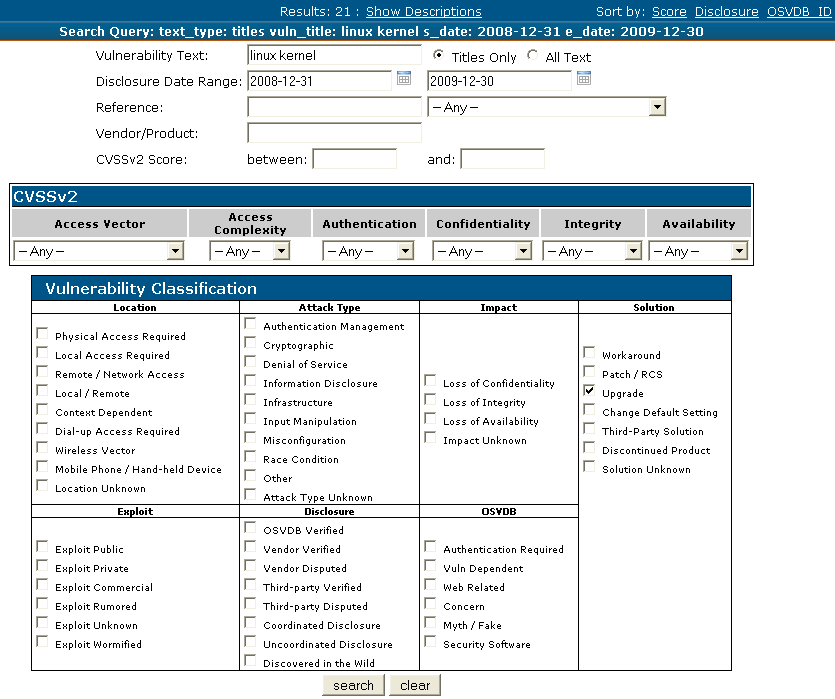 |
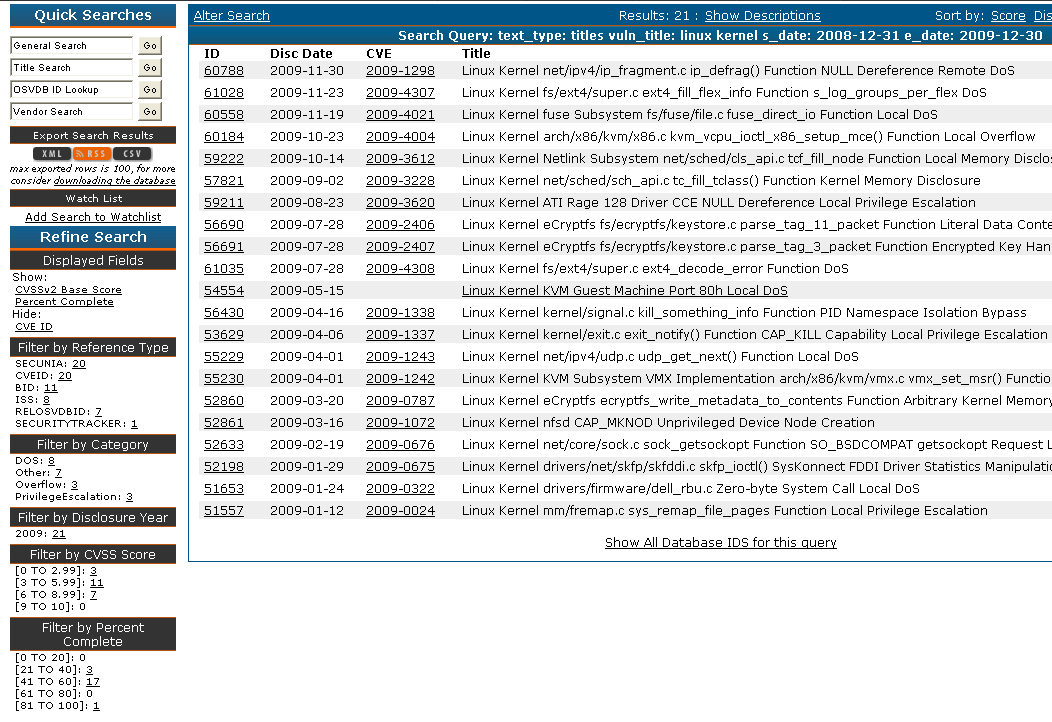 |
While we feel that the numbers for Solaris, AIX and HP-UX are fairly accurate based on the year’s list of advisories, we also realized that trying to determine a patch count for Red Hat, Debian or any Linux distribution would be messy. For instance, Red Hat will sometimes issue patches for third-party products before the software’s actual author or vendor does, which ends up complicating matters when doing queries for “solution = patch/RCS”. Since many kernel vulnerabilities cross Linux OS platforms, we added a title search for “Linux kernel” and found that up to 87.85% have patch or upgrade coverage, which would appear to be somewhat low. “Linux kernel” covers Red Hat and Debian OSs as well as other distributions such as Ubuntu and SUSE, so additional research is required to determine which specific OSs are affected by a particular kernel vulnerability. To truly get a better idea of coverage, you would also need to consider if the vulnerable kernel functionality is installed on the Linux distribution, or if it is disabled by default.
While OSVDB strives to be as inclusive and current as possible, we realize that there are other sources of information that could dramatically change the results of our searches if those sources were factored in. Mailing lists and other vulnerability databases may contain information about patches for programs or libraries used by multiple operating systems, not to mention the seemingly never-ending flow of vendor changelogs that need to be reviewed and analyzed in detail to determine whether or not a vulnerability existed in a product and was eventually patched. While we did mention that the statistics listed above are only as good as the dataset that generated them, it’s important to note that they can still provide value to an organization looking to prioritize its patch management procedures or organize its overall IT efforts.
