How to Know If Your Smart Home Is Vulnerable

Do you ever wonder if your smart home is vulnerable to cyber threats? As we place more and more connected devices in our homes to automate simple tasks that used to be done manually, we also place more and more risk for unwanted attackers to compromise our personal lives.
What if you had a way to find out whether there are vulnerabilities in your home systems that attackers can exploit?
You’re in luck! You can use a vulnerability scanner like Nessus Essentials to do the job. In this post, we will step through the quick, four-step process.
Before getting started: Although unlikely, scanning may cause device disruption. Typically, rebooting the device will bring it back online.
#1. Set up your scanner
Register and download Nessus Essentials.
Once you register, you will receive an email with the activation code. Next, download the appropriate Nessus file for your operating system.
Install Nessus Essentials by opening the file and proceeding through the wizard. Once complete, a browser should open up that takes you to the Nessus Scanner website on your local machine. If the website does not appear, open a browser and head to https://localhost:8834.
Nessus will begin to compile its plugin database, so you can scan for vulnerabilities.

Plugins are scripts that check for vulnerabilities on your smart home devices. For example, there is a Windows plugin that checks for all installed software on your computer.
You can search for more plugins here.
Once the Nessus Essentials user interface loads, you will be prompted to create a username and password. You’ll also need to enter the activation code previously sent to your email.
#2. Set up a scan
Afterward, you will see the following screen where you can enter your target IP.
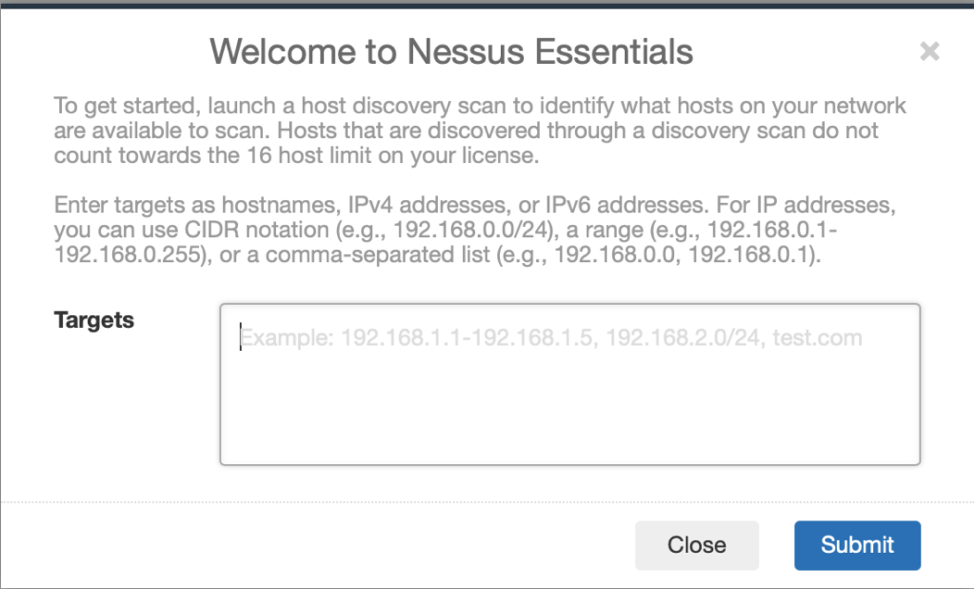
Place the local IP address of your smart home device in the Targets box and then click “Submit.” Don’t know the local IP address of your smart home device? Log in to your home router and look at the connected devices section. This section will list all items connected to your router and their local IP address.
#3. Run your first scan – and review the results
Nessus will then attempt to find the device’s name. Select the device in the box below and click “Run Scan.”
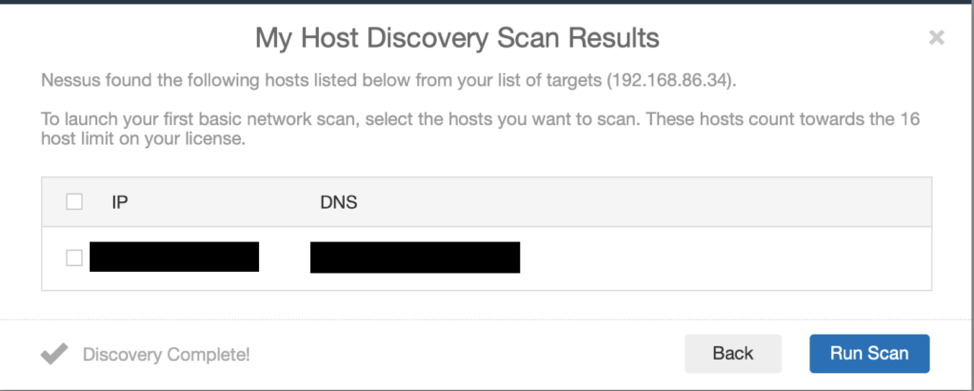
Once the scan completes, review the results of the plugins.
By looking at my OS identification Plugin, we can see that this is my Smart TV.