Using Nessus to scan for missing patches or upgrades is a crucial part of any vulnerability remediation process. As an example, we show an excerpt from Nessus Plugin 42431:
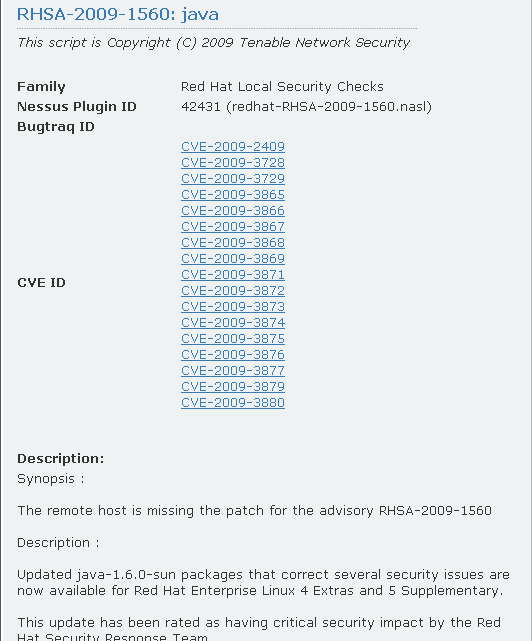 |
Using OSVDB to search for RHSA-2009-1560, we see that 13 vulnerabilities are linked to the RHSA-2009-1560 advisory:
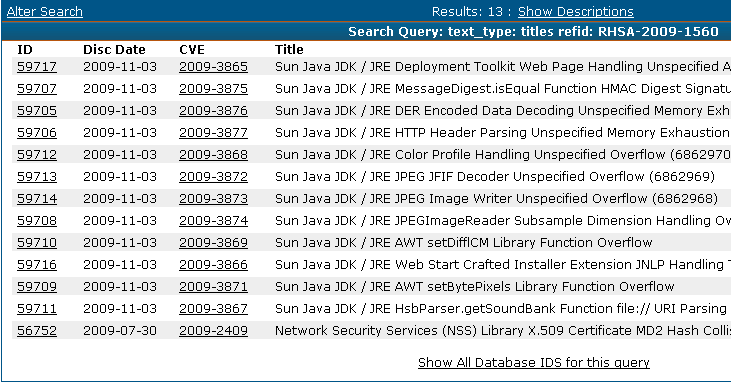 |
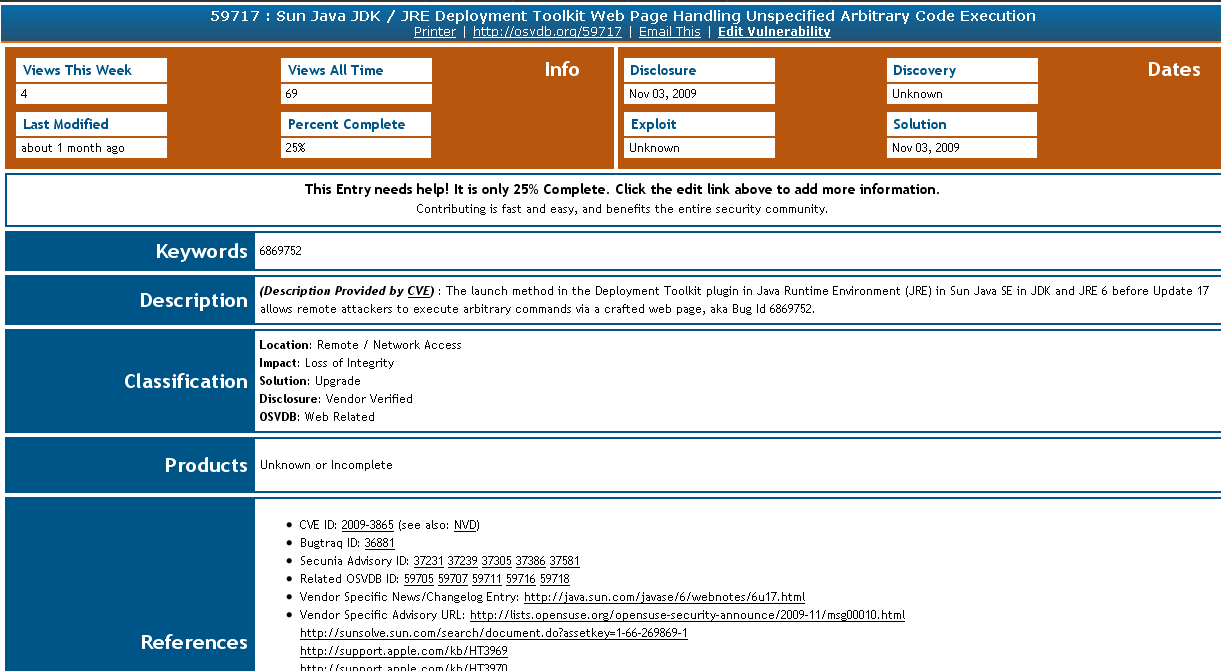 |
Nessus will identify missing patches and OSVDB can be used to provide additional references to give system administrators more information about a particular vulnerability. While one CVE may cover several vulnerabilities, OSVDB typically abstracts and creates unique entries for each issue. This may assist administrators as each entry can in turn have a distinct CVSS score or workaround solution.
System administrators are generally confronted with a wide variety of challenges in their particular environments, which usually includes the need to seek additional information about vulnerabilities and solutions that effectively fix those vulnerabilities. In addition to resources such as OSVDB, we also encourage system administrators and security practitioners to use online resources provided by Tenable, such as the Tenable blog page, podcast and RSS feeds to assist in securing their network assets.
Related Articles
- Nessus