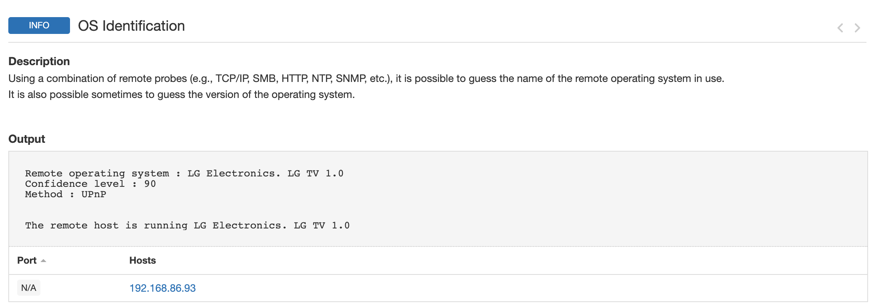
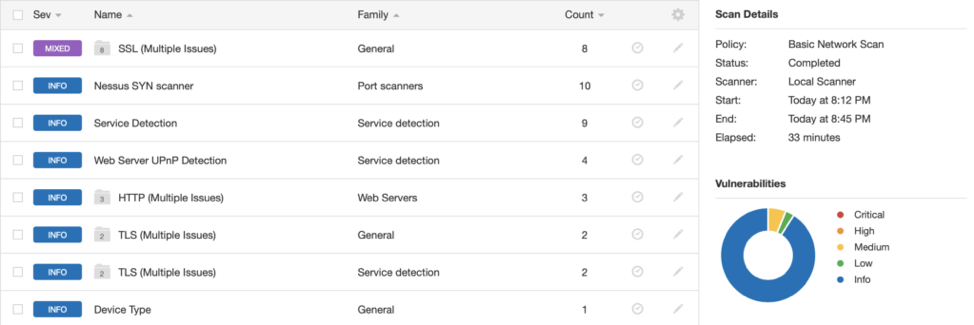
Upon reviewing the overall results, you can see that my Smart TV has some SSL issues as well as HTTP and TLS issues. We can take a closer look by clicking the issues.
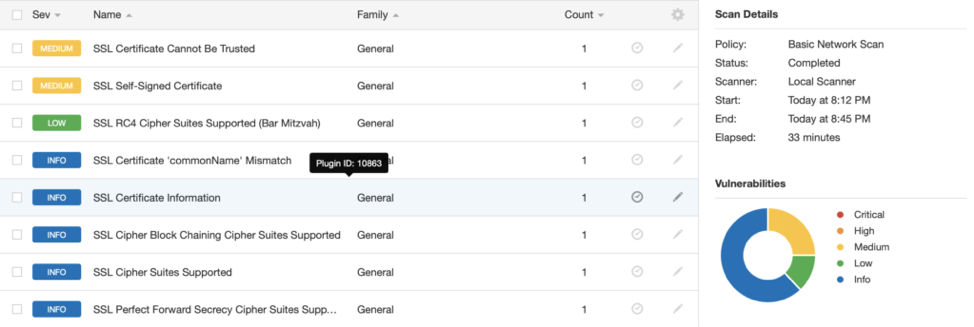
By clicking once more on a particular plugin, you can find further information.
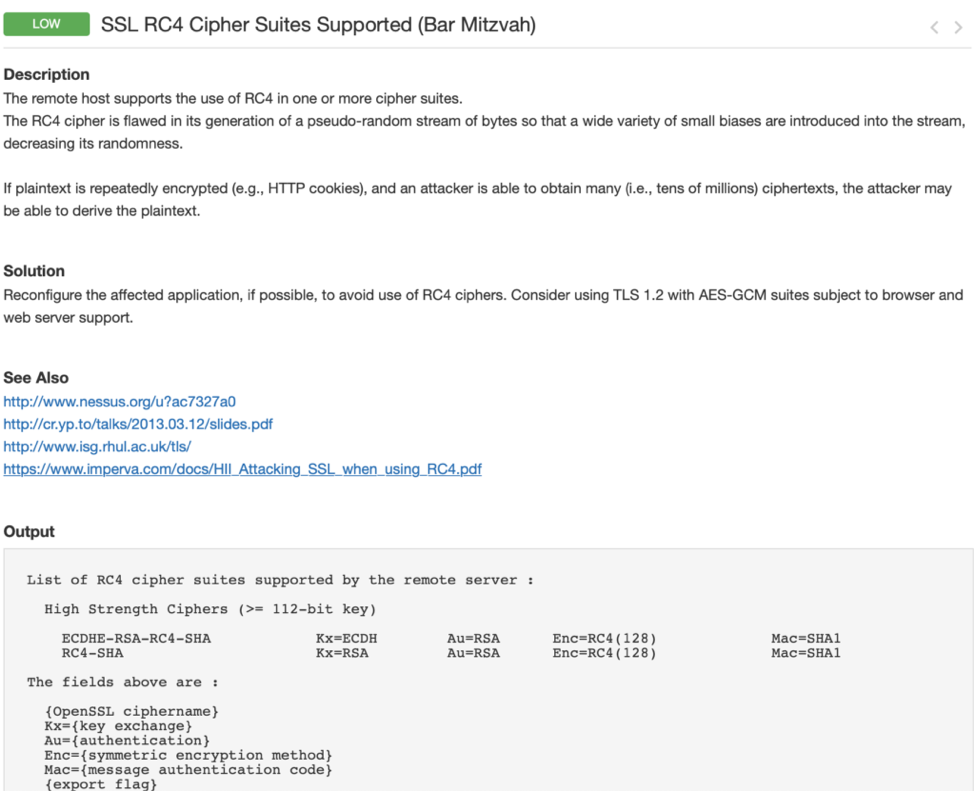
#4. Decide whether you need to take action
By looking at the Description, Solution, See Also and Output sections, you can determine if this vulnerability is a threat to the device, if exploited. Once you have a good understanding of the vulnerability, take action with the recommended solution and/or contact the device vendor about the vulnerability to request an appropriate fix.
Note: It may not always be possible or necessary to remediate the vulnerabilities found with your vulnerability scanner. Also, the device vendor may release an update before the vulnerability is remediated.
Related Articles
- Nessus
- Vulnerability Management
- Vulnerability Scanning






